- Home
- Blog
- Cloud Computing
- Cloud Security Architecture

What is Cloud Security Architecture?
Why is Cloud Security Architecture essential?
Core Capabilities of Cloud Security Architecture
What are the threats to Cloud Security?
How to develop a competent Cloud Security Architecture?
What is the Cloud Security Architecture Shared Responsibility Model?
Companies are increasingly moving to cloud services for computing, data storage, etc. But at the same time, the companies face stability, reliability, and security problems in the cloud environment because of threats and vulnerabilities. These threats have the potential to cause severe financial and reputation damage to businesses, undoubtedly. So, there is no surprise that the security of cloud resources has become one of the high-priority aspects for companies.
Now, the question is, how can we mitigate threats and protect cloud resources?
The answer is simple! We can establish a cloud security architecture to protect resources from threats intelligently. An efficient cloud architecture includes many crucial components, such as creating security policies, rules, and procedures. It also includes implementing the security procedures and methods, tracking the methods, and logging the results for performance analysis. Ultimately, the cloud security architecture tightens the security of cloud resources with no gap. In the end, it builds confidence among users and businesses.
Okay! Now it’s time to dig into the cloud security architecture. In this blog, you will find comprehensive details about cloud security architecture, its capabilities, developing a cloud security architecture, its advantages, and much more.
What is Cloud Security Architecture?
Essentially, the cloud security architecture is the security strategy that aims at protecting applications, data, and systems in a cloud environment. In other words, the cloud security architecture is a model that defines various crucial components in the cloud environment and monitors them closely to secure its resources.
The components include the security layers, identity management, infrastructure, access control, best practices, protection mechanisms, policies for security compliance, threat management, security compliance standards, etc.
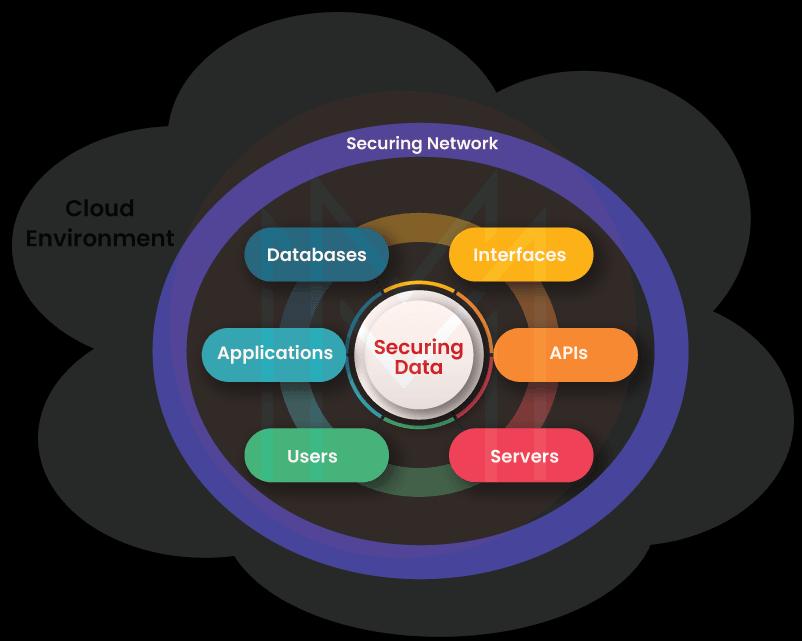
The significant thing about cloud security architecture is that it works based on shared responsibility. It is nothing but the responsibility shared between customers and cloud providers.
| Do you want to get certified and build your career in Cloud Security? Then enroll in "Online Cloud Security Certification" this course will help you to achieve excellence in this domain. |
Why is Cloud Security Architecture essential?
Cloud Security Architecture streamlines the policies and mechanisms to ensure the security of resources in a cloud environment.
- It eliminates security holes in cloud environments. Consequently, it prevents risks and vulnerabilities significantly.
- It reduces redundancy in the various security measures you plan to protect your cloud resources. It results in improved agility and efficiency and reduces costs as well.
- It speeds up service delivery. Thus, it boosts trust and reputation among stakeholders.
- On top of all, it ensures consistency and sustainability in securing cloud resources.
Core Capabilities of Cloud Security Architecture
Any cloud security architecture is built on three excellent core capabilities.
Let’s have a closer look at the capabilities as follows
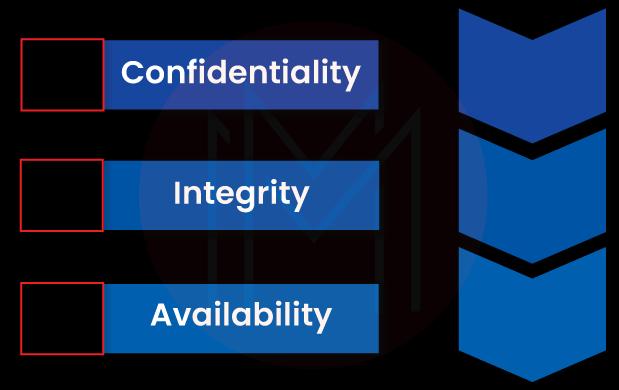
1. Confidentiality
This is one of the capabilities of the cloud security architecture, which focuses on trust and privacy. Essentially, confidentiality is the ability of security policies and methods to protect cloud data and applications. This architecture ensures that no one can access cloud resources without permission.
2. Integrity
It ensures applications and other resources in the cloud environment are working as per users’ expectations – from the security point of view.
3. Availability
This is yet another capability of the cloud security architecture that ensures the availability of data and other resources in the cloud environment to access by users at any time. For example, a cloud environment must be free from DoS attacks anytime. If not, you cannot run your business normally.
What are the Threats to Cloud Security?
No doubt there would be loopholes in the cloud environment's security if you don't design the cloud security perfectly. It will result in security failures and other severe damage. So, it is essential to create robust cloud security that easily overcomes high-profile threats.
Let’s look at the listicles of the few threats to cloud security.
1. Inefficient Security Strategies
When it comes to cloud security, you cannot employ the same security models and strategies you use to secure data centers and on-premises resources. But, you must embrace integrated security systems in clouds to overcome the security breaches that may occur due to advanced and automated attacks.
2. Misconfigurations
Misconfigurations in cloud security will lead to security breaches. It usually occurs because of human errors. Lapses in the security perimeter also induce errors in cloud security.
3. Inconsistency in Security
This problem occurs because of poor visibility across the cloud environment. Not only that, lack of centralized controls and policies may cause inconsistency in the security of cloud resources.
4. Insider Threats
These threats occur because of the people who access data internally. It means the people who work in the organization have more chances to access and misuse data easily. Similarly, cloud service provider administrators can misuse the data and other resources.
5. DoS Attacks
DoS stands for Denial-of-Service. When a low-scale DoS attack is made against systems and data, users cannot access the services until the attack is resolved. If it is a high-scale attack, no surprise restoration of systems will take days and weeks.
6. Shadow IT
This is yet another severe threat when people manage cloud resources without understanding them completely. For example, developers may connect workloads with their personal accounts. It will definitely open doors to access the cloud resources without authorization.
Apart from all the mentioned threats, there are a few other threats to cloud security, such as malware injection, credential stuffing threats, advanced persistent threats, zero-day attacks, insecure APIs, phishing, and many more.
How to develop a Competent Cloud Security Architecture?
A neatly designed cloud security architecture will protect the cloud environment in the best way, undeniably.
You can build a competent cloud security architecture by using the following procedure.
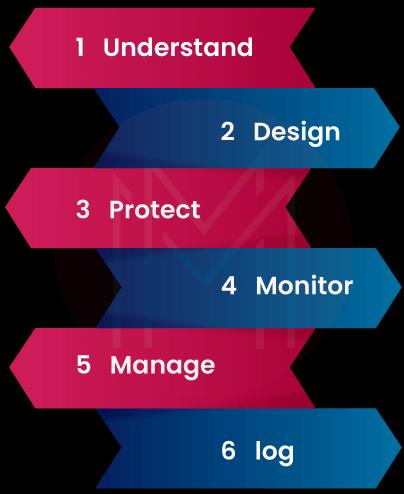
-
Understand
Before designing the cloud security architecture, you must understand the users, resources to secure, threats, vulnerabilities, business environment, and other associated elements. Mainly, you need to assess the current and potential risks. Also, you need to define the security requirements and the associated security measures and controls.
-
Design
Next, you can create a roadmap to implement the security measures to build a powerful cloud security architecture. You must define security policies and methods to manage data, users, and other cloud resources. In addition, you need to define roles and responsibilities, automation features, security configurations, etc. The design must also include security measures to meet the industry security standards and compliances.
Further, you need to perfectly define the boundaries of network traffic in and out of cloud resources without eliminating the interfaces that connect resources with external systems.
-
Protect
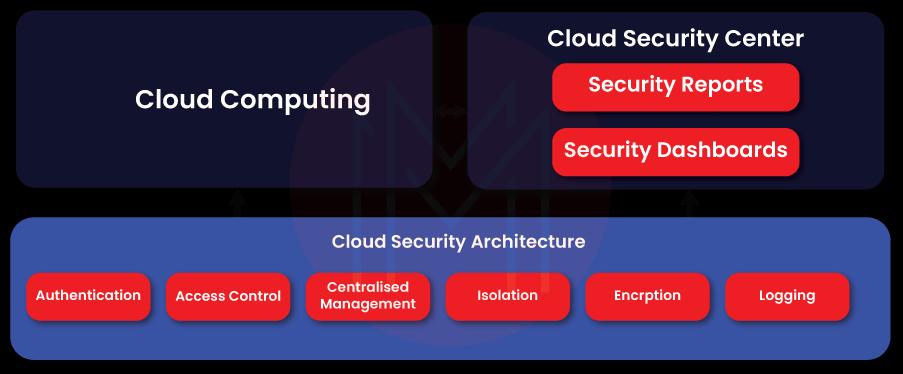
The essential thing is that when building a cloud security architecture, you need to leverage sound control mechanisms to protect applications, data, endpoints, etc. So, you need to effectively set the protection methods such as authentication, isolation, access control, permissions, and encryption to improve cloud security.
Let’s find them briefly as follows
-
Identity Management and Access Control
Know that the security of resources hugely depends on identification and authorization mechanisms. You can identify and authorize users by setting strong identifiers or passwords.
Strong keywords and two-factor authentication will help to improve the security of applications. For example, we can use a temporary one-time password for authentication. It is the password that we can use only once to access cloud resources. Similarly, we can use digital certificates to allow users to access cloud assets, which is one of the safest methods than passwords. Besides, we can use token services to ensure the security of resources.
-
Isolation
You can divide the cloud architecture into different sections, which will increase the security of resources in a significant way. For example, you can isolate operating systems, containers, virtual machines, applications, networks, and data. This logical separation of resources will reduce the impact if any attack is made on the cloud resources.
-
Encryption
You must encrypt all the data in the cloud – it doesn’t matter whether the data is idle or moved to other resources. In the encryption method, data is encrypted at first, converted into ciphers, and then decrypted. Only authorized persons can decrypt and access the data.
-
Monitor
You need to monitor the security measures closely and track their performance of them. As a result, you can detect the risks and vulnerabilities in the cloud environment. It allows you to investigate the root cause of threats and identify the effectiveness of preventive measures applied in the cloud security architecture.
-
Manage
Based on the performance reports of security measures, if needed, you can make changes in the security systems for enhanced performance of the cloud security architecture. No wonder you can automate the convenient features of the security measures.
-
Log
Finally, you need to ensure that all the security activities in the cloud environment are logged without leaving anything. This is because you can use the logged files to investigate and analyze the security measures in the cloud security architecture.
What is the Cloud Security Architecture Shared Responsibility Model?
This shared responsibility model includes cloud service providers, customers, and network service providers.
Know that resources in a cloud environment can be divided into two layers. The top layer is responsible for cloud customers. And the bottom layer is responsible for cloud providers.
It is essential to note that each resource in the cloud environment will be mapped to any one of these two layers. The contract between cloud service providers and customers will usually define the boundaries, responsibilities, and other associated things.
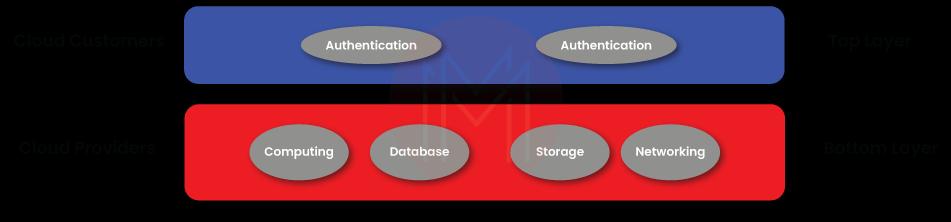
The cloud service provider will usually be responsible for securing resources such as computing, database, storage, hardware, networking, etc. Undeniably, these components are vital to run cloud services. At the same time, the customer is responsible for identity and access management.
Although service providers and customers are clearly defined with their responsibilities, sometimes they may overlap based on the type of cloud platforms such as PaaS, IaaS, and SaaS.
Let’s take a look at them briefly.
1. PaaS
PaaS refers to Platform-as-a-Service. This type supports software developing, running, and maintaining applications. Multiple parties may use this platform, so monitoring data moving in and out of the platform is essential.
When it comes to PaaS, the customer is entirely responsible for securing application deployment, permissions, and configuration. Note that AWS is one of the PaaS types of the cloud platform.
2. IaaS
IaaS refers to Infrastructure-as-a-Service. This platform offers the necessary infrastructure to develop and run applications. It also includes orchestration activities in the cloud environment.
When it comes to IaaS, customers are responsible for the entire infrastructure. This is because customers install their applications, operating systems, and middleware in the infrastructure. Note that Microsoft Azure is one of the IaaS types of cloud platform.
3. SaaS
SaaS refers to Software-as-a-Service. This platform needs monitoring from both cloud service providers and customers to secure the cloud resources.
When it comes to SaaS, the customer is responsible for identity and access management, network security, etc. At the same time, the cloud provider is responsible for the back-end security. Note that Salesforce and Office 365 are a few examples of SaaS.
| Related Article: What is Cloud Security |
Best Practices in the Cloud Security Architecture
Importantly, leveraging effective practices supports building a trusted cloud security architecture. The best practices will enhance the security of cloud resources to high levels.
-
Firmware Resilience
It is the capability of the architecture to prevent attacks on the firmware itself and restore resources back to normal.
-
Stack Validation
If you validate all the resource components in the system stack, no doubt it will enhance the security of clouds significantly.
-
Managing APIs
If you use APIs in the cloud environment to connect workflows to external systems or other clouds, you need to validate these resources frequently to ensure security. Moreover, you can use APIs such as SOAP or REST to automate firewall policies, access control, and configuration.
| To get answers to your Cloud Security Questions, Read here "Cloud Security Interview Questions" |
Advantages of Cloud Security Architecture
There are many merits in leveraging cloud security architecture to protect cloud resources.
Let’s list them in the following one by one
- A well-designed cloud security architecture will empower you by identifying risks and preventing them entirely before they cause any severe damage to the cloud systems.
- You can get high visibility across all the users who access the cloud resources and their activities in the cloud. It will help to ensure the security of the cloud resources.
- Cloud security architecture ensures the availability of cloud resources to users at any time.
- You can easily fulfill regulatory compliances and industry security standards.
- You can entirely prevent severe attacks such as DDoS by creating a robust cloud security architecture.
Conclusion
Long story short – cloud security architecture helps to secure your cloud resources by creating security policies, adapting suitable security mechanisms, etc. Once an efficient cloud security architecture is established in the cloud, the security of resources will no longer be an issue. It’s worth noting that you can implement cloud security architecture in any platform, whether it is SaaS, PaaS, or IaaS. Overall, you can secure the systems and boost the productivity of businesses remarkably.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Cloud Security Training | Feb 21 to Mar 08 | View Details |
| Cloud Security Training | Feb 24 to Mar 11 | View Details |
| Cloud Security Training | Feb 28 to Mar 15 | View Details |
| Cloud Security Training | Mar 03 to Mar 18 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .















