Undoubtedly, the framework of Identity and Access Management (IAM) has undergone a variety of evolution in the past few years. As businesses grow and scale, they must adapt to applications that can streamline operations and networks. Earlier, an employee had to handle just one email profile. However, today, the IT team has to manage thousands of credentials on multiple devices. Thus, mere one security good-up could be the end of the business.
Considering that the workforce and workplace have transformed tremendously in the last decade, organizations and companies across the world have realized the need to regulate the digital identities of employees, partners, and contractors more securely.
Okta is an Identity Standard that helps secure your vital resources from cloud to ground. In this post, let’s find out how Identity and Access Management (IAM) by Okta can address modernized security threats and decrease IT friction.
OKTA Identity and Access Management - Table of Contents
- Identity and Access Management
- OKTA Identity Management
- Active Directory and LDAP Integration
- Framework
- How to Mitigate Risk with OKTA Identity Management?
| If you want to enrich your career and become a professional in OKTA, then enroll in "OKTA Training". This course will help you to achieve excellence in this domain. |
What is Identity and Access Management?
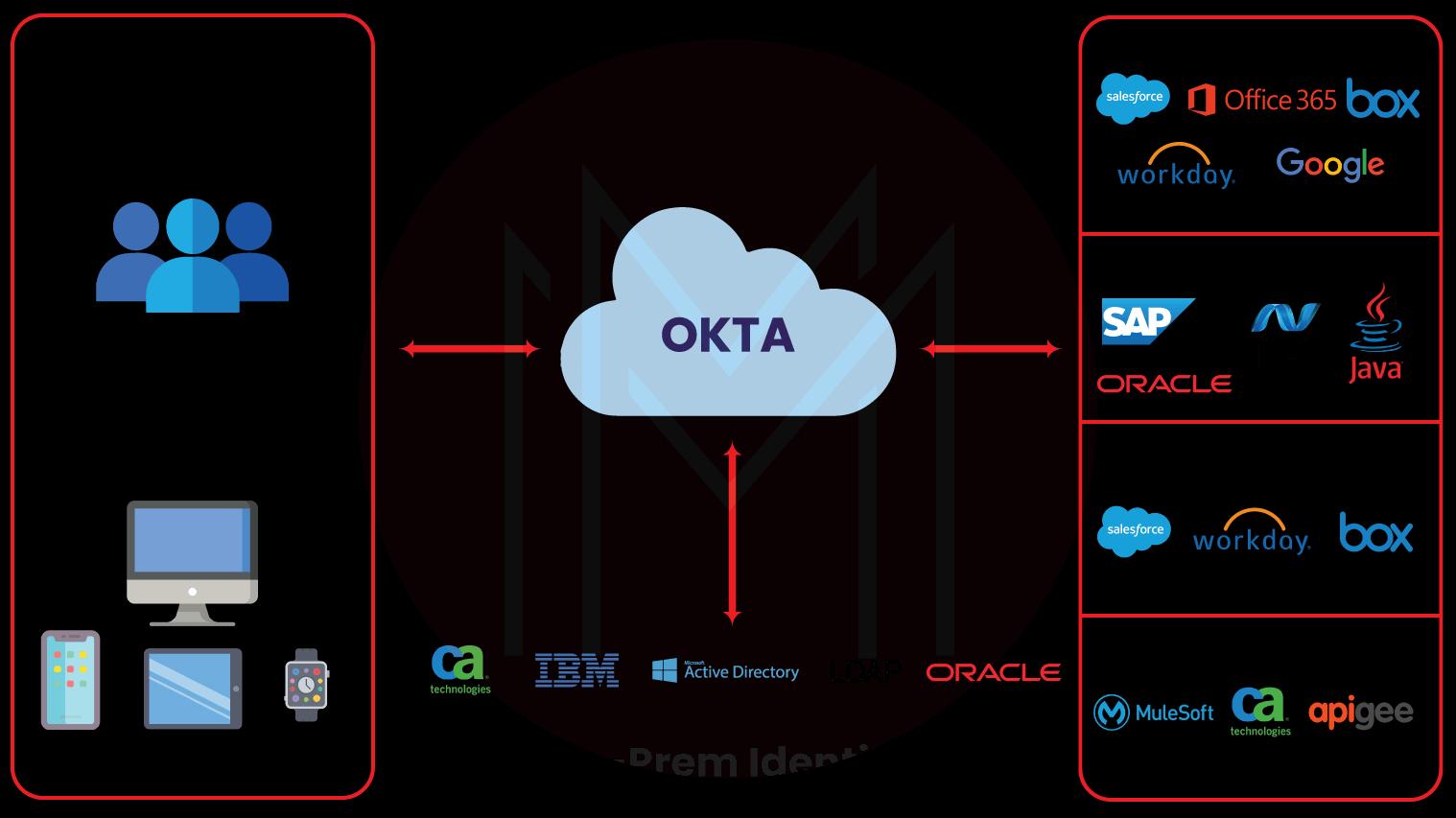
Identity and Access Management is a comprehensive process that helps in codifying users and groups in a complete software system. Along with that, it also helps with access to resources and performing varying functions.
With IAM, you can address authentication, authorization, and access control. By making sure the correct individuals are signing into the business networks, executives can always have their cybersecurity game up to the mark.
All About OKTA Identity Management
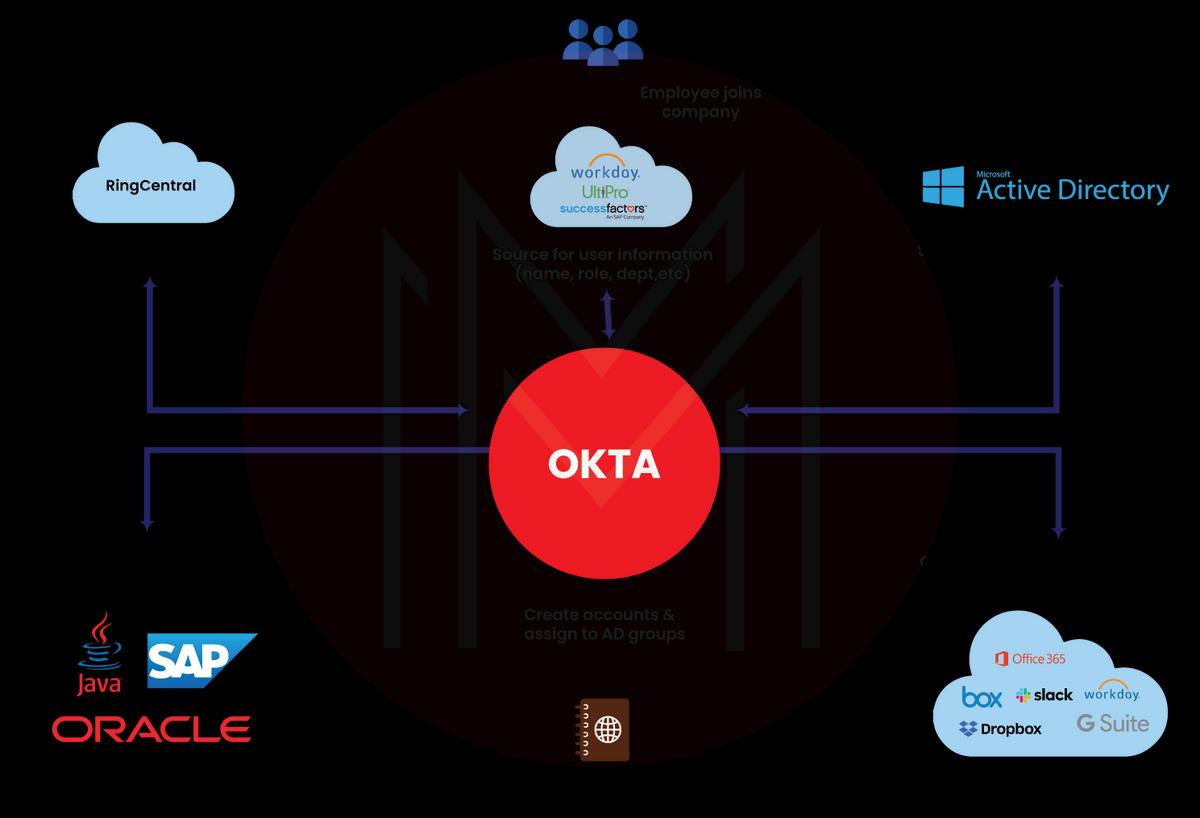
OKTA is an enterprise-grade IAM service that is specifically developed for the cloud. However, its compatibility is not restricted to the cloud. Rather, it can work efficiently with a variety of on-premises applications.
Okta helps connect people with any device or application. With this tool, the IT team can handle the access of employees. Okta runs on a secure, extensively audited, and reliable cloud platform that integrates profoundly with identity management systems, directories, and on-premises applications.
This tool is equipped with an array of useful features, such as:
- Provisioning
- Active Directory (AD)
- Single Sign-On (SSO)
- LDAP Integration
- Centralized Deprovisioning of users
- Multifactor Authentication (MFA)
- Mobile Identity Management.
Along with that, it has several flexible policies for the company’s security and control. All such functions come together via a network of pre-integrated applications, which is known as the OKTA Integration Network (OIN). This OIN app offers an extensive range of integration options that enable SSO login for each app your users have to access during a work day.
Active Directory and LDAP Integration
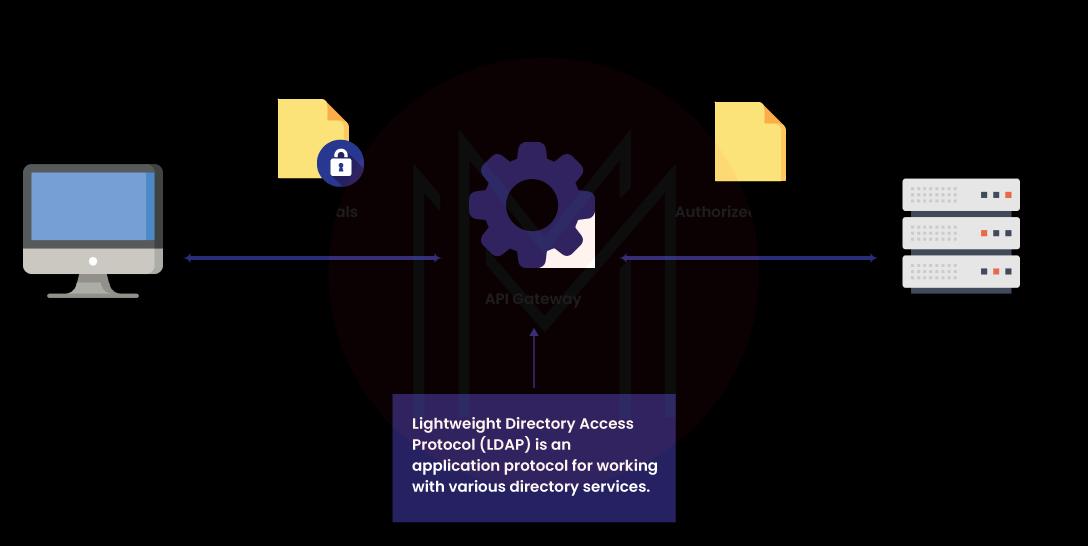
In a lot of enterprises, the Active Directory (AD) of Microsoft is an authoritative user directory that regulates access to primary business applications. SaaS apps were developed with their native user directories. And since they run outside the firewall, they are generally beyond the AD’s reach.
The restriction requires users to consider multiple logins and usernames. IT is compelled to create, handle and map user accounts in AD and around their SaaS apps. Okta fights against these issues with a robust, complete, and easy AD SSO integration.
There are also alternatives to Active Directory, such as LDAP and other on-premises identity managers. In the end, Okta overcomes the technological and economic restrictions of a legacy that the identity management scheme has.
| Check out OKTA Alternatives |
OKTA Identity and Access Management as a Framework
Before you can understand IAM, you must look at its framework. This is such a structure that helps organize several services, concepts, policies, and more.
To understand it better, let’s take an example of a federal act of Congress. As a framework, this complicated aspect of public law helps organize rights and services offered to the ones who come under its jurisdiction.
However, not everyone would have the training or time to comprehend each line of code that goes into the development of IAM. However, the basics can get clear. Thus, in simple words, a good IAM framework assists you in governing who exactly is the target audience of the business networks and what services they can or cannot access.
How to Mitigate Risk with OKTA Identity Management?
As per the Business at Work 2019 report by Okta, almost 40% of employees are using the same two or four passwords to access more than 100 apps. In a workplace, this simply means corporate IT admins are busy managing credentials for varying systems.
As companies shift to cloud-based tools for on-premise and online services, IT admins will have to take the liability to secure access to several platforms with different identity management and access control solutions. This, in turn, could be difficult for the IT teams and can make users more frustrated.
When talking about the IT team's effectiveness, it is helpful in tracking, monitoring, and controlling different accounts with access to sensitive data. This is done while safeguarding the data with secure authentication solutions. Since employees don’t use best practices for passwords, admins must add additional layers of authentication protection to avert any unauthorized intrusion into the system.
By pairing adaptive multi-factor authentication with SSO, administrators can safeguard the company from single-password-related threats by providing additional factors during the authentication process. It also allows administrators to set conditional access that checks the devices, networks, and locations of users while assigning them a risk rating - all in real-time.
With the help of physical tokens and smartphones, users can easily access their applications via a single authentication experience, decreasing the risk created by weak password practices. Integrating such tools and other primary security measures will help safeguard and benefit the employees and IT teams.
IAM also needs efficient lifecycle management, especially as companies consistently see people change, enter or leave the role. When dealing with role changes, administrators must either modify, allow or revoke employees' access to several applications effectively. Companies can automate the task and mitigate the associated risks by integrating a lifecycle management solution.
| Learn OKTA Interview Questions and Answers |
Wrapping Up
Undeniably, Okta identity management has turned out to be a boon for organizations, especially IT companies all around. However, if you are not sure about investing a huge amount in this platform, you can begin by using their 30-days free trial. With this trial, you can import approximately 10,000 users and activate 100 of them.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| OKTA Training | Feb 17 to Mar 04 | View Details |
| OKTA Training | Feb 21 to Mar 08 | View Details |
| OKTA Training | Feb 24 to Mar 11 | View Details |
| OKTA Training | Feb 28 to Mar 15 | View Details |

Viswanath is a passionate content writer of Mindmajix. He has expertise in Trending Domains like Data Science, Artificial Intelligence, Machine Learning, Blockchain, etc. His articles help the learners to get insights about the Domain. You can reach him on Linkedin




