- Home
- Blog
- Hardware Design Development
- DAA Interview Questions

A Data Access Arrangement (DAA) electronically connects a computer to a regular phone line. A DAA is the same as a telephone line interface circuit (or Module). Data transmission equipment on the end user's end of a public switched telephone network, including all devices that could affect the interface's characteristics.
Data Access Arrangements are hierarchically organized and frequently connected to a role or role group. A set of users with the same database access level is called a role group. Users with a legitimate business need for access to the database will be the only ones to whom access will be granted under the terms of the access arrangement.
Learn some facts about Data Access Arrangement
- Any device that connects to the public switched telephone network (PSTN) needs a DAA. It includes fax machines, private branch exchanges, set-top boxes, alarm systems, and more.
- The DAA protects the electronic device, among other things, from the higher voltage on the phone line. DAA circuitry must be registered with the organization in charge of the phone system.
- However, most modem and device manufacturers incorporate a DAA design that has already been approved into the modem.
Now we will go through some DAA Interviews. Then we will move on to the DAA Interview questions and answers separately for each of the following-
Top 10 DAA Interview Questions
- What is the DAA algorithm?
- What is Backtracking in DAA?
- What are the different types of algorithms?
- What is a Dynamic Method in DAA?
- What is a Sorting Network?
- Explain the Bubble sort algorithms.
- What is DAA Programming?
- What is the function of DAA instruction?
- What exactly is Dynamic Programming?
- What are some examples of Data Structures Applications?
DAA Interview Questions And Answers For Freshers
Are you looking for the best DAA interview questions and answers to help you get through the interview process? You're definitely heading in the right direction!
Here are some DAA interview questions for fresher graduates include below
1. What is an Algorithm?
The Term 'Algorithm' refers to the set of instructions that must be followed to solve a problem. The logical description of the instructions can be executed to carry out a critical function. Algorithms are typically generated independently of primary languages, implying that an algorithm can be accomplished in more than one programming language.
| If you want to enrich your career and become a professional in Hardware Design Development, then enroll in "Hardware Design Development Training". This course will help you to achieve excellence in this domain. |
2. What is the DAA algorithm?
A DAA algorithm is a procedure that accomplishes its goal effectively and can be expressed in a finite amount of time and space. DAA algorithms are instructions for computers to follow when they need to perform a calculation, process some data, or use some form of automated reasoning to resolve a problem.
3. What is DAA design?
The fields of algorithm design and analysis help design algorithms that can be used to solve various problems in computer science. It is beneficial to design and analyzes the logic governing how the program will function before developing its actual code.
4. What is the Algorithm's Time Complexity?
The time complexity of an algorithm was the total amount of time required for the program to run until it was finished. In most cases, it is expressed with the notation known as the big O. The length of time needed for a program to run entirely was indicated by the Algorithm's time complexity.
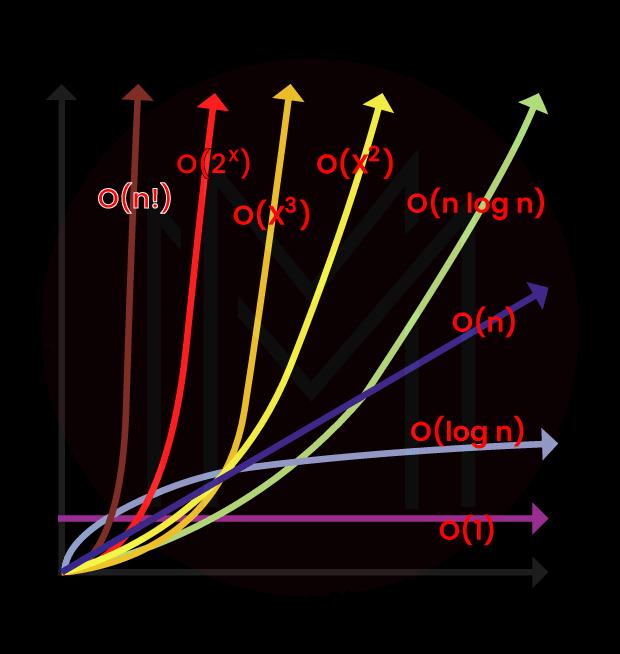
5. What is Data Structures?
Data Structures are one of the most basic ways to store and display data. Data is how a processor shows facts, ideas, and instructions for all computing tasks. Data structures are the different ways all this information can be organized helpfully.
6. What is Backtracking in DAA?
The term "Backtracking" refers to a recursive algorithmic technique for solving problems by first attempting to build a solution and then discarding any solutions that don't meet the problem's constraints at that stage. You could say that going backward is better than going forwards with force. The backtracking method involves searching through all options to find a solution to a problem
7. What is a Greedy method in DAA?
Greedy algorithms construct a solution piece by piece, selecting the subsequent component in a way that provides an immediate benefit. This method never takes prior decisions into account. This method is primarily employed to address optimization issues.
8. What are the different types of algorithms?
There are many different types of algorithms available, and they are listed below:
- Randomized Algorithm
- Hashing Algorithm
- Recursive Algorithm
- Brute Force Algorithm
- Searching Algorithm
- Sorting Algorithm
9. What is Asymptotic Notation?
A method that can represent the behavior of functions when they are either in the limit or when they are not bound. The notations are explained in terms of methods, and the domains of those methods are the set of natural numbers represented by the numbers 0 through 2.
Notations of this kind make defining the worst-case running time function T more convenient (n). It is possible to extend it to cover the realm of real numbers.
10. What is a Dynamic Method in DAA?
Similarly to the divide-and-conquer strategy, the key to success in dynamic programming is to merge the results of previously solved subproblems. In addition, the dynamic programming algorithm only needs to compute the solution to each sub-problem once, and then it can reuse that information from a table.
11. What is Dijkstra's Algorithm?
Dijkstra's Algorithm computes the shortest path from a given source vertex to a given target vertex in a weighted graph or digraph by solving the single-source shortest path problem. Dijkstra's Algorithm works properly for graphs with positive weights.
12. What exactly are Huffman Trees?
A Huffman tree is a binary tree that shortens the time it takes to travel from the root node to each of the leaves by using weights that have already been determined. The most effective application of Huffman trees is to create a Huffman code with their help.
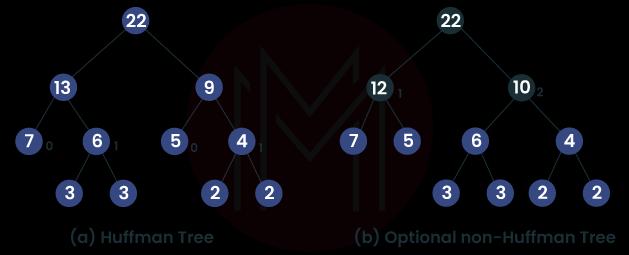
13. What criteria are used to make the Algorithm work better?
The various standards used to raise the Algorithm's effectiveness include
- Input: "Input" means that one or more quantities come from the outside.
- Output: The composition of at least one quantity constitutes an output.
- Clarity: Every guideline is easy to understand and follows.
- Finiteness: Algorithms are said to be "finite" if they can be solved in a finite number of steps by following their instructions to the letter.
- Effectiveness: Efficient teaching requires starting at the very beginning.
14. What is the Knapsack Problem?
Assume we have n elements, where we know their weights wi and values vi for i=1, 2, etc. Given n and W, identify the most valuable subsets of the elements that fit in a knapsack of size W.
When sorting the components of a specific instance, it helps to do so in descending value-to-weight order. It means that the payoff per unit of weight is highest for the first element and lowest for the last.
15. What is Dynamic Huffman Encoding?
The dynamic Huffman encoding tree is updated after each character is read. It guarantees the highest degree of precision in the coding process. For the most precise coding, this is a must. To avoid the problems inherent in the bare-bones implementation, we turned to dynamic Huffman n-coding.
16. Write the difference between dynamic programming and the greedy method?
Greedy method
- There is always only one path that can unfold.
- It need not always supply the best possible answer.
Dynamic programming
- There are a plethora of options from which to choose.
- Provides the best possible answer every time
DAA Interview Questions And Answers For Experienced
17. What are Minimum Spanning Trees?
A tree is a spanning tree for a linked graph if its set of vertices is the same as the graph's set of vertices and its edges are a subgroup of the graph's edge set.
A spanning tree is a component of every linked graph. The sum of the weights of each edge in a spanning tree is the tree's weight, denoted by the symbol w (T). The Minimum Spanning Tree, abbreviated MST, is a spanning tree with the least amount of weight that is practically possible.
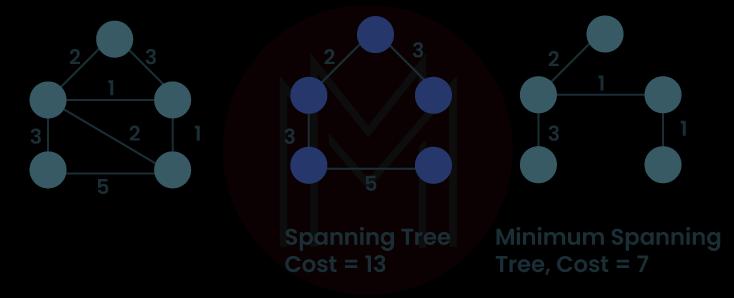
18. What exactly do you mean by the Huffman code?
A Huffman code is an optimal variable-length prefix tree encoding method. This method works by assigning bit strings to characters in a text based on the number of times those characters appear.
19. What exactly is Backtracking?
The generation of depth-first nodes is referred to as backtracking when using the bounding method. The backtracking method can find the solution in a significantly smaller number of iterations than m trials.
20. What is a Sorting Network?
A sorting network is a mathematical representation of the wired network and comparator modules used to order a set of numbers.
This model is used to sort the numbers. Every comparator has two wires that connect and sort the values by sending the value lower to one wire and the other wire higher. In contrast, with comparison sorting algorithms, the series of comparisons is determined by the outcome of the comparisons that came before it. Because of this independence of comparison series, parallel execution of the methods can benefit greatly from having this property.
21. What is time Complexity in DAA?
Time complexity, a particular case of computational complexity, describes the time it takes to run an algorithm. The time complexity algorithm is the specific time that must elapse before any statement can be executed. Accordingly, this is highly dependent on the amount of data being processed.
22. What is the principle of optimality in DAA?
When the subsolutions of a problem's optimal solution are also the optimal solutions for their respective subproblems, we say that the problem satisfies the principle of optimality. It means that the optimal solution to the problem has subsolutions that satisfy the principle.
Examples: The principle of optimality can be shown to be satisfied by the shortest path problem.
23. What is reliability design in DAA?
The probability that a product will continue to function past the time specified and under the specified conditions is known as reliability. It implies that even if a keyboard has 99% reliability over 1000 hours, 1% of those 1000 hours could still see a malfunction.
24. What is the order of growth in DAA?
The order of growth of an algorithm provides a rough estimate of the amount of time needed to execute a computer program as the size of the input variable increases. The order of growth does not take into account the constant factor that is required for fixed operations. Instead, it emphasizes the operations that expand in proportion to the input size.
25. What is the Importance of Algorithms?
An algorithm is merely a procedure for accomplishing a goal. Computers, smartphones, and websites can't perform their tasks or make decisions without them; they're the foundation of programming. Many of the activities we engage in daily are, like algorithms, used by technology.
26. Explain the Bubble sort algorithms.
Bubble sorting involves splitting the list into two parts. They are sorted and unsorted. The smallest item in a sublist that hasn't been sorted is "bubbled." When the smallest piece of the wall is shifted, the entire wall shifts forward one space. The idea behind bubble sort was to highlight the item at the top of the list in a giant bubble. It does not matter if the highest or lowest item is bubbled. In this variant, two adjacent components are switched around based on a comparison. Since bubble sort performs a full array check, sorting a record with n elements can take up to n-1 iterations.
27. Explain the Quick sort algorithms.
The Quicksort algorithm relies on division to sort the data. The term "partition exchange sorting" is also used to refer to this technique in some contexts. The quick sort algorithm involves picking one item from an array and then rearranging the rest of the data so that it revolves around that item. This item caused the initial list to be divided in half. The "pivot" is the currently chosen option. Any items whose values are less than the pivot are shifted to the left, and those whose values are more significant than the pivot are shifted to the right when the pivot is selected. Until sub-lists containing only one item are found, selecting a pivot and dividing the list is repeated in a while loop.
28. What is DAA Programming?
Data Access Arrangements (DAAs) connect a computer and modem to a public telephone network. DAAs, called TLICs, are telephony line interface circuits (or Modules).
29. What exactly is NP-Complete?
Any other NP problem can be simplified to an NP-Complete problem in a polynomial amount of time, which means that an NP-Complete problem is just as tricky as any other problem in this category.
30. What is the Knapsack Problem in DAA?
The DAA knapsack problem is challenging in combinatorial optimization. Given a set of items with weights and values, find the optimal number of each item to include in the collection such that the sum of the weights is as tiny as possible and the sum of the values is as large as possible.
31. What is a multistage graph in DAA?
The nodes in a multistage graph are directed and weighted, and the edges between them can only go from one stage to the next (This means that there is no edge connecting the vertices of the same stage, nor is there an edge connecting a vertex of the current stage to a vertex of the stage before it.)
32. What exactly is Binary Search?
Binary search is superior to linear search. On a non-sorted data structure, however, it cannot be tested. The basis of binary search is the divide-and-conquer tactic. The binary search starts by testing the central element of the array's data. Doing this can determine whether a specific event or piece of information occurs in the first or second half. We do not need to check the second half if the object is found in the first half and vice versa if it is discovered in the second half.
33. Explain the Insertion Sort algorithms.
In both selection and bubble sorts, items are interchanged. In contrast, insertion sort does not exchange items. Like card insertion, the item is inserted into the insertion sort at the appropriate location.
Frequently asked DAA Interview Questions
34. What exactly do you mean by "optimal solution"?
We first identify the subset of the input that can satisfy the constraints to solve the input problem. A workable solution is any subset that complies with these conditions. The solution that maximizes or minimizes the pertinent variables is always the best solution to a problem.
35. Why do we study algorithms in DAA?
People who aren't familiar with the inner workings of algorithms or how to strategically use them have a clear disadvantage over tech professionals who have taken the time to study them. Participating in a web development Bootcamp designed to accelerate the development of web-based skills is one method by which you can broaden your understanding of the characteristics of algorithms.
36. Which Algorithm is used in DAA?
It takes a top-down approach and uses the divide-and-conquer strategy.
The divide-and-conquer strategy is accompanied by algorithms that consist of three steps, which are as follows: Create many additional issues stemming from the initial issue. Recursively find solutions to each of the individual subproblems.
37. What is the function of DAA instruction?
DAA is an abbreviation for decimal adjust accumulator and is used in BCD addition. The DAA instruction converts the accumulator's binary values to BCD.
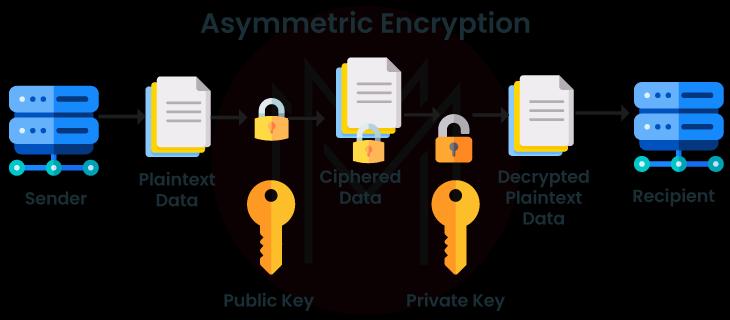
38. How does the asymmetric encryption algorithm work?
To encrypt something means transforming it from its "plaintext" form into an unbreakable "Ciphertext" form. The content is "keyed" to an algorithmic string of bits that serves as a basis for estimation in the conversion process. The more significant the key, the more possible combinations for creating the ciphertext. Most algorithms for secure communication employ fixed-length blocks of input—typically 64 bits to 128 bits in length—while others employ the stream technique.
39. What exactly is Dynamic Programming?
DP is an alternative strategy for optimal substructure problems. The optimal solution to a problem will include the answers to any subproblems that must be solved. Not all optimal solutions to individual subproblems will necessarily contribute to a complete answer. Each top-down subproblem can be tackled in any order, making the divide-and-conquer strategy very flexible.
40. What are some examples of Data Structures Applications?
This is a common data structure question asked during interviews. Expertise in various fields, including but not limited to statistical analysis, operating systems, numerical analysis, compiler design, artificial intelligence, graphics, database management, and simulation.
| Related Article: Data structures Interview Questions |
41. What exactly is the distinction between file structure and storage structure?
The access to the memory area is what sets these two types apart. The data structure stored in the computer system's memory is called the storage structure. On the other hand, the file structure is the storage structure that is stored in the auxiliary memory.
42. Which sorting Algorithm is best?
Quicksort is the most efficient sorting Algorithm, which explains why it is widely used. The first step is to choose a pivot number. This number will divide the data, with smaller numbers to its left and more significant numbers to its right.
Conclusion
We hope this article on DAA interview questions and answers will be helpful for the candidates, whether they have prior experience or are just starting in the job market. Therefore, make sure you study hard for the test and use this list of interview questions to help you get the job of your dreams at the DAA.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Hardware Design Development Training | Mar 10 to Mar 25 | View Details |
| Hardware Design Development Training | Mar 14 to Mar 29 | View Details |
| Hardware Design Development Training | Mar 17 to Apr 01 | View Details |
| Hardware Design Development Training | Mar 21 to Apr 05 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .


