- Home
- Blog
- Unix Shell Scripting
- Unix Commands Interview Questions

Know that computer scientists in Bell laboratories invented the Unix operating system in 1969. Unix is a family of computer operating systems. Unix is popular for its flexibility, portability, adaptability, interoperability, and many more. Not only limited to this, but you can also perform multiple operations since the Unix operating system is a multitasking and multiuser operating system.
When it comes to Unix commands, you can perform various functions using them. For example, you can create, move, and remove files and folders using Unix commands. In this blog, the MindMajix subject expert team has devised Unix commands interview questions and answers with great care. If you go through all these top 50 Unix commands interview questions, it will be beneficial to face your interviews with courage and confidence.
Importantly, the MindMajix subject expert team has prepared these interview questions and answers considering all levels of learners. So, you can find the Unix commands questions and answers from this blog according to your expertise. The team has divided the blog into different sections as follows
Top 10 Unix Commands Frequently Asked Questions
- What are the Different File Types of Unix?
- What do you mean by Kernel in Unix?
- What is the Use of Unix Wildcard?
- What is the use of the Grep Command?
- What do you mean by the File System in Unix?
- List out the Network Commands in Unix.
- How would you remove a File in Unix?
- What are the Various IDs used in Unix Processes?
- What do you Understand by Permissions in Unix?
- What Commands would you use to get User Information?
Unix Commands Interview Questions For Beginners
1. What is Unix?
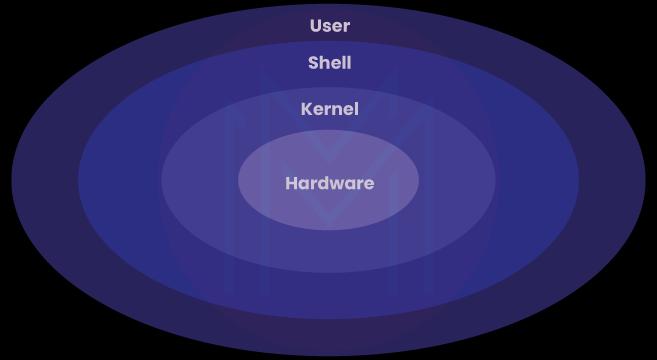
Unix is also referred to as Unics. UNIX stands for UNiplexed Information Computing System. It is one of the most famous operating systems. It is a multiuser as well as a multitasking operating system that provides flexibility and adaptability. Kernel, file system, Shell, and programs are the core components of UNIX.
| If you want to enrich your career and become a professional in Unix Shell Scripting, then enroll in "Unix Shell Scripting Training" - This course will help you to achieve excellence in this domain. |
2. What do you understand by filters in Unix?
A filter in Unix is a program that receives a standard input, processes the input, and delivers a standard output. You can also use the program between two programs in a pipeline.
3. What are the Different File Types of Unix?
The following are the different file types of Unix.
- Ordinary files
- Directories
- Special files
- Pipes
- Sockets
- Symbolic links
4. What is the Process in Unix?
The process is nothing but an instance of a program that runs on a computer. A process starts when a program is initiated. A process or parent process can trigger a subprocess known as the child process. If you terminate a parent process, the child process also gets completed.
5. What do you mean by Kernel in Unix?
The kernel is the hub of the Unix operating system. The function of the kernel is to allocate time and memory to programs. Mainly, it manages file storage. Also, it initiates communication when receiving system calls.
6. Can you describe the general format of Unix command syntax?
The Unix command syntax consists of three parts: the command, a list of options, and arguments.
Syntax
command - (options) argument1 argument2..- The first part, the command, describes the type of operation
- The next part, the list of options, changes the way the command operates
- The last part, the list of arguments, is the additional information required to execute the command.
7. What is the Use of Unix Wildcard?
The wildcard is the symbol used to replace unknown characters. Asterisk (*) and question mark (?) are Unix's two commonly used wildcards. You can use an Asterisk wildcard to replace unknown characters, whereas a question mark wildcard can replace only one unknown character. More to the point, you can use an asterisk to replace an empty string.
8. What do you mean by pipes and links in Unix?
A pipe is used to redirect the output of a command to another. Similarly, you can use pipes to redirect the output of a process or program. In other words, you can combine two or more commands using pipes. It is essential to note that pipes are unidirectional.
Links act as the pointer to a file or directory. There are two types of links such as soft links and hard links. Soft links are also known as symbolic links.
9. What do you understand by the Zombie Process in Unix?
The Zombie Process is also referred to as the defunct process. Generally, the zombie process occurs in parent-child functions. Once the child function completes the execution, it sends an exit message to the parent function. Only when the parent function acknowledges the exit message the child function can exit. In the meantime, the child function is in a zombie state.
10. What is the use of the chmod Command?
Chmod refers to change mode. This command is used to change access permissions of files and directories based on the specified mode in the command. Note that mode is usually identified with octal numbers or letters.
11. What is Command Substitution?
In this process, any command's output is substituted as another command's argument. Command substitution is usually expressed in double-quotes.
12. What do you Understand by a Superuser?
Superuser is the privileged account that can access any file or command. The super status is required to perform many administrative tasks and execute associated commands. The root is the user name of this account. If you want to become a super user, you can achieve this in two ways. One way is logging into the root directory. Another way is executing the su command.
13. What is Superblock?
It is a collection of metadata describing a file system's properties. It describes file systems along with inode and entry. The properties can be block size, filled blocks, block group size, magic number, pointers, and location of inode tables.
14. What is the use of the Grep Command?
Grep refers to the global search for regular expression and print. This command is used to search and match text files. This command searches files for a pattern of characters in text files. After the execution, it displays all the lines of the pattern. The pattern is usually expressed in a regular pattern.
15. What is the use of mount and unmount Commands?
Generally, files are structured in a tree format. And the files are distributed across many devices. The mount command is used to attach a file to the big tree. On the other hand, unmount command detaches a file from the big tree.
16. What is the difference between Absolute Path and Relative Path?
| Absolute Path | Relative Path |
| It is known as the absolute path | It is known as the non-absolute path |
| It refers to a specific location in a file system without denoting the current directory. | It refers to a location denoting the current directory |
| It contains the complete address of a file location. | It contains the partial address of a file location. |
| This path doesn’t change if we change the current directory | This path changes if we change the current directory |
17. What is Inode?
An inode is an entry that contains all the information about a file. It is created on a disk. An inode contains information such as where the file begins, file size when the file was changed along with time, all the associated read and write, execute permissions, the file owner, and many others.
18. What do you mean by the File System in Unix?
A file system is a logical method to store and manage information in the form of files, folders, as well as directories. Know that a file is the smallest unit to store data. Directories contain files and folders. In the Unix file system, all the Directories are organized in a tree structure. This entire system, including files, directories, and folders, is the file system in Unix.

19. Can you brief about the daemon?
Daemon is nothing but a background process that performs a task or set of functions. The background processes include memory management, printer jobs, file system management, network connections, etc.
20. What is the role of the fork ( ) system call?
This system call creates a new process from an already-existing process. The new process is known as the child process, and the primary process is known as the parent process.
Intermediate Level Unix Commands Interview Questions
21. What is Shell and Shell Variable?
- Essentially, the shell is the command interpreter used to process Unix commands.
- Shell variable is usually available to the current shell only. Shell variables are temporary and are deleted soon after the shell session.
| Related Article: Unix Shell Scripting Interview Questions |
22. How would you find a File in Unix?
We can use the ‘find' command to identify Unix files. The following is the syntax of the find command.
Syntax
find (starting directory) (matching criteria and actions)23. How would you copy a File from one host to another in Unix?
We can use the scp command to copy files from one host to another. Using this command, you don't need to start an FTP session or log into the remote systems. Note that this command uses SSH to transfer data. So, if you want to share files or directories in remote systems, you must apply a password or passphrase.
24. List out the Network Commands in Unix.
Following are the various network commands used in Unix.
- hostname
- Ifconfig
- ping
- nslookup
- netstat
- traceroute
- telnet
- finger
25. What do you mean by kill ( ) system call and return value in Unix?
With the kill ( ) system call, you can send any signal to any process or process group. The syntax for this system call is given as follows:
If a signal is sent successfully, then zero will be returned. If not, the value -1 will be returned. Note that at least one signal must be sent successfully to return a zero.
26. Can you differentiate the ‘cmp’ and ‘diff’ commands in Unix?
| Diff Command | Cmp Command |
| It compares files in a directory | It compares text files |
| It denotes the changes that are required to make the files identical | It compares texts byte by byte. And the first mismatch byte is displayed. |
| You cannot use the directory names | You can use the directory names. |
| It will list the files and sub-directories that differ between the two files. | It will list the lines and column numbers that differ between the two files. |
27. How would you remove a File in Unix?
We can use the rm command to remove files from Unix. If you want to delete a file, you need to get write permission on the parent directory as well as execute permission.
Syntax
rm { file name }For example, if you want to remove a text file, you can use write the command as follows
rm abc. txt28. What is the difference between the cat command and the more command?
Both cat and more commands display file contents. However, they differ in displaying the contents. The Cat command's output is the entire file content on a single page, whereas more command outputs file contents page by page.
29. How would you find out whether a system is 32-bit or 64-bit?
We can find this in two ways. One way is using the “uname – a" command, and another way is using the “arch” command.
30. Can you name some File Manipulation Commands?
| Commands | Description |
| cat filename | This command displays file contents |
| mv old_name new_name | This command performs move and rename operations |
| cp source destination | This command copies the source file in the destination. |
| touch filename | This command creates or changes modification time. |
| Is – F | This command displays file type information |
| Is – ltr | This command displays long formats |
| rm filename | This command removes file names |
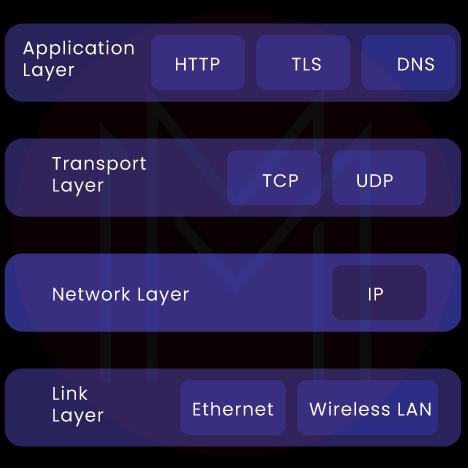
31. What do you mean by Networking Stack and Protocol?
Know that TCP/IP is the networking stack protocol for the Unix kernel. TCP refers to the transmission control protocol. It manages a virtual circuit layer that ensures bidirectional data transmission. IP stands for internet protocol that manages packet transmission between user processes and the networking layer. TCP/IP has four layers as shown below.
32. Why do we use the tee Command?
We use the tee command for two purposes. One purpose is that the tee command receives data from a standard input and sends the data to a standard output. Another purpose is that it redirects the input into a specified file.
33. What do you understand by Wildcard's Interpretation?
When a command line consists the wildcard characters such as * and ?, they will be replaced with the shell.
34. How does the Unix system identify that one command ends and another start?
Semicolons and ampersand characters denote the end of a command. Similarly, the newline character generated by the enter and return key helps to show a command that ends and another start.
35. What do you mean by Aliasing Mechanism?
It is the short form of long commands. By using aliasing, you can reduce the time to type long commands again and again. Below is an example of an alias.
Advanced Level Unix Commands Interview Questions
36. How would you find a hostname if you have an IP address in your network?
We can find the hostname using the nslookup command.
37. Can you write a Unix Command to shut down in 15 minutes and reboot?
We can use /sbin/shutdown –r +15 to shut down a Unix system and then reboot the system.
38. Write a Unix Command to identify the files that must not have the word ‘wonderful’.
We can use grep –vi wonderful *.txt command to find the files that don’t have the word wonderful.
39. How would you display files in the current directory in color and long format?
We can use the command ls-l-color to display files in the current directory in color and long format.
40. How would you Change any user type to a super user type?
We can use the su command for the same. At the same time, you must enter the password to access the privileges granted to you.
41. What are the Various IDs used in Unix Processes?
PID, PGID, and PPID are the three IDs used in Unix Processes.
- PID – It is known as process ID
- PGID – It is known as process group ID
- PPID – it is known as parent process ID
42. How does system boot-up occur in Unix?
It occurs in the following five phases.
- Hardware: First, BIOS starts and makes checks for hardware connections
- OS Loader: It is loaded in MBR, a 512-byte block of the boot device.
- Kernel: It initializes the computer's operating system, drivers, and other components.
- Root user-space process: It establishes an accessible environment for usage
- Boot scripts: The startup scripts are located in directories for every managed service.
43. How would you check disk space using the Unix command?
We can use the %quota –v command to check the space left in disk space. So, it will know the space left in the disks and clean them regularly.
44. How would you check the size of files using a Unix Command?
We can use the %du - s * - command to know the size of various files in the file system of directories and sub-directories. So you can remove unwanted files and empty spaces.
45. Which Unix Command would you use to compress and decompress files?
We can compress files using gzip command. The syntax is given as follows
Similarly, you can decompress files using gunzip command. The syntax is given as follows
46. What do you Understand by Permissions in Unix?
Generally, users are segregated into three groups in Unix: users, groups, and others. The user is the person who created the file. The group is the users with the privileges to access the file as the owner does. Others are the people who have offered access to the file.
Users can read, write and execute when it comes to access rights. Read permission represents that users can only read the contents of the file. Write permission indicates that users can change the contents of the file. Execute permission means that users can only execute the file.
47. How would you Change the Permissions of a File in Unix?
We can use the chmod Command to change the permissions of a file. The syntax for the command is given as follows
This command allows groups, Users, and others to read and write as well as execute.
48. What Commands would you use to get User Information?
- Id: you can get the active user id along with login and group detail by executing this command.
- Last: you can find the last login details of a user by running this command.
- Groupadd admin: you can add group admin using this command.
- Usermod –a: This command can add an existing user to a group.
49. What is the Crucial Function of a Pipe?
You can use the pipe function if you like to run two or more commands simultaneously. While executing pipe functions, the output of one program goes as the input to another program.
You can execute grep and sort commands using pipe functions.
50. How would you differentiate swapping from paging?
| Swapping | Paging |
| The entire process is moved from the swap device to the main memory. | The memory pages required to move are copied into the main memory. |
| Process size matters in swapping | Process size is not a problem in paging |
| Handles memory flexibly | Doesn’t handle memory flexibly. |
Most Common Unix Commands FAQs
1. What is a File System in Unix?
Essentially, a file is the collection of data. Unix has different types of files, such as special files, ordinary files, and directories. Directories are the file types in which ordinary and special files and folders are stored.
2. How to identify the users who are currently logged in using the Unix command?
We can use the who command to identify the users currently logged in now.
3. Which Unix command would you use to view the names of users logged in?
We can use the user command to view the names of users currently logged in users.
4. Is Unix a Programming Language?
No. Unix is an operating system.
5. What language is used to write the Unix Operating System?
C language is used to write the Unix operating system.
| Related Article: Unix Interview Questions |
Tips for Unix Commands Interview preparation
- Solid subject knowledge: It is the first and foremost thing to crack any interview. You must have substantial knowledge of Unix commands and operations. You must research how to use Unix commands for various functions.
- Clear and concise Communication: You must clearly communicate what you are trying to convey to the interviewers. For this, you must have enough courage and confidence in your knowledge. Then, it will be easy to express what answer you are trying to deliver. At the same time, you should answer only the question precisely. You shouldn’t pour what all you know about Unix commands.
- Discuss real-time examples: Before attending a Unix interview, you can get hands-on experience. Work on small projects or complete certification on the Unix operating system. It will help to strengthen your knowledge as well as ease your interview.
- Know the company: You must know the details of the company where you are going to attend interviews. You can go through their websites, whitepapers, case studies, etc. They will give you what they are doing in the market precisely.
- Continuous learning: Show the interviewers that you are a continuous learner. Communicate to them the skills you recently acquired relevant to the job you are attending the interview.
Conclusion
We hope that the Unix commands interview questions and answers provided in this blog post sharpened your knowledge in a better way. We advise you to learn the concepts deeply to ace your Unix command interview soon. This way, MindMajix offers a Unix Training Course and certification with which you can enrich your knowledge and add a feather to your skillset. Apart from this, you can find all other courses on the MindMajix training page. We are sure that you will be one step ahead among your competitors after taking a MindMajix course.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Unix Shell Scripting Training | Feb 28 to Mar 15 | View Details |
| Unix Shell Scripting Training | Mar 03 to Mar 18 | View Details |
| Unix Shell Scripting Training | Mar 07 to Mar 22 | View Details |
| Unix Shell Scripting Training | Mar 10 to Mar 25 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .









