Information security is one of the most crucial aspects of data communication. If you want to transfer sensitive data, you must send them with the highest level of protection so that others cannot access and read the data. Information security is highly needed in military applications. It is also much-needed in transferring highly-confident commercial and scientific information.
On this note, cryptography and its algorithms play a crucial role in information security. RSA is one of the cryptographic algorithms with which you can encrypt and decrypt original messages or plaintext effectively. This is why the demand for information security professionals is on the rise nowadays. Candidates with sound knowledge of cryptographic techniques and RSA algorithms are highly-sought in the job market.

This blog post aims at providing you with the RSA interview questions and answers in a crisp way. This blog has split the questions into three categories:
Top 10 RSA Frequently Asked Questions
- What is Cryptography?
- Compare Symmetric Encryption and Asymmetric Encryption.
- What is the RSA algorithm?
- What are the advantages and disadvantages of RSA?
- What do you mean by Two Factor Authentication (2FA)?
- Compare RSA and DSA.
- Can you brief the different RSA vulnerabilities?
- What is the purpose of applying Padding in RSA?
- What different attacks can be made against RSA encryption?
- What is the advantage of using the Euclidean algorithm in ESA Encryption?
RSA Interview Questions For Freshers
1. What do you mean by SIEM?
SIEM is the short form for Security Information and Event Management. With SIEM, you can monitor and analyze real-time events accurately. Also, you can log security data for compliance and make informed decisions. Simply put, you can completely protect networks, data, and other sensitive resources from potential threats and vulnerabilities.
| If you want to enrich your career and become a professional in RSA, then enroll in "RSA Archer Training". This course will help you to achieve excellence in this domain. |
2. What is Cryptography?
Cryptography is one of the powerful methods used to perform secure data transfer. Encryption and decryption are the two crucial techniques used in cryptography to encode and decode data, respectively. Cryptography allows only the sender and receiver to read the data. You must note that you can perform encryption and decryption using various algorithms based on the applications and requirements.
| Related Article: Cryptography Tutorial |
3. What are the types of Cryptography?
There are three types of cryptography as follows

- Secret Key Cryptography: It is also called symmetric key cryptography. It uses a single public key. Keeping the public key safe is essential in this method; otherwise, attackers can easily misuse it. Blowfish is one of the secret key cryptographic methods.
- Public Key Cryptography: It is also known as asymmetric key cryptography. It uses two keys such as the public key as well as the private key. This method is more secure than symmetric cryptography since it uses a private key. RSA algorithm is one of the example of asymmetric key cryptography.
- Hash Functions: This cryptographic technique doesn’t use any key. This technique generates a hash value based on the plaintext and adds to the plaintext. As a result, no attacker can crack the plaintext easily.
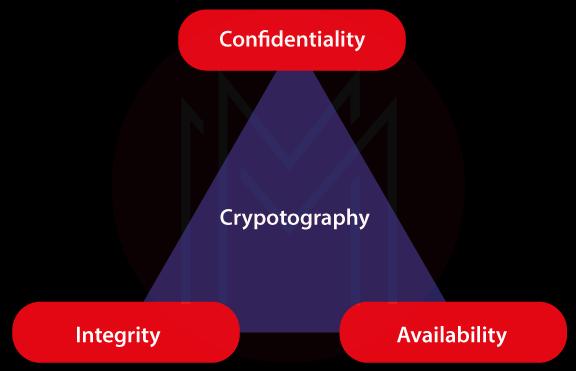
4. What do you mean by CIA Triad in RSA?
- CIA refers to the Confidentiality, Integrity, and Availability of the data encrypted by the RSA algorithms.
- Regarding confidentiality, RSA ensures that only authorised persons can access the data being transferred.
- Regarding Integrity, RSA provides that the actual information is not changed even after the application of encryption and description processes.
- Regarding availability, RSA ensures that users can access the encrypted data anytime.
5. What do you understand from Encryption and Decryption?
- When we convert plaintext or actual messages into ciphertext, it is known as encryption. Note that ciphertext will usually be in the unreadable form.
- On the contrary, converting the ciphertext into the actual message or plaintext is known as the decryption process.
6. What are Public Key and Private Key?
- When it comes to the public key, we use it for both encryption and decryption. This key is known as the secret key. Both sender and receiver of the message will have the secret key.
- When it comes to the private key, we use one key for encryption and another key for decryption. The key that we use for encryption is known as the public key. The key that we use for decryption is referred to as a private key. Only the receiver of the message will have the private key.
7. What is a Session Key?
A session key is used for both encryptions as well as decryption. In a way, a session key is also a public key. But the significant thing is that you can only generate a session key for a specific session. In other words, a session key is a temporary key that becomes invalid once the session is over.
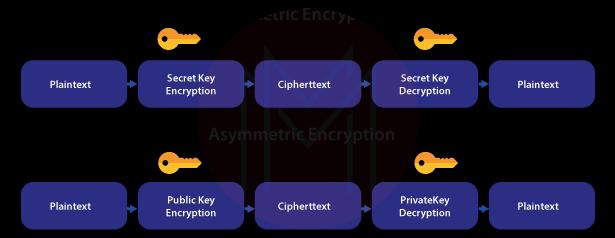
8. Compare Symmetric Encryption and Asymmetric Encryption.
- In symmetric encryption, we use the public key. It means we use the same key for both encryption and decryption. The public key is also known as the secret key. That’s why it is called secret key encryption.
- In asymmetric encryption, we use the public key as well as the private key. It means we use a public key for encryption and a private key for decryption.
- Know that plaintext is the actual or original information, whereas ciphertext is the encrypted information.
9. What is the RSA algorithm?
RSA stands for Rivest, Shamir, and Adleman. They are the computer scientists who developed the RSA algorithm. RSA algorithm is one of the cryptographic algorithms with which you can make secure data communication. Also, it is an asymmetric algorithm that uses both public and private keys. RSA Algorithm performs two essential tasks – one is generating keys and another is encrypting as well as decrypting information.

| Related Article: What is RSA Algorithm? |
10. How does an RSA algorithm work?
- First, the RSA algorithm generates public and private key pairs.
- Next, the algorithm uses encryption and decryption functions to create ciphertext and retrieve plaintext.
11. What do you mean by Two Factor Authentication (2FA)?
2FA is the two-step verification process that you can use for making secure data transfer. In other words, this process uses two authentication factors to perform a secure data transfer. Usually, a password may be one of the authentication factors, and another would be a security token or biometric. Here, the biometric can be a fingerprint or facial scan. Providing additional security mechanisms is the key focus of 2FA so intruders cannot easily access the data being transferred.
12. What do you understand by RSA SecureID Token?
It is a robust security mechanism used to perform two-factor authentication. This mechanism generates authentication codes for every RSA token. The authentication codes are sent to receivers through SMS, email, or other modes. The receivers will enter the codes to ensure authentication. This authentication process is completed in a short span for every token. As a whole, this mechanism ensures reliable and secure information transmission.
13. What do you mean by RSA Signature?
It is a digital signature scheme, which includes inserting a digital signature as well as asymmetric keys. Three steps are involved in implementing the RSA signature mechanism: RSA signing, key generation, and verifying the signature. RSA signature mechanism effectively uses modular exponentiations, discrete algorithms as well as RSA algorithms for its processes.
14. What is the role of RSA SecureID authentication agents?
It is the software that directs the requests of users to the RSA authentication manager server for authentication. It allows only authorized users to access applications securely.
15. What is SSL Encryption?
SSL stands for Secure Sockets Layer. It is an encryption-based internet security protocol. With this protocol, you can ensure authentication, privacy, and data integrity of data transfer on the internet. In short, SSL provides privacy through the encryption process. It ensures authentication through a handshaking process to verify the authenticity of the sender as well as the receiver. SSL employs the digital signature method to ensure the integrity of the data being transferred.
16. What do you understand by System Hardening?
Applying system hardening techniques reduce risks and vulnerabilities in computer systems significantly. It is the process of strengthening the security of data and other resources through effective tools and best practices. You can apply hardening techniques in many ways. For example, you can frequently audit security systems, eliminate unnecessary accounts, quickly patch vulnerabilities, and so on.
Know that there are many types of system hardening, such as Application hardening, server hardening, Operating System hardening, database hardening, endpoint hardening, and network hardening.
17. What do you mean by Defense in Depth?
The DiD or Defense in Depth is one of the powerful mechanisms used in cyber security to secure data and systems. DiD is a set of defense layers leveraged in systems to protect them from various risks and vulnerabilities. The multiple defense layers can include firewalls, intrusion detection systems, malware scanners, integrity audits, encryption methods, etc. Simply put, you can tightly close all the gaps in the security arrangements in systems using this method.
18. Can you list out some other asymmetric algorithms?
- ECDSA- Elliptic Curve Digital Signature Algorithm
- Diffie- Hellman Algorithm
- PGP- Pretty Good Privacy Algorithm
19. What is salting in cryptography?
It is the process of adding unique strings of characters to a password before making a hash. Salting is performed to increase the strength of the password. Here, the string of characters is known as salts. You can either prefix or suffix a password with the salt.
It is a simple but essential note that a good salt will usually be long and unique.
20. What are Euclidean Algorithms?
A Euclidean algorithm helps to find the Greatest Common Divisor (GCD) of two numbers. If you want to get the GCD of two numbers, you need to factorize the numbers and then multiply the common prime factors. Note that the extended Euclidean algorithm is another type of Euclidean algorithm.
21. What is DES in Cryptography?
DES is the short form of Data Encryption Standard (DES). Like RSA, it is yet another cryptographic algorithm that encrypts and decrypts data using the block-cipher method. This algorithm uses 48-bit keys to convert the 64-bit blocks of the plaintext into cipher text.
22. What are the advantages and disadvantages of RSA?
Advantages
- You can securely send messages
- You can improve the authenticity of messages
- Key creation and distribution are simple
Disadvantages
- RSA uses only asymmetric algorithms. If you need to use both symmetric and asymmetric encryption for specific applications, then RSA won’t be helpful.
- Significant efforts are required to decrypt messages on the receiver’s end
RSA Interview Questions For Experienced
23. Compare RSA and DSA.
| RSA Algorithms | DSA Algorithms |
| RSA is the cryptographic algorithm | DSA is the Digital Signature Algorithm |
| It is used for secure message transmission | It is used for creating digital signatures and verification |
| It works based on the product of two large prime numbers | It works based on discrete algorithms and modular exponentiation |
| Decryption is slower than DSA | Decryption is faster than RSA |
| Encryption is faster than DSA | Encryption is slower than RSA |
24. What is the difference between RSA and the Diffie-Hellman algorithm?
| RSA | Diffie-Hellman |
| It works based on asymmetric key encryption. So RSA generates both public and private keys. | It works based on symmetric encryption. So the same key is used for both encryption and decryption. |
| Anyone can generate a public key, but only authorised persons can use the private key. | Only authorised persons can access the keys. |
| RSA uses integer factorisation, which is more vulnerable when the integer is short. | DSA uses discrete logarithms,which is more vulnerable |
25. In what ways can attackers break RSA security?
Attackers can break RSA security in the following days.
- Small factors
- Elliptic Curve Method
- Fermat factorization
- Fault Injection
- Known Partial Bits
- Weak Entropy
- Weaknesses in Signatures
- Side Channel Attacks
- Shared Bits
- Number Field Sieve
26. Where will you use RSA encryption?
- You can use RSA encryption to secure data transfers using Transport Layer Protocol (TLP).
- You can use RSA encryption in Virtual Private Networks (VPN), web browsers, email services, and other communication channels.
27. Can you brief the different RSA vulnerabilities?
Following are the RSA vulnerabilities that will challenge the effectiveness of the RSA algorithm.
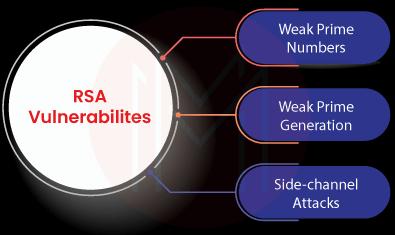
- Weak Prime Numbers: Creating weak prime numbers will end in weak RSA encryption. So, you must use powerful random number generators to create strong prime numbers.
- Weak Key Generation: If you choose very close prime numbers, it weakens the keys. Similarly, if one of the private key pairs is very small, it weakens the key and quickly increases the chances of cracking.
- Side-Channel Attacks: In this attack, attackers take control of the system that performs the RSA encryption. Also, the attackers use branch prediction analysis to track the key and access the data. As a result, they could easily access the message encrypted.
28. What should be the size of the keys to making a secure data transfer using RSA encryption?
The keys must have at least 1024 bits. You can use 2048 and 4096 bits keys if you want to send highly-sensitive messages.
29. What do you understand by ECDHE-RSA?
ECDHE refers to Diffie-Hellman Ephemeral that uses Elliptic Curve cryptography. In this RSA method, both the server and the browser share a key to encrypt the web traffic. Once the key is discarded, the contents of the web traffic will no longer be available. Mainly, you can prevent man-in-the-middle attacks using this method.
30. Can you replace RSA with AES?
We cannot replace RSA with AES. This is because we can use RSA to encrypt messages. You cannot use RSA for encrypting arbitrary data.
31. What is the purpose of applying Padding in RSA?
We apply padding to increase the security of RSA-encrypted data. In this process, random data is added to the actual message to make the RSA-encrypted data more secure and unbreakable.

Optimal Asymmetric Encryption Padding (OAEP) is one of the padding methods used to add data to the plaintext. The random data is added to the message before the encryption and removed after the decryption.
32. Compare Encryption and Hashing.
In encryption, you encrypt the plaintext and convert it to ciphertext. If you want the plaintext back, you can decrypt it.
When it comes to hashing, you can encrypt the plaintext, but you cannot decrypt it.
Advanced RSA Interview Questions
33. Do you think that quantum computing will affect RSA?
Know that Quantum computing uses Shor's algorithm. This algorithm quickly solves integer factorizations, discrete logarithms, as well as elliptic-curve discrete logarithms. It can factorize numbers much faster than other algorithms. When it comes to RSA, if the prime number factorization is resolved, RSA encryption gets failed and allows attackers to access the data easily. In short, quantum computing will definitely affect the future of RSA.
34. How does RSA encryption overcome Brute Force attacks and Dictionary attacks?
- Attackers can predict a large number of possible keys for the RSA keys. But it will need a long time to identify the correct key. That's why brutal force attacks will fail if it is made against RSA encryption.
- Generally, RSA keys don’t contain numeric as well as characters. So, dictionary attacks can’t break RSA encryption.
35. What do you mean by Cryptographic Blinding?
When it comes to side-channel attacks, attackers observe the computation time, power consumption, and other characteristics of the systems where the algorithms are running. Besides, the attackers may have some inputs and features of the algorithms with which they try to crack the keys.
Blinding is used to prevent side-channel attacks made on asymmetrically encrypted messages. It is essential to note that we can avoid this attack by adding one-off values while encrypting the information.
36. What are the different attacks that can be made against RSA encryption?
- Short Message Attack: If an attacker knows any block of the original text, it is easy for them to decrypt the ciphertext. You can avoid this attack by applying padding in the original text.
- Cycling Attacks: In this attack, attackers try all the possible permutations to decode the cipher text.
- Unconcealed Message Attack: Sometimes, even though you encrypt the original message, the cipher text may seem like the original text. So you need to verify the ciphertext every time you generate it.
- Factorisation Attack: If attackers come to know the private key through the p, q, and n values of the RSA algorithms, then they can quickly access the original message. So you must create long 'n' values to avoid this attack.
37. What is the advantage of the public key over the private key?
Generating a public key is much simpler than creating private keys. Not only that, public keys allow digital signatures, which in turn simplifies authentication.
38. What is the advantage of using the Euclidean algorithm in ESA Encryption?
Generally, the ESA encryption process consumes a higher level of computing resources. When we use the extended Euclidean algorithm for RSA encryption, it avoids negative integer operations. As a result, there is a significant reduction in the complexity and computing resources required for RSA encryption.
39. How can you generate RSA Keys?
We can generate RSA keys using two methods, known as the Cryptomath method and the Rabin Miller method.
40. How can you effectively generate large prime numbers for RSA algorithms?
As you know, the RSA algorithm works based on the concept that the prime numbers must be tough to factorize. If the size of the prime number is large, then the keys generated will be so strong. And the keys must be between the size of 1024 to 2048 bits. The following method will help you to create large-sized prime numbers.
- First, choose a random number.
- Check whether the number is not divisible for the first few hundred prime numbers.
- Then, apply a few iterations of Rabin-Miller primality tests
- Finally, select the prime number within the acceptable error rate.
Conclusion
Well! We hope that now you will be able to crack your RSA interviews with courage and confidence. This blog covered all about cryptography, algorithms, encryption, decryption, and many more. We advise you to read the RSA interview questions and answers frequently to keep your knowledge fresh and green. It would help you to attend RSA interviews and deliver answers sharply. We wish you the best of luck for your success and colorful career.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| RSA Archer Training | Mar 03 to Mar 18 | View Details |
| RSA Archer Training | Mar 07 to Mar 22 | View Details |
| RSA Archer Training | Mar 10 to Mar 25 | View Details |
| RSA Archer Training | Mar 14 to Mar 29 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .


