Everyone is aware of the importance of cybersecurity in the modern digital world. Massive losses are being incurred as a result of digital risks. Attackers primarily target companies with weak infrastructure and weak defenses. To safeguard our firm's accounts, infrastructure, secrets, credentials, and other important assets, we must be ready for such threats and call for more advanced cybersecurity tools like CyberArk and Wallix are popular and have a lot of potential to stop security intrusions.
On that note, this blog aims at analyzing Wallix and Cyberark in all possible dimensions. Once you complete this blog, you should get a clear-cut idea about the two, which will assist you in picking the right one for your software protection.
Let’s get on board now!
| Wallix VS Cyberark - Table of contents |
What is Wallix?
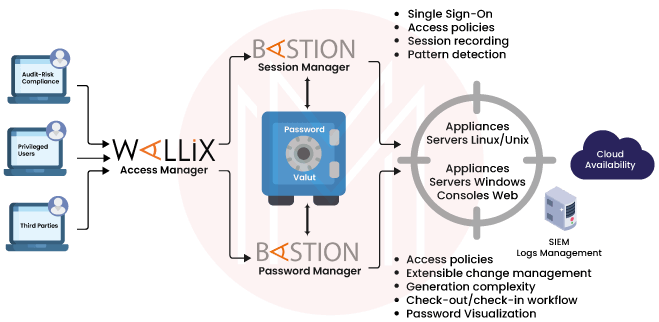
Secure remote access is made possible by WALLIX to help support healthcare organizations. Speed and effectiveness are essential during this period of high activity if you want to give your workers easy access to IT systems and maintain business continuity.
WALLIX solutions can reduce your vulnerability to security breaches and free up your time and resources so you can concentrate on what you do best: saving lives. All the features we need for access management, securing, and restricting access across multiple devices are provided by WALLIX Bastion.
What is Cyberark?
CyberArk Privileged Access Manager's user interface has been streamlined and consolidated.
Authentication, access control, firewalls, encryption, and VPNs are just a few of the tried-and-true cybersecurity techniques that CyberArk employs to safeguard your business from hacking attempts and other online criminal activity. With authorized access security, CyberArk safeguards the server or vault and your user data.
| If you want to enrich your career and become a professional in CyberArk, then enroll in "CyberArk Training" - This course will help you to achieve excellence in this domain. |
What are the Key Features of Wallix?
Wallix comes along with many features such as
- Customize the PAM: Access Manager to the organization's specific requirements with the centralized, customizable admin site. Utilize a common interface to categorize information in accordance with corporate policy and quickly search among Bastions for breach or suspected activity investigations.
- Scalable multi-tenant architecture: The security solutions ought to be able to adapt as your organization changes. Security teams can build Bastion clusters and grant other users both general and specific access privileges thanks to the Access Manager.
- Reduces attack surface area: The Access Management utilizes a specific https point of entry for all accesses and sessions, reducing the attack surface area. Your organization's assault surface is greatly reduced with just one entrance point, allowing you to concentrate resources where they're most required.
- Compliance and audit tools: Tools for auditing and ensuring compliance are included in the Access Manager to help with legal compliance.
What are the Key Features of Cyberark?
The following are CyberArk's standout characteristics
- Advanced Threat Protection: CyberArk offers threat protection policies that support the detection and mitigation of the businesses' particular application risks. These security measures protect against threats to wireless monitoring, Microsoft Windows operating systems, Web browsers, and other IT applications.
- Industrial Regulate Systems Security: CyberArk makes it possible to monitor, detect, and control changes to the Cyberark components, events, and processors of industrial machinery that are frequently the target of cyberattacks. Unauthorized access to vital Industrial Control Systems (ICS) can cause havoc with the infrastructure of smart cities, transportation networks, and power plants. Organizations with OT systems can easily protect and provide remote access to crucial applications using CyberArk Alero.
- Windows Security: With CyberArk Vault, the system sets up the identifying solutions that let users access their vaults directly without having to log in again elsewhere. The user must follow the steps necessary for the system design in order to install Vault.
| Related Article: SailPoint vs CyberArk |
Wallix VS Cyberark- Comparison?
| Features | Wallix | Cyberark |
| Vendor Verified | No | No |
| Protect Password exposure during login | Yes | Yes |
| Black listing/Whitelisting of commands | No | Yes |
| Restrict usage of critical commands through SQL plus, RDP, SSH client, etc. | No | Yes |
| Session recording | No | Yes |
| Central management console | Yes | Yes |
| Log all commands fired over a session | No | Yes |
| Password Management solution | Yes | Yes |
| IAM | Yes | Yes |
| Password Policy | Yes | Yes |
| 2-FA authentication | Yes | Yes |
| AD/LDAP support | Yes | Yes |
| User Activity Monitoring | Yes | No |
Wallix VS Cyberark - Benefits
Wallix Benefits
Administrators are given a configurable admin portal by the WALLIX PAM Access Manager that enables them to obtain access to all WALLIX Bastions.
It features a multi-tenant scalable architecture that is simple to connect with your current security solutions and expands with your company.
Additionally, it has audit and compliance features that produce a verifiable audit trail and gather session and script metadata in video-like captures.
- From a single location, control and secure all access.
- Swift deployment with minimal disruption to operations
- Adapts to current security systems so you may utilize all of their features.
- Supports advanced research and search across all of your Bastions utilizing optical character recognition (OCR) technology.
- Easily adhere to rules of compliance

Cyberark Benefits
CyberArk's key advantages include ensuring compliance with laws and IT standards, safeguarding your devices and passwords, and assisting you in streamlining your security procedures. Details are provided below:
- Certain jobs are automated
By automating the whole privileged lifecycle management operations, CyberArk Advantaged Password Management and Control are able to safeguard the passwords, networks, accounts, and devices. Because of the faster process, as a result, users have more time to concentrate on current urgent issues.
- Assures responsibility
The approach removes the users' right to anonymity when using shared privileged accounts. This will simplify identifying the accountable party whenever something needs to be investigated.
- Flexible
The module is adaptable enough to offer the amount of detail and additional protocols that the audit demands. This degree of adaptability makes it simpler to implement the corporate security policy that prioritizes privileged accounts. The complexity of the passwords and other factors determine the necessary adjustments for the audit requirements.
- Total command of the privileges
Administrators of the CyberArk Privileged Password Management and Control have complete control over every privileged user's access and capabilities. CyberArk provides administrators with the means to specify, alter, and restrict the access of particular privileged users. Users' access rights may be granted based on their "need to know" basis or may be unrestricted, as determined by the administrators.
- Creates reliable audit reports that are secure
CyberArk is able to create and provide an intricate audit report on the documents and access for each and every privileged account. In addition, any privileged behavior can be investigated. These can all be produced and used for forensic investigation and audit proofing. Records are accurate because all of their data is held in a safe location that cannot be altered. The data repository's structure guards against content reconfiguration, unauthorized access, and log erasure.
Disadvantages of Wallix
- Less dedication to your company
Any contractor you employ won't be as loyal to the business or even to the team they're working on. Always please remember that they have been merely a hired shooter to complete a specific task.
- Possible lack of focus
While a competent contractor should be proactive in assisting you with chores, with clear directions and expectations being communicated, you risk paying someone to sit around doing nothing for an hourly rate.
- Increased threat to security
Any outside component that is added to an IT system will inevitably increase the security risk. The unknown factors that a subcontractor brings into your company are numerous. Make it obvious where and what access contractors have, and be sure to withdraw that access when one particular task is finished.
Disadvantages of CyberArk
Some of the disadvantages of cyberark are as follows
- CyberArk Vault is wonderful for enterprises but comes at a hefty price.
- CyberArk Vault User Behavior Analytics tools may be somewhat complicated for non-enterprise customers.
| Related Article: Thycotic vs CyberArk |
Wallix VS Cyberark - FAQs
1. Is CyberArk a PAM solution?
Yes, CyberArk's PAM as a Service enables enterprises to identify, onboard, and have credentials in on-premises, cloud, and hybrid environments, all from a simple cloud computing solution to implement and maintain.
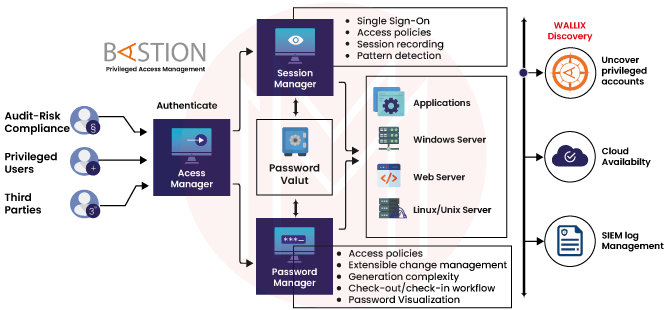
2. What is the Wallix bastion?
The WALLIX Bastion is a modular solution that lets organizations use it based on their big-picture needs, launching features one at a time to create a long-term, sustainable way to protect privileged access.
3. Is CyberArk a SIEM tool?
Yes, CyberArk can interface with SIEM to deliver audit logs via the syslog protocol and establish a comprehensive audit record of privileged account actions within the business SIEM solution.
4. What type of tool is CyberArk?
CyberArk is an Identity and Access Management (IAM) security tool that may be utilized to manage privileged access.
5. What is LDAP in CyberArk?
The LDAP integration parameters define the information necessary for CyberArk Vault to recognize external directories and generate User accounts and Groups. Each external directory with which the Vault will interact has a unique set of directory configurations.
6. What does Wallix do?
WALLIX systems, which specialize in Privileged Access Management, ensure compliance with the most recent IT security standards and defend against cyber-attacks, theft, and data leaks caused by compromised credentials and elevated access privileges to key company assets.
7. What is a vault in cybersecurity?
Vaults function by encrypting each secret to prevent access by unauthorized parties. They primarily serve as an active repository for secrets and an account management system for managing many privileged accounts across the organization.
8. What is the PIM and PAM solution?
Access management terms like PAM, PIM, IAM, and others all mean the same thing: ways to protect your valuable assets. These terms have to do with keeping information and systems safe by controlling who has access and what they can see and do.
9. What is the Wallix access manager?
The WALLIX Access Manager is the guardian of your IT infrastructure. It controls who can access your most important resources from the outside, whether it's a remote employee or a third-party provider.
10. How do PAM tools work?
PAM software and tools function by storing the credentials of privileged accounts, also known as system administrator accounts, in a secure repository in order to isolate their use and record their behavior. The separation is meant to reduce the likelihood that administrative credentials would be stolen or misused.
| Related Article: CyberArk Interview Questions |
Conclusion
Let’s wrap off! Wallix and Cyberark are essentially great platforms to use for security. Secure remote access is made possible by WALLIX to help support healthcare organizations. To manage privileged access, you can use CyberArk as a security tool for Identity and Access Management (IAM). It provides complete options for managing, storing, and dispersing passwords around your businesses. So based on the usage, select the right tool (Wallix VS Cyberark) for your business.
To know more about Cyberark, then enroll your names on CyberArk Training Course and start learning!
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| CyberArk Training | Feb 24 to Mar 11 | View Details |
| CyberArk Training | Feb 28 to Mar 15 | View Details |
| CyberArk Training | Mar 03 to Mar 18 | View Details |
| CyberArk Training | Mar 07 to Mar 22 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .
















