- Home
- Blog
- Cyber Security
- Network Security vs Cyber Security

- Cyber Security Career Path
- Cyber Security Certifications
- Cyber Security Frameworks
- Cyber Security Interview Questions
- Cyber Security Threats and Prevention Methods
- Top 10 Cyber Security Tools In 2024
- How to Become a Cyber Security Engineer
- Reasons to Learn Cyber Security
- Cyber Security Best Practices
- What is Cyber Security?
- New Technology Trends in 2024
- Spoofing vs Phishing
- Penetration Testing Interview Questions
- What is Penetration Testing?
- Bug Bounty Interview Questions
- CRISC VS CISA
- Cyber Security VS Data Science
- Cybersecurity Projects and Use Cases
Everyone is aware of how important security is in the digital age. Strong security is essential, and frequent news headlines about high-profile hacks and data breaches prove this. But how do information security, cybersecurity, and network security differ from one another?
There is undeniably some misunderstanding surrounding these terms, in part due to the substantial overlap between them.
Information security can be dated to the beginning of human secret-keeping when tangible files and documents were literally locked away. Network security became crucial to safeguarding the electronic network infrastructure of these crucial systems once the business world started employing computers. Everything changed with the introduction of the internet, which added previously unimaginable technological capabilities while simultaneously introducing new dangers and spawning a vital new economy.
So, which one is more crucial? While the first two are undoubtedly important for the practice of keeping systems, information, and assets secure, cybersecurity currently dominates the conversation.
However, some assessments view information security as an all-encompassing phrase because it covers the procedures and methods used to prevent unwanted access to any type of sensitive data or information, whether it be in print or electronic form.
According to this perspective, cybersecurity is a subset of information security that deals with defending a company's internet-connected systems against prospective cyberattacks. A subset of cybersecurity called "network security" is concerned with safeguarding an organization's IT system from internet dangers. Despite the fact that the phrases are frequently used together, cybersecurity is thought to be the more comprehensive field, with network security being one component of information and/or cybersecurity.
| Table of Content: Network Security vs Cyber Security |
What is Network Security?
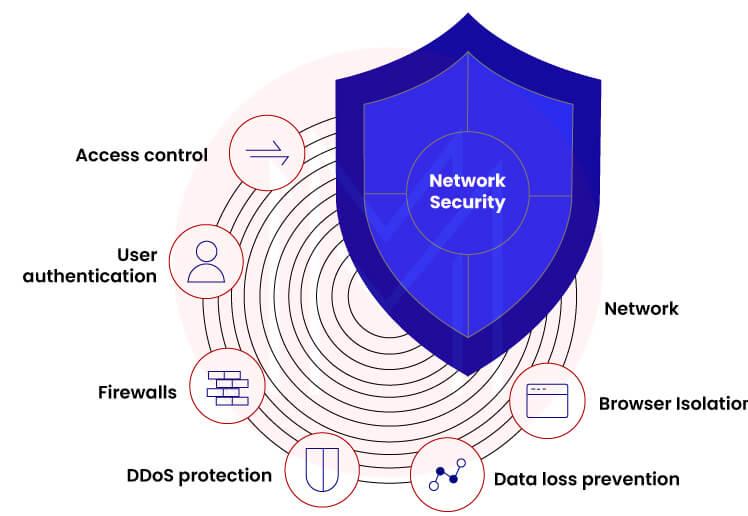
Let's first examine what a computer network is before going any further because network security is a really vast topic.
A group of computers that are digitally interconnected and use a common set of communication protocols to share resources that are stored on or made available by network nodes is referred to as a computer network.
The application of methods, procedures, and protocols to safeguard a person's or an organization's communications and information is referred to as network security.
Therefore, if you have a computer network, there is a possibility that the data being transferred via it will be leaked or interfered with in some way. To prevent this, we build these network security protocols.
Networks can be open to the public or private, as those inside of a business. Access to data must be authorized in a network that is under the control of a network administrator.
| Gain essential skills to defend your organization from security threats by enrolling in our Cyber Security Training. |
Why Network Security?
One of the most crucial issues is network security.
Example: A person by the name of Ashok exists. Ashok now wants to send his coworker John a message and speak with him. The communication contains confidential information about the company and trade secrets that shouldn't be accessed or read by outside parties. He uses email to deliver the message. Assume Evy that the communication has been read by a stranger. Now that Evy has access to firm data, the organization could be in grave danger.
If the rival business learns about your sales data, client information, and business plans, there will be financial damage.
We can seal the connection between Ashok and John to stop this from happening so that trespassers cannot access it. The metaphorical lock represents network security.
| Related Article: Why Network Security Needs to Have Big Data Analytics? |
What is Cybersecurity?

We protect our data from fraudsters in the area of cyber security. Cybersecurity is the process of preventing data breaches on computers, mobile devices, and other electronic device components.
Cyber-security could refer to the use of computer networking, software, or other technologies to protect against online dangers. It keeps up the variety of practices used to protect the integrity of networks, programs, and data from unauthorized access.
Why Cybersecurity?
To illustrate how cyber security procedures protect us against data breaches and unauthorized views, let's look at an example.
Tarun is a client who consistently makes online purchases from a particular website. Tarun kept her personal information, including her email address, address, and credit card details, for easier and quicker buying. The min server contained the necessary data. One day, Tarun got an email from her online store announcing that she was qualified for a special discount coupon. To get the promo code, she had to input the login information for her purchasing website. She assumed it was an account check at the time, so it didn't appear suspicious to her. She had no idea how dangerous her situation would be. Tarun was completely floored when a sizable sum of money was taken out of her account.
Since a third party gained access to her information and appeared to be the company's owner, Tarun did in fact receive a fake email from the shopping website.
Tarun had access to a variety of Cyber Security tools that she could have used to defend herself.
Cybersecurity strategies include those that help protect various digital systems, networks, data, and components against unauthorized digital access.
| Related Article: Cyber Security Career Path |
Pros and Cons of Network Security vs Cyber Security
- Pros and Cons of Network Security
Pros:
- Safeguard data
Unauthorized entry is prevented by network security. A network holds a lot of sensitive information, including customer personal information. Any hacker who gains access to the network could damage this sensitive data. Therefore, network security should be implemented to safeguard them.
- Block cyberattacks
The internet is where the majority of network attacks originate. Expert hackers exist in this field, and viral attacks also exist. They can play around with a lot of the network's information if they are negligent. These attacks cannot harm PCs thanks to network security.
- Access levels
Different users are granted access at different levels by the security software. After the user has been authenticated, the authorization approach is used to determine whether the user has the right to access a certain resource. Some shared papers might have been password-protected for security. The program is aware of who has access to which resources.
- Centrally organized
The network security software, in contrast to desktop security software, is managed by a single user under the name of the network administrator. While the latter can stop hackers before they cause any damage, the former is more vulnerable to worm and virus attacks. This is due to the software being installed on a device without an internet connection.
Cons:
- Expensive setup
A network security system's installation can be somewhat pricey. It can be expensive to buy the software, install it, etc., especially for smaller networks. Here, a network of computers that can store a vast amount of data is being discussed rather than a single computer. As a result, the cost of security will undoubtedly increase. It must not be disregarded at all costs!
- It takes time
Some networks' installed software can be challenging to use. Every time you update a document, you must authenticate using two passwords to provide double protection. Additionally, the passwords must contain letters, numbers, and other special characters in order to be unique. Before choosing a password, the user may need to type a number of sample passwords, which takes a long time.
- Needs Skilled employees
Large-scale network management is a difficult task. It calls for highly qualified specialists that can tackle any arising security issues. Employing a network administrator is necessary to guarantee the network's smooth operation. To fulfill the criterion, he needs to receive proper training.
| Related Article: Network Security Interview Questions |
- Pros and Cons of Cyber Security
Cybersecurity offers a number of benefits. Your company will prosper when it is protected from all network-related dangers and reaps the following advantages:
Pros:
- Increased availability of data and systems
The greatest way to improve the efficiency of data and its network is through cyber security; to lessen the number of malicious attempts to access your computer, use firewall software.
- Preventing Hackers from Accessing Your Data
A data leak is significantly less likely thanks to cyber security. Restrict resource access based on user roles and tasks or network connections by utilizing DLP techniques in conjunction with a web server, firewalls, and other access control techniques and technologies.
- Greater conformity
Integrated security measures are required under several regulations. Running a global business while managing sensitive customer data, such as credit cards or social security numbers is achievable. for instance. Your system can be subject to European data privacy laws. Such information needs to be safeguarded against theft and illegal access.
Terrorist organizations and other enemies may steal or even leak important government information as a result of weak cyber security. Nations that ignore this problem will experience quick and severe economic and political consequences.
Cons:
The use of a cyber security system has a number of disadvantages. First, even when you take drastic efforts, cyber security has its limitations. If only a few employees have access to the proper credentials, for instance, employee or corporate data may be compromised. Additionally, there are the following issues with cyber security:
- Cost to Operate and Maintain
When done alone, the cost of installing and maintaining a cyber security system is exorbitant. Both having staff that are informed about cyber security and integrating hardware and software are crucial.
Although protecting your systems may be expensive, the consequences of a cyberattack or other attacks may be much more costly.
- Cybersecurity Measures Implementation Requires Patience
If you don't have the right people in place to complete the implementation, you can end up spending a lot of money. Additionally, because threats are always evolving, you'll need to stay current with new cyber security laws as they become available. Having a full-time IT team isn't always feasible if your business is tiny or has the necessary resources.
- Procedure Restriction
The company's total productivity could be harmed by the installation of cyber security. For instance, businesses may implement suitable restrictions by requiring employees to use complicated credentials for each session or two-factor authentication while accessing a system from home.
When choosing the steps to take in your firm, it would be prudent to take the drawbacks of cyber security into account. For instance, if you don't take enough security measures to safeguard your computer systems and data, access to them may be prohibited.
| Related Article: Cyber Security Frameworks |
Network Security vs Cybersecurity- Comparison
Here are a few of the key distinctions between Fortinet and Sonicwall, according to various criteria
| Network Security | Cyber Security | |
| Definition | Data is safeguarded as it moves through and across a network with the use of a feature called network security. As a result, it safeguards company information from dishonest workers who are not permitted to examine particular critical information. | The server and device data of a business are protected by a cyber security system. In other words, it adds another line of protection against online thieves. |
| Hierarchy | It falls under cyber security. | It falls under information security. |
| Types of Attacks | It deals with preventing worms, viruses, and DOS attacks. | It deals with defending against online threats, including phishing and pre-texting, as well as online crimes. |
| Data | It safeguards the information traveling through the network. Network security guarantees that only the data in transit is protected. Everything in the network domain is protected by it. | It safeguards the information stored on servers and devices. Cybersecurity ensures that all digital data is protected. Anything in cyberspace is protected. |
| Security | It protects the data that terminals send across the network. | It deals with safeguarding residing data. |
Conclusion
Network security is a subset of cyber security that is concerned with protecting an organization's IT infrastructure and limiting access to it. Cyber security is a subset of information security that deals with the security of data during storage and transport. Both terms are frequently used in connection with one another, however, network security is one component of information/cyber security, whereas cyber security is a term used in a much broader sense.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Cyber Security Training | Mar 07 to Mar 22 | View Details |
| Cyber Security Training | Mar 10 to Mar 25 | View Details |
| Cyber Security Training | Mar 14 to Mar 29 | View Details |
| Cyber Security Training | Mar 17 to Apr 01 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .















