
The world is fast-paced, and many business applications are moving from private to public clouds. They have become virtualized and are also distributed across multiple locations. More so often, they are beyond the physical control of the security teams, which has caused a spike in the number of attacks on companies. In this kind of scenario, network security would come to aid these organizations. It is a set of technologies made for the protection of the company's infrastructure by inhibiting the entry of threats.
Highlights for Network Security:
- Accessing control over the network is an important job. If the security of the network goes out of the access, then the network becomes much more prone to DDoS or malware attack.
- The need for threat control is important after access control. It safeguards the network from the entry of unknown malware objects.
- The need for remote access VPN in network security can create a secure environment for exchange of ensured sensitive information.
- Other factors affecting the security over the network include ransomware, Trojans and viruses. The use of anti-malware are the prevention measures for providing network security in such cases.
We have categorized DevSecOps Interview Questions into 3 levels they are:
Top 10 Network Security Interview Questions
- Describe pipelining.
- Which are the layers that are referred to as network support layers?
- What is MAN in networking?
- Describe the intranet.
- What types of DDoS attacks are there?
- Tell us about CIA Triad in the network security.
- In terms of network security, what is IPS?
- Give some examples of Shadow IT.
- A proxy firewall: what is it?
- Define Ransomware?
Network Security Interview Questions For Freshers
1. Tell us about what "risk" means in terms of network security. How about "vulnerability" and "threat"?
Ans: When a system is secure but not adequately secure, the possibility of a threat increases, creating a risk. A vulnerability is a flaw or opening in your equipment or network (e.g., routers, modems, access points). A viral attack is an example of a threat; it is the real mechanism of producing an occurrence.
2. Explain protocol?
Ans: It is a collection of guidelines that control every element of information exchange.
3. Describe pipelining?
Ans: When a task is started before the one preceding, it has been finished, and this is called "pipelining."
| If you want to enrich your career and become a professional in CCNA, then enroll in "CCNA Online Training" - This course will help you to achieve excellence in this domain. |
4. What is a network?
Ans: A network is a collection of interconnected computers and other gadgets that enables the communication between them. This is the procedure that connects the gadgets and enables the communication between them. The capacity to distribute data is among networking's most crucial features.
A vast network called the Internet enables people to exchange information and connect with one another. People can get information more quickly and efficiently by exchanging data. Security is a key component of networking. It's risky to the network since so many things are possible that you can't predict. For instance, you can lose all of your data if someone hacks into your computer. You could get into problems if your identity is stolen.
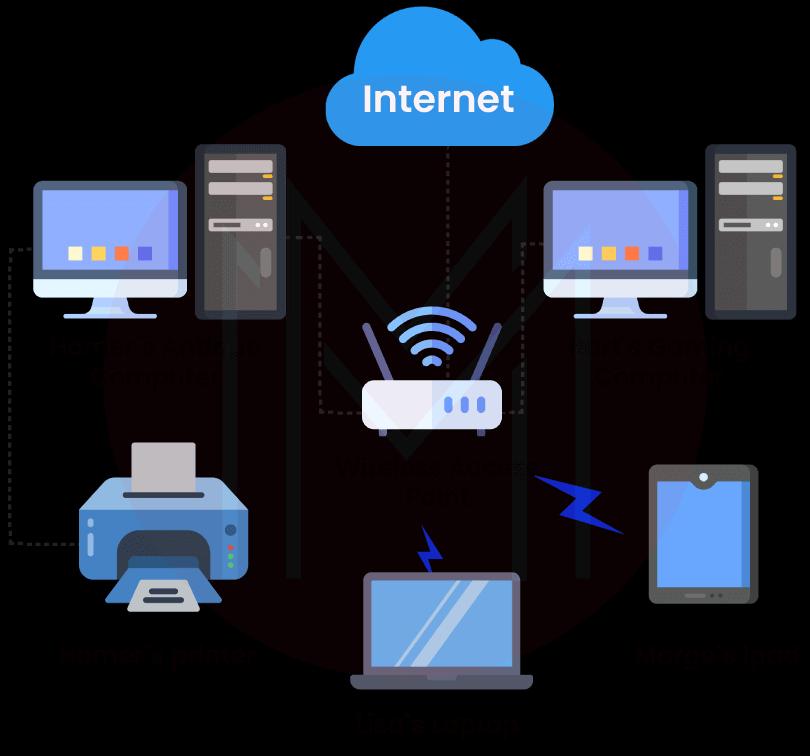
5. Which are the layers that are referred to as network support layers?
Ans: The layers that are referred to as network support layers are listed below:
- Data Link layer
- Physical layer
- Network layer
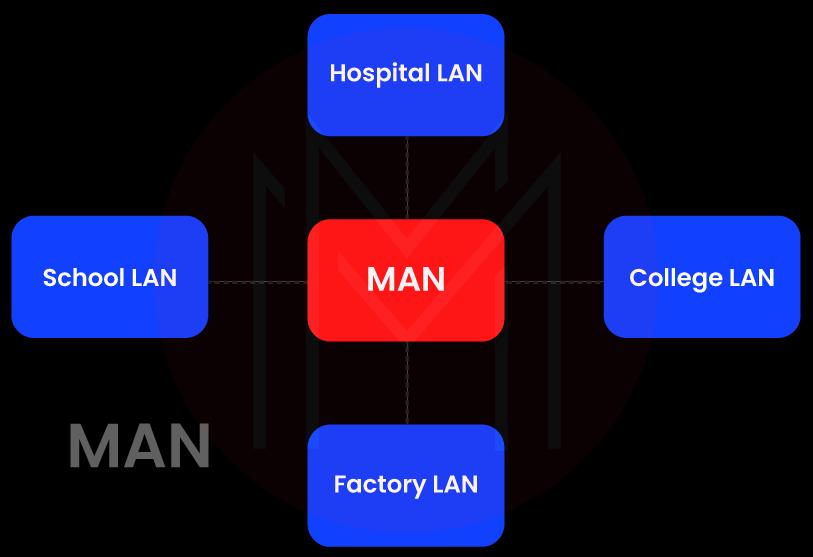
6. What is MAN in networking?
Ans: A MAN, as opposed to a WAN, links many computers that are physically apart yet located in two or more cities. It is employed to deliver fast connectivity. It has a wide geographic scope and might serve as an ISP (internet service provider). MAN connections come in Mbps ranges. A MAN network's complexity makes it challenging to set up and maintain.
MANs are more congested and less dependable. They are expensive and might or might not be under the authority of one entity. Although MANs can transfer data quickly, there isn't much of it. Data is sent through modems and wire or cable. A MAN is a section of a telephone company network that connects a cable TV network in a city to a customer's DSL line.
7. Define RIP?
Ans: Routing Information Protocol, or RIP, is a basic protocol used to communicate information between routers.
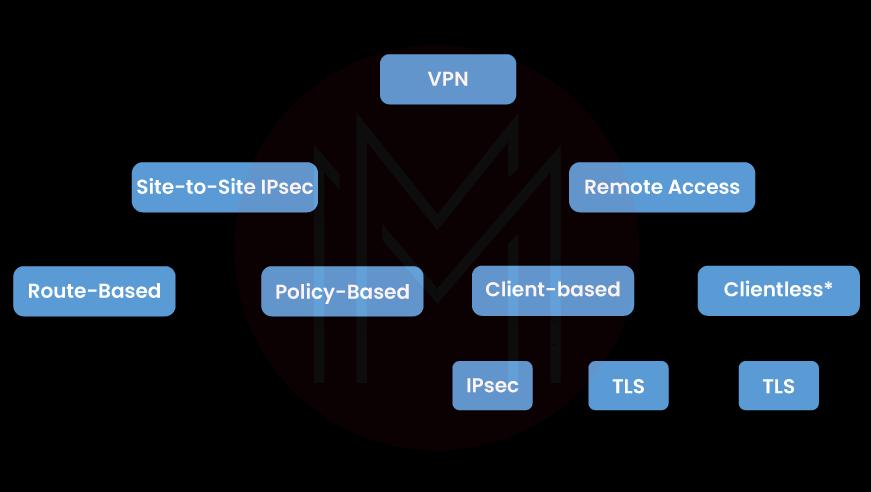
8. What Types of VPNs Are There?
Ans: These categories apply to VPNs:
Remote access and site-to-site
9. What do you think should be the goal of information security in a company or an organization?
Ans: Security for networks should:
- Ensure that the network is always accessible to all users.
- Stop unauthorized access to the network
- keep all users' privacy protected
- Protect the networks against DDoS attacks, malware, and hackers
- Defend and safeguard all data against theft and corruption.
10. Describe the intranet?
Ans: A closed network of sorts is an intranet. It is used by a number of businesses, and only its staff members have access to it. Networks called intranets to enable PCs from several organizations to connect with one another.
An intranet is a private network to which only its users can have access. Many businesses and enterprises have private intranet networks that are exclusively accessible to their clients and workers. An intranet is a closed network; thus, it safeguards your data by not transmitting it to the outside world.
21. What are various techniques there for user authentication?
Ans: Several commonly used techniques for user authentication include:
- Authentication Token
- Biometric Authentication
- Password Authentication Protocol (PAP)
22. What types of DDoS attacks are there?
Ans: DDoS assaults are classified into three categories:
- Attacks based on volume: Attacks focused on volume employ a lot of traffic to fill the network's bandwidth.
- Protocol attacks: Attacks against protocols are intended to exploit server resources.
- Application attacks: Applications are the target of application attacks, which are the most dangerous type of attacks.

23. Describe how symmetric and asymmetric encryption differ?
Ans: Asymmetric encryption uses different keys for encryption and decryption, whereas symmetric encryption utilizes the same key for both operations. For obvious reasons, symmetric is faster, but there is a danger involved in transferring the key via an unencrypted channel.

| Related Article: CCNA vs CCNP - Difference |
24. Describe ALOHA?
Ans: Access to a shared communication network channel can be coordinated and arbitrated using the ALOHA system. It is frequently employed to address the channel allocation problem.
ALOHA can be of two types:
- Pure Aloha
- Slotted Aloha
25. What distinguishes a local area network that is wired from one that is wireless?
Ans: Wireless LAN devices comprised WLAN routers and MiFi routers, while wired LAN devices included hubs, routers, and switches.
Network Security Interview Questions For Experienced
26. Describe adware?
Ans: Unwanted advertisements are displayed on your mobile device or computers by malware known as adware. Without the user's awareness, adware is frequently installed on computers and mobile devices. Adware frequently gets activated when customers try to install legitimate software.
However, some pop-up windows are meant to target you with personalized advertisements. Some pop-up windows just display advertisements without gathering data or infecting your computer. You could be exposed to computer viruses if adware exploits advertisement links to lead you to dangerous websites and infected pages.

27. In regards to network security, what does AAA mean?
Ans: AAA refers to Authentication, Authorization, and Accounting. The protocols are what control how a network is accessed. It functions as a system for controlling user access, enforcing rules, and monitoring all network activities. Two network protocols that support AAA are Radius and Diameter.
A user's authorization to use the system and network is determined via authentication. There must be a username and password. Authorization refers to the rights that control access. It means that each network user can only access a limited set of data and information according to their status within the company. Accounting helps compile every network activity for every use.
| Related Article: CCNA Tutorial for Beginners |
28. List the basic principles of network security?
Ans: A set of rules and regulations for network security and access, along with appropriate hardware and software solutions. Network security describes all methods used to safeguard a network and its data from intrusions and other dangers.
Network security includes a variety of measures such as traffic monitoring, virus detection and elimination, data encryption, and access control for computer networks and applications.
A solid network security plan safeguards client data, upholds the confidentiality of shared data, and ensures dependable network performance. It reduces overhead expenses while shielding companies from expensive data breaches and other security failings. In order to protect themselves against cyber threats, businesses must make sure users have authorized access to data, systems, and apps.
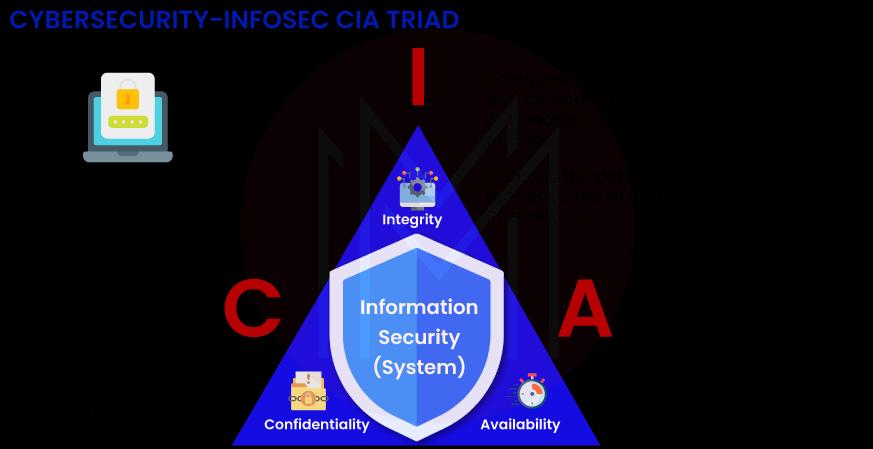
29. Tell us about CIA Triad in the network security?
Ans: Confidentiality, Integrity, and Availability are abbreviations for these concepts. The CIA also referred to as the CIA Triad, is a well-known example of how privacy policies should be upheld in businesses. Security professionals evaluate threats after evaluating their possible impact on the availability, confidentiality, and integrity of the organization's assets.
Only when a network has all three of the CIA Triad's essential elements can it be said to be secure:
- The practice of keeping an organization's data private and secret by a determined effort is known as confidentiality. As a result, those who are not permitted are blocked from accessing certain assets, while those who are approved have access to them.
- Integrity is the guarantee that information is accurate and reliable.
- The availability of systems, programs, and data must be constant, and authorized users must have access to resources at all times.
30. What advantages does a firewall provide?
Ans:
- To make sure no harmful code is present, a firewall needs to keep track of all data that is transferred via a network. Every packet is monitored to see whether it includes any potentially harmful content. If it does, it immediately blocks it.
- Because a Trojan hides on a computer and watches everything you do, it is hazardous to users. It might be able to observe anything you do on your computer, including private data. Your computer is most likely being controlled by a Trojan when it starts acting suspiciously. Once they have entered your system, Trojans will be promptly blocked by a firewall.
- In order to commit online felonies, computer hackers search the internet for susceptible machines. When they come upon such machines, they would start running malicious software, such as computer viruses. Unknown people, including your neighbors, may also be looking for free internet access. It is essential to be secured by a firewall security system in order to stop these situations.
- In order to stop hackers from abusing them, a firewall might restrict access to specific hosts and services. Blocking access to the system from these hosts is the best line of action. This access policy may be applied if a user feels that they need to be protected from these kinds of unauthorized access.
- One of a user's main worries when using the internet is privacy. Hackers search for information about the user's privacy to understand it. Many online services, such as the domain name service and the finger, can be blocked by a firewall, for instance. Hackers are so prevented from obtaining user data. In addition, DNS information may be blocked by firewalls, preventing an attacker from learning the name and IP address of the targeted website.
31. In terms of network security, what is IPS?
Ans: Intrusion Prevention System is referred to as IPS. Intrusion Detection Prevention System is the second name for it (IDPs). The main goal of IPS is to monitor the network for any malicious or suspicious activity that might be trying to take advantage of a known vulnerability.
Once such activity is recognized, the threat is either detected and allowed (IDS) or prevented (IPS). A few methods for preventing intrusions include policy-based, protocol-based, anomaly-based, and signature-based IPS.
The IPS notifies system administrators of such occurrences and responds by blocking access points and configuring firewalls to stop further intrusions.

32. Why would you use a proxy firewall?
Ans: A proxy firewall, a primitive form of firewall device, serves as a gateway from one network to another for a particular application. By filtering communications at the application layer, a proxy firewall is able to secure network resources. Through the proxy, the firewall proxy server performs its duties at the application layer. This is achieved by creating and running a firewall process that imitates a service that is present on the target host.
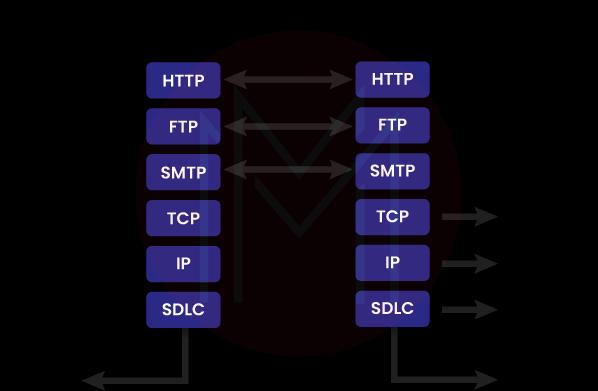
33. Define Administrator Privileges? Why are they necessary while attempting to install a download?
Ans: The permissions given by administrators to users are referred to as administrative privileges. They have the ability to add, remove, and change settings and items thanks to their capabilities.
We are unable to make various system modifications without administrative rights, such as installing software or adjusting network settings. We could be able to run a program but not upgrade it if we don't have administrator rights.
34. Give some examples of Shadow IT?
Ans: All IT-related transactions and activities that the IT department is not aware of are referred to as "shadow IT." It consists of all tasks completed in accordance with the rules set forth by the business.
The samples shown below are grouped in several ways:
- Cloud services include SaaS, IaaS, and PaaS.
- Hardware includes computers, tablets, laptops, flash drives, smartphones, and so on.
- Packaged Software
- Slack and Trello – productivity tools.
- VoIP and Skype – communication programs.

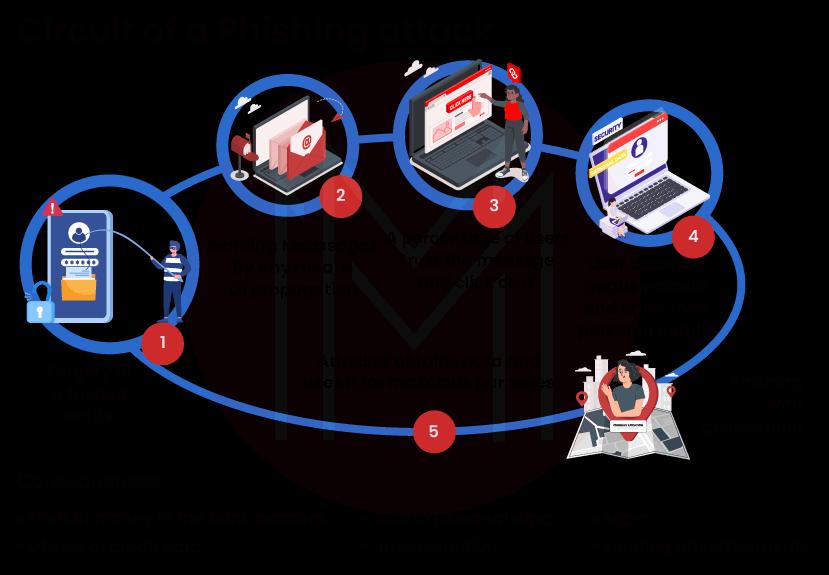
35. How is phishing carried out?
Ans: Hackers can take the victim's personal data, including login credentials and credit card details, by using phishing, a type of social engineering attack. It begins with a phony text message, email, or other kinds of communication designed to lure a victim. The message appeared to have come from an established source.
In order to obtain sensitive information, the victim is tricked into opening those emails or text messages by the phishers, which has disastrous consequences.
In addition to stealing personal data, hackers can corrupt computers with viruses and convince victims to participate in money laundering.
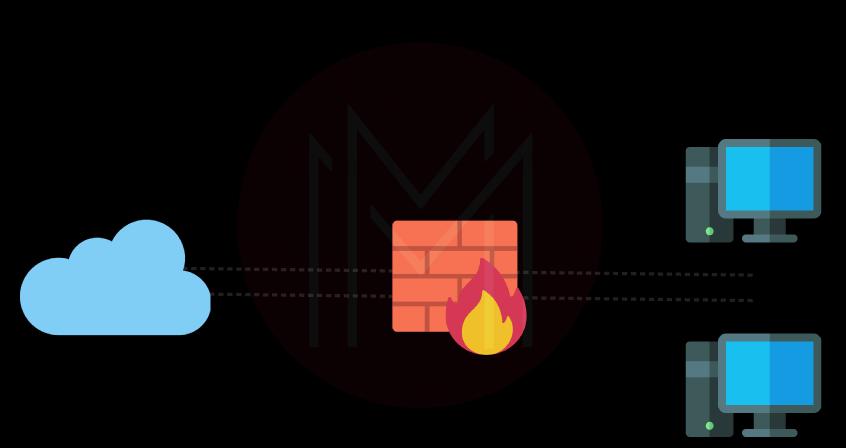
36. A proxy firewall: what is it?
Ans: By filtering packets at the application layer rather than the network or transport levels, a proxy firewall safeguards network resources. However, utilizing one can cause applications to lag and have reduced functionality.
Traditional firewalls do not prioritize traffic decryption or application protocol traffic inspection. As a result, IPSs and antivirus programs only cover a limited percentage of the threat landscape. In order to allow the transfer of safe data between computers and servers on the internet, proxy servers function as a conduit between two networks.
To safeguard networks against cyberterrorism and unauthorized access, a proxy server filters manages, blocks, archives, and controls requests from devices. It chooses which traffic is allowed and forbidden and looks for indicators of a malware incursion or cyber threat.
37. What are the most effective measures against a login brute force attack?
Ans: You may protect yourself from a brute force login attempt in three main ways. There is an account lockout as a start. Except when the administrator decides to revive them, violating accounts are disabled. The progressive delay defense is the following. Here, after a few failed login attempts, the account remains locked for a specified amount of days. The challenge-response test, which prevents automatic submissions used on the login page, is the last step.
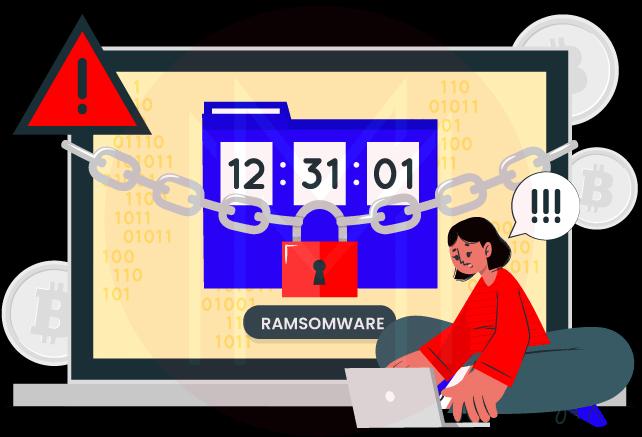
38. Define Ransomware?
Ans: Data is often encrypted or encoded by a ransomware threat until the victim pays the attacker a ransom. The ransom demand frequently includes an expiration date. The demand is satisfied if the victim doesn't make a timely payment, the data is lost forever, or the ransom is raised. Attacks using ransomware are commonplace today. Ransomware affects companies all around Europe and North America.
Cybercriminals target various types of consumers and businesses. Several government organizations, like the No More Ransom Project, in addition to the FBI, advise against paying the ransom to prevent promoting the ransomware cycle. In addition, it's possible that 50% of those who pay the ransom will once again be the target of ransomware, particularly if the infection is left on the computer system.
39. What are some of the various ways of phishing attacks?
Ans: The types of phishing attacks are:
- Email Phishing: Phishing via email is the most prevalent kind. The phisher will set up a bogus domain that impersonates a reliable source and send victims general demands for confidential information. The information is used by scammers to commit fraud or launch other attacks.
- Spear Phishing: It looks for victims on social media and other websites in order to personalize communications and make them seem more genuine rather than targeting a large group of people.
- Whaling: Here, the assailants target persons in high-ranking positions. Attackers spend a lot of time analyzing their targets to determine the best moment and the best way to steal their private information.
- Smishing and Vishing: Smishing involves text messages, but Vishing involves a telephone call with the victim. Both phishing attacks have the same ultimate objective as other phishing attacks.

40. What's traceroute?
Ans: Administrators can track the route that data packets take to their destination from their source and identify connectivity issues by utilizing network diagnostic tools like traceroute. On a Windows computer, the command is TRACERT; on a Linux or Mac, it is traceroute. Both traceroute and TRACERT perform a similar function: they show the path that data takes from one point in a network to a certain IP server. Each device that a data packet must pass through in order to get to its final destination is listed by Traceroute along with its name and IP address.
The round-trip time (RTT) and the device name are then provided. Traceroute can help you locate a problem, but it can't tell you whether there is one or not. Ping can be used to help you figure out if there is an issue. Consider attempting to visit a website where the pages load slowly. You can locate the issue by using traceroute to find the locations with the greatest delays.
Frequently Asked Network Security Interview Questions
1. Which three factors affect network security?
Ans: Confidentiality, integrity, and availability are the three elements that make up the idea of network security; collectively, they are known as the "CIA triad." A network may only be considered secure when all three elements are active at once.
2. What main varieties of network security are there?
Ans: Different Forms of Network Security Measure:
- Data Loss Prevention (DLP)
- Email Security
- Firewall
- Hyperscale Network Security
- Intrusion Prevention Systems (IPS)
- Network Segmentation
- Remote Access VPN
- Sandboxing
3. Define network security?
Ans: A group of technologies known as network security guards against a wide range of potential dangers from entering or spreading within a network, preserving the usefulness and integrity of a company's infrastructure.

4. In terms of network security, what is a firewall?
Ans: An example of a network security tool is a firewall, which monitors incoming and outgoing network traffic and decides which traffic to allow or block in accordance with a set of security rules. Firewalls have been the primary line of defense for network security for more than 25 years.
5. What is the purpose of network security?
Ans: Having a secure network is essential for both private and professional networks. Most homes with high-speed internet have one or possibly more wireless routers, which, if they are not sufficiently protected, might be targets of attacks. A robust network security system can reduce the risk of sabotage, data loss, and theft.

6. Where is the use of network security?
Ans: Network security includes a range of computer networks, both private and public, that are utilized in daily tasks, including carrying out transactions and facilitating interactions between enterprises, governmental organizations, and people. Networks can be private, like that inside of a business, or they might be public.
7. Who is in charge of maintaining network security?
Ans: The Cybersecurity and Infrastructure Security Agency (CISA), in more detail, protect US infrastructure from cyber threats. CISA is in charge of defending critical infrastructure and federal networks from intrusions as a part of the Department of Homeland Security.
8. Define network threats?
Ans: A threat to your network and data systems is exactly what a network security threat is. A network threat is any attempt to access your data through a network breach.
9. Tell us about the types of firewalls?
Ans: There are five types of firewalls. The following are:
- Application-level gateway (aka proxy firewall)
- Circuit-level gateway.
- Next-generation firewall (NGFW)
- Packet filtering firewall.
- Stateful inspection firewall.
10. What are the five causes of issues with network security?
Ans: 5 Typical Network Security Issues and Their Solutions:
- Problem #1: A Lack of Defense in Depth
- Problem #2: Abuse of User Account Privileges
- Problem #3: Not Enough IT Security Management
- Problem #4: Unknown Assets on the Network
- Problem #5: Unpatched Security Vulnerabilities
Conclusion
With the world getting a step closer to the advancements of technology, they are also getting a step closer to falling into the vicious cycle of cyber threats. It is self-explanatory why network security is not only a need but also a must. The opportunity in network security as your career is endless. The questions that we provided you are some of the possibilities and top ones, but we do not guarantee that only these will be asked. So we wish you the best in your preparations!
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| CCNA Training | Mar 10 to Mar 25 | View Details |
| CCNA Training | Mar 14 to Mar 29 | View Details |
| CCNA Training | Mar 17 to Apr 01 | View Details |
| CCNA Training | Mar 21 to Apr 05 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .









