ArcSight Enterprise Security Manager (ESM) is a Big Data analytics-based enterprise security solution that transforms Big Data into actionable intelligence. ArcSight ESM is a demand security event data collection, correlation, and reporting solution. This ArcSgith SIEM blog explains deeply the components of ArcSight, architecture, overview, and its features.
The following topics will be covered in this “ArcSight SIEM” blog:
| Table of Content - ArcSight SIEM |
|
➤ SIEM ArcSight Architecture Overview |
What is SIEM ArcSight?
ArcSight is a platform for Enterprise Security Manager (ESM). It is a tool created and used to manage the company's security policy. It can promptly detect, analyze, and resolve cyber security risks. Event collection, real-time event management, log management, automatic response, and compliance management are all products available on the ESM platform.
| If you want to enrich your career and become a professional in ArcSight, then enroll in "ArcSight Online Training" - This course will help you t o achieve excellence in this domain. |
SIEM Arcsight Overview
Arcsight is an enterprise security manager (ESM) that includes data intake and interpretation, threat feed connections, real-time device correlation, data analytics, security alerts, and user data display via UI (user interface) dashboards and data reporting.
Baselining and mechanism notification are also supported by ESM, which may be accomplished by integration with various analytical tools such as Arcsight user behavior analytics or UBA. Data enrichment elements such as data evaluation, network modeling, geo-location, user modeling, and vulnerability are also included in Arcsight.
Why SIEM ArcSight?
The following are the main reasons why SIEM ArcSight is required:
- SIEM is an acronym for "Synthetic Intellig ArcSight supports Hadoop's big data features and assists with event collection and data analysis.
- SIEM is a two-letter acronym that stands for " ArcSight uses machine learning to aid with a variety of event management activities.
- Easy integration of threat risk management services with third-party and external users.
- This tool also aids in the administration of Active Directory objects and properties. Additionally, it aids in the management of Active Directory permissions.
- Manage the permissions of the target system and provide extensive configuration and customization options.
- Connectivity with people, things, and devices that are secure. This application also allows you to assess the setup of many system properties.
- SIEM ArcSight is also a cyber security technology that aids in protecting devices from threats and the management of licenses.
SIEM ArcSight Architecture Overview
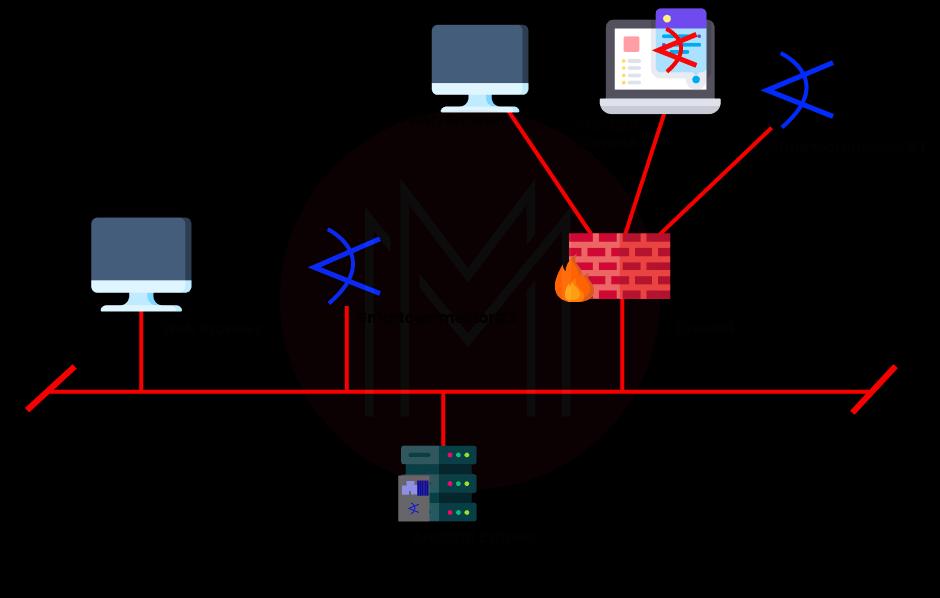
The SIEM ArcSight architecture shows how the system functions and how operates. In this section, we'll give a quick summary of the architecture.
SIEM ArcSight is a maximum-security solution that performs with a wide range of service architectures to obtain optimum operating efficiency. Communication, caching, commitment, recovery, and physical hardware are also included by design. To connect ESM, Logging, and CA, analysts will use the Arcsight interface or a web application.
The logger will get the enhanced occurrences from ESM for long-term event storing. The ESM instances will receive events from across all sophisticated connections. The ArcSight connector appliances or the ESM manager are used to remotely manage all smart connectors.
The logger will then send events of relevance to ESM for real-time comparison. Cross-correlation occurrences will be submitted to the logging for long-term archiving. For load balancing, events from all smart connectors will be transmitted to different recorders. The Arcsight connector appliance is used to manage all smart connectors remotely.
Components of ArcSight
Given below are some of the major components of ArcSight:
Smart connector
- Assists in gathering all essential event logs from network devices.
- Data filtering allows you to conserve space and bandwidth.
- Assists in the parsing of all events and the normalization of the common schema.
- The events are even aggregated to reduce the number of events.
- Sort the events into logical order in order to create rules and filters.
ArcSight manager
- This is a server-side Java component.
- Assesses the events in light of the network model and information vulnerability.
- Assists in the creation of real-time threat summaries.
- Events are written to the CORR event engine.
CORR event engine or Correlation optimized retention and retrieval engine
- In this case, ESM assists in the organization of data and its storage in the corr engine according to the appropriate event retention time.
- Even event correlation occurs in the corr engine, which is archived for long-term usage.
| Related Article : What is ArcSight |
User Interface components of ArcSight
Below given are the User Interface components of ArcSight:
Arcsight command center
- Assists with the management of users, event data, and storage.
- Assists in event monitoring.
- Create reports and keep the license up to date.
Arcsight console
- Create the filters, reports, patterns, discovery, rules, and dashboards in step one.
- Assists in data monitoring.
- Keep track of the users and workflows.
ArcSight web
- This is a web interface manager that assists with event monitoring.
- Used mostly to drill down into dashboards, reports, and security analyst notifications.
ArcSight risk insight
- As a result of specific threats, it helps to assess the business impact and specify the rules.
Pattern discovery
This is used to detect numerous data patterns in any event flow, and the following are some of the uses:
- Identify zero attacks
- Identify low- and slow-speed attacks
- Identify and analyze prevalent networking patterns
- Assists in the automatic application of security regulations.
| Related Article : ArcSight Interview Question and Answers |
SIEM Arcsight Features
Some of the features of the SIEM ArcSight are given below:
Threat blocked
One of the most critical aspects of security management is this. It provides data access to the ArcSight threat framework and aids in the marketing of the latest security solutions, such as rules, reports, use cases, and dashboards.
Source ingestion
The most recent and also essential component of the SIEM ArcSight tool is that it aids in the analysis of information from existing sources, as well as incorporating cyber threat data intelligence via STIX and CIF standards dashboards. In source ingestion, smart connections take care of event format, APIs, logs, flat files, firewall logs, Net flow, XML/JSON, and database connectivity.
High-level Performance
This feature also includes 100,000 EPS (events per second).
Value
Users can convert from legacy license data models to the new or newest release using this functionality, and the ADP of any architecture can report on difficulties to help control conversion difficulty and costs. To accomplish this, Microfocus has made adjustments to its license arrangement, which now includes pricing alternatives that limit free data access.
Implementation
This is also a new function, and users have reported that it is simple to use. ArcSight, according to the Gartner research, is a highly configurable technology that supports threat management and compliance use cases. In many SOC contexts, the ArcSight API allows for broad data integration.
Management
This is ArcSight's most well-known and effective function. This functionality allows various custom rules, other contents, and SIEM dashboards to be exported and shared among customers, devices, and systems with the use of data modular packages. Centralized management, reporting of enterprise security events, and data analysis are also included in this function.
Supporting
Users will get good data management and security help here, but it will come at a price.
Scalability
This is a significant aspect as well; you can scale up to 100,000 EPS while using distributed correlation.
Advantages of SIEM Arcsight
SIEM ArcSight has lots of benefits, some of the benefits are listed below:
Improves the customer experience
With each new product and service, customers' expectations shift. They want your company to give them the same digital experience as other businesses.
Digital transformation services
Digital technology is transforming businesses, products, and services, and it is a wellspring of new ideas. Enterprises are confronted with the task of undertaking a digital transformation, which will mostly result in internal changes. External partners are looking for ways to provide the best possible customer experience to end-users.
SIEM ArcSight offers flexible deployment and fully transparent
- High availability and rapid deployments.
- Clustering and virtualization (appliance or virtual).
- Agents, spanning, and bridge modes are all available.
- Governance and security.
Explore ArcSight Logger Administration and Operations Sample Resumes! Download & Edit, Get Noticed by Top Employers!
Conclusion
The blog has come to an end. We hope that this ArcSight SIEM blog has given you a better understanding of the SIEM ArcSight cybersecurity features, architecture, and benefits. SIEM ArcSight's major goal is to provide security for data connections, devices, and systems. SIEM ArcSight's powerful automation technologies aid in the integration of end-user business applications and give customers digital transparency. With SIEM ArcSight, you can protect your company's data from attacks and computer viruses, as well as confidential information.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| ArcSight Training | Feb 28 to Mar 15 | View Details |
| ArcSight Training | Mar 03 to Mar 18 | View Details |
| ArcSight Training | Mar 07 to Mar 22 | View Details |
| ArcSight Training | Mar 10 to Mar 25 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .
















