CCNA is a popular certification amongst computer network engineers. This certification program is valid for all graduates from all the streams, and for the network administrators, network engineers, network specialists, and network support engineers. CCNA launched in the year 1998, and it estimates there are one million certified professionals from then.
Cisco CCNA Tutorial
| In This CCNA Tutorial, You Will Learn |
Let's check out what a Computer Network is
A computer network is a group of interconnected devices or systems that can communicate with each other using a standard protocol.

- Above is the example of two computers that are communicating with each other by using a cable, this small network can help to exchange the data among two systems/machines.
- After seeing the above example, the one question that arises in everyone's brain is what if there are multiple systems?
- If there are multiple systems, we can use a hub, a network design, or a switch to connect more than two devices.
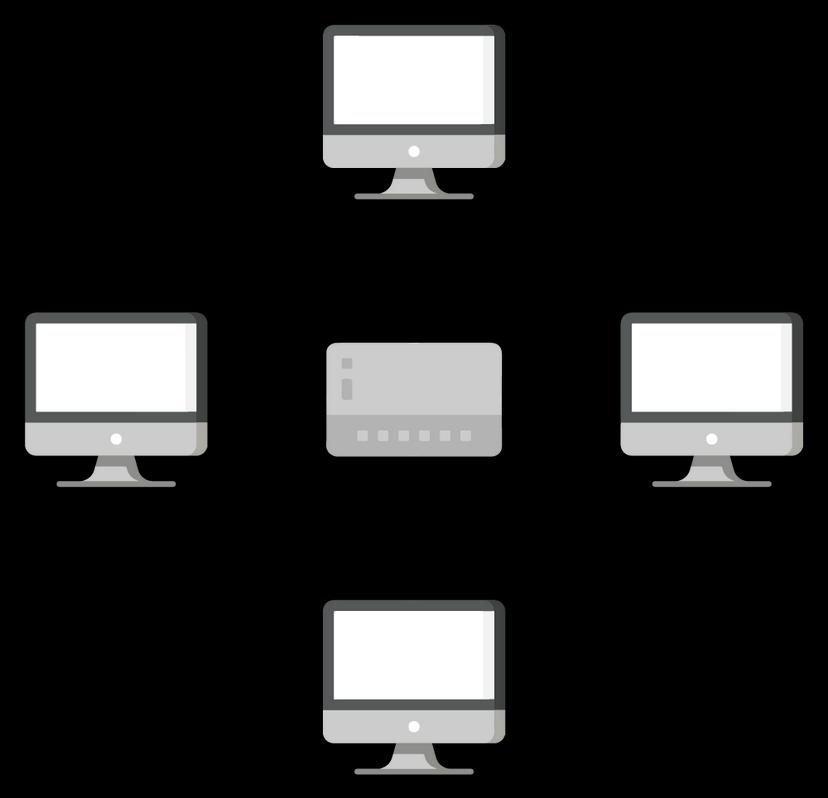
Now every device upon the network will be able to interact with each other.
CCNA Full Form
CCNA, Cisco Certified Network Associate is a certification from the world's most famous company Cisco for selling and manufacturing equipment of the network.
How to get CCNA certification:
Obtaining a CCNA certification needs decent practice and qualifying for the necessary exam. The training option is available at one of the Cisco Learning Partners. Registration to the examination can be arranged straight at Cisco or including with the assistance of a Cisco learning partner.
Cisco partners in education are known for their unmatched excellent training and giving quality learning supplies simultaneously, including the certified lecturers.
Qualifying grades may differ on the exam you necessitate. Typically, it is about 80%. Getting the CCNA Certification can make somebody operate as a Computer Support professional, network consultant, or Network administrator.
The CCNA certification is legitimate for up to three years. Immediately to stimulate your certification, you ought to pass an Assistant or Licensed professional level exam before the contemporary certification lapses. It guarantees advanced learning and makes you convinced that you are competing adequately in the constantly evolving world of (I.T.)Information Technology.
| If you want to enrich your career and become a professional in CCNA, then Enrol Our "CCNA Online Training" This course will help you to achieve excellence in this domain |
CCNA basics for beginners
These are some of the important basics and common topics covered under CCNA certification OSI models
-
OSI models
-
IP addressing
-
IP routing
-
Network security and management
-
WLAN and VLAN
-
Routing protocols and routers
-
Troubleshooting
-
Network Device Security
OSI Models
OSI is a hierarchical model to explain how the various protocols, applications, and devices interoperate to give a network. The Open System Interconnection(OSI) was created by the IOS(International Standard Organization).
There are seven different models in the OSI model they are
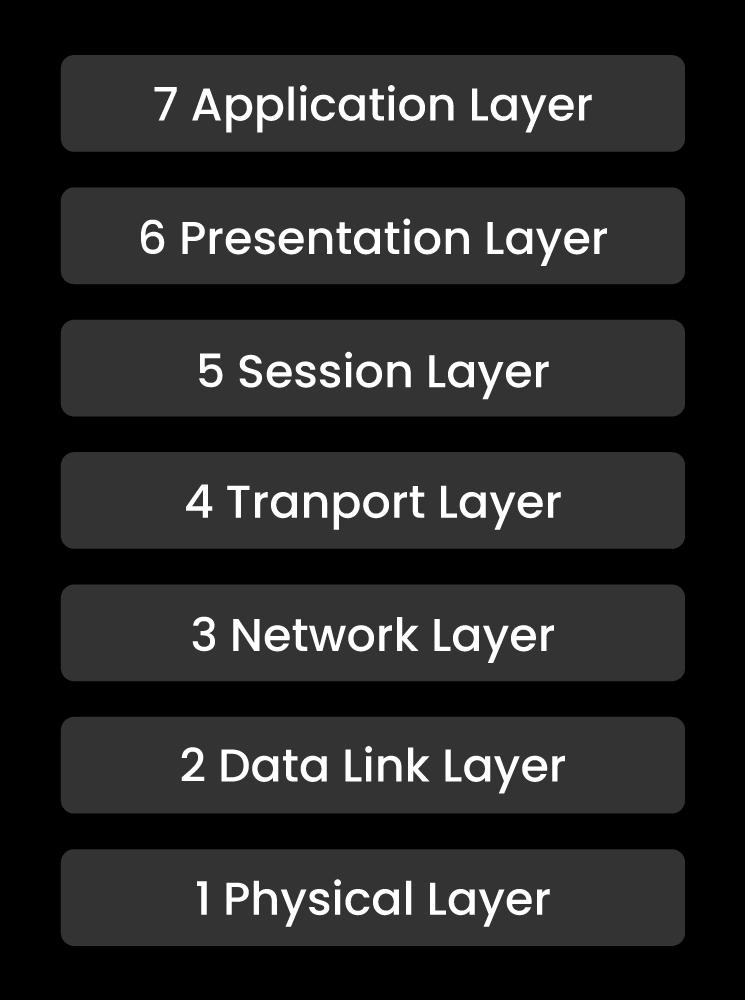
Layer 7: application
Layer 6: presentation
Layer 5: session
Layer 4: transport
Layer 3: network
Layer 2: datalink
Layer 1: physical
Application layer:
The application layer is where the rules, customs, and services that build up your application continue. Representatives of whatever is situated here signify Telnet, FTP(File Transfer Protocol), and SMTP(Simple Mail Transfer Protocol).
Presentation layer:
The presentation panel/layer presents the session layer information toward the application. Representatives of whatever is situated here are encryption, JPG, and ASCII.
Learn end-to-end CCNA concepts through the CCNA Course in Hyderabad to take your career to a whole new level!
Session layer:
The session layer is accountable for starting and stopping network associations. Representatives of the session layer are RPC(Remote Procedure Call) functions including the login part of a SQL concourse.
Transport Layer:
UDP and TCP operation at the transport layer. TCP gives the robust, the in-order delivery of our information, as quite as sequencing, error correction, and windowing. Additionally, TCP within the transport layer gives origin and target port numbers that are commonly associated with applications. For instance, port 25 of TCP is SMTP, 23 of the port is telnet, 22 of the port is SSH, 80 of the port is HTTP, etc.
Network Layer:
The network layer is anywhere the 'I.P.' part of 'TCP/IP' results. I.P. is subject to marking within the network. Because I.P. operates at the 3rd layer, you could also assume that routing and routers operate at the 3rd layer. Any information at the 3rd layer has also been designated a packet.
Leave an Inquiry to learn CCNA Course in Bangalore
Datalink Layer:
If you recall regarding a WAN, several rules operate at the 2nd layer like Frame-Relay and PPP. Nonetheless, if you simply see at the LAN, the usual well-known rule connected with the 2nd layer is Ethernet. The Ethernet rules utilize MAC approaches to recognize unique tools on the network. Any data at the 2nd layer has invited a frame.
Physical Layer:
The physical layer gives real association among the devices. Fiber optic cables and ethernet cables operate at the 1st layer. Data travels over the cables through light or electricity. That information is instantly described as a bit a zero or else a one.
| Related Article: CCNA Questions and Answers |
Routing Loops:
Distance-vector routing protocol utilizes broadcast messages to promote and study network paths.
A router operating a distance-vector routing protocol periodically addresses broadcast messages away from each of its current interfaces. This broadcast information incorporates the entire routing record of the router.
While few other routers running the similarly distance-vector routing protocol accept those broadcast communications, they acquire distinct routes from the advanced routing record and attach them toward their routing table.
From this process, all routers that are operating the similar distance-vector routing protocol study the whole routes of that network.
Why use CCNA?
-
CCNA assists the users in resolving any problem easily.
-
CCNA validates the capability to configure, understand, troubleshoot, and operate the switched and routed networks.
-
It guides the users to build a point-point connection.
-
CCNA guides and explains how to build a network address.
-
You can be highly paid if you are a CCNA certified person.
Advantages of CCNA certification:
-
Companies give priority to the people with the CCNA certification.
-
Certification of CCNA will act as a building block to another Cisco course of networking.
-
New anticipations come afoot, and brand new job chances are built for a person who finishes the CCNA certification program. Eminent I.T. firms look forward to giving jobs to the CCNA certified professionals and also give huge incentives to make them stay in the job a longer-term.
-
The competitor can outflank other systems administration designs based on the refreshed type of information.
| Related Article: CCNA Online Certification |
Features of CCNA:
-
Connectivity of I.P.: OSPFv2, IP routing.
-
Security fundamentals: port security, VPNs, wireless security.
-
I.P. services: QoS, DCHP, SNMP, NTP.
-
Network fundamentals: TCP and UDP, switches, IPV4, AND IPV6.
-
Network Access: trunking, Etherchannel, VLANs.
-
Programmability and automation: Chef, SDN, REST APIs, Puppet.
I.P. addressing:
An I.P. address is a kind of an address utilized to extraordinarily distinguish a device on an I.P. organize. The location is comprised of 32 binary bits, which are distinguishable within a part of the system and host parcel with the assistance of a subnet mask. The 32 binary bits are broken into four octets where one octet = 8 bits.
MAC addressing:
As per Edward Snowden, the U.S. National Security Agency has a framework that tracks the developments of cell phones in a city by observing MAC addresses. Macintosh address randomization during filtering was included Android beginning from variant 6.0, Windows 10, and Linux bit 3.18.
Difference between MAC and I.P. address:
Both the I.P. Address and MAC Address are utilized to interestingly characterize a device on the web. NIC Card's Manufacturer gives the MAC address, then again, Internet Service Provider provides an I.P. Address.
| MAC address | IP address |
| MAC address is abbreviated as Media Access Control. | I.P. address control is abbreviated as Internet Protocol. |
| This is a hexadecimal six Bit address. | There are two different addresses in the I.P. 4 Bit address(IPV4) and six-bit Address (IPV6). |
| Third-party cannot find the MAC address very simply. | It is very simple for the third-part people for finding the I.P. address. |
| ARP protocol can retrieve the device that is attached to the MAC address. | RARP protocol will retrieve the device that is attached to the I.P. address. |
| The NIC card gives a MAC address. | The Internet Service Provider gives the I.P. address. |
| In the Data Link, the Layer MAC address operates. | In the network layer, the I.P. address operates. |
| The MAC address addresses the Physical Address of the computer. | The logical address of the computer is addressed by the I.P. address. |
| We cannot modify the MAC address based on the environment and time. | We can modify the I.P. address based on the environment and time. |
| We can simply recognize the data using the MAC address. | We can recognize the connection of the network by using the I.P. address. |
Types of Router Memory:
There are four different types of router memories:
Non-Volatile Random Access Memory(NVRAM):
We can save the configuration file of a startup. IOS will read this configuration file whenever the router boots up. NVRAM is remarkably fast memory, and it can retain its content whenever the router is restarted.
ROM:
ROM is abbreviated as read-only memory which is available on the processor board of the router. The starting bootstrap software that operates on a Cisco router is generally saved within ROM.
RAM:
RAM is a quick memory that loses its data when the switch is closed down or restarted. On a switch, RAM is utilized to own executing Cisco IOS Operating System, IOS framework tables, and RAM is additionally used to store steering tables, keep ARP reserve, Perform bundle buffering.
Flash Memory:
Flash memory is a memory by which we can re-program and erase the memory electronically. The Flash memory contains the full Operating System Image (Internet Operating System ). This permits you to redesign the O.S. without evacuating chips. Streak memory holds content whenever the router is shut down or restarted.
Working in network security:
Various layers of defenses are merged in the network security within the network at the edge. Every layer of network security executes controls and policies authentic clients/users can obtain access to the network resources, but unauthorized users are immediately blocked from giving the intimidations.
Different types of network security:
There are a few different types of network security they are:
-
Email Security
-
Firewalls
-
Network segmentation
-
Anti-Virus Software
-
Access control
Disadvantages of CCNA:
-
Whenever hosts within your network send a request to a remote web, the remote web will observe the relation as it is transferring from your NAT router. Few hosts execute a level of security as to numerous associations with acknowledging from another host, and they don't react if the characterized number of requests has been reached. This can debase the presentation of your network.
-
End-to-end I.P. discernibility is additionally lost. If you have to investigate your system from a remote site, you will discover investigating progressively troublesome and some of the time even unimaginable.
One of the common questions asked by many people about CCNA is,
Leave an Inquiry to learn CCNA Training in Dallas
Is CCNA hard for beginners?
If you are determined then nothing is hard, the only thing you have to do is get some good training and for giving you better training MindMajix is always here.
Explore CCNA Sample Resumes! Download & Edit, Get Noticed by Top Employers!
Conclusion:
It is mandatory to know the basic topics like IPV6, IPV4, basic networking to dive into topics like switching, and CCNA routing. The topics that we have covered in this CCNA tutorial are fair enough to get a basic grip on the CCNA, so if you want to get complete knowledge, please enroll in the course.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| CCNA Training | Mar 07 to Mar 22 | View Details |
| CCNA Training | Mar 10 to Mar 25 | View Details |
| CCNA Training | Mar 14 to Mar 29 | View Details |
| CCNA Training | Mar 17 to Apr 01 | View Details |

Yamuna Karumuri is a content writer at Mindmajix.com. Her passion lies in writing articles on IT platforms including Machine learning, PowerShell, DevOps, Data Science, Artificial Intelligence, Selenium, MSBI, and so on. You can connect with her via LinkedIn.









