Mindtree is an Indian-origin MNC that renders IT technology and consulting solutions to many clients. This company has a workforce of nearly 40k employees all over the world. Mindtree offers services across multiple domains, including cloud computing, data analytics, ERP, e-commerce, etc. Further, this company provides R&D services in video surveillance, IT infrastructure management or MWatch, integrated test methodology, or More
Mindtree offers a robust platform for its employees to learn and excel. But at the same time, acquiring a job in Mindtree is not a walk in the park. You must be thorough with Mindtree interview questions and learn them intelligently to crack the interview.
On this note, MindMajix content experts have prepared this blog with the top 60 Mindtree interview questions and answers to help learners of various expertise levels. This blog's Q&A is divided into three sections. You can directly jump into the correct section based on your expertise level.
- Mindtree Interview Proces
- Mindtree Technical Interview Questions with Answers
- Leadership Principles
- Tips
- FAQs
- Conclusion
Top 10 Frequently Asked Mindtree Interview Questions
- What do you mean by PYTHONPATH?
- Describe Python functions
- Define data integrity.
- List out the uses of SQL.
- What do you mean by Java thread lifecycle?
- Define state object in ReactJS.
- How can you prevent re-renders in ReactJS?
- List the types of automation testing.
- What is the use of Power BI?
- Where is Power BI data stored?
Mindtree Interview Process
Mindtree interview consists of three rounds: online assessment, technical interviews, and HR interviews.
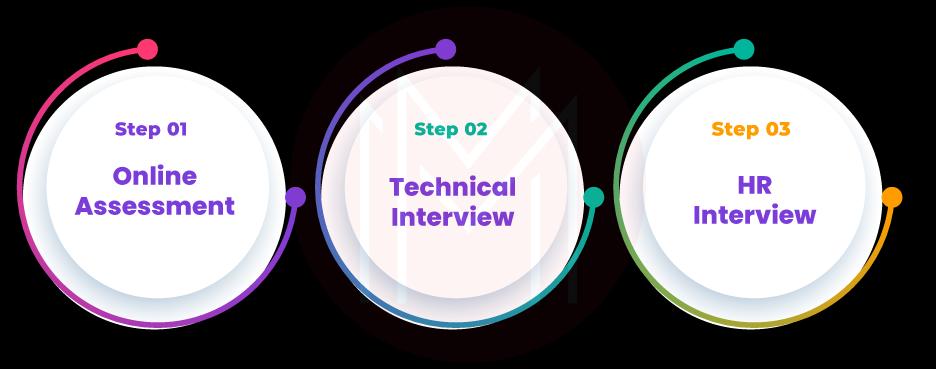
Let’s look into the rounds deeply one by one.
Round: 1 - Online Assessment
In this round, you will be asked various questions from the following three sections to test your quantitative, written English, and coding ability.
Quantitative: The assessment will include questions to check your quantitative and analytical skills. No doubt you must be quick and accurate to clear this round.
Written English: The assessment will include questions to test your knowledge of English tense forms, prepositions, antonyms, synonyms, etc. Additionally, you will also be asked to write a few short passages to test your writing abilities.
Coding: The assessment will have questions to code for at least two problems. The difficulty level of the coding would be either easy or medium, but there won't be any need for complex coding. Mainly, you will be asked to write codes in C, Python, or C++ languages. To clear this round, you must be familiar with programming.
Round: 2 - Technical Interview
Only when you clear the online assessment you will be allowed to attend the technical interview. In this round, your technical expertise will be tested in-depth. You will be asked questions about your previous experience, projects worked on, and achievements.
To clear this round successfully, you must be thorough in computer fundamentals, including data structures and algorithms, computer networks, operating systems, etc. Mainly, you must have expertise in programming languages such as C, Python, and C++. This round may have additional rounds based on the performance of your initial rounds.
Round: 3 - HR Interview
It is one of the key rounds of the Mindtree interview process. Even if you have attended technical rounds successfully, you must tackle this round intelligently. In this round, they will test your attitude, problem-solving skills, and stress management in many ways. To pass this round successfully, you must know Mindtree’s core values, leadership principles, culture, etc.
Moreover, you must provide accurate answers to the questions that are shot at you based on the information provided in your resume. And there will be common questions related to your short and long-term goals, why Mindtree, willingness to switch over locations, challenges, your leadership qualities, etc. So, you must prepare thoroughly before you attend this HR round.
| If you want to enrich your career and become a professional IBM BPM Developer, then visit Mindmajix - a global online training platform: "IBM BPM Training" This course will help you to achieve excellence in this domain. |
Mindtree Technical Interview Questions
Mindtree Python Interview Questions
1. What exactly are the packages and modules?
Modules are essentially Python files that come with .py extensions. The files may have classes as well as functions. A module can import other modules as objects. We use the import statement for the same.
When it comes to packages, it is a folder or directory. A package may contain sub-packages and modules.
Packages eliminate clashes between module names. They support the hierarchical structuring of module namespaces using dot notation. Besides, we can quickly create packages in Python.
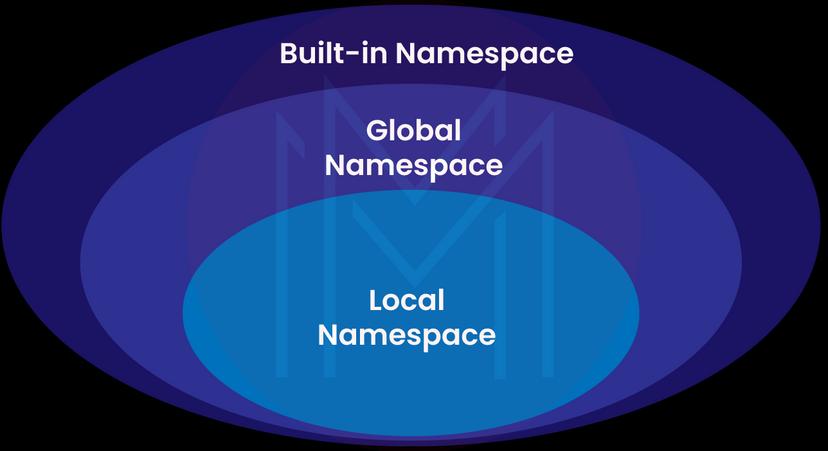
2. Why do you use namespaces in Python and name their types?
Know that Python maintains a namespace in dictionaries. We use Namespaces to ensure every object in a Python program has a unique name. As a result, it eliminates name conflicts between objects.
Following are the different types of namespaces.
3. What do you mean by PYTHONPATH?
It is essentially an environment variable used to add directories when importing a package or module. The interpreter uses this variable to determine the module that must be loaded. A Python program can access these modules and packages. It is possible to use PYTHONPATH to ensure that the imported files exist in the directories. Besides, PYTHONPATH helps maintain libraries we don't install in the global default location.
4. What is the role of Python's dir ( ) and help ( ) functions?
The help function displays the documentation of functions, modules, etc. If we don’t pass an argument in this function, then the help utility is initiated in the console.
The dir () function returns a valid list of attributes in addition to method objects. But it works differently for various objects. When it comes to module objects, it returns a list of attributes. Similarly, when it comes to class objects, it returns a list of valid attributes along with base attributes. If we don’t pass any argument, it returns a list of attributes in the current scope.
5. What do you understand by iterators in Python?
An iterator is nothing but an object that remembers its state. With iterators, we can iterate over strings, lists, etc. We use the _iter_ ( ) method to initialize iterators.
6. Explain the types of Python literals.
Literals are nothing but a value or data assigned to a variable. There are many types of literals, as shown below:
- String literals: Two types of string literals are single-line literal and multiline. Single-line literals have a single line, whereas multiple-line literals have multiple literals. Note that single-line strings are enclosed in a single quote. Double quotes enclose numerous line strings.
- Boolean literals: These literals contain true or false values.
- Numeric literals: There are three numeric literals used in Python. They are integer, float, and complex. These literals are typically immutable.
- Special literals: Python has only one special literal known as ‘none’. We use this literal to define a NULL variable. Also, we use this literal for the end of lists.
7. Describe Python functions
It is a block of code we can use in a program as and when required. A function contains an arguments list, a valid name, and a body. The main thing is that functions simplify modular programming. When it comes to Python, it provides many built-in functions. Not only that, it allows users to build their own functions as well.
In Python, there are three types of functions.
8. State the difference between remove ( ) and del functions.
We use the 'remove ( )' function to delete a specific data element from a list regardless of location. On the other hand, we can use the 'del' statement to delete a data element in a specific location in a list. The index value is used to specify the element's location in the del function.
9. Write a Python program to count the vowels in a given string.
Program:
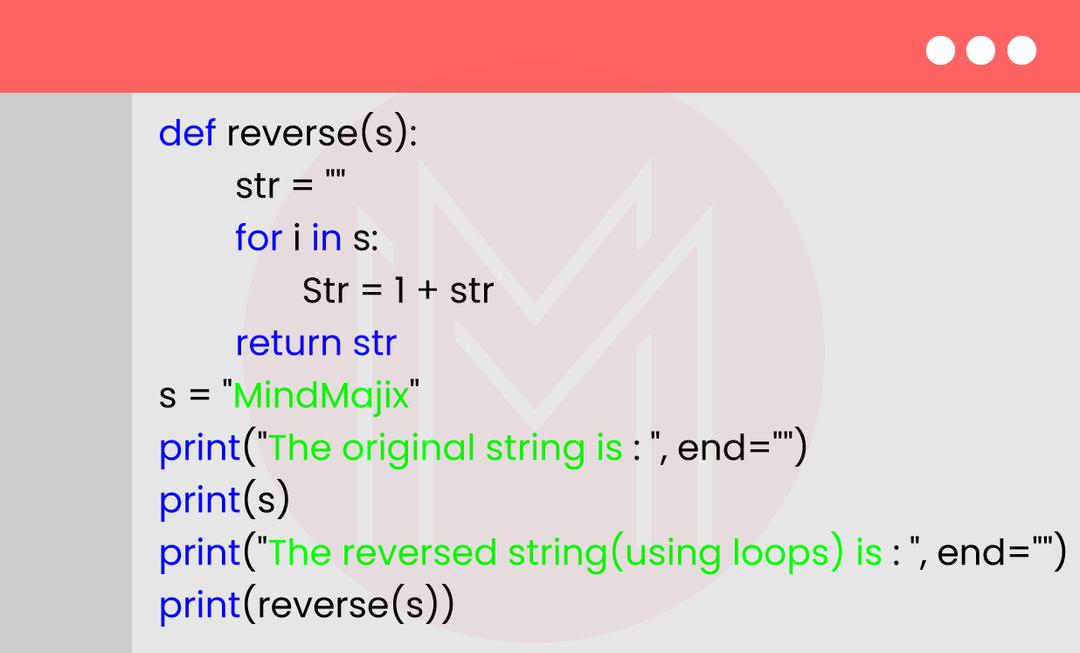
Output
310. Create a Python code to find the nearest value from the given NumPy array.

Output:
0.5581
Mindtree SQL Interview Questions
11. Briefly describe the super key, foreign key, and candidate key.
- Super Key: We use an attribute or group of keys to identify table rows. Typically, super keys are the supersets of candidate keys.
- Foreign Key: It denotes a single or set of columns of a table stored in a database. The columns are usually associated with the primary key of another table.
- Candidate Key: like super key, it is an attribute or group of attributes that we use to identify tuples of a table. Note that candidate keys have the same strength as primary keys.
12. Define data integrity.
It is the ability of data to keep up its consistency and accuracy throughout its lifecycle. It is one of the crucial aspects considered in software design in addition to implementation.
13. Mention the clauses used with SELECT statements in SQL.
WHERE, GROUP BY, ORDER BY, and HAVING are the clauses used with SELECT statements.
We use the WHERE clause to filter records based on certain conditions.
GROUP BY clause can be used to group records based on identical data. It is typically used with aggregate functions and generates summarized results.
We will use the ORDER BY clause to sort field records in ascending or descending order.
We use the HAVING clause and the GROUP BY clause to filter records in a table. It is essential to note that the WHERE clause is entirely different from the HAVING clause because we use the HAVING clause to filter aggregated records.
[Related Article: SQL Interview Questions]
14. Briefly describe the relationships used in SQL.

One-to-one: It is a relationship made between two tables. It means that a record in a table is associated with a record in another table.
Many-to-one: It is similar to the previous one. Many records in tables are associated with a single record in a table.
One-to-many: It is a relationship made between a record in a table and multiple records in other tables.
15. List out the uses of SQL.
SQL is a query language that performs various operations in a database. Jotted down are the uses of SQL.
- It executes queries in a database
- It inserts, deletes, and updates data in a database
- It fetches data from a database
- It creates a new table or view in a database
- It creates a new database
16. Explain pattern matching in SQL.
In pattern matching, wildcards are used instead of writing the exact word. We can use the LIKE operator with wildcards to retrieve the required data.
There are four ways by which we can fetch the required data.
- By using the % wildcard for a simple search
- By using % wildcard twice
- By using the NOT keyword
- By using the _wildcard to match the pattern based on position
17. Describe User-Defined Functions.
UDF or User-Defined Function helps to create functions using SQL expressions. User-defined functions accept parameters, perform operations, and return a value. We can define UDF in two ways: persistent and temporary. We can reuse a persistent UDF in multiple queries and use a temporary UDF in a single query.
Furthermore, UDFs provide many benefits, such as quick execution, modular programming, and reduced network traffic.
Two types of user-defined functions are denoted below:
- Table-valued functions – They return a table. A single SELECT statement is used to return the table.
- Scalar functions – they return a scalar value. The value is usually defined in the RETURNS clause.
18. Is a zero equivalent to a NULL value?
No. A NULL value is not equivalent to a zero or blank space. This is because NULL is the unavailable value for performing arithmetic operations. We can consider a NULL value as a missing value or unknown value.
19. Differentiate the Truncate and Delete SQL statements.
| Truncate | Delete |
| We use this statement to remove all table rows. | We use this command to remove specific rows of a table. |
| It is a DDL statement | It is a DML statement |
| The WHERE clause is not used. | The WHERE clause is used. |
| It doesn’t support indexed views. | It supports indexed views. |
20. Compare NO SQL with SQL.
| NoSQL | SQL |
| It uses a dynamic schema. | It uses a predefined schema. |
| It takes work to process complex queries. | Complex queries can be quickly processed. |
| Scaling is done horizontally. So, we must add more servers to balance loads. | Scaling is done vertically. So we need to add SSDs and RAMs to balance loads. |
| It supports CAP Theorem. CAP stands for Consistency, Availability, along with Partition tolerance. | It supports ACID properties. |
Mindtree Java Interview Questions
21. What exactly is ClassLoader in Java?
ClassLoader is nothing but a subsystem of JVM. It loads the required interfaces and classes to the JVM when needed.
There are totally three built-in classloaders in Java as follows:
- Bootstrap classloader
- System classloader
- Extension classloader
22. What is precisely JVM?
JVM stands for Java Virtual Machine. It is a runtime engine that enables a computer to run Java programs. It is achieved by converting Java codes into byte codes. In other words, the JVM loads, examines, and executes codes. Also, JVM calls the main method in a Java program.
23. What do you mean by Java thread lifecycle?
A thread in Java goes through various stages throughout its lifecycle. Below are the multiple stages of a Java thread lifecycle.

24. What do you understand by static variables in Java?
It is the variable declared only in the class itself. No other instance cannot use the variable. Simply put, only one copy of the variable is available in memory, no matter how many class instances are created. The main thing about using a static variable is that it simplifies memory management. Simply put, it makes a Java program memory-efficient.
25. State the various access specifiers used in JVM.
Access specifiers are nothing but keywords. They help to define the access scope of a method, class, or variable.
Java comes with four access specifiers, as mentioned below:
- Public
- Default
- Protected
- Private
26. Compare static and instance methods.
| Instance method | Static method |
| It is a method that is not declared static. | It is a method declared static. |
| We do need objects to call static methods. | Objects are not required to call static methods |
| Both static as well as non-static variables can access instance methods | Non-static variables cannot access static methods |
27. Is it possible to declare a constructor as final?
No. It is not possible to declare a constructor as final. This is because constructors never inherit. If we declare a constructor, the compiler will throw an error definitely.
28. State the differences between checked and unchecked exceptions in Java.
| Checked exceptions | Unchecked exceptions |
| They are checked during the time of compilation. | They are checked during the time of execution. |
| They support using ‘throws’ keywords. | They don’t support using these keywords. |
| They are the subclass of the exception classes. | They are not part of the exception classes since they are runtime exceptions |
| The JVM needs the exception to handle these exceptions. | The JVM doesn’t need the exception for the same. |
| FileNotFoundException and IOException are checked exceptions. | ArithmeticException and NullPointerException are unchecked exceptions. |
29. Write a Java code to perform a recursive binary search.
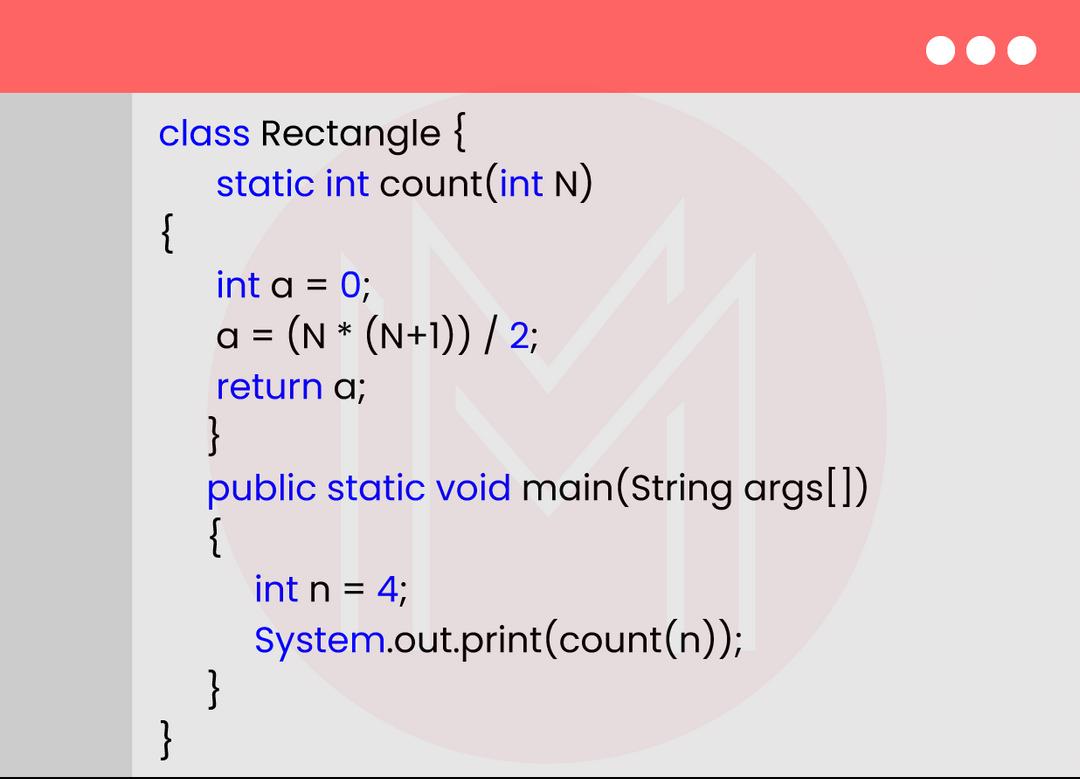
Output:
2
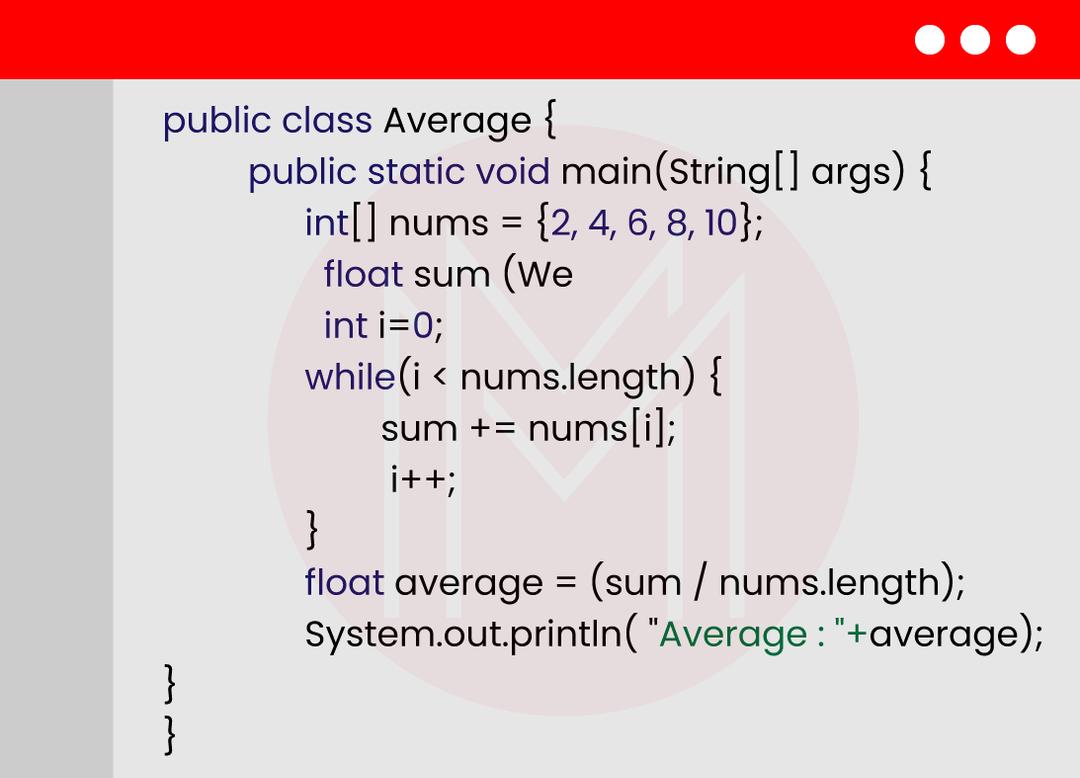
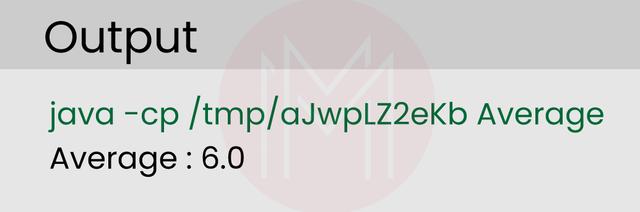
30. Create a Java program to find the average of given numbers.
Mindtree React JS Interview Questions
31. List the advantages of ReactJS.
- Scripting is simple
- It comes with a component-based architecture
- It is easy to learn and use
- Mobile app development is simplified
- It ensures a stable code structure
32. What is precisely useState( ) in ReactJS?
The useState ( ) is nothing but a built-in React hook. It allows having state variables in functional components. In other words, it will enable tracking state in a function component. Here, the state denotes the data that needs tracking in applications.
This hook typically returns an array with two values. One value is the current state, and another is the function needed to update the state. Besides, we can use this hook when the DOM is manipulating something dynamically.
33. What do you mean by JSX?
JSX stands for JavaScript XML. With JSX, we can write HTML codes inside JavaScript. We can also place them in DOM without using any function. Note that DOM represents Document Object Model.
34. Define state object in ReactJS.
Every component in ReactJS contains the built-in state object. This object has all the property values of the component.
In a way, state objects control the behavior of ReactJS components. If there is any change in any property value of a state object, then it leads to the re-rendering of the component.
35. What is the role of prop drilling in ReactJS?
We use props to pass data from the higher hierarchy to a component in a deeper order. The props can go deep until it reaches the required hierarchy level.
[Related Article: ReactJS Interview Questions]
36. Briefly Describe React hooks.
They are essentially built-in functions. It allows using state along with lifecycle methods in react components. As a result, we can improve the reuse of codes and navigate the component tree flexibly.
The main thing about react hooks is that we can use all the features of hooks without writing class components. In other words, we cannot use hooks in class components.
37. Why do we use Custom Hooks?
It is a function of JavaScript. With custom hooks, we can replace render props as well as Higher Order Components(HoCs). It also reduces the amount of nesting required. Custom hooks will help to avoid multiple layers of abstraction.
38. How can you prevent re-renders in ReactJS?
Re-rendering of a component occurs when props are changed. Not only components, but re-rendering may also happen in child components. If we don't update the re-rendering components, it will significantly affect the applications' performance.
We can prevent re-rendering using the ‘shouldComponentUpdate ( )’ method.
39. How React Hooks is different from Classes.
| React Hooks | Classes |
| We use react hooks in functional components. | We use classes in class-based react components. |
| It won’t require the declaration of constructors. | It is necessary to declare constructors inside class components |
| It doesn’t use the ‘this’ keyword in state declaration. | It uses the ‘this’ keyword for state declaration. |
| The ‘usestate’ feature makes react hooks ‘easy to use’. | No single function is used for ease of use. |
| It supports implementing context and Redux API. | Classes are not preferred for context and redux API. |
40. Differentiate Controlled and Uncontrolled Components.
| Controlled Components | Uncontrolled Components |
| They are managed by React state. It means that their internal states don’t play any role | They are managed by their own internal states. |
| Data usually flows from the parent component to other components. | It flows within components. |
| The parent component controls data. | DOM controls data. |
| We can easily debug these components. | We cannot easily debug these components. |
| It has good control over the data. | It needs better control over data. |
| The complexity is less. | The complexity is high. |
| It does validation control. | It doesn’t do validation control. |
| It is faster. | It is slower. |
Mindtree Automation Testing Interview Questions
41. List the types of automation testing.
We can list the types of automation testing in functional and non-functional testing.
Functional testing:
- Unit testing
- Smoke testing
- Integration testing
Non-functional testing:
- Performance testing
- Keyword-driven testing
- Regression testing
- Data-driven testing
[Related Article: Automation Testing vs Manual Testing]
42. Define the test environment.
A test environment denotes a computer or a server. This is where developers or testes test software or a piece of software. The following are the necessary components of a test environment.
- A computer or server with all the configurations similar to a production environment.
- Test database similar to a production database
- Sample test data to test software or piece of code.
43. What do you mean by cross-browser testing?
It is essential to know that users may use any web browser to run web applications. So we need to test web applications in all browsers to check their compatibility and adaptability. We can ensure that users get the same experience in any browser. Thus, we can achieve increased customer satisfaction and boom business productivity.
44. What do you mean by automated regression testing?
This testing is conducted to check whether a newly added feature in no way affects the performance of the software. We can use different frameworks and tools to conduct automated regression testing.
45. Mention the best practices that we should follow in automated testing.
Here are the best practices that we should follow in automated testing.
- Being accurate with what to automate
- Removing uncertainty in test cases altogether
- Performing test cases purely based on skill and experience
- Keeping on the test tests in a database unfailingly.
- Choosing the correct frameworks and tools
46. List the essential qualities of a tool or framework we use for automated testing.
- It supports the test environment
- It should have good debugging capabilities
- It must be easy to use
- It should perform database testing
- UI must be user-friendly
47. Briefly describe the risks associated with automated testing.
Following is a brief of a few risks associated with automated testing.
- Steep learning curve: Learning testing tools and frameworks takes work. Testers must have decent expertise to use the tools and derive valid results.
- Unexpected results: sometimes, the testing tools may generate unexpected results deviating from the expected ones.
- Selection of tools: we need to select testing tools carefully. It means that we must verify the compatibility and adaptability of the tools thoroughly. Otherwise, it would be a waste of time and resources.
- Tedious Maintenance: We must keep up with the test results and cases. Sometimes, preparing the tool takes a long time, which will take a toll on productivity.
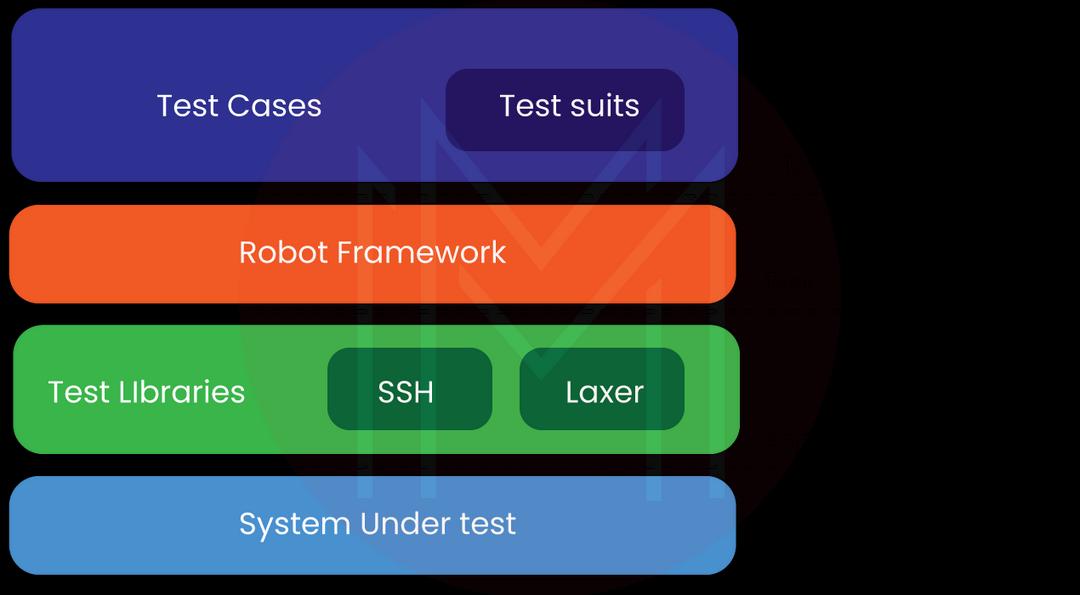
48. Describe Robot Framework.
It is an open-source automation framework widely used for testing robotic process automation. Most of the libraries of this framework are also open-source. Besides, it is a platform-independent tool that is built in Python.
49. Can you automate the testing of CAPTCHA?
No. We cannot automate the testing of CAPTCHA.
50. Is it possible to achieve 100 % automated testing?
No. It is not possible to get 100% automated testing. Mainly, checking the background or using CAPTCHA will restrict the efficiency of automated testing. At this time, it is better to use manual testing.
Mindtree Power BI Interview Questions
51. What is the use of Power BI?
With Power BI, we can:
- Connect to various data sources
- Transform and then model the raw data
- Create reports, charts, and graphs
- Sharing data with others
In short, we can convert raw business data into valuable visual data. So we can make informed decisions.
52. What is the significance of Power Pivot?
Power pivot extends the analytical capabilities of MS Excel. Know that it is one of the add-ons offered by Microsoft Excel 2010.
53. List out the filters used in Power BI.
Following are the filters used in Power BI.
- Manual filters
- Cross drill filters
- Include/exclude filters
- Pass-through filters
- URL filters
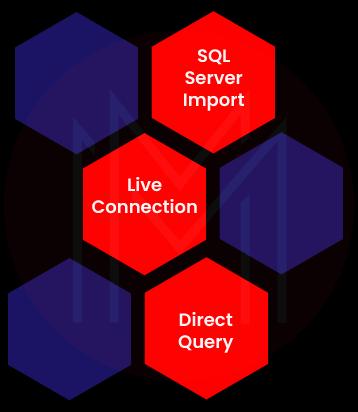
54. Mention the different connectivity modes of Power BI.
The below graphic shows the different connectivity modes of Power BI.
[Related Article: Power BI Interview Questions]
55. Where is Power BI data stored?
Microsoft Azure is the cloud service associated with Power BI. Following are the locations where power BI data is stored.
- Azure Blob Storage
- Azure SQL Database
56. What is the significance of responsive slicers in Power BI?
We can resize a responsive slicer into various sizes and shapes. As we change the responsive slicer, the report's data also adjusts. Note that responsive slicers work in mob applications too.
57. Compare Tableau and Power BI.
| Tableau | Power BI |
| It can handle a large amount of data. | It can handle only a limited amount of data. |
| It is the best tool for experts. | It is the best tool for novices and experts. |
| UI is user-friendly. It comes with drag-and-drop features. | UI is complex when compared with Power BI. It provides powerful features |
| It uses MAX for the same. | It uses DAX for measures as well as dimensions. |
| It connects with most databases in addition to web services. | It is mainly used with SQL servers and MS Excel. |
| It offers good customization features. | Customization options are limited. |
58. Can you elaborate on how relationships are defined in Power BI Desktop?
- Relationships are defined both manually as well as automatically.
- Manually: primary as well as foreign keys are used to relate tables.
- Automatic: the relationship between tables is both created and detected automatically.
59. Why Do we use the custom visual file?
When prepackaged files are insufficient, we use custom visual files. Custom files can be created and imported as we perform for prepackaged files.
60. How can you reshape data in Power BI?
We can use a data editor to manage rows and columns of data. In other words, it allows the reshaping of data smoothly.
Mindtree Leadership Principles
The leadership model of Mindtree is built based on three principles – Leadership Competence, Learning Agility, and Self-awareness.
Leadership Competence
This principle has four tracks – Coach, Thought Leader, Ninja, and Rainmaker.
A coach is a leader who inspires people, shares vision, and creates more leaders.
A thought leader is the one who creative thinker and expert in Mindtree business.
Ninja is the leader who ensures quality output and raises business values to new levels through operational excellence.
Rainmakers find new opportunities and create new segments to impact the business directly.
Learning Agility
This principle is based on the ability of leaders to adapt to challenging situations. In other words, leaders must have good agility to cope with and handle changing conditions. So leaders should have the qualities such as curiosity, interpersonal skills, the ability to manage ambiguities, and resourcefulness.
Self-awareness
This leadership principle deals with the ability of a leader to handle challenging situations and achieve success. In other words, the leader must be able to strengthen the weak areas through their leadership skills.
Tips to crack Mindtree interview
Tip #1: Research the company
First and foremost, research Mindtree in all aspects. Know who the clients of Mindtree are and the services and consultations that Mindtree offers to the clients. Understand the sectors where Mindtree has its multiple businesses. Learn the vision of the company, its leadership principles, and its work culture. Please ensure you have learned everything about Mindtree without leaving no stone unturned.
Tip #2: Strong Analytical Skill
Mindtree will test your quantitative and analytical skills through the online assessment. Before attending the interview, go through many quantitative mock tests, puzzles, and aptitude questions. It will enhance your analytical skills better.
Tip #3: Sound Technical Competence
In the technical round, interviewers will scrutinize your technical competence in popular programming languages such as C, Python, and C++ in-depth. So, you must have sound technical knowledge to answer tough technical questions.
Tip #4: Review your Attitude
Undeniably, attitude plays a vital role in a person’s success. In the HR round, interviewers will test your attitude in many ways. For example, how are you responding to stressful situations, solving critical problems, and your collaboration skills? Before attending the interview, review your attitude and weigh the positives and negatives accurately. Collect feedback on your attitude from your friends, mentors, and colleagues. Then plan to improve your attitude accordingly.
Mindtree FAQs
1. Do you think the Mindtree interview is challenging to crack?
Yes. Mindtree interview is a bit difficult to crack. You need to face tough technical questions and HR rounds. However, if you have prepared well, the Mindtree interview will be a cakewalk.
2. What questions might be asked in the Mindtree technical interview?
The questions will be about modern programming languages, computer fundamentals, computer networks, Operating systems, data structures, algorithms, etc.
3. How many rounds of interviews must you go through in a Mindtree interview?
There are totally three rounds – Online Assessment, Technical Interview, and HR Round.
4. How the passing criteria are set in the Mindtree interview?
You need to clear all three rounds of interviews consecutively. The three rounds are online assessment, technical interview, and HR interview. You won't be allowed for the next round if you don't clear any of the three.
5. How to effortlessly crack Mindtree technical interviews?
You need to have strong technical expertise in computer programming and fundamentals. Learn the programming concepts thoroughly but at the same time get some hands-on experience in coding.
Conclusion
In the Mindtree interview process, you must go through three rounds: online assessment, technical interview, and HR interview. And all these 30 Mindtree interview questions and answers might have helped you in the best way. The tips to ace your Mindtree interview must have been helpful to you. Of course! You can easily take this article as a guide to cracking your Mindtree interview. If you want to prepare further, you can successfully attend MindMajix courses and ace your Mindtree interview.
If you wish to learn about IBM BPM, you may enroll in an" IBM BPM Course" and achieve certification.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| IBM BPM Training | Feb 21 to Mar 08 | View Details |
| IBM BPM Training | Feb 24 to Mar 11 | View Details |
| IBM BPM Training | Feb 28 to Mar 15 | View Details |
| IBM BPM Training | Mar 03 to Mar 18 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .













