- Home
- Blog
- Cyber Security
- Cybersecurity Projects and Use Cases

- Cyber Security Career Path
- Cyber Security Certifications
- Cyber Security Frameworks
- Cyber Security Interview Questions
- Cyber Security Threats and Prevention Methods
- Top 10 Cyber Security Tools In 2024
- How to Become a Cyber Security Engineer
- Reasons to Learn Cyber Security
- Cyber Security Best Practices
- What is Cyber Security?
- New Technology Trends in 2024
- Spoofing vs Phishing
- Penetration Testing Interview Questions
- Network Security vs Cyber Security
- What is Penetration Testing?
- Bug Bounty Interview Questions
- CRISC VS CISA
- Cyber Security VS Data Science
Nowadays, the internet has become one of the essential parts of our life. No single day can be spent without using the internet in this digital world. As the number of computers and volume of data increases tremendously every day, the consumption of the internet also goes up at rocket speed.
Cybersecurity is a big challenge that every individual and company faces in this digital world. Every day, cybercriminals pass new viruses and malware to computers and networks in different forms through the internet. It challenges the efficiency of existing cybersecurity solutions. So, protecting computers and data from theft and damage has become crucial.
That’swhy, Cybersecurity is the word buzzing around everywhere. Also, there is a soaring demand for cybersecurity professionals worldwide. Those who are proficient with cybersecurity solutions are prone to get hired by top companies and gain attractive packages.
Now, a question may come up in your mind – how to hone my skills in Cybersecurity?
Don’t worry! We unlock the answer in this blog.
Practicing projects on Cybersecurity is the best way to enhance one’s prowess in Cybersecurity. Completing cybersecurity projects can reap exceptional hands-on experience in cybersecurity solutions.
This blog covers critical cybersecurity projects, the need to learn them, skills you will gain, FAQs, etc.
Let’s uncover all!
| Table of Contents - Cybersecurity Projects |
What is Cybersecurity?
Cybercriminals make cyberattacks in multiple ways, such as bypassing malware and viruses, making unauthorized access, stealing or corrupting sensitive data, etc. Cybersecurity is a crucial computer domain that deals with applying various methods and tools to safeguard networks, computers, and data from cyberattacks and vulnerabilities.
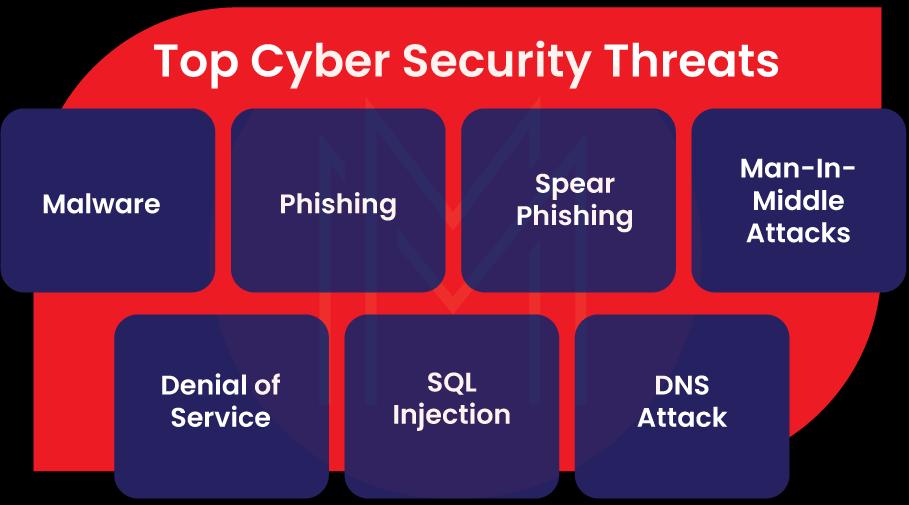
Know that the cyber-attacks can be both internal and external. When it comes to internal attacks, own employees of a company may make unauthorized attempts to access sensitive data or corrupt the data. On the other side, cybercriminals make external attacks to damage computers and data.
No wonder natural disaster is also one of the external cyberattacks. It can cause severe damage to data and computers.
| If you want to enrich your career and become a Cyber Security professional, enroll in "Cyber Security Training".This course will help you to achieve excellence in this domain. |
Why Cybersecurity Projects?
Let’s see why projects on Cybersecurity are crucial in developing one’s skills in Cybersecurity.
Although cybersecurity solutions evolve daily, new threats and cyberattacks still challenge the efficiency of existing cybersecurity solutions. Only competent cybersecurity professionals can tackle new threats as well as attacks effectively. That’s why there is always an ever-increasing demand for skilled cybersecurity professionals worldwide.
If you want to become a cybersecurity expert, you must groom your skills on robust cybersecurity tools and methods. Then, dealing with harmful viruses and threats won’t be a big deal to you.
Practicing cybersecurity projects is the best way to improve your expertise in cybersecurity methods and tools. It will help to breeze through your interviews for cybersecurity jobs. Not only that, you will start performing in your job right from the very beginning.
Pre-requisites to learning Cybersecurity projects
Before diving into learning projects on Cybersecurity, ensure that you have the following essential skills and abilities. If you fulfill the requirements, practicing cybersecurity projects will be a cakewalk.
Here we go:
- Knowledge of spyware, malware scanners, and intrusion detectors
- Exposure to operating systems such as Linux and Windows
- Basic understanding of computer networks
- Basic coding skills in C, JavaScript, Python, HTML, and PHP
- Knowledge of various cyber vulnerabilities.
- Familiar with computer forensic tools
- Basic understanding of security incident management
- Strong analytical and problem-solving skills
- Proficiency in risk analysis as well as a security audit
Skills that will develop through Cybersecurity projects
By completing various cybersecurity projects, no doubt you will acquire many vital skills in Cybersecurity.
Let’s outline the skills that you will develop.
- Identifying threats in Computer Networks and data storage
- Exposure to cyber risk management methods
- Familiar with robust cybersecurity frameworks
- Proficiency with advanced cryptographic algorithms
- Expertise in handling firewalls
- Exposure to penetration testing, malware analysis, etc.
- Sound knowledge of cloud platforms like Microsoft Azure, AWS, GCP, etc.
Above all, you will emerge as a competent cybersecurity expert.
Cybersecurity Projects
As mentioned earlier, it is essential to work on Cybersecurity projects to gain mastery over cybersecurity solutions. In this section, MindMajix content experts picked up a few crucial projects on Cybersecurity for beginners as well as experienced learners. Once you complete all these projects, cracking your Cybersecurity interviews or growing up in your career is a walk in the park.
Let's dive deep into them!
[Related Article: Cyber Security Interview Questions]
Cybersecurity Projects for Beginners
This set of cybersecurity project ideas comprises basic methods and algorithms to secure computers, data, and networks from Cyberattacks. If one practices the project ideas intensely, he/she will get a basic understanding of cybersecurity solutions.
Let’s start now!
-
Text encryption using Cryptographic algorithms
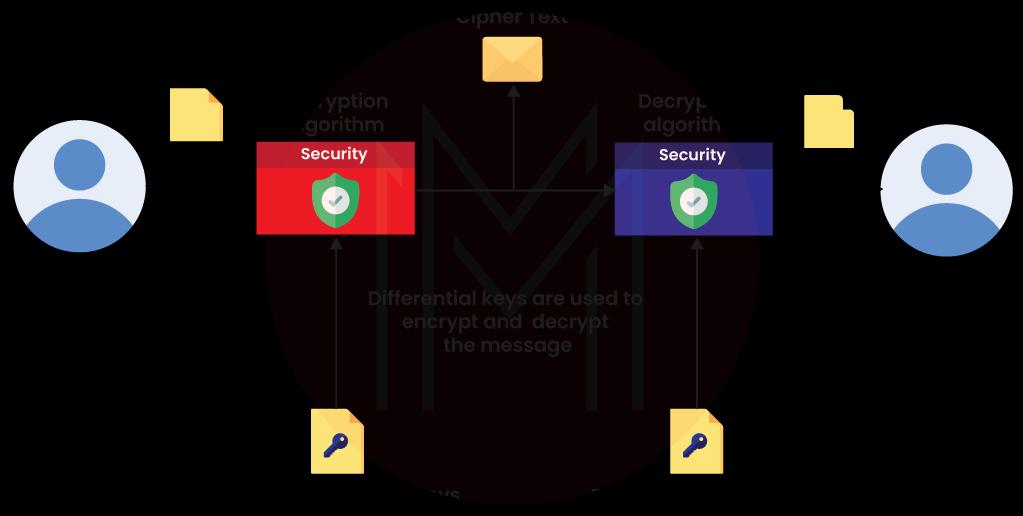
This is one of the best cybersecurity projects for beginners. Know that encryption is the process of converting input data into cipher code. With the encryption method, you can secure data from unauthorized access. Also, you will learn to encrypt input messages fed into web applications. Note that the same input will generate multiple outputs if the encryption method is so strong.
By learning this project, you will get exposure to various algorithms like Caesar Cipher, Playfair Cipher, Railfence Cipher, etc. Also, you will learn programming languages such as JavaScript and Node. JS.
-
SQL Injection
SQL injection is one of the harmful cyberattacks in which attackers manipulate SQL queries to access sensitive data. When there are vulnerable security headers and unprotected input fields in the data, it opens up ways for cyber attackers to make SQL injection attacks.
In this Cybersecurity project, you will learn to develop a system to verify whether the applications under the test are vulnerable to SQL injection. If the system identifies any vulnerability, you will learn to remove the vulnerability and strengthen the system.
-
Image Encryption method
Of course! We can encrypt images similar to texts. If you have the right key, you can decrypt images quickly. Also, you will learn to use powerful algorithms such as DES, AES, and RSA through this project.
By doing this project, you will learn to transfer data using remote networks as well as servers. Also, you will understand to encrypt data using keys.

-
Keylogger Software
This is a cyber-security project that helps to ensure the security of companies’ data and computers internally. Keylogger is software for recording all the keystrokes an employee hits on a computer keyboard. This project allows learners to get familiar with programming languages such as JavaScript and Node.js.
By practicing this project, you will develop a system to identify the suspicious activities of employees by monitoring their keystrokes. No matter what type of keyboard – virtual or physical – this system supports tracking keystrokes made by employees.
-
Password Strength Tester
Undeniably, a strong password provides robust security. In this cybersecurity project, you will put up a system to validate the strength of passwords. You will check whether the password satisfies the Open Web Application Security Project (OWASP) standards. If a weak password is entered, the system will make alerts instantly.
Completing this project, you will learn to set ground rules for creating a strong password. Note that a strong password must have a minimum length, include numerical and special characters, avoid using the username, and more.
-
Hackathons and Bug Bounties
Hackathon is a great channel to boost your knowledge of internet security. You can collaborate with interface designers, graphic designers, and cybersecurity experts to gain an understanding of internet security.
A bug bounty is a software with which you can find bugs in codes. Completing this project, you will learn to develop a system to find code errors.
-
Caesar Cipher Encryption and Decryption
This is yet another simple Cybersecurity project that employs the earliest encryption algorithms. The exciting thing is that it is used by the king of Rome, Julius Caesar, to communicate secret messages to his subordinates.
Completing this project, you will learn to develop software based on the Caesar Cipher algorithm.
Cybersecurity Projects for Experienced
This part of the blog includes advanced cybersecurity project ideas with which you can polish your skills in cybersecurity solutions.
Let’s take a close look at them now.
-
Security Scanner
It is crucial that you must scan computers and networks regularly to ensure that they are safe and reliable. By working on this project, you will get exposure to programming languages like JavaScript and Node.js. Also, it is possible to get exposure to container platforms like Docker through this Cybersecurity project.
In this project, you will design a cyber-security system to scan computers and networks to detect risks. The main thing is that it is easy to assign numerical values to the risks and apply suitable corrective measures immediately.
-
Cloud Access Security Broker - CASB
CASB is software that acts as the bridge between cloud applications and cloud services. We use this software to monitor user activities and examine the implementation of security policies.
By working on this project, you will get expertise in user activity monitoring, enforcing security policies, identifying suspicious activities, and much more.
.png&w=1920&q=75)
-
Credit Card Encryption and Decryption
This is another important project on Cybersecurity that deals with two key domains – Cloud Computing and Cybersecurity. In this Cybersecurity project, you will learn to design a system to prevent unauthorized access to credit cards by embracing robust encryption methods.
By learning this project, you will become proficient with encryption algorithms like DES, ECC, RSA, etc. Also, you can get mastery over access control management as well as cryptography techniques. Also, this project opens up opportunities to learn Java coding and Google Cloud services.
-
Antivirus Software
This is another interesting project with which you will learn to create antivirus software. This antivirus software can detect and remove malicious content in computers and networks. With this software, you can prevent hackers from accessing any sensitive data and systems.
Moreover, you can build antivirus software by adding features such as real-time scanning, auto-cleaning, automatic updates, etc. This project will teach you the valuable features of popular antiviruses such as Avast, Bitdefender, Kaspersky, and many others. Also, it is easy to get familiar with C# programming by doing this project.
-
Image Steganography System
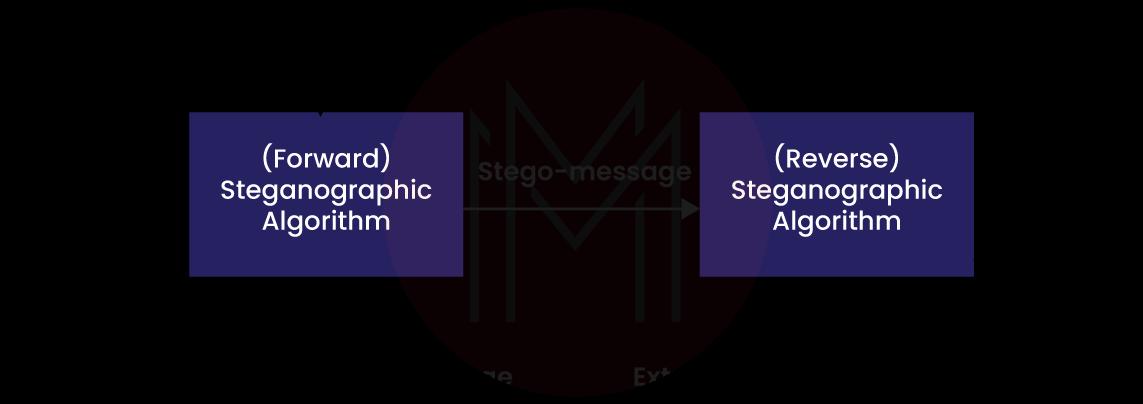
Know that steganography is the method that helps to hide sensitive data inside a normal text. The sensitive data is usually embedded in images and passed to destinations through the internet.
You can apply many algorithms in this project, such as Least Significant Bits, Batch Steganography, and Chaos-based spread spectrum.
Practicing this project will make you proficient with open-source image processing libraries. The important thing is you will also learn Java programming and Android Studio by doing this project.
-
User Authentication System
This is a crucial project that will strengthen your knowledge of Cybersecurity significantly. In this project, you will construct a user authentication portal. This is where users can sign up/out and log in/out. By practicing this project, you will get exposure to multi-factor authentication, facial recognition, biometric authentication, and many more.
This project will help to get exposure to various text editors, Model View Controllers, SQLite, and other popular frameworks. Besides, you will acquire knowledge of Express.js, Node.js, and MongoDB.
-
Wazuh - Open Source SIEM
This is yet another cybersecurity project that helps to elevate your skills in Cybersecurity. We use this software to monitor, detect, and alert security incidents. Mainly, this software provides security to cloud workloads and endpoints. This project will teach you about endpoint security, log data analysis, threat intelligence, and much more.
By completing this project, you will get expertise in collecting data from systems and networks, historical reporting, making trend analyses, and much more.
Cybersecurity Real-time Projects Examples
Here’s a list of a few real-time cybersecurity projects that will help to top up your knowledge of Cybersecurity in a big way.
Let’s have a look at them right here!
-
Packet Sniffing
By learning this project, you will get familiar with tracking all incoming and outgoing traffic in a network with the help of packet sniffers. Also, you can follow the information stuffed in data packets and the source and destination details.
-
Web Application Firewall
This project helps to examine the traffic between web applications and the internet. So you can protect web applications from viruses and threats from various channels.
-
Web-based facial Authentication System
We use this software in KYC processing, exam centers, and many crucial places. Completing this project will make you proficient in the OpenCV real-time computer vision tool.
-
RFID Blocking
By completing this project, you will know how to block RFID scanners from reading credit/debit cards and critical documents without your approval. Also, even you can identify the people who read the cards without your consent by doing this project.
-
Log Analyzer
This project will give you comprehensive visibility of the activities happening across the computers and networks.
-
Malware Analysis Sandbox
We use this tool to analyze if any malware attacks stored files. This tool generates a report based on the aim and behavior of the malware accurately.
Cybersecurity Projects: Why are they so important?
Following are the reasons why Cybersecurity projects are important to heighten the skills of Cybersecurity professionals.
-
Protection from Cyberattacks
It is highly important to protect computers, data, and networks of individuals and organizations from cyberattacks. The attacks can be data theft, data corruption, or any other. One can learn to protect valuable resources from cyberattacks by working on cybersecurity projects.
-
Cloud Migration
Many companies migrate their data to the cloud for security and cost-effectiveness. But at the same time, it opens up many chances for data misuse, cyberattacks, or data theft. So there is a need to employ cybersecurity solutions in place. Practicing projects on Cybersecurity can get expertise in securing data in the cloud.
-
Improving Reliability and Security
Suppose companies want to enhance their reliability in the market; they must leverage advanced cybersecurity solutions to protect their resources. One can get exposure to implementing advanced cybersecurity solutions by learning about cybersecurity projects.
-
Evolving new risks
On top of all, cybercriminals create new threats and viruses and pass them into the internet frequently. That's why employing advanced cybersecurity solutions to protect resources is a must. One can learn advanced cybersecurity solutions and protect resources by doing projects on Cybersecurity.
Thus, working on cybersecurity projects makes you an intelligent cybersecurity professional and equips you to secure computers, data, and networks efficiently.
Cybersecurity FAQs
1. What are the five different types of Cybersecurity?
Jotted down are the different types of Cybersecurity.
- Network security
- Data security
- Cloud Security
- Application security
- Mobile security
2. Name the seven layers of Cybersecurity.
Below are the seven layers of Cybersecurity.
- Physical security
- Perimeter security
- Network security
- Endpoint security
- Data security
- Application Security
- User education
3. What are the programming languages used in Cybersecurity?
C and C++ are widely used in cybersecurity applications.
Mention the significant cybersecurity threats.
- Trojan malware
- Viruses
- Adware
- Spyware
- Ransomware
- Worms
4. How do companies widely use cybersecurity tools?
Jotted down are the various cybersecurity tools used in companies.
- Firewalls
- Penetration testing
- PKI services
- Antivirus software
- Managed detection and response service
5. List the various types of cyber-attacks.
Following are the various types of cyber-attacks.
- DoS and DDoS attacks
- phishing attacks
- man-in-the-middle attack
- drive-by attacks
- SQL injection attack
- password attack
- cross-site scripting attack
- birthday attack
- eavesdropping attack
- malware attack
6. What is the future of Cybersecurity?
The future of Cybersecurity is bright and in demand. AI and ML models will make revolutionary changes in developing future cybersecurity solutions.
7. List the ten steps we apply for a practical cybersecurity approach.
- Assessing the security risks
- Making configuration
- Monitoring user access and applying controls
- Securing networks
- Educating users and creating awareness
- Secured home and mobile working
- Efficient incident management
- Monitoring computers and data
- Preventing malware and viruses
- Controlling removable media
Conclusion
It’s a wrap! By reading this blog, you have come across what Cybersecurity is, key projects on Cybersecurity, the importance of practicing the projects, and so on. You will undoubtedly gain an excellent hands-on experience with Cybersecurity tools by working on cybersecurity projects. It will aid you in acing your interviews on Cybersecurity and handling your real-time projects in the workplace efficiently.
However, if you devote some time to professional training, it will help to polish your skills in Cybersecurity. It is wise to sign up for a course in Cyber Security Training a leading e-learning provider, and get certification. Ultimately, it will help to expand your knowledge spectrum of Cybersecurity and leg up to shine in your carrier in Cybersecurity.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Cyber Security Training | Feb 24 to Mar 11 | View Details |
| Cyber Security Training | Feb 28 to Mar 15 | View Details |
| Cyber Security Training | Mar 03 to Mar 18 | View Details |
| Cyber Security Training | Mar 07 to Mar 22 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .















