- Home
- Blog
- Cyber Security
- Cyber Security Career Path

- Cyber Security Certifications
- Cyber Security Frameworks
- Cyber Security Interview Questions
- Cyber Security Threats and Prevention Methods
- Top 10 Cyber Security Tools In 2024
- How to Become a Cyber Security Engineer
- Reasons to Learn Cyber Security
- Cyber Security Best Practices
- What is Cyber Security?
- New Technology Trends in 2024
- Spoofing vs Phishing
- Penetration Testing Interview Questions
- Network Security vs Cyber Security
- What is Penetration Testing?
- Bug Bounty Interview Questions
- CRISC VS CISA
- Cyber Security VS Data Science
- Cybersecurity Projects and Use Cases
Are you one among them who is confused about starting a career in the Cybersecurity field? Then you have reached the right place. In this blog, we’ll clear all your doubts and provide complete information regarding the Cybersecurity field.
Gain essential skills to defend your organization from security threats by enrolling in our Cyber Security Training.
Before we start with the explanation of each topic, let’s have a look at the list of key topics that we are going to discuss in this blog:
Is Cybersecurity a good career?
Cybersecurity is a fast-growing technology with lots of exciting opportunities worldwide. As the threat of cyberattacks is spreading all over the world at a rapid pace, organizations of all sizes require Cybersecurity professionals to protect their data. Due to this, the demand for Cybersecurity professionals has raised drastically. In recent years, there has been a three-fold increase in the number of job postings for Cybersecurity professionals when compared to other IT jobs.
Skills Required for Cybersecurity
There are many core skills required for individuals looking to enter into the Cybersecurity realm.
Below mentioned are few of the required skills:
- Fundamentals of Cybersecurity
- Communication Skills
- Able to work in a team environment
- System forensics
- Hacker techniques
- Integrity and Discretion
- Problem-solving skills
- Programming Skills
- Malware analysis and reversing
- Deep knowledge of Security Principles
- Risk Analysis and mitigation
- Network Protocols
- Malicious Codes
- Intrusion detection
Related Article: Cyber Security Frameworks
How to start a career in Cybersecurity
- Attain a Bachelor's degree - Most jobs in Cybersecurity field require a four-year Bachelor’s degree in Cybersecurity or a related field such as information technology or computer science.
- Complete advanced training - Some organizations look for individuals who hold an advanced degree such as Master’s or certifications in Cybersecurity.
How to find the right Cybersecurity degree?
There are various levels available in Cybersecurity degrees right from an associate-level to the Ph.D. degree. Depending on the aspirant’s goal, they should select the Cybersecurity program as each level offers specific opportunities.
Frequently asked Cyber Security Interview Questions & Answers
Careers in Cybersecurity
There are various careers available in Cybersecurity from entry-level to senior management level.
Some of the major career paths along with their job responsibilities are listed below:
- Chief Information Security Officer (CISO)
- Forensic Computer Analyst
- IT Security Consultant
- Penetration Tester/Ethical Hacker
- Security Architect
- Information Security Analyst
- Security Systems Administrator
1. Chief Information Security Officer (CISO)
A chief information security officer (CISO) is a senior-level executive responsible for maintaining and establishing organization strategy, vision, and program.
If you wish to lead a team and IT initiatives, becoming a CISO is a lucrative and rewarding career path.
Job responsibilities:
- Conduct employee security awareness programs and communication practices.
- Develop strategic plans to deploy information security technologies.
- Protect the organization's data privacy.
- Conduct electronic discovery and digital forensic investigations.
2. Forensic Computer Analyst
Forensic computer analyst works with law enforcement agencies and private firms to retrieve information from computers and data storage devices. They collect data from digital tools as part of their investigation.
Job Responsibilities:
- Use forensic tools and software to retrieve and analyze data.
- Recover damaged, deleted, or encrypted files.
- Keep up to date with the latest cyber-crime developments and methods within the digital forensics field.
- Work to relevant ISO accreditations.
Learn Cyber Security Online Course in Bangalore
3. IT Security Consultant
IT Security Consultants implement the best security solutions for an organization's needs. They meet with clients to protect an organization’s Cybersecurity objectives efficiently and effectively.
Job Responsibilities:
- Prepare cost estimates and detect integration issues for IT projects.
- Find the most effective ways to protect data, networks, software, etc., from possible attacks.
- Perform security assessments and risk analysis.
- Define and maintain corporate security policies.
- Plan, research, and design robust security architectures for any IT project.
4. Penetration Tester/Ethical Hacker
Penetration Testers identify security weaknesses in IT systems, applications, and networks using the tactics employed by criminal hackers.
They work with a series of tools to simulate real-life attacks, detect weak spots, and improve the organization's security posture.
Job Responsibilities:
- Design and execute new penetration tools and tests.
- Uncover security holes and methods that attackers could use to exploit system weaknesses.
- Execute penetration tests on web applications, systems, and networks.
5. Security Architect:
Security Architects are responsible for implementing and maintaining network security for organizations.
If you are passionate about problem-solving and developing strategies for organizations' security, then the Security Architect career path is right for you.
Job Responsibilities:
- Handle hands-on repair of issues raised in problem reports and also analyze breaches followed by security incidents.
- Research and implement advanced security standards, systems, and best practices.
- Perform security assessments, risk analysis, and vulnerability testing.
6. Information Security Analyst:
Information security analysts are responsible for planning and implementing security measures to secure the organization's data and networks.
Job Responsibilities:
- Test and implement network disaster recovery plans.
- Perform risk assessments.
- Prevent data loss and service interruptions by staying up to date with advanced technologies.
- Install firewalls, data encryptions, and other security practices.
Visit here to learn Cyber Security Course in Hyderabad
7. Security System Administrator:
Security systems administrators are in charge of the daily operations of security systems such as systems monitoring, running regular backups, and configuring and maintaining individual user accounts.
Job Responsibilities:
- Protect systems against unauthorized access, and perform vulnerability and penetration tests.
- Configure and support security tools (firewalls, antivirus, and IDS/IPS software).
- Monitor traffic for suspicious activity.
- Conduct security audits.
- Implement network security policies.
- Develop and update disaster recovery protocols.
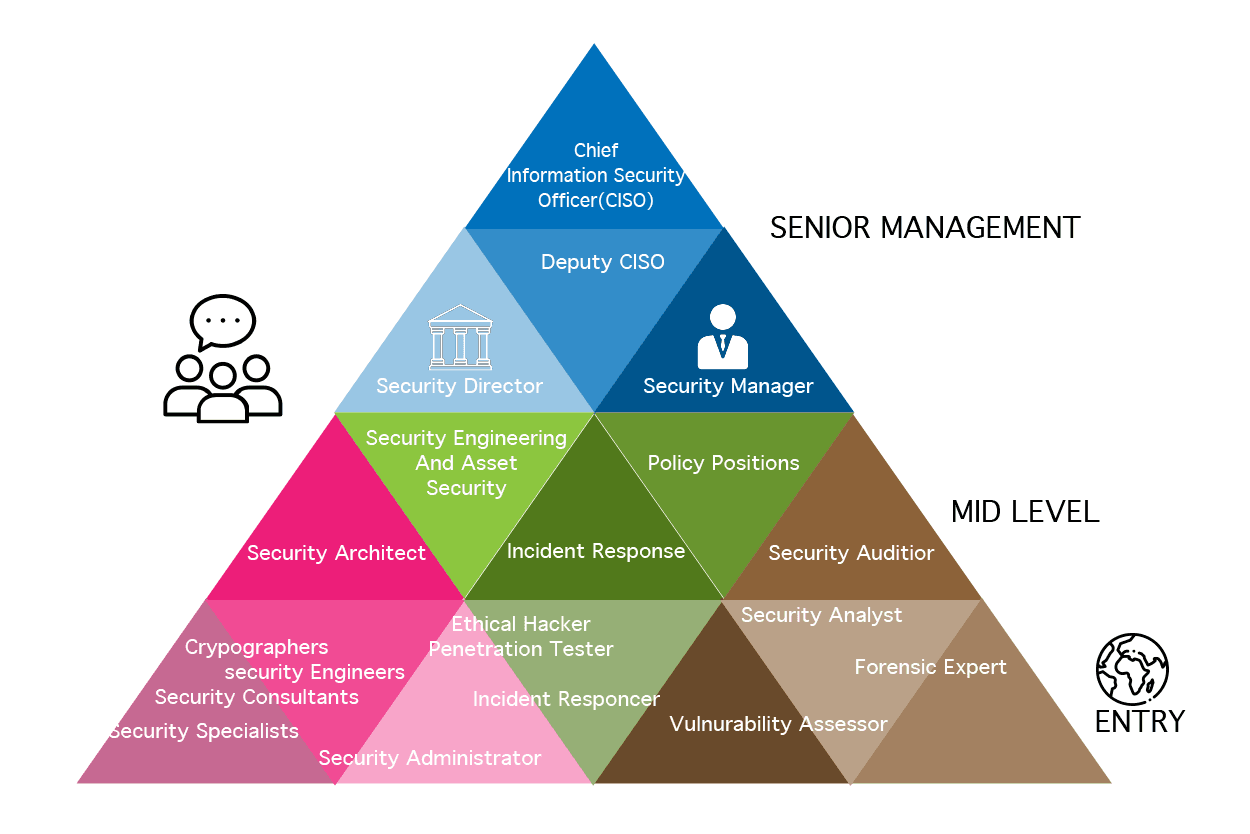
Cybersecurity career roadmap
The below-mentioned figure shows how an individual has to cross through to reach the top positions available in the Cybersecurity realm.
Cybersecurity salaries
| Cybersecurity job title | Average salary |
| 1. Chief Information Security Officer | $223,916 |
| 2. Computer Forensic Analyst | $95,510 |
| 3. Security Consultant | $83,014 |
| 4. Penetration Tester | $81,356 |
| 5. Security Architect | $121,601 |
| 6. Information Security Analyst | $98,123 |
| 7. Information security director | $111,379 |
| 8. System Security Administrator | $69,750 |
Related Article: Top 10 Cyber Security Tools In 2020
Benefits of Cybersecurity
- Individuals in this field always work with the latest technologies.
- There is no defined career path in this field.
- Cybersecurity professionals are always in high demand.
- Great job satisfaction.
- Unlimited career growth opportunities.
- Learning never stops.
- Salaries continue to rise.
Cybersecurity Certifications
The major Cybersecurity certifications which are in-demand in the market are listed below:
- CompTIA Security+
- Computer Hacking Forensic Investigator (CHFI)
- Certified Information Security Manager (CISM)
- Certified Ethical Hacker (CEH)
- Certified Information System Security Professional (CISSP)
- Certified Cloud Security Professional (CCSP)
- Certified Information Systems Auditor (CISA)
- NIST Cybersecurity Framework (NCSF)
- Cisco Certified Network Associate (CCNA) Security
Conclusion:
In this blog, we’ve tried to explore and make you understand the Cybersecurity field, roles, certifications, and more that aspirants should know to advance their career in this field. We hope this will be a quick reference for you to make a decision about moving ahead in the Cybersecurity realm.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Cyber Security Training | Feb 24 to Mar 11 | View Details |
| Cyber Security Training | Feb 28 to Mar 15 | View Details |
| Cyber Security Training | Mar 03 to Mar 18 | View Details |
| Cyber Security Training | Mar 07 to Mar 22 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .















