Since the dawn of computing, the RSA Algorithm has been a reliable security source, and it continues to establish itself as a key tool in cybersecurity. Learning this helps you understand how many aspects of our online lives are kept secure.
Therefore, this Article will teach you everything you need to know about how RSA works, its advantages, and many more. Before diving into the RSA algorithm directly, we must first understand asymmetric encryption.
| What is RSA Algorithm? - Table of Contents |
What Is Asymmetric Encryption?
In Asymmetric Encryption, there are two different keys, one for encrypting data and the other for decrypting it. The public key is used for encryption, and the private key is used for decryption. Of course, the receiver must be the rightful owner of both keys.
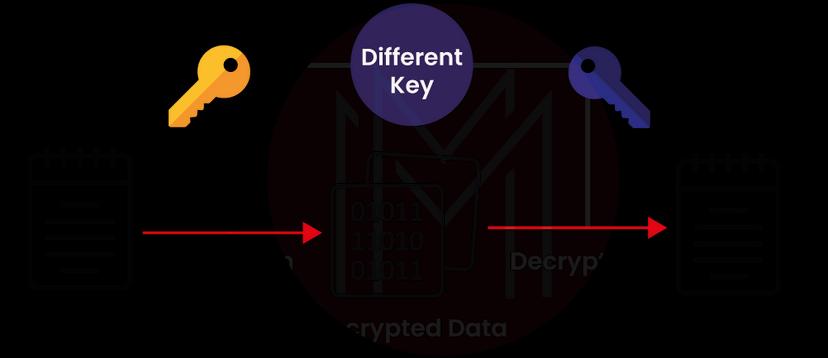
As seen in the picture above, using separate keys for decryption and encryption has made it possible to avoid key exchange, which is a problem with symmetric encryption.
For instance, if Bob needs to receive a message from Alice, Saurav must own both private and public keys.
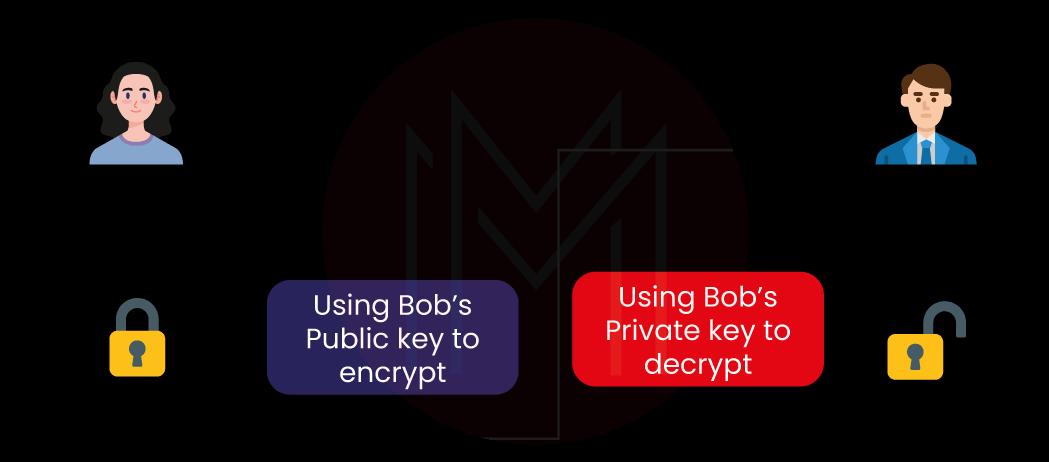
The following steps were taken to create the image above
Step 1: First, Alice encrypts the message using Bob's public key.
Step 2: This step involves sending Bob an encrypted message.
Step 3: Bob uses his private key to decrypt the message.
As a result, there is no longer a need for the sender and recipient to exchange any secret keys, narrowing the window of opportunity for exploitation.
Now that you are aware of how asymmetric encryption works, you can examine the design of the digital signature architecture.
| If you want to enrich your career and become a professional in RSA Algorithm, then enroll in "RSA Archer Online Training". This course will help you to achieve excellence in this domain. |
What Are Digital Signatures?
Files and Documents can be verified and authenticated using digital signatures. This is essential to preventing digital alteration or forgery and tampering during official documents' transmission.
With one slight exception, they operate on the public key cryptography architecture. A public key is typically used for encryption in an asymmetric key system, whereas a private key is typically used for decryption. With digital signatures, the situation is the opposite. The signature is encrypted with the private key and decrypted with the public key. Since the keys complement one another, decrypting the file with the public key verifies that the signature was created using the right private key, hence confirming the signature's authenticity.
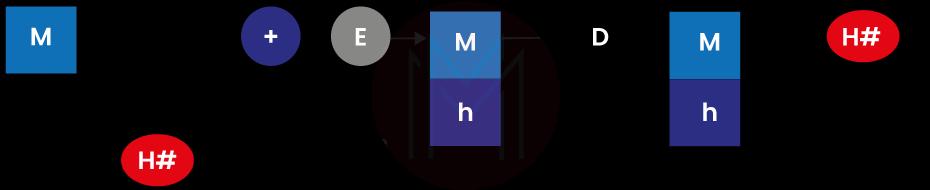
h - Hash digest
M - Plaintext
H - Hash function
E - Encryption
‘+’ - Bundle both plaintext and digest
D - Decryption
The entire procedure, from the signing of the key to its verification, is depicted in the graphic above. Go through each stage, then, to fully comprehend the process.
Step 1: M stands for the initial message. Prior to transmission, the data is first processed through a hash function designated by the numeral H#.
Step 2: The message and the hash digest, indicated by the letter h, are then combined, and the message is encrypted with the sender's private key.
Step 3: The recipient receives the message and digests it in an encrypted bundle, decrypted using the sender's public key.
Step 4: Once the message has been decrypted, the same hash function (H#) is used to construct the hash digest once more.
Step 5: The recently generated hash is compared to the hash that was received in the decrypted bundle. If they coincide, the accuracy of the data is confirmed.
The above methodology can be applied in two ways that are considered industry standards: DSA Algorithm and RSA Algorithm.
Despite sharing the same objective, they take distinct approaches to encryption and decryption. Look at the RSA algorithm, which is the subject of today's discussion, now that you are aware of how it is intended to work.
What Is the RSA Algorithm?
Ron Rivest, Leonard Adleman, and Adi Shamir developed the public-key signature algorithm known as RSA. It was first introduced in their 1977 publication and uses logarithmic functions to keep the working complicated enough to fend off brute force attacks while remaining streamlined and quick to implement. The graphic below demonstrates how it uses the RSA approach to validate digital signatures.
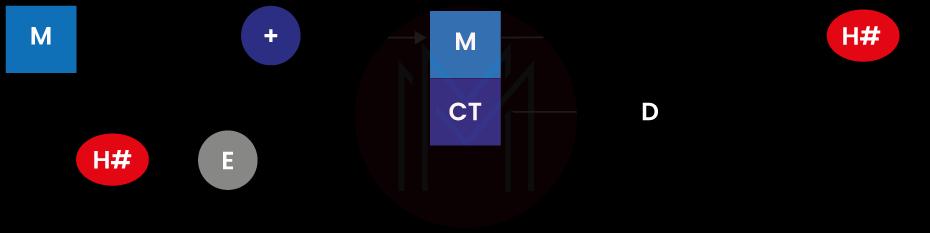
Along with handling the verification of digital signatures, RSA can also decrypt and encrypt generic data to enable secure data sharing. The RSA algorithm's full process is depicted in the graphic up top. The following part will explain it in more detail.
How does RSA Work?
The choice to encrypt using the private or public key offers RSA users a wide range of benefits. If the material is encrypted using the public key, it must be decrypted using the private key. When the data receiver sends the data sender their public key, this is ideal for delivering sensitive data via a network or Internet connection. Sensitive data is then encrypted by the data sender using the recipient's public key before being sent. Only the owner of the private key can decrypt the sensitive material because the public key encrypted the data. Therefore, even if the data were intercepted in transit, only the intended recipient of the data may decrypt it.
Encrypting a message with a private key is the alternative asymmetric encryption technique with RSA. In this illustration, the sender of the data uses their private key to encrypt the data before sending it together with their public key to the recipient of the data. The data can then be decrypted by the receiver using the sender's public key, allowing the recipient to confirm that the sender is who they claim to be. The data could be intercepted and read in transit using this method, but the real goal of the encryption is to establish the sender's identity. The recipient would be aware that the data had been altered in transit if it had been stolen and altered while in the route since the public key would be unable to decrypt the new message.
The technical aspects of RSA are based on the assumption that while it is simple to multiply two sufficiently large numbers together, it is highly challenging to factorize the result back into the original prime numbers. Two numbers are used to generate the public and private keys, one of which is the sum of two huge prime numbers. The same two prime numbers determine the values of both. The typical length of an RSA key is 1024 or 2048 bits, making it very difficult to factorize them, though 1024-bit keys are rumored to be breakable soon.
| Related Article: RSA Interview Questions |
Who uses RSA Encryption?
As was previously mentioned, RSA encryption is utilized for a variety of purposes. Digital signing for codes and certificates is one of them. By signing a public key with the private key of the key pair owner, certificates can be used to confirm who the public key belongs to. This establishes the owner of the key pair as a reliable source of information. The RSA algorithm is also used for code signing. The code is signed using the creator's private key to make sure the owner is not delivering erroneous or harmful code to a buyer. This demonstrates that the code has not been maliciously altered while in transit and that the code's author has confirmed that the code performs as promised.
Transport Layer Security (TLS) and RSA were combined to protect communications between two people. RSA has been used in the past or currently by other well-known products and algorithms, such as the Pretty Good Privacy algorithm. RSA has also been utilized by email services, web browsers, virtual private networks (VPNs), and other communication channels. The handshake between the two parties in the information exchange will be implemented by VPNs using TLS. To confirm that both parties are who they claim to be, the TLS Handshake uses the RSA encryption method.
RSA in Data Encryption
It uses the opposite key set while encrypting and decrypting generic data with RSA. In contrast to signature verification, it encrypts data using the recipient's public key and decrypts it using the recipient's private key. Therefore, in this situation, no keys need to be exchanged.
When it comes to RSA cryptography, there are two major parts
- Key Generation: It is the process of creating the keys that will be used to encrypt and decode the data that will be transferred.
- The Function of Encryption and Decryption: This procedure needs to be followed when data needs to be recovered after being scrambled.
In our upcoming sub-topic, each of these actions will be clear to you.
Steps in RSA Algorithm
Examine the entire process, from developing the key pair through encrypting and decrypting the data while bearing in mind the illustration above.
1. Key Generation
Prior to using the functions to create your ciphertext and plaintext, you must first create your public and private keys. They make use of the following parameters and variables, which are all described below:
- Pick two enormous prime numbers (a and b)
- Figure out n = a*b and z = (a-1)(b-1)
- Pick a number e such that 1 < e < z.
- Determine d = e-1mod (a-1)(b-1)
- Private key pair bundles are available as (n,d)
- Public key pair bundles are available as (n,e)
2. Encryption/Decryption Function
Once you construct the keys, you pass the parameters to the functions that compute your plaintext and ciphertext using the right key.
- If m is the plaintext, then ciphertext equals me mod n.
- Plaintext = cd mod n if the ciphertext is c.
You can use the example where a = 17 and b = 13 to comprehend the aforementioned processes better. Since it satisfies the condition: 1 < e < (a-1)(b-1), the value of e can be 5.
N = a * b = 221
D is equal to e-1mod(a-1)(b-1)=29
Pair of public keys: (221,5)
Pair of private keys: (221,29)The encryption process can be carried out using the equation me mod n = 82 if the plaintext(m) value is 10.
This ciphertext(c) must be decrypted back to the original data using the equation cd mod n = 29.
Now you may look at the qualities that set the RSA algorithm apart from its rivals in the benefits section.
Advantages of RSA
- No Key Sharing: Since RSA encryption uses the recipient's public key, receiving messages from others does not need to share secret keys.
- Proof of Owners Authenticity: Because the key pairs are linked together, a receiver cannot intercept a message if they do not have the proper private key to decrypt the data.
- Faster Encryption: Compared to the DSA method, encryption is completed more quickly.
- Data Cannot Be Modified: Since tampering with the data would change how the keys were used, the data would be impenetrable in transit. Additionally, the information cannot be decrypted using the private key, alerting the recipient to manipulation.
| Explore RSA Archer Sample Resumes! Download & Edit, Get Noticed by Top Employers! Download Now! |
Conclusion
You now know the value of asymmetric cryptography, how digital signatures operate, how the RSA workflow works, and why it is better than others. We hope this blog helps you become more familiar with how the RSA algorithm is applied in today’s industry.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| RSA Archer Training | Mar 07 to Mar 22 | View Details |
| RSA Archer Training | Mar 10 to Mar 25 | View Details |
| RSA Archer Training | Mar 14 to Mar 29 | View Details |
| RSA Archer Training | Mar 17 to Apr 01 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .


