In this ever-evolving digital age, organizations face many challenges in protecting applications and data against misuse and exploitation. Unauthorized access to digital resources is one of the most critical challenges.
To overcome this, they leverage robust strategies and tools to manage and protect user identities and ensure identity security.
SailPoint is one of the Identity Governance and Administration (IGA) platforms that organizations adopt to protect their identities.
In this quick guide, we will explore SailPoint's features, capabilities, and opportunities in detail.
Table of Contents
- Overview of Identity and Governance Administration (IGA)
- Product Suite Overview
- IdentityNow Architecture Overview
- Workflow
- Features and Use Cases
- Market Demand and Career Scope
- Learning Path for SailPoint
- Certification Roadmap
- Hands-On Practice Ideas
- Interview Preparation
- Resources for Learning SailPoint
- Common Mistakes that You Must Avoid
- Frequently Asked Questions
Overview of Identity and Governance Administration (IGA)
To start with, let’s understand the fundamentals of IGA, its key features, and market position, etc.
-
What is IGA?
IGA is a discipline that provides policies, processes, and controls to implement identity security solutions in enterprises.
IGA guides IT security teams to control user identities and users’ rights to access digital resources. They protect their organization’s digital assets from unauthorized access, meeting compliance requirements.
-
Why IGA?
Let’s take a look at why IGA is crucial for organizations today.
-
- Reduce operational costs: IGA automates mundane processes such as access certifications, password management, and access requests, thereby reducing operational costs.
- Reduces risks: IGA provides security teams with enhanced visibility across all the digital assets of an organization. It helps detect inappropriate access, policy violations, and weak controls, thus reducing risks.
- Automated lifecycle management: IGA automates the identity lifecycle end-to-end. It helps security teams to streamline access management and enforce security policies.
- Increase business agility: Although users’ roles and responsibilities change dynamically, IGA ensures timely access so users can continue their tasks without delays. It helps improve business agility and productivity.
- Improve compliance: IGA helps organizations ensure that their security policies and controls comply with regulatory standards of HIPAA, SOX, GDPR, etc.
-
Growth of the IGA Market & SailPoint
IGA is a promising solution for managing access across cloud and on-premises environments. Let’s look at the market growth and SailPoint’s position.
-
-
Gartner Peer Insights named SailPoint the customer’s choice for identity governance and administration for 2024.
-
According to Research and Markets, the IGA market is forecasted to grow by 5 billion USD during 2024-29 with a CAGR of 14.5%.
-
-
Who can benefit from this SailPoint guide?
- IAM Engineers
- IT Security Engineers
- IT Administrators
- IT Compliance teams
- Aspiring security professionals
-
Key Components of the IGA

-
-
Access Certification
-
Access certification is a part of the IGA auditing process. Managers and data owners periodically review and ensure that users access the right resources.
It helps IGA professionals to trigger alerts, generate audit reports, and approve or remove access and exceptions.
It helps organizations ensure that they comply with SOX and GDPR.
-
-
Access Requests
-
IGA solutions automate access requests through a self-service portal. You can create workflows to simplify the approval process for managers and data owners.
IGA solutions can automate provisioning across connected systems. It helps enhance security and perform auditing processes consistently.
-
-
Access Review
-
IGA solutions can streamline access review processes and verify user access to multiple apps and resources. They also simplify access removal when an employee leaves the organization.
-
-
Policy Enforcement
-
IGA solutions enable security teams to create policies and rules to control risky access and transaction rights. It helps organizations prevent fraud and avoid errors.
For example, Segregation of Duties (SoD) controls prevent fraud and errors significantly.
-
-
Password Management
-
IGA solutions allow users to reset passwords from anywhere and at any time. It ensures seamless business processes for organizations.
In addition, you can make strong and consistent passwords using password policies. These policies comprise the instructions, such as minimum password length, inappropriate patterns, use of special characters, and more.
In summary, IGA streamlines IGA implementation, improves operational efficiency, reduces costs, and enables secure and consistent identity security solutions.
| Do you want to get certified and build your career in SailPoint? Then enroll in "Online SailPoint Certification Training" this course will help you to achieve excellence in this domain. |
SailPoint Product Suite Overview
SailPoint is an AI-based identity security platform that simplifies access control with its self-service capabilities.
-
- SailPoint helps control access to applications and data, improving security.
- It automates manual tasks, improving productivity and security.
- You can use SailPoint to set up roles and ensure compliance.
- You can generate robust reports and analytics, which help to reduce data breaches and security risks.
- It helps businesses make data-driven decisions and maximize efficiency using AI agents.
SailPoint product suite consists of two key products, as follows:
-
-
- IdentityIQ
- IdentityNow
-
Let’s learn them in-depth in the following.
A. IdentityIQ
SailPoint IdentityIQ is an on-premises Identity and Access Management (IAM) solution that offers effective identity governance solutions.
- SailPoint IdentityIQ provides users with enhanced visibility. It enables them to make accurate decisions on access control using its AI capabilities.
- It offers robust security controls to protect complex applications and systems.
Why SailPoint IdentityIQ
Here are the reasons why IdentityIQ is crucial in IAM.
- SailPoint IdentityIQ automates mundane IT tasks and implements compliance policies. It increases operational efficiency.
- It controls users' internal and external access, reducing security threats and risks.
- Its preconfigured workflows and wizard setups speed up the onboarding processes, from weeks to hours.
- You can manage thousands of applications, data sources, identities, and access points using SailPoint IdentityIQ.
- It builds and updates access models more quickly.
- You can analyze access patterns, trace risky accesses, and generate actionable insights with its AI capabilities. It helps you perform approvals and removals based on recommendations.
Modules of SailPoint IdentityIQ
Let’s walk through the key modules of SailPoint IdentityIQ.
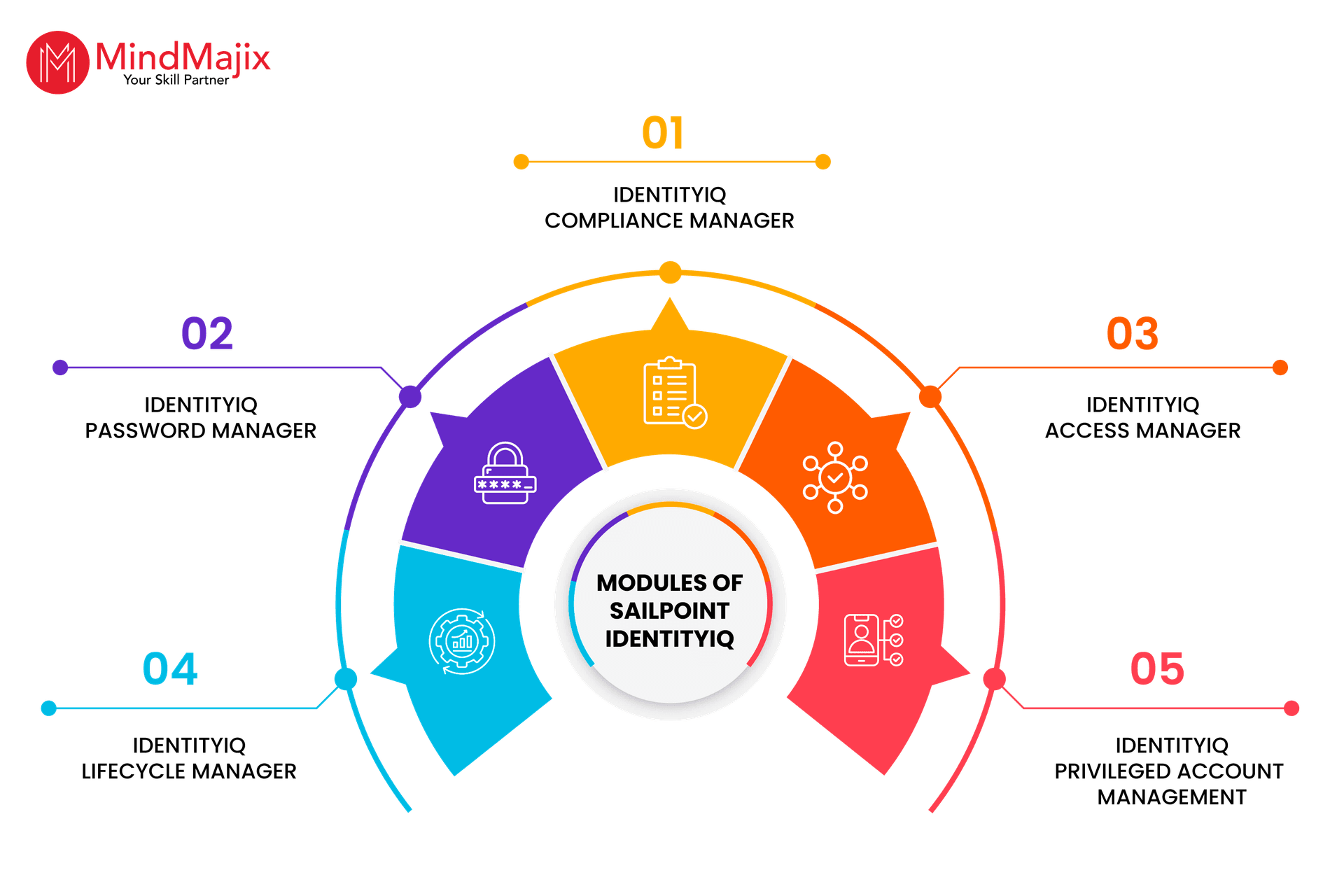
- IdentityIQ Compliance Manager: This module plays a key role in streamlining compliance processes. It reviews user access, prevents inappropriate access, and simplifies auditing processes.
- IdentityIQ Password Manager: This module helps reset passwords without the need for IT teams. It also supports creating strong passwords based on password policies for robust security controls.
- IdentityIQ File Access Manager: IdentityIQ identifies sensitive and risky data stored on-premises resources. Based on the severity, it enables the required security controls to protect data from vulnerabilities.
- IdentityIQ Lifecycle Manager: It is an IdentityIQ self-service platform that allows users to easily make requests and approvals. This module tracks changes in users’ access activities based on roles and makes adjustments automatically.
- IdentityIQ Privileged Account Management: This module implements a standardized approach to handling high-privileged accounts.
SailPoint IdentityIQ Services
Here, we will go through the IdentityIQ services in detail.
- Dashboards: IdentityIQ dashboards provide a consolidated view of access management. It allows you to manage your passwords and approvals, track access requests, review and manage accesses, and perform other related tasks.
- Risk scoring: This feature detects the risky users and accounts. You can determine risk scores for every identity and application.
- Reporting: You can generate reports that simplify internal and external auditing processes. You can create reports of violations in policies, access reviews, user access information, and more.
- Recommendations: IdentityIQ identifies anomalies in user access activities, which helps prevent issues proactively.
- Connector configuration: You can configure the SailPoint connector to provide seamless governing and provisioning access to applications.
- Login configuration: IdentityIQ supports two types of SSO configuration, such as SAML and rule-based.
- Integration with Active Directory: You can use the SailPoint AD connector to integrate SailPoint with the AD infrastructure. It enables managing AD resources across multiple domains effectively.
Now, you must be clear that SailPoint IdentityIQ is a well-known on-premises identity governance platform.
B. Sailpoint IdentityNow
It is another SailPoint product that plays a vital role in SaaS identity security.
-
What is SailPoint IdentityNow?
SailPoint IdentityNow is a cloud-based identity governance solution. It is built with a multi-tenant microservices SaaS architecture. It controls identity access to IT resources located in the cloud.
-
- SailPoint IdentityNow is a self-service platform that automates the creation of access requests and approvals.
- It ensures users can only access the resources required for their roles and tasks.
- It provides guidelines to configure access requests for entitlements.
- Why SailPoint IdentityNow
- You can deploy the SailPoint IdentityNow solution quickly without much technical expertise.
- IdentityNow updates new releases automatically. It allows users to access the updated software at any time.
- It tracks identity access activities continually. It helps identify and rectify threats before they cause any severe damage.
-
Capabilities of SailPoint IdentityNow
Let’s take a look at the capabilities of SailPointNow.

-
Access Reviews and Certification
IdentityNow reviews user access activities and permissions regularly. It helps swiftly control overexposure to permissions.
-
- You can create a request to remove access to resources. Access to resources can be removed when users change their role.
- SailPoint IdentityNow simplifies access to resources by creating segments in which users can access a group of resources based on their roles.
- The users in a specific segment cannot access the resources of other segments.
- You can generate SailPoint certifications based on the review results
-
Policy Enforcement
IdentityNow creates effective policies for security and compliance to manage high-risk and sensitive tasks.
-
- IdentityNow ensures that the right users access the right files based on their roles and requirements.
- SailPoint provides the step-by-step guidelines to create policies, manage passwords, and perform other tasks.
-
Entitlements Management
Entitlements are a key aspect of identity governance. They represent a user's access rights on a source.
You can configure entitlements for the following.
-
- Direct access requests
- Grouping related entitlements in access profiles
- Reviewing and managing certifications
-
File Access Manager
IdentityNow classifies files based on their sensitivity and risk level and monitors how users access them. Additionally, it triggers alerts on inappropriate access and overexposed resources.
-
AI Services
- Access Insights: IdentityNow helps you track and visualize data over time with Data Explore, which is SailPoint’s access insights service. This feature helps monitor the governance-focused metrics across your organization. Moreover, it generates deep insights and valuable information.
- Access Modeling: SailPoint's access modeling service tracks user activity patterns and creates potential roles. It helps you customize new roles, create new roles from potential roles, refine entitlements, and more.
- Recommendation Engine: The recommendation engine enables users and certifiers with relevant recommendations. It helps them make approvals.
The recommendations are generated based on peer group analysis, dense clustering, and other advanced techniques.
In summary, SailPoint IdentityNow is a robust cloud-based management solution. Organizations use the platform for effective IAM implementation.
Differences between IdentityNow and IdentityIQ (Cloud vs. on-premises)
Let’s explore the differences between IdentityNow and IdentityIQ.
|
Comparison factors |
IdentityNow |
IdentityIQ |
|
Platform |
It is a SaaS-based IAM solution |
It is an on-premises IAM solution |
|
Components |
|
|
|
Implementation |
Starting and scaling IdentityNow takes less time as it is a SaaS solution. |
Deployment and configuration consume a lot of time, as it is an on-premises solution. |
|
Upgrades |
Upgrades and maintenance must be performed manually. |
Everything is performed automatically. |
SailPoint IdentityNow Architecture Overview
SailPoint IdentityNow is built on a microservices and multi-tenant Cloud SaaS architecture. It helps to implement IGA on applications and systems effectively.
The diagram below depicts the architecture of SailPoint IdentityNow.

- Key features of the SailPoint IdentityNow architecture
- This architecture doesn’t require additional software or hardware for installation and maintenance.
- It provides robust security for your data, systems, and applications.
- It helps enhance the operational efficiency of the systems.
- It enables users to manage access, passwords, provisioning and deprovisioning, and policies effectively.
- It allows users to access resources based on the size and number of identities.
- Most importantly, this architecture ensures zero downtime for software upgrades.
| Related Article: Sailpoint Interview Questions |
SailPoint IdentityNow Workflow
SailPoint IdentityNow Workflow has many parts, such as metadata, actions, triggers, and operators. It provides the required flexibility for users to build workflows for specific actions.
Most importantly, SailPoint allows you to create workflows without code. The image below shows an example of a SailPoint workflow.

- Why SailPoint Workflow
Let’s see the importance of SailPoint workflow in the following.
-
- SailPoint workflow automates repetitive processes in IT resource management, simplifying identity security implementation. For example, it automates event-driven certification and approvals, thus accelerating the identity security implementation.
- Workflows help ensure identity compliance and security in organizations
- They connect entire business processes to ensure identity security. For example, it generates tickets for investigation when there is an aggregation issue.
- You can connect workflows with other SaaS applications within a cloud environment.
- You can integrate workflows with an external cloud environment and SailPoint’s partner network.
- It deactivates all accounts of employees who leave the organization
-
Workflow Parts
Let’s clearly understand the SailPoint workflow parts here.
-
- Triggers: A SailPoint workflow gets initiated by a trigger and runs according to a specific event. The trigger itself provides inputs to the workflow. The inputs change continuously as they pass through the workflow steps.
- Operators: Operators help configure choices and conditional logic. They allow making comparisons between values. So, a new path is chosen in the workflow based on comparison results.
- Actions: It is a task that is performed outside of a workflow. Actions usually have many fields, such as action name, select input, description, and select result. They receive inputs in JSON format from the previous step.
- Data flow: It refers to the directional movement of data.
- Inputs: A workflow receives inputs in JSON format. This JSON data moves through each step in the workflow.
- Results: Once a step in a workflow processes JSON data, it generates a result that is given as the input to the next step.
- Outputs: It is the final result of a workflow. You will receive outputs only after all the workflow steps have processed the data.
We hope that you have gained a deep knowledge of the SailPoint workflow, its parts and uses extensively.
SailPoint Features and Use Cases
In this part of the SailPoint tutorial, we will go over the features and applications of SailPoint.
- Automated User Provisioning
SailPoint simplifies user onboarding and off-boarding processes. It helps create and delete identities based on new user roles and activities.
-
- SailPoint allows you to configure user provisioning and deprovisioning, manage roles, set up lifecycle states, and configure attribute synchronization.
- It will enable updating source provisioning policies, including mapping attributes and re-ordering attributes.
- Role-based Access Control (RBAC)
SailPoint IdentityIQ implements RBAC using the following features.
-
- Role editing and modeling
- Role mining
- Entitlement analysis
- Certifications for role membership and composition
- Workflows for managing changes
- Campaigns
Campaigns or access certification in SailPoint enable you to certify permissions and identities.
When you start a certification campaign, source owners examine the identities of the resources that they manage. They certify that users have access only to permitted sources. If there is any lapse, you can unauthorize the access to the resources.
Moreover, you can review certification campaigns using the reports below
-
- Campaign composition
- Campaign exclusion
- Campaign status
- Campaign remediation status
- Certification sign-off
- SoD policy
SailPoint’s Separation of Duties (SoD) policy separates duties for different individuals to avoid security compromises. SoD policies enable you to prevent policy violations before they happen.
SailPoint generates violation reports using the following information.
-
- SoD business name
- Description
- Policy owner display name
- Policy owner IDN unique ID
- AI-driven identity recommendations
Let’s learn how AI-driven recommendations help you in IAM.
-
- Help make reliable access control and informed decisions
- Provide recommendations to automate low-risk access requests, thereby allowing teams to focus on higher-risk access requests
- Identify outliers in user access and make informed decisions
- Maintain accurate compliance requirements
In summary, SailPoint automates user provisioning, enabling RBAC, performing campaigns, and enforcing security policies effectively.
| Related Article: SailPoint vs CyberArk |
SailPoint Market Demand and Career Scope
-
Industries adopting SailPoint
According to TheirStack, many industries use SailPoint for their identity governance solutions, including:
-
- IT Services and Consulting
- Financial services
- Healthcare
- Software development
- Government sectors
- Companies use SailPoint: SailPoint reports that top companies such as Wipro, GXS, Philips, AES, Vodafone, Upwork, and Swedbank use SailPoint for their IAM solutions.
- In-demand SailPoint roles: SailPoint professionals can secure multiple job roles in diverse industries. Here are some of them:
- SailPoint Developer/Architect/Engineer
- SailPoint IAM Consultant/Specialist/Engineer
- Identity Security Administrator/Engineer
- SailPoint Identity Security Cloud Developer/Engineer/Specialist
- SailPoint IAM Engineer/Administrator
- SailPoint IIQ Developer
- SailPoint Access Governance Consultant
- Global Salary Range for SailPoint professionals
|
Job Role |
Country |
Salary | |
|
SailPoint Developers |
USA |
$87,000 to $100,000 per year (Glassdoor) | |
|
India |
3 LPA to 16 LPA (AmbitionBox) | ||
|
SailPoint Engineers |
USA |
$38,000 to $192,000 per year (ZipRecruiter) | |
|
India |
5 LPA to 10 LPA (Glassdoor) | ||
Overall, career opportunities in the SailPoint platform are plentiful across multiple industries worldwide.
Learning Path for SailPoint
Here, we discuss the learning paths for beginners, intermediate and advanced learners to gain in-demand skills and become skilled SailPoint professionals.
- Beginner
- Learning IAM and IGA fundamentals
- Exploring IdentityIQ/IdentityNow User interface
- Understanding connectors and integrations
- Understanding RBAC, access requests and certification
- Intermediate
- Develop and configure lifecycle events and workflows
- Troubleshoot and resolve IT security issues
- Creating roles, groups, policies, and user accounts
- Integrate SailPoint with internal and external applications
- Advanced
- Developing custom rules and scripts in BeanShell
- Implementing provisioning and advanced SoD policy
- Managing deployments and managing repositories
- Integrating with Multifactor Authentication (MFA), SIEM, and other security tools
The learning paths guide you to become a qualified identity security SailPoint professional.
SailPoint Certification Roadmap
Next, we will explore the SailPoint certification roadmap that will help you achieve certification and secure a suitable role in the security identity arena.
Let’s introduce you to the SailPoint certification roadmap, which will help accelerate your learning journey.

- Official Certifications
SailPoint offers the following certifications. You can take your career to the next level by completing the SailPoint certifications.
-
- Identity Security Engineer Certification
- IdentityIQ Engineer Certification
- IdentityIQ Associate Certification
- Identity security leader credential
- Identity security professional credential
- How to choose the right certification
As SailPoint offers multiple certifications, it is crucial to select the right certification based on your role or individual needs.
If you are a beginner, you can complete the following certifications and pass the exams to gain new skills. You can apply the skills in projects or showcase your abilities in IAM interviews.
-
- Identity security leader credential
- Identity security professional credential
If you are already in the IAM field and aim to enhance your expertise based on your roles, you can complete the certifications and exams.
-
- Identity Security Engineer Certification
- IdentityIQ Engineer Certification
- IdentityIQ Associate Certification
- Exam Details
|
Certification |
Format |
Duration |
Cost |
Topics Covered |
|
SailPoint Identity Security Leader Credential
|
30 Qns |
45 minutes
|
Free |
|
|
SailPoint Identity Security Professional Credential
|
51 Qns |
90 minutes |
Free |
|
|
SailPoint Certified Identity Security Engineer
|
|
|
400 USD |
|
|
SailPoint Certified IdentityIQ Associate |
|
|
300 USD |
|
|
SailPoint Certified IdentityIQ Engineer |
|
|
400 USD |
|
- Certification and Exam Preparation Tips
The following training path will help you become a top-notch SailPoint professional and gain industry recognition.
-
- Build a foundation: First, build a foundation on identity security by completing the identity security leader certification. It will provide you with essential identity security concepts and best practices in SailPoint implementation.
- Expand your skillset: Next, improve your knowledge of technical components, frameworks, and identity data management, completing the identity security professional credential.
- Prove your expertise: lastly, complete the SailPoint role-based professional certifications based on your individual needs. Gain the certification to validate your SailPoint knowledge and skills.
We hope that this SailPoint certification guide provides you with the required information to identify your right certification path and move forward in your career.
Hands-On Practice Ideas
Below are some of the hands-on practices that will help you gain expertise in the SailPoint platform.
- Setting up a SailPoint sandbox environment: In this project, you will learn to set up a sandbox environment using sample data. It helps you to test rules without risking live data.
- Running a certification campaign: This project provides you with hands-on skills in creating campaigns, using campaign filters, and running and completing campaigns.
- Onboarding a sample application: In this practice, you will learn to integrate SailPoint with Active Directory. You will use the SailPoint AD connector to manage AD infrastructure across multiple domains.
- Creating SoD rules and testing violations: In this project, you will learn to create SoD policies to identify and manage conflicting access. You will learn to generate policy violation reports to gather the necessary data to manage violations.
SailPoint Interview Preparation
Here, we will guide you through to crack your SailPoint interviews.
- Top 20 SailPoint interview questions
Let’s start with some crucial SailPoint interview questions.
-
- Define IAM
- What are SailPoint IdentityNow and IdentityIQ?
- What are the key capabilities of SailPoint?
- What is the SailPoint IdentityIQ lifecycle manager?
- What is account mapping
- What is an identity warehouse?
- What is a role modeler
- What are the different certification types available in SailPoint?
- What are the different types of provision types in SailPoint?
- What is partitioning in SailPoint?
- What is the delegation rule in SailPoint?
- List some examples of the SailPoint identity cube.
- What are the extended attributes of SailPoint?
- Brief the auditing and reporting capabilities of SailPoint IdentityIQ.
- Explain the process of role mining in SailPoint IdentityIQ
- How does SailPoint IdentityIQ facilitate regulatory compliance?
- Explain SailPointIQ’s disaster recovery capabilities.
- What is the difference between roles and entitlements in SailPoint?
- What is risk scoring in SailPoint IdentityIQ?
- How does SailPoint IdentityIQ handle complex policy violations and remediation?
- What is the role of identity analytics in SailPoint IdentityIQ?
- Scenario-based questions
-
- How would you create direct links to IdentityIQ?
- How would you handle orphan accounts?
- How to approve role changes?
- How will you create a service account using the simple mapping method?
- How will you add or edit role types?
- How does IdentityIQ integrate with other systems?
- How to make a custom logging setup for IdentityIQ rules
- How will you configure the source for password management?
- SailPoint provisioning engine keeps ignoring attribute changes. How will you rectify this issue?
- How will you trigger a password reset at the desktop login in SailPoint?
- How to present SailPoint projects on your resume
It is crucial to include your SailPoint project details in your resume to demonstrate your technical expertise to interviewers.
Here, we provide some tips on how to present projects on your resume.
-
- Describe your projects in the professional experience section
- Explain your role and contribution in the project briefly
- Add the list of tools and platforms that you used in the projects
- Mention the duration of the project
Resources for Learning SailPoint
We have compiled some useful SailPoint learning resources in this part of the guide. They will help you strengthen your understanding of SailPoint better than ever before.
- SailPoint Key official links
- SailPoint Documentation - https://documentation.sailpoint.com/
- Community Forums - https://community.sailpoint.com/
- GitHub projects for connectors and rules
- Connectors
- Rule Development
- YouTube Tutorials
- https://www.youtube.com/watch?v=dTbjRVsiHYk
- https://www.youtube.com/watch?v=dwEWFGi7C-0
- https://www.youtube.com/watch?v=sNnFyLMWgyw
- https://www.youtube.com/watch?v=CHVstm7ZT5U&list=PL4S_vg5GUvWGBaD4jHrgprJZC1X4daBQ3&index=3
- https://www.youtube.com/watch?v=9EF2l_p_zQI&list=PL4S_vg5GUvWGBaD4jHrgprJZC1X4daBQ3&index=8
The Importance of Professional or Paid Training
Although you can utilize the online resources to gain knowledge and skills in SailPoint, undergoing professional training makes a world of difference.
A professional SailPoint training will enhance your knowledge and skills to the next level with guided hands-on practices.
In this way, MindMajix offers expert-led SailPoint training for both beginners and advanced learners. Our experts have designed the SailPoint course curriculum with learning modules from foundational concepts to advanced.
We cover hands-on labs, real-time projects, and industry use cases in identity management in the training to enhance the practical expertise of learners.
Let’s see the key features of the training.
- Get the opportunity to interact with our experienced trainers and have your questions answered on the spot.
- Get one-on-one guidance in labs and real-time projects
- Use our resume samples to strengthen your portfolio
- Learn the SailPoint interview questions that we offer
- Explore interview preparation and job search assistance
Common Mistakes that You Must Avoid
Here, we list the common mistakes that SailPoint professionals make while working on SailPoint projects.
- Before updating to the new SailPoint features, you must test them. If not, it will cause broken connectors, failed jobs, and user sync issues.
- You shouldn’t accept new policies as they are. You must examine them before accepting them.
- Creating custom rules with improper logic leads to failures. To avoid it, you must test custom rules in full aggregation cycles and avoid nested queries and unsupported functions.
- You must configure connectors and accurately monitor their health. Otherwise, it will break the sync. Especially, a small error in attribute naming can spoil the entire task.
- You must make cloud deployments using fresh workflows and identity models.
- You shouldn’t overcomplicate role hierarchies.
Conclusion
We hope this SailPoint IAM tutorial has provided you with information on identity security from foundational to advanced topics. Various industries and leading companies adopt SailPoint for their IAM solutions. That’s why SailPoint professionals are open to more career opportunities for competitive salaries across the globe.
You can start learning SailPoint by working on a simple project. To begin with, you can learn to build a simple workflow in SailPoint using the procedure given in this link.
If you want to explore SailPoint further, you can enroll in MindMajix’s SailPoint Training. The training will provide you with holistic knowledge of SailPoint IAM concepts and strong hands-on experience.
Frequently Asked Questions
1. Is SailPoint easy to learn?
Ans. Yes, you can learn SailPoint easily. However, if you are familiar with IT security concepts and methods, you will find it easier to learn SailPoint.
2. Which is better: SailPoint IdentityNow or IdentityIQ?
Ans. SailPoint IdentityIQ is the on-premises solution. It is ideal for complex environments that demand multiple integrations. Companies that involve frequent customizations use this platform. Technical expertise is required to perform upgrades and maintenance.
On the other hand, SailPoint IdentityNow is a SaaS platform that offers a higher level of scalability, usability and cost-effectiveness. You can make easy and quick upgrades and maintenance with this platform.
So, both platforms come with their strengths. Companies can choose the right one based on their IAM requirements.
3. What is the latest version of SailPoint?
Ans. SailPoint IdentityIQ 8.5 is the latest version of IdentityIQ.
4. Is coding required for SailPoint?
Ans. Yes, you need coding knowledge to work in SailPoint. You need to know BeanShell scripting, SQL, XML, PowerShell and CSS to play around with the SailPoint platform.
5. What is object modeling in SailPoint?
Ans. Object modeling includes constructing and structuring objects and reading data from objects.
The code below shows how to retrieve information about a specific identity.

6. How can I set up custom logging for SailPoint IIQ rules?
Ans. You must follow the two steps below for the setup.
-
- Log4j2.properties
- Rule XML
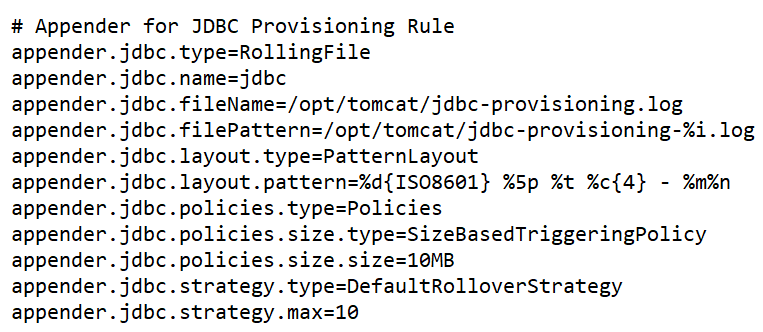
1. Log file configuration
- Define the log file: The code snippet below shows defining a new RollingFileAppender named JDBC.
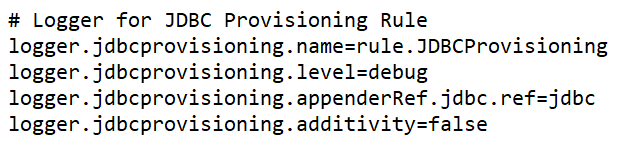
- Direct log messages: The code below creates a specific logger for the JDBC provisioning rule.
2. Rule implementation: The code below shows using the logger for the JDBC provisioning rule.

7. Who is eligible for learning the SailPoint IAM platform?
Ans.
- Beginners
- Identity security professionals
- Security analysts
- Compliance officers
- System integrators
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Sailpoint Training | Feb 21 to Mar 08 | View Details |
| Sailpoint Training | Feb 24 to Mar 11 | View Details |
| Sailpoint Training | Feb 28 to Mar 15 | View Details |
| Sailpoint Training | Mar 03 to Mar 18 | View Details |






