In this growing and fast-paced world, there is a need for effective resource-sharing management with a faster response. It has become quite important for organizations to get a system that authorizes users, effectively allocates resources and passes on database requests by applications to the appropriate managers. In these aspects, CICS, or Customer Information Control System helps organizations. It is a middleware made to support high-volume, rapid online transactions. CICS replaces the functions and structure of an operating system, specifically regarding communication with numerous terminal devices.

Let us look at some facts related to CICS:
- CICS originated in the United States at a Development center of IBM in Des Plaines, Illinois.
- There was a formalization of CICS using Z notation in collaboration with the Oxford University Computing Laboratory.
- It won a Queen's Award for technological achievement.
- A version of CICS produced by IBM in the 1980s came to be known as "Command-level CICS."
Now we will go through some FAQs about CICS Interviews. Then we will move on to the CICS Interview questions and answers separately for each of the following-
Top 10 Frequently Asked CICS Interview Questions
1. What is the need for CICS translators?
The function of the COBOL compiler depends upon the Integrated CICS translator when one uses it from the compiler option. The integrated CICS translator is put into use by the compiler to interact with CICS statements that are found in the source program. The translator then acts on the CICS statements before going back and telling the compiler what native language statements are supposed to be produced. Comparing Integrated Translator to Separate translator, there are no constraints in managing statements included in CICS and native Cobol in the Source Program.
2. What CICS command will you use to access the current date and time?
ASKTIME is the command one should use if one wants to access the current date and time.
| If you want to enrich your career and become a professional in IBM DB2, then enroll in "IBM DB2 Training". This course will help you to achieve excellence in this domain. |
3. How would you differentiate EXEC CICS XCTL and the command of EXEC CICS LINK?
The main difference is that the XTCL command transfers the control to an application that lies at the same logical level and does not expect to control it back. On the other hand, the LINK command passes the control to an application program to the next logical level and expects a control back.
4. How would you define CICS?
CICS, which stands for Customer Information Control System, is software created by IBM that keeps track of communications. Batch and time-sharing are IBM's mainframe operating systems.
5. What do you understand by a CICS task?
A CICS task is essentially a single-time CICS transaction execution. When the enter key is hit after entering the key into the transaction, this procedure kickstarts. Until the software returns control to CICS, the execution process is still in progress.
6. Draw the differences between PCT and FCT.
Program Control Table, or PCT, collects all transaction IDs linked to their related programs. Whereas the FCT, which stands for File Control Table, contains an exhaustive list of all the files utilized by CICS, together with information on their status and record length.
7. How would you initiate a CICS transaction?
The process to start a CICS transaction is very simple. You can initiate by pressing the CLEAR button to clear the screen. Following that, you enter the transaction identifier, either by itself or follow it up with data on the screen's command line.
8. What do you understand by EIB?
Every job in a command-level environment has a control block known as the EXEC interface block (EIB) associated with it, apart from the usual CICS control blocks. All fields in the EIB can be accessed by name by an application program.
9. Can you use dynamic calls in CICS?
Yes. If one wants to use dynamic calls in CICS, one must specify the call function in a PPT, and the calling program must use the CALL identifier.\
10. What is the most important aspect of CICS?
CICS primarily deals with the creation and execution of web applications. It makes a seamless communication channel through the terminal for structured data to be received and sent. The accessibility of databases and the files they contain is one of the most important features of CICS.
CICS Interview Questions and Answers for the freshers:
1. What is the full form of CICS? What is it primarily used for?
CICS is an acronym for the term Customer Information Control System. It is a system control software in charge of online transactions of IBM management. It also assesses the telecommunication from IBM. The mainframe OS of IBM is primarily time-sharing as well as batch. CICS is a kind of processing that was mainly started by using a single request that one or more objects can also effectuate.
2. What are the essential requirements of an Integrated CICS translator?
Following are the reasons Integrated CICS translators are used:
- You will need it to work with a COBOL compiler. If you select the Fromcompiler option, it will work with the Integrated CICS translator.
- The compiler contacts the integrated CICS translator when it encounters CICS statements in the source program.
- The translator, after that, acts on the CICS statements before returning to the compiler to inform it of the native language statements it should produce.
- As opposed to a Separate Translator, there is no restriction in an Integrated Translator.
- Apart from that, it can manage the source program's embedded CICS statements and native COBOL statements.
3. How would you differentiate between call and link in CICS?
The most important difference between call and link in CICS is that when it comes to calling, whenever any changes or alterations are made to the program, one also needs to compile the calling program. The same is not necessary when it comes to links.
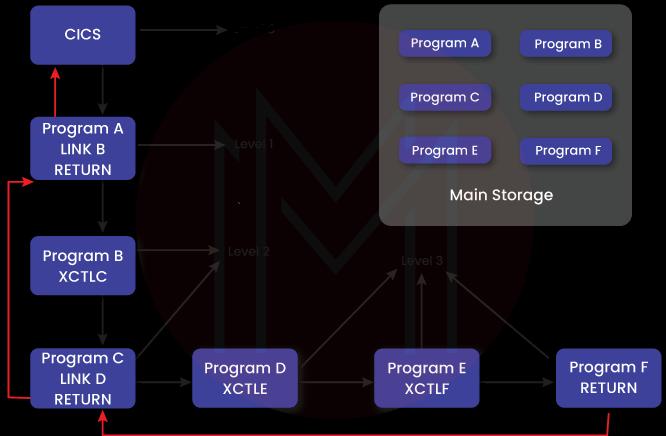
4. How would you differentiate START from XTCL?
One can initiate a new task with the help of the START command. It is a command specifically for interval control. Whereas the XCTL command is used to transfer control to a program running within the same job, it is a command specifically for program control
| Related Article: Oracle DBA Tutorial |
5. What exactly is CEMT?
CICS Execute Master Terminal is the full form of CEMT. Its purpose is to serve as a transactional ID for the system, and it is primarily used to check on and change the status of CICS environments and other system processes. Transactions, tasks, files, programs, etc., may all be managed with ease because of CEMT. One can also change the status of the resources with CEMT's help. By entering CEMT and clicking ENTER, we can view all available possibilities.
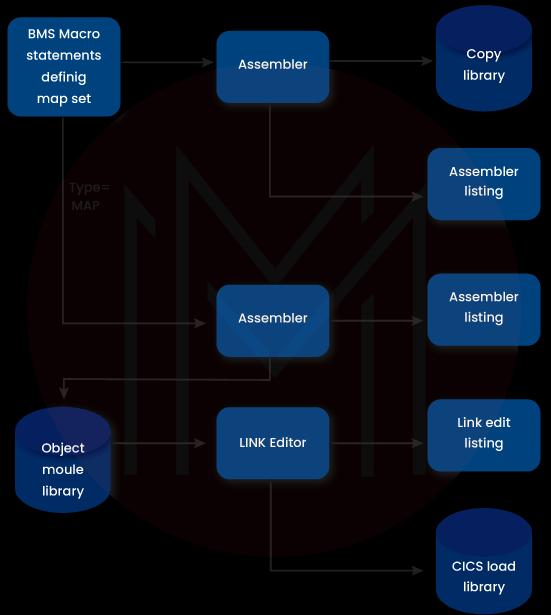
6. What is BMS in the context of CICS?
CICS uses BMS or Basic Mapping Support to define and format the screen. The screen so defined is referred to as MAP. The collection of it is called the Mapset.
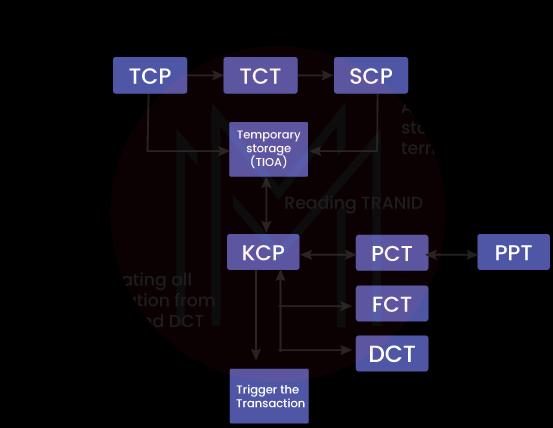
7. What are some of the most important control tables regarding CICS?
Some IBM-supplied control tables that CICS uses need to be updated regularly with the application information. Here is the list of some of the most important control tables:
- TCT: Terminal Control Table, or TCT, is a storehouse of terminal IDs connected to the present CICS region. It recognizes all the incoming data from the terminal.
- PCT: Program Control Table or PCT consists of the matching program names or IDs. It also contains the Transaction IDs or TRANSID. A distinct Transaction ID, or TRANSID, is in place for each PCT table.
- PPT: Processing Program Table, also known as PPT, consists of information such as the name of the application or Mapset, Main storage address, Language, Size, Load library address, Task Use Counter, etc. There is an appearance of a distinct Program or Mapset name in every PPT table.
- FCT: File Control Table, also called FCT, consists of file names, type, record length, and other related features. Every file used by a CICS program needs to be declared in FCT, and their opening and closing occur in CICS.
8. What do you mean by COMMAREA, and what are its advantages?
The most popular and concise name for a communication area happens to be COMMAREA. It is the name of the data area where information or data is stored and transmitted between programs. It serves as a data transmission medium between various programs loaded by a group of transactions or a single transaction. COMMAREA is primarily a temporary storage place. To provide information back to the program that performs the Transaction ID so that the user may utilize it when performing that transit, COMMAREA is typically used in parallel with the TRANSID option. The longest piece of data that can transit over COMMAREA can go up to 64K.
9. How would you differentiate tasks and transactions in CICS?
In the context of CICS, the primary difference lies between task and transaction because many users can invoke a transaction at once, but each user has to initiate their task.
10. What are some of the most commonly used CICS programs?
Here are some of the most commonly used CICS programs:
- Storage Control Programs
- Task Control Programs
- File Control Programs
- Terminal Control Programs
11. What do you understand by the term TRANSID?
TRANSID is an acronym for the term transaction identifier. Four letters in this character code can be used to invoke a task in CICS.
12. What BMS options do you use in CICS?
Minimum, Standard, and Full are the 3 BMS options used in CICS.
13. What will be the attribute values of the Stopper and Skipper fields?
We can make use of ASKIP for the attribute value of the Skipper field. When it comes to the stopper field, we can make use of PROT.
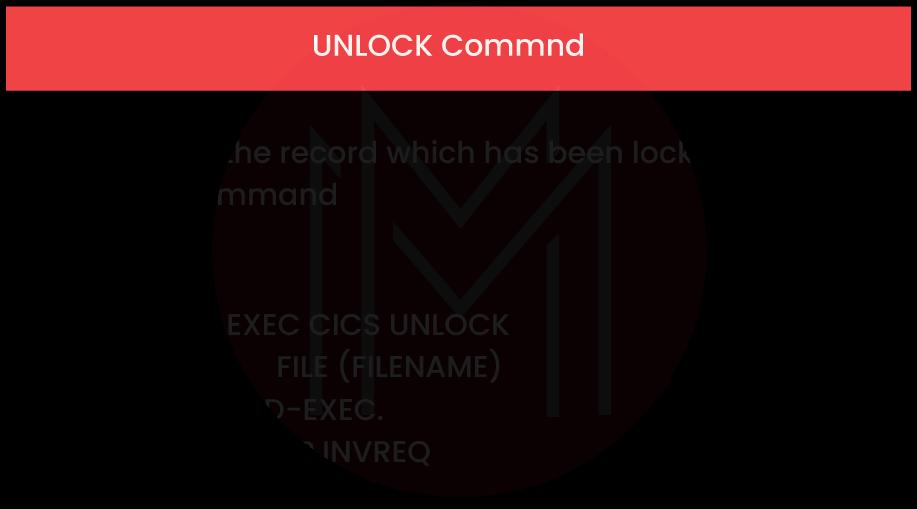
14. Which command will you use to release a record where you gain exclusive control?
We can utilize the EXEC CICS UNLOCK END-EXEC command to release a record where you gain exclusive control.
15. What processes can be utilized to make a MAP in CICS?
There are three types of processes one can utilize to create a MAP in CICS, namely, DFHMDF, DFHMSD, and DFHMDI.
CICS Interview Questions and Answers for experienced professionals:
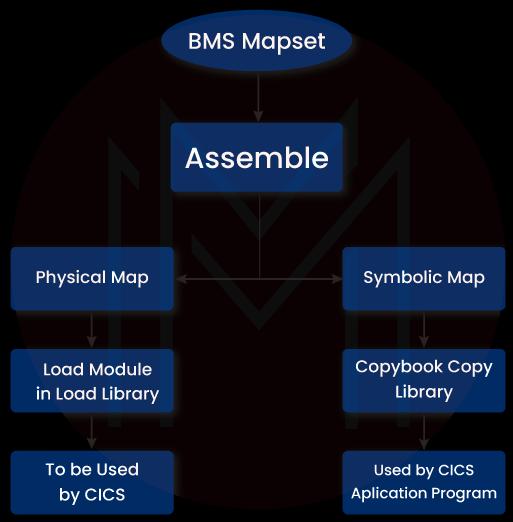
1. What do you understand by the term mapset?
Mapset is a collection of edited and linked maps that form a load module. It must consist of a PPT entry with names starting from one to seven chars.
2. What do you understand by the term MDT? What is the purpose of FRSET and FSET when it comes to MDT?
Modified Data Tag is known by its acronym MDT. During the execution of an input operation, MDT is put to use. When you alter a field's value on the screen, MDT acts like a bit of an attribute byte. Flag Reset is known by its acronym FRSET. It is used mainly to reset MDT and disable the modified data tag in all the fields on the screen's attribute bytes. An altered data tag that has been turned on once—by the user or the program—continues to remain on until expressly turned off, even across multiple screen broadcasts. FSET, however, activates the changed data tag. FSET, on the other hand, activates the altered data tag. To ensure that MDT sends out the field, it is put to. During an output operation, FSET is utilized. The user may update the field if you don't mention this.
3. How would you classify all the CICS programs?
One can classify CICS programs into the following types:
- Conversational Programs
- Pseudo Conversational Programs
- Non-conversational programs
4. What is the main difference between INTO and SET options regarding EXEC CICS RECEIVE MAP command?
The information collected and stored in TIOA is transferred into the designated, reserved space in CICS using the INTO option. Moreover, the address of the TIOA to the designated BLL cell or "address-of" a linkage section is also returned to the original position with the use of the SET option.
5. When using multiple maps, how does one determine the storage in the symbolic map?
If there are multiple maps in usage and one wants to determine the storage in the symbolic map, then the first and foremost thing to be done is the largest map.
6. What do you mean by the term Multi-Region Operation?
The way that several CICS address spaces inside a single CPU may communicate and share resources is possible with the help of MRO or Multi-Region Operation.
7. What are the primary differences between PCT and FCT?
The acronym PCT in the context of CICS stands for Program Control Table. A comprehensive collection of transaction IDs, along with their appropriate related applications, altogether make up for the list of PCT. On the contrary, FCT is the acronym used for File Control Table. It consists of a comprehensive list of all the files that CICS uses and information on their status and record length.
8. What are some primary transaction uses in the context of CICS?
- A transaction takes up the work to initiate or complete a certain task. Transaction serves as a distinctive identity. A transaction can be started simultaneously with several systems simultaneously, but not simultaneously from two separate systems.
- Although background transactions are not always supposed to be feasible, a transaction is often interactive processing that gets its initiation by a single request.
- A transaction is a four-character input type that prohibits repetition in the transaction names.
- A transaction may map to the program one-to-one or multi-to-one. When the transaction trigger occurs, it is put into action.
9. What do you understand by the term deadlock?
Deadlock occurs when two or more tasks are waiting for a resource to either be held free or prevent each other from accessing it.
10. How can you solve the issue of ASRAABEND?
To solve an ASRA ABEND, one has to begin with CEBRA and then reach out for instructions on offsets.
11. How does one handle errors when it comes to CICS programs?
After calling the program, one needs to check the EIBRESP to handle problems better in CICS processes. The HANDLE condition is then put to use to implement a substitute option.
12. What is error code AEIY?
AEIY is primarily the length error code. This error occurs when the length of the source data crosses the limit of the length of the receiving field.
13. What is the use of a DFHMSD process?
With a DFHMSD process, you can group a single map into a map set.
14. What effect would it have on RECEIVE MAP if we press PF and PA keys?
When one presses the PF key, there is a data transmission on RECEIVE MAP. In contrast, there would be no data transmission if one presses the PA key.
15. What is the process of terminating a transaction?
We can use the EXEC CICS SYNCPOINT and assume it is LUW. There will be no termination of Xn, but it will terminate the transaction.

Concluding Remarks
The benefits of implementing CICS are manifold. A lot of enterprises have traditionally run various CICS regions with dedicated responsibilities to each one of them. Because of its high availability and continuous operation, CICS has exceeded the business requirements. This is the reason why it is in demand these days. It has been able to create a lot of opportunities for youth these days. We hope we were able to effectively contribute to your preparation of CICS interview questions through this article.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| IBM DB2 Training | Feb 28 to Mar 15 | View Details |
| IBM DB2 Training | Mar 03 to Mar 18 | View Details |
| IBM DB2 Training | Mar 07 to Mar 22 | View Details |
| IBM DB2 Training | Mar 10 to Mar 25 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .
















