- Home
- Blog
- Internet Of Things
- What is ICMP?

- Big Data in IoT
- Big Data vs IoT
- IoT Architecture
- IoT Career
- IoT Devices
- IoT Examples
- IoT Hardware and Software
- IoT Interview Questions and Answers
- IoT Tutorial - What is IoT?
- Top 10 Reasons Why You Should Learn IoT
- Technology and Protocols of IoT
- Top 10 Real World IoT Applications
- Internet of Things Devices
- What is IoT? - A Complete Guide
- Real Time Applications of Internet of Things
- loT Solutions Architect
Setting up a secure and effective communication between devices is necessary to ensure the privacy and integrity of a network. Because of this, protocols such as ICMP are essential and are used extensively in modern times. The term "Internet Control Message Protocol," or ICMP, will be defined in this article. It will also provide examples of why you should use it.
What is ICMP - Table of Contents
- What is ICMP?
- What is ICMP Used For?
- ICMP Work
- Risk
- Benefits
- Limitations
- ICMP Port
- ICMP Ping
- ICMP vs TCP
- ICMP Message Codes
- DDoS Attacks
- FAQs
What is ICMP?
The ICMP (Internet Control Message Protocol) is a network layer protocol that network devices use to identify problems with connectivity.
The primary purpose of ICMP is to ensure that data reaches its destination on schedule. ICMP is often used in network devices, such as routers. Although ICMP is necessary for error reporting and testing, it may also use for distributed denial-of-service (DDoS) attacks.
| If you want to enrich your career and become a professional in ICMP, then enroll in "IoT Online Training". This course will help you to achieve excellence in this domain. |
What is ICMP Used For?
ICMP is mainly used for error reporting. If some of the data does not arrive as expected when two devices are linked via the internet, ICMP can be used to cause errors that can go from the transmitting device to the receiving device.
For instance, a router cannot handle massive data packets. In that situation, the router will drop the data packet and send the sender an ICMP message notifying it of the problem.
ICMP is also frequently used as a diagnostic tool to evaluate the performance of a network. ICMP is used by both ping and traceroute.
- Traceroute
- Ping.
Ping and traceroute are signals that are sent to establish whether or not the data transfer was successful. The traceroute report details the various nodes and circuits traveled by a data packet on its way to its final destination. It is made up of the physical routers that are responsible for managing the data.
- Traceroute: Using the traceroute, you can also find out how long it takes for data to travel from one device to another. A hop is a trip that data takes between two routers. Using the information supplied by the traceroute, it is feasible to identify the devices along the path slowing traffic.
- Ping: Similar to the more complex traceroute, a ping can help determine where a packet is sent. How much time passes between two specified locations is reported. The ICMP echo request and ICMP echo reply are used in the ping process and thus make the usage of ICMP very convenient.

In addition, ICMP may be used to degrade the performance of a network. Assaults like a Smurf attack, an ICMP flood, and a ping of death are used to accomplish this goal. These attacks overload a device on the network and prohibit it from functioning normally.
How Does ICMP Work?
The ICMP is a prominent protocol in the Internet Protocol (IP) family. However, it is not a part of any transport layer protocol like User Datagram Protocol (UDP) or Transmission Control Protocol (TCP).
ICMP is a connectionless protocol, which means that the device sending the data doesn't have to first connect to the device receiving the data before sending the data. It is because ICMP is one of the connectionless protocols. IMCP is the primary distinction between it and other protocols, such as TCP, which requires an active connection between the two devices. It is impossible to send a message until both devices have completed a TCP combine and confirmed that they are ready.
Each ICMP message is sent as a datagram with an IP header that includes the ICMP information. A datagram is an independent, self-contained packet of information. Think of it as a little envelope carrying a crucial part of a larger message being transmitted via a network. ICMP packets are Internet Protocol packets that have the ICMP protocol in their IP data part. For completeness, ICMP messages also include the original message's whole IP header. The destination system can use this data to track down the faulty packet and fix it.
[ Related Article: IoT Technologies and Protocols ]
What is the Risk of Allowing ICMP?
Threat actors have looked for ways to exploit the environment they are attacking, just like they would with any platform, protocol, service, operating system, and application. They have discovered ways to improve their ability to maintain transfer data and connections, communicate with command & control servers, Etc. Threat actors have discovered techniques to misuse ICMP in the instance of ICMP:
1. Ping of Death
It was the first example of ICMP misuse. This improper Ping request might cause a system to crash. Updates to the protocol have rendered this attack ineffective. Today, ping floods (a rapid series of ping queries) are still feasible, but firewalls should detect and prevent them.
2. ICMP Tunneling
ICMP packets can conceal malicious data and conversations sent across networks without being detected by firewalls. However, as data tunneling through other protocols (such as DNS and HTTPS) is commonplace nowadays, this is less of an ICMP-specific risk.
3. Ping Sweeps
Attackers can quickly discover the hosts on a network by sending out ping queries across all of the networks in a subnet. Again, unless the threat actor is scanning the same subnet as a compromised endpoint, firewalls should be able to identify and block them (in which case, firewall rules are rendered ineffective). Once again, this is something that firewalls should be able to do.
While it's true that ICMP may be abused, it's clear that most harmful acts via ICMP are no longer a threat and are effectively worthless in modern networks. Furthermore, ICMP is still important today.
Benefits of ICMP
ICMP is used by network devices to transmit error messages in addition to allowing administrators to debug the network with Ping and Tracert commands. Administrators use these notifications to diagnose network connectivity difficulties. An excellent example is a destination or gateway host delivering an ICMP message to the source host if there is an issue or a change in network connectivity that necessitates notice, such as a destination host or networking becoming inaccessible, packet loss during transmission, Etc.
Additionally, ICMP is frequently used in network performance and connection monitoring tools to detect the presence of problems that the network team has to address. The ICMP protocol, which consists of questions and responses, is a fast and easy way to test connections and trace the source of delivery and performance issues in a network.
[ Check out Internet of Things Architecture ]
Limitations of ICMP
The following is a list that describes the two primary drawbacks of the Internet protocol. Before you can fully understand the ICMP requirements, you need to know what these limitations are.
- No Error Reporting
- No Communication.

1. No Error Reporting
If the router drops a packet, it might be because of a mistake; however, there is no way for the sender to be informed of this issue because of how the IP (internet protocol) is designed. Assume that a data packet's lifetime is complete while being transmitted over the internet and that the time to live field's value has fallen to zero; in this situation, the data packet is deleted.
2. No Communication
Devices often need to communicate with one another, but Internet Protocol does not provide a standard way for them to do so. For example, before the data transmission, the host must identify whether the destination is still functioning by checking its vital signs.
What is ICMP Port?
One of the protocols of the ICMP Protocol Suite, generally known as the IP/TCP protocol suite, is the ICMP. The internet is used to communicate via this group of protocols. It means that aside from the internet layer, it is not available. Port numbers don't seem to be detected until the transport layer, which is the ICMP layer below it in the stack.
ICMP uses types and codes, even though it does not implement the idea of ports as Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) do. The most common forms of ICMP traffic are echo reply and echo request (both of which are used for the ICMP Ping protocol), as well as TTL (time-to-live), used for Traceroute.
What is ICMP Ping?
Ping messages refer to both the ICMP echo request message and the ICMP echo reply message. System administrators may manually test for connection between network devices with the ping command, which is a helpful troubleshooting tool. In addition to that, they use it to check for delays and losses in the network's packets.
When it comes to Ping Monitoring, ICMP Ping is by far the most helpful protocol to use. It operates by repeatedly pinging a specific device. A particular device or service on the network is targeted with an ICMP echo request during this kind of check. The target server or device then immediately responds with an ICMP echo reply. That indicates that the connection was successful and that the targeted device or server is operational without any problems.
If the ICMP ping time measured in ms (milliseconds) is significantly longer than usual, this almost certainly indicates problems with the network.
[ Check out Top Reasons to Learn IoT ]
ICMP vs TCP- Difference
There are differences across protocols, and familiarity with those differences helps speed up the process of finding and fixing bugs. Most individuals familiar with the internet know that information does not just flow through their Ethernet line like water from a tap. Instead, the material is being conveyed in discrete units known as packets, bits of data small enough for routers and other devices to send back and forth with little chance of corruption.
The difference between ICMP and TCP are as follows:
Transmission Control Protocol (TCP)
- The Transmission Control Protocol, also known as TCP, is one of the oldest protocols. TCP was a component of the first network transmission software, which later evolved into the IP used in contemporary networking.
- TCP is used because it is reliable, orders things (the packets are handled in a set order, not just as they come in), and fixes mistakes. TCP is used for many different things, like file transfers, email, and other tasks where getting data in the proper order and without mistakes is more important than getting it done quickly.
- TCP is the protocol that should be used in network diagnostic tools such as PingPlotter for evaluating particular instances when a TCP-like segment fails to reach its destination or has difficulty doing so. One excellent illustration of this is FTP. Suppose you see the ICMP traffic going via your FTP connection is limited or obstructed. In that case, you may begin using a TCP trace to determine where the FTP connection is being impeded along the path.
Internet Control Message Protocol (ICMP)
- ICMP is not like other data packet protocols like TCP. ICMP is a customized packet that is used to communicate between devices. It can send anything from redirect instructions to synchronization timestamps.
- ICMP is used for something completely different than TCP. Most people don't use ICMP as a data packet protocol. It is also a control protocol, which means it is not meant to interact with application data. Instead, it is used to send messages between different devices, such as instructions to reroute traffic or timestamps to ensure that different devices are in sync. Always remember that ICMP is not a transport protocol that moves data from one device to another.
What are the ICMP Message Codes?
ICMP is a protocol that sends and receives error reports, control messages, and management inquiries, among other data types. Simply being the first code field in the ICMP block, it can communicate a considerable amount of information.
The following are examples of possible initial code field values and their descriptions.
- 0: echo reply – used for ping
- 3: destination unreachable
- 4: source quench – the router is overloaded
- 5: redirect – use a different router
- 8: echo request – used for ping
- 9: router advertisement reply
- 10: router solicitation
- 11: time exceeded – used for traceroute.
| Learn Top IoT Interview Questions and Answers that help you grab high-paying jobs |
How is ICMP Used in DDoS Attacks?
DDoS (Distributed Denial-of-Service) attacks are increasingly common cyber dangers. They are launched to overwhelm the victim's server, device, or network. As a result, standard users cannot use the victim's services. An attacker can use ICMP to carry out these assaults in a variety of methods, as follows below:
1. ICMP Flood Attack
An ICMP flood DoS attack also called a Ping flood attack, is a common type of Denial-of-Service attack in which an attacker tries to send too many ICMP to echo requests packets to a target device to stop it from working (pings).
Network devices can be "pinged" using ICMP echo-request and echo-reply messages to check their connectivity and the health of the connection between the sender and the device. Pinging a network device also determines whether or not the sender can interact with the device. The network is coerced into responding with an equal amount of request packets and reply packets when the target is bombarded with request packets. Because of this, the objective will be inaccessible to the typical traffic flow.
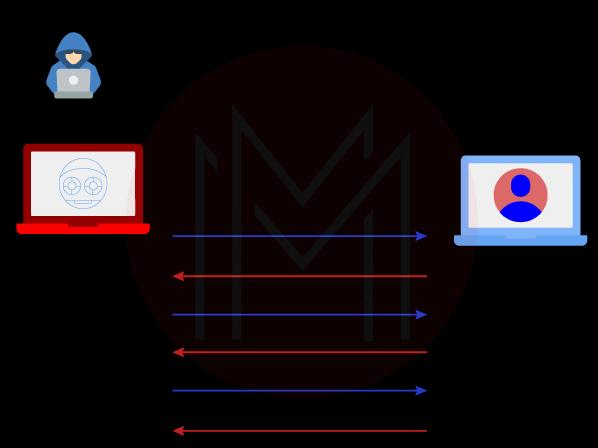
2. Ping-of-Death Attack
When an attacker sends a ping to a vulnerable system that exceeds the system's maximum packet size, this is known as a "ping of death" attack. It usually results in a system freeze or crash. The packet is fragmented while traveling but is reconstituted at its destination to its original size, which exceeds the limit. Due to the large size of the packet, a buffer overflow occurs.
Today, the "ping of death" strike is mainly forgotten, lost to the pages of history. However, older pieces of networking hardware may still be at risk.
3. Smurf Attack
An attacker will carry out a Smurf attack by sending an ICMP packet that contains a fake source IP address. The target is inundated with unsolicited ICMP packets due to the networking equipment's response to the packet sent to the faked IP address. The Smurf assault, much like the "ping of death," can only be performed with legacy equipment in the modern day.
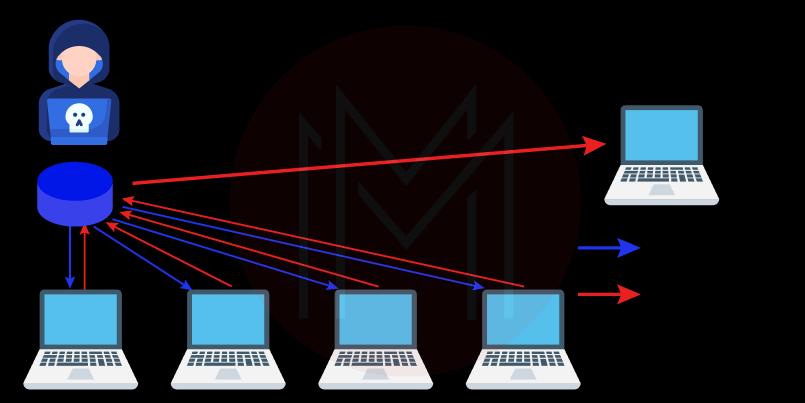
Regarding layer 3 DDoS attacks, ICMP isn't the sole network layer protocol exploited. For example, attackers have previously employed GRE packets in their attacks. Network-layer DDoS attacks are more common than application-layer DDoS attacks directed at websites.
Most Common ICMP FAQs
1. What is ICMP used for?
ICMP is a protocol used on networks. ICMP packets inform the compromised device when a network has a connectivity issue. It transmits control messages such as source quench, source route failure, and destination network inaccessible.
2. What is an ICMP example?
The "ping" tool, which employs an ICMP request and ICMP reply message, is an excellent example. ICMP may send a message to the source if a specific host or port cannot be reached.
3. Is ICMP a Ping?
The ping command relies on the Internet Control Message Protocol (ICMP), perhaps the most well-known application of ICMP. Whenever you type "ping," an ICMP echo request is sent to the remote host. An echo reply is sent back from the destination host.
4. Is ICMP a TCP or UDP?
ICMP is not linked to a transport layer protocol like TCP or UDP like the Internet Protocol (IP) is. It turns ICMP into a connectionless protocol, allowing devices to deliver ICMP messages without first establishing a connection with another device.
5. What is the ICMP Protocol?
The Internet Control Message Protocol, or ICMP, is a protocol used at the network layer and by network devices to identify problems with network communication.
6. What is the purpose of ICMP messages?
The purpose of ICMP messages is to offer feedback on difficulties connected to IP packet processing.
7. What port is ICMP?
Unlike TCP and UDP, ICMP does not rely on ports but not on types and codes. Popular ICMP messages include time-to-live-exceeded-in-transit, echo request (used for ping), and echo reply (used for traceroute).
Conclusion
ICMP is a remarkable network layer protocol enabling devices to report faults and enhance communication. It does this by working at the network layer. It should not be surprising that many system administrators use it regularly to better comprehend their networks using the well-known applications ping and traceroute. Finally, monitor your network adequately to keep it safe against DDoS attacks that exploit the protocol.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| IoT Training | Mar 07 to Mar 22 | View Details |
| IoT Training | Mar 10 to Mar 25 | View Details |
| IoT Training | Mar 14 to Mar 29 | View Details |
| IoT Training | Mar 17 to Apr 01 | View Details |

Viswanath is a passionate content writer of Mindmajix. He has expertise in Trending Domains like Data Science, Artificial Intelligence, Machine Learning, Blockchain, etc. His articles help the learners to get insights about the Domain. You can reach him on Linkedin



