In today’s world, no one can deny that protecting data in devices and applications is one of the prime tasks for organizations. This is because users may use the same device for performing their official and personal works. Especially when they are away from the office, they use smartphones and tablets to access organizational applications and data. Of course, it might compromise the security of the resources and not-so-positive things. For example, users may open official emails or apps on their personal devices and copy the data on the devices, which in turn questions the security of the data. Therefore, a need arises to protect organizational data and resources in this scenario.
Microsoft Intune – one of the excellent Microsoft products now comes in to resolve this problem and helps protect organization data and apps on personal devices. Microsoft Intune allows limited use to employees based on their roles and job requirements, even on company-owned devices.
This blog will discuss Microsoft Intune, why we need it, its key features, how it will support protecting the data and resources, etc.
- What is Microsoft Intune?
- Why is Microsoft Intune?
- Architecture
- Features
- Mobile Device Management (MDM)
- Mobile Application Management (MAM)
- Use-cases
- Benefits
What is Microsoft Intune?
Microsoft Intune, a cloud-based tool, part of Microsoft’s Enterprise Mobility + Security Suite (EMS), performs Mobile Device Management (MDM) as well as Mobile Application Management (MAM) to protect data on mobile devices. In other words, Microsoft Intune manages devices and applications to protect data and resources from misuse or data loss. To do so, you must configure policies, isolate organizational data from personal data, control access to resources, and many more. For example, using Microsoft Intune, you can prevent sending emails outside your organization. Know that mobile devices could be laptops, smartphones, or tablets.
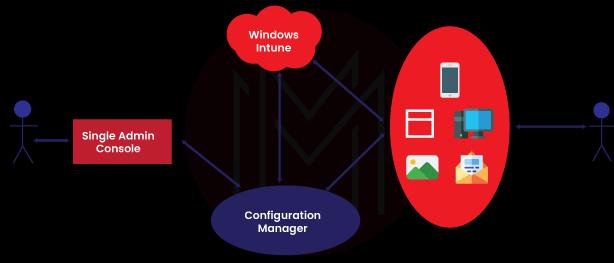
Why is Microsoft Intune?
Are you wondering why we should use Microsoft Intune to secure the apps and devices? Let’s get the answer right below:
- Microsoft Intune supports all platforms such as Windows, Linux, Android, macOS, iOS, etc.
- You can protect and control organizational data from any mobile device such as laptops, tabs, and smartphones.
- You can deploy applications on devices and control the access remotely
- With Microsoft Intune, you can create policies and rules to manage data on the devices
- You can ensure compliance with organizations' security policies for both devices and applications.
| If you want to enrich your career and become a professional in Microsoft Intune, then enroll in "Microsoft Intune Training". This course will help you to achieve excellence in this domain. |
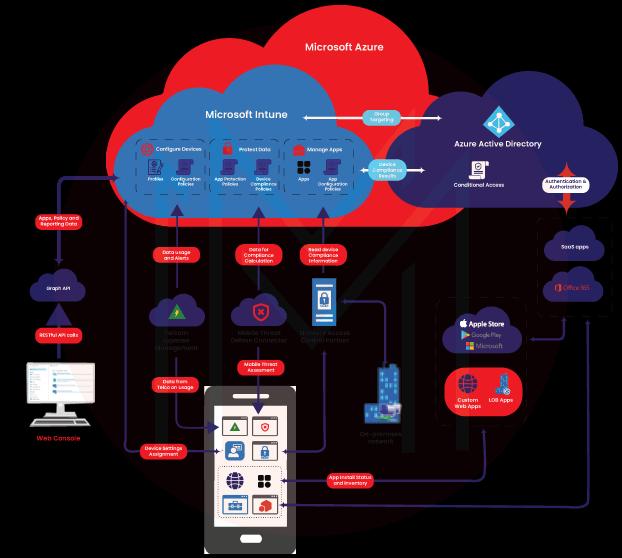
High-level Architecture of Microsoft Intune
Microsoft Intune architecture consists of Microsoft Azure Active Directory, Office 365, SaaS Apps, App stores, APIs, etc. Microsoft coordinates with all these services to manage apps and configure devices, thereby protecting data.
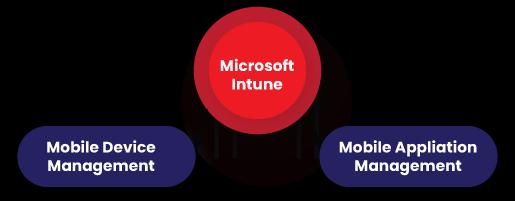
Key Features of Microsoft Intune
Microsoft Intune protects devices and applications with the following features. They are given as follows:
- Mobile Device Management (MDM).
- Mobile Application Management (MAM).
1. What is Mobile Device Management (MDM)?
With Microsoft Intune, you can control both company-owned and personal devices. Microsoft Intune offers a feature known as enrolling devices. By enrolling, you can protect your personal and company-owned devices by creating VPN connections, setting passwords and PINs, and setting up threat protection.
At the same time, users won't prefer Microsoft Intune to control their devices completely when using their own devices. Microsoft Intune offers options to overcome this issue by providing separate access to resources using personal and official credentials. In addition, users can set up policies such as MultiFactor Authentication (MFA) to securely access organization data and applications.
What is Microsoft Intune MDM Lifecycle?
All we know is that every device has a lifecycle, indeed. And the life cycle begins from enrolling, configuring, protecting, and ends with retiring.
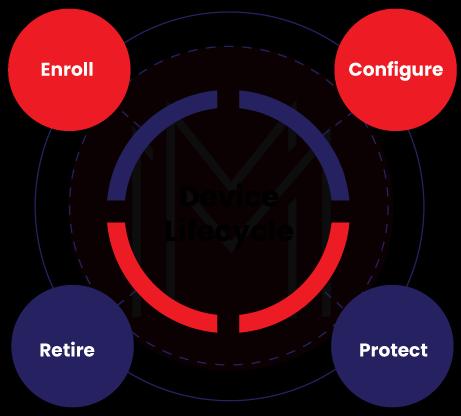
- Enrolling: Your device could be a mobile, tablet, or PC, which might be working on any platform such as Windows, Linux, etc. first of all, all you have to do is that you need to enroll your devices with Microsoft Intune. Device enrolment is a vital process made by Microsoft Intune, which makes sure users and devices are in alignment with organizational policies and settings. With enrolling, admins can collect the list of devices accessing the organizational resources. It enables them to issue certificates for users to access Wi-Fi and VPN connections. It also helps to generate security compliance reports for users and devices.
- Configure: In this stage, you must choose device protection policies based on the work requirements. Then, you have to configure your devices with the required features and capabilities. On the same track, configuring must be taken place to protect organization resources from unauthorized access. With Microsoft Intune client software, you can configure even PCs for device management capabilities.
- Protect: These days, protecting devices from malicious attacks is a much-needed task. With Microsoft Intune, this can be achieved in three ways: MultiFactor Authentication (MFA), Windows Hello for business settings, and setting policies for protecting Windows. At first, MFA provides an extra layer for authentication for accessing resources. Secondly, Windows Hello acts as the alternative method for signing-in in the form of a gesture or Windows Hello. At last, with Microsoft Intune client software, you can protect PCs through software updates, end-point protection, and Windows firewalls.
- Retire: As all we know, there might be frequent situations such as a device being lost or stolen or needing replacement. At these times, you need to retire or wipe the devices entirely. If not, it will increase the chances of organizational data being misused. So, retiring or wiping out of devices must be performed as fast as possible by removing them from device management, resetting the devices, and wiping out the corporate data.
How does Microsoft Intune MDM Protect Data and Devices?
Microsoft Intune MDM protects data and devices through two policies – configuration policies and device compliance policies.
Let’s check them out as below:
- Configuration Policies: You can configure the profiles and settings of the devices using these policies. Simply put, the configuration of devices, such as end-point protection, setting software update behavior, provisioning certificates for authentication, etc., can be carried out using these policies.
- Device Compliance Policies: These policies support creating device requirements for different platforms considering OS versions, use of disk encryption, etc. Over and above, you can manage security settings such as software updates, VPNs, and security baselines through device compliance policies.
Additionally, Microsoft Intune combines with Microsoft Azure AD, which will help isolate personal data from organizational data. And users will be restricted from copying and pasting or saving data on their personal devices.
2. What is Mobile Application Management (MAM)?
MAM is used to protect the data of apps for both custom and store apps. With MAM, you can manage apps on both personal devices and company-owned devices. MAM helps admins for assigning apps to user groups and devices. Not only this, they can assign apps to specific groups too. MAM supports configuring apps with specific settings and updates. Moreover, it helps to view the track reports on accessing applications by users.
How Does Microsoft Intune MAM Protect Apps?
Microsoft Intune protects apps using App protection policies. With these policies, you can control access to applications. With enrolled devices, App protection policies provide an extra layer of protection. For instance, if users sign in to their devices with their organizational credentials, they can access the organizational resources. At the same time, if they use their personal credentials to sign in to devices, they cannot access organizational resources.
Microsoft Intune provides a feature known as – Microsoft Intune Managed Apps. These apps are integrated with App SDK or Microsoft Intune App wrapping tool. Also, they are managed by Microsoft Intune app protection policies. Using the Managed Apps only, users can access organizational data. As a result, you can avoid data leaks and keep organizational data safe. Note that Managed Apps don’t interfere with personal data; instead, they deal with organizational data.
How Does Microsoft Intune integrate with other Services?
Microsoft Intune integrates with various other services of Microsoft and reaps many benefits. To list a few, Microsoft Azure AD is one of the integrations that Microsoft Intune makes. Similarly, Microsoft Intune integrates with Azure Information Protection for data protection. Besides, Microsoft Intune can be used with the Microsoft 365 Suite of products.
Let’s discuss the integrations one by one below:
- Integration with Microsoft 365: Initially, Microsoft Intune creates user groups and manages them with Microsoft 365. For example, you can create iOS or macOS groups using Microsoft 365. As a next step, you can push policies into these groups using the following actions: accessing App stores, backing up iCloud, using Airdrop, using Apple’s Web filter, and many more.
- Windows Defender: With this integration, you can protect Windows client services and control access to organizational resources. For this, ‘Windows Defender SmartScreen’ instantly identifies suspicious activities in the files and apps stored or installed on mobile devices. Similarly, ‘Microsoft Defender for end-point supports eliminating security breaches on mobile devices.
- Microsoft Azure AD: Know that Microsoft Intune with Azure AD offers conditional access to organizational resources. Simply put, devices can only be allowed to access SharePoint, emails, and other apps on a conditional basis.
| Learn Microsoft Intune Interview Questions and Answers that help you grab high-paying jobs |
What are the Use-cases of Microsoft Intune?
Following are the brief descriptions of a few use-cases of Microsoft Intune.
- Secured access to emails and Data on Mobile Devices: Mobile devices and apps can access organization emails only if they are enrolled with Microsoft Intune. This setup ensures that the devices comply with the organization's security requirements. Also, business app servers support to make secure access to on-premises data from mobile apps. Microsoft Intune-managed certificates help access on-premises data with a standard VPN gateway or proxy. Besides, Microsoft Intune’s App Wrapping tool and App SDK help access data within your line-of-business app, which resists others from accessing the data.
- Secured Access to Data through Microsoft 365: ESM allows devices and apps to access Microsoft 365 only if they meet the compliance needs you have put in place. In this regard, data containment policies help prevent data from being shared with other apps and storage. On the same line, app protection policies streamline the use of organization apps to access resources safe and secure.
- Offering a BYOD Program to all Employees: As mentioned earlier, employees get enrolled to access organizational apps and data from their personal devices. But, how would employees' mindset be toward allowing employers to manage their own devices? No doubt, they won’t prefer it. To resolve this, Microsoft Intune offers a solution – BYOD. Here, BYOD stands for Bring-Your-Own-Device. Nowadays, BYOD is gaining popularity among companies since it decreases hardware expenses and increases the chances of using mobile devices. In this regard, Microsoft Intune supports organizations in two ways. The first is that Microsoft Intune separates personal and organizational data on personal devices. The second one is that the app protection policies of Microsoft Intune support preventing data misuse from unmanaged apps and storage.
- Issuing Corporate-owned Phones to Employees: These days, we can’t deny that employees are moving everywhere, either inside or outside of the organization – for their work's sake. Consequently, they must carry mobile phones wherever they move and access organization apps and data respecting security. For this, Microsoft Intune offers a security solution through bulk provisioning and management. According to this program, Microsoft Intune integrates with the Apple device enrolment program and Samsung Knox mobile security platform to authenticate mobile phones and control access to resources.
- Issuing limited-use Shared Tablets to Employees: Consider Retail employees, they use mobile devices like tablets increasingly for many reasons, which could be – checking the status of stocks or sales or customer interaction, etc. At the same time, they need mobile devices in a limited way. With Microsoft Intune, employees can use mobile devices in a limited-use mode and maximum time.
- Preventing Employees from Accessing Microsoft 365 from unmanaged Public Kiosk: There might be situations where employees may access organizational resources from public computers. Without a doubt, we realize that it will question the security of the organization's resources. So, with the help of Microsoft Intune, you can prevent employees from accessing resources from untrusted locations and allowing only the enrolled devices to access the same.
Benefits of Microsoft Intune
Microsoft Intune offers many benefits, from listing the devices to wiping data out of them. Let’s go through them below.
- You can keep the list of assets of mobile devices through enrolled programs and control the access to resources and data.
- You can deploy and retire devices.
- You can wipe out and disable lost and stolen devices.
- Updates can be made on mobile devices regardless of platforms.
- You can configure devices based on the required security standards.
- Pushing certificates to access Wi-Fi and using VPN networks and emails by which make sure the security considerations.
- You can collect reports of compliance of devices and users.
- Microsoft Intune is used to track devices from the central point.
Conclusion
On the whole, Microsoft Intune offers a unified solution to protect organizational data from mobile devices. As a part of it, it isolates personal and organizational data on personal devices. Not only devices, Microsoft Intune helps to control the access to organization applications from mobile devices. We conclude that Microsoft Intune opens the door to producing a more mobile workforce without compromising the security of resources. Without a doubt, Microsoft Intune will be a wonderful tool to break the walls of organizational premises to liberate the workforce to work from anywhere and at any time – respecting security at the same time.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Microsoft Intune Training and Certification | Feb 28 to Mar 15 | View Details |
| Microsoft Intune Training and Certification | Mar 03 to Mar 18 | View Details |
| Microsoft Intune Training and Certification | Mar 07 to Mar 22 | View Details |
| Microsoft Intune Training and Certification | Mar 10 to Mar 25 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .



