- Linux Commands for Beginners
- Linux Environment Variables
- Linux File Permissions
- Linux Interview Questions
- Linux Kernel Tutorial
- Linux Networking Commands with Examples
- What is Linux? - A Complete Beginners Tutorial
- Linux vs Unix
- Linux Advanced Functions And Commands
- Introduction to Linux Operating System
- Monitoring Tools in Linux
- Top 10 Reasons Why You Should Learn Linux
- Shell Scripting Tutorial
- What is Linux Operating System?
- Arch Linux Vs Ubuntu
- Parrot OS vs Kali Linux
- Network Administrator Interview Questions
- Linux Projects and Use Cases
- Linux Connect to MySQL
- Linux Networking Tutorial
The name Kali Linux originates from Sanatan dharma, which means death, time, black, and Lord of Death: Shiva. Also, the OS was written right from the ground up. Kali Linux is the OS dedicated to ethical hacking and fiddling with networking utilities. The best part of the one-of-a-kind OS is that it is completely free for life.
In this article, we have enlightened the essential Concepts like Kali Linux Introduction, Uses, Advantages, Tools used, etc. which will help you understand About Kali Linux
Often regarded as Hacker Paradise, Kali Linux is a strategically curated OS that offers unparalleled power to network analysts and penetration testers. Kali Linux comes with a cutting-edge plethora of tools that are default in the OS. The tools make Kali Linux a swiss-knife for ethical hackers across the world.
Kali Linux came into being back in 2013, and it was a brainchild of Offensive Security which primarily focuses on training and certification based on cybersecurity. Offensive Security made use of the existing security module in Backtrack Linux, which was further redeveloped into Kali Linux, relying entirely on the Debian variant.
What is Kali Linux - Table Of Content
- Uses of Kali Linux
- Why use Kali Linux?
- Kali Linux - Development
- List of Tools in Kali Linux
- Cybersecurity professionals and Kali Linux
- Advantages of Kali Linux
- System Requirements for Kali Linux
- The Best Method to learn Kali Linux
| If you would like to Enrich your career with a Linux certified professional, then visit Mindmajix - A Global online training platform: “Linux Certification Course”. This course will help you to achieve excellence in this domain. |
Uses of Kali Linux
Kali Linux is mainly used to initiate advanced-level Security Auditing and Penetration Testing. The OS comprises numerous tools responsible for carrying out tasks like information security, security research, penetration testing, reverse engineering, and computer forensics.
There are a series of steps that professionals need to follow to ensure the proper installation of Kali Linux. In this holistic guide on the most revered OS in the world, we’ll take you through everything you need to know about Kali Linux’s uses. Before moving forward, the users need to understand why they need to use Kali Linux, given that several other computer OSes are perfect for commercial use. Remember, installing a different version of Kali Linux is different as each version comprises its package types.
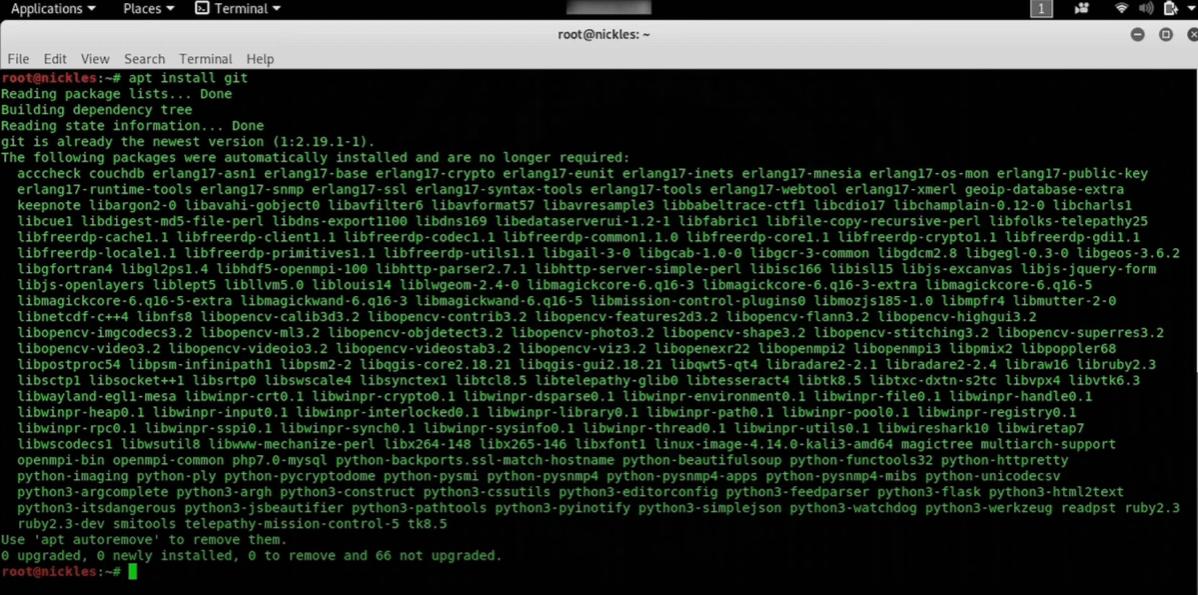
1. Install Git
Installing Git will allow you to download the sample codes from the repository of any git. Some might call this step cloning a repository; nevertheless, you’ll still need to use a git command.
To install Git, you’ll have to write: “apt install git”, and this step will solve the dependencies that need addressing in the OS. Check the image below for a better understanding. Then all you need to do is visit a GitHub repository, select anyone from the list, and you’re good to go.
2. Configure Bash Aliases
This process involves updating and upgrading the computer. By the looks of it, this method needs to be done frequently prior to installing software packages. Generally, Bash Aliases are saved in a file that you can update to add new ones. For updating Bash Aliases, the user has to type nano -/.bash_aliases and press enter.
Furthermore, the step will open a list of distinctive aliases.
| Related Article:- About Linux Operating System |
3. New-low Privileged User
Setting up a low privileged user is the need of the hour as it would require to stop logging into a route more miniature than ever. It would also ensure that the attacker cannot take over any computer whatsoever. The step plays a critical role as the software segment that runs like a route can take over a computer irrespective of any intervention.
In Kali Linux, adding low privilege users is relatively straightforward and straightforward. The command is:
"Add user {name of the user account}"
Once the command is entered, you'll have to enter a new password alongside other information like Room Number, Home Phone, and Work Phone. After entering the data, the user has to certify that the inputs are correct.
4. Install Terminal Multiplexer
It will oversee the installation of several scripts right from a similar terminal window. Generally, users transfer to a terminal window that runs a hand by enabling them to run different things on different taps.
Command to install Terminal Multiplexer is also simple. All you have to do is type: "apt install tilix". After the completion of the installation, users will have to type "Tillix".
5. Installing Hacking Tools
After you're done installing Kali Linux, you'll immediately figure that Kali Linux doesn't have tools. Installing tools one by one can be a slight hassle, so you can type:
"Sudo apt update && Sudo apt install and the name of the said data package."
6. Install TOR (Latest Version)
In Kali Linux, TOR serves as an essential tool to enlist privacy from DDoS attacks. TOR comes with an anti-censorship virtual which keeps hackers at bay. TOR can be a massive target for literally anyone who is trying to develop exploits. Ensure that TOR on Kali Linux is updated to the latest version in the market.
Before installing, it is crucial to consider the Kali repository to feature the latest version of TOR. However, downloading TOR and keeping it updated will solve 70% of your overall problems.
Why use Kali Linux?
There are numerous ways that you can implement to become an ultimate user of the OS. Specific uses that make Kali Linux different from other OS are:
- Free for life, beyond time: The OS is completely free throughout its existence.
- Offers several tools: Kali Linux comprises more than 600 unique tools that aid in security analysis, penetration testing, and other related devices.
- Open Source: Do you like Android OS over iOS? If you're one of the people who dig Android rather than iOS, then you're aware of the customization, usage that Android offers to users. As Kali is an integral part of Linux's extended family meaning it strictly follows the open-source criteria. The development tree of Kali Linux is available on Git, whereas the code is already available for tweaking.
- Multi-lingual support: The tools for penetration are written in the English language; the OS still supports multi-language. The idea is to get the OS popular among people hailing from different backgrounds from different backgrounds to come together and use the tool for their goals.
- Exponentially Customizable: Offensive Security's developers truly understand the necessity of building a highly customizable OS. The designing method of Kali Linux is enormous. If Kali Linux falls into the hands of adventurous users, then customizing the OS is only limited by the imagination.
| Related Article:- Tutorial on Linux |
Kali Linux - Development
The OS was the brainchild of Deavon Kearns and Mati Aharoni, who are also the core developers. It was the idea of the duo to rewrite Backtrack Linux completely. Moreover, the duration of the OS was a prime example of penetration testing across Linux. Development of the OS is made according to Debian OS as most of the code of Kali Linux originates from the Debian repositories.
The early development of Kali Linux began in March 2021 with only a handful of developers. Over time, only a few chosen developers were permitted to provide packages and mainly in a contained/protected ecosystem. The development of Kali Linux did conclude with the first release sometime in 2013. Over the years, the OS has witnessed massive updates that have benefitted cybersecurity professionals and analysts worldwide. Even to this day, Offensive Security oversees the whole development of Kali Linux.
List of Tools in Kali Linux
Kali Linux became incredibly popular as the OS comes with numerous cybersecurity tools from its default. Let's get into the popular cybersecurity tools that Kali Linux offers to users globally.
1. Aircrack-ng
As a suite of several tools which are used for assessing the Wi-Fi networking security, it focuses on the Wi-Fi security's crucial extent via Monitoring, Attacking, Cracking, and Testing. Tools are appropriately placed in the command line that further allows massive scripting options. Several GUIs have already taken the benefit of the said feature.
2. John the Ripper
It is a unique password cracking tool which is highly customizable. It combines several modes of interpreting that suit the needs of the individuals. The device could also run against several types of encrypted formats of passwords. Further, it performs other cracking techniques like brute force attacks and dictionaries.
3. Metasploit
The tool makes it easier for cyber professionals to carry out hacking. It is a fantastic penetration tool for testing. Metasploit transcends manual processes like gathering information, evades detection, gains access, and automates the whole process. The device is quite popular among cybersecurity professionals in the field of information security. Also, Metasploit is a formidable tool to test vulnerabilities and exploitations.
4. Wireshark
The open-source packet analyzer is used not just to view and evaluate the traffic on the network. Wireshark also makes it entirely imperative for systems administrators and security professionals. When the tool runs and is analyzed, it has a real-time traffic implication that runs through the network. Wireshark is a perfect tool for troubleshooting purposes.
5. Netcat
As a network tool, Netcat is used for reading and writing data across network connectivity. The device includes tons of features running from the port's scanning to transferring files and port listening. The tool can create almost any form of connection that is needed and is preferred during port scanning.
| Related Article:- About Monitoring tools in Linux |
Cybersecurity professionals and Kali Linux
The reason why cybersecurity professionals prefer Kali Linux is due to its source code. The way the developers designed the OS gave users all the access to tweak the OS as per their liking. So far, this is why Kali Linux still dominates the world of OS when it comes to ethical hacking, cybersecurity, and customization. Personalization played a critical role to make Kali Linux incredibly popular today. The personalization that Kali Linux offers is excellent for cybersecurity tasks.
Till 2019, the OS was specifically designed to have single root access for users. From 2019, users are provided with exclusive rights, and at the same time, they have access to everything that Kali Linux has to offer. Recently, the OS was then altered to provide accommodation to users using the OS for more than cybersecurity purposes.
Advantages of Kali Linux
Kali Linux comes with popular applications which are popular among users. These default applications are entirely free, and they support cross-platform integration. With Kali Linux, things get significantly more straightforward as it does all the essential hard work. Further, compiling the operating system applications makes Kali Linux a holistic operating system for cybersecurity and ethical hacking.
System Requirements for Kali Linux
Everything comes down to one thing, how much powerful a system do you need to run Kali Linux. Irrespective of how great the OS is, you still need to sport a minimum requirement to run Kali. Installing the OS is by far one of the simplest tasks in the world. Kali supports Intel, AMD, ARM-based processors. The hardware requirements to run Kali Linux are exponentially low. Check out the minimum requirements below:
- RAM of 2 GB
- Disk Space of 20 GB
- 32-BIT OR 64-BIT CPU (Single-Core Processor) with at least 2GHz or better clock speed
- Vivid monitor and HD Graphics Processor Unit
- Internet Connect (Broadband or Wi-Fi)
The Best Method to learn Kali Linux
Before you begin to learn the basics and the ins and outs of Kali Linux OS and how it supports cybersecurity, then follow the steps that follow:
1. Building Kali Linux via a virtual machine
Numerous freeware ways allow setting up hypervisors and then working together with virtual machines for deploying Kali Linux. The environment set by the virtual machine will aid in setting up as well as tearing down on several instances.
VirtualBox from Oracle is a popular yet free hypervisor. Upon installation, you can easily install and download the hypervisor directly inside the virtual machine. You should also install several other free distributions that Linux offers and then build them to several different distributors that the OS provides. The idea is to create a virtual machine like CentOS and Ubuntu.
2. Exploring cybersecurity tools in Kali Linux
After Kali Linux is installed into Virtual Machine, there are specific tasks that you need to do. For instance, you should look at several tools which are built directly into the OS. You'll be surprised to see that the devices are sorted in the form of categories. Ensure that you choose only one tool right from the variety and simply just begin working with it. Over time, you will learn about all tools but try to be patient.
3. Use the tools among legal hacking sites
It is entirely illegal to hack into any website that hackers aren't authorized to explore. However, several other websites are spread throughout the internet for this purpose. These websites are made to lure hackers to exploit them. Use any search engine you deem fit to exploit to test these tools.
Conclusion
Kali Linux is one of the simple and highly effective OS that is in existence. Given that the OS is not for beginners, but it's not rocket science, that beginning won't find its knack. You can start off learning about the tools one day at a time. However, if you're new to the realm of Linux, you can do a little research on other Linux operating systems to see how they work. Exploring other Linux-based OS will give you a heads up regarding where you're getting into it. There are specific points you still need to consider while using Kali Linux:
- Do not use tools from Kali Linux as opposed to systems that aren't authorized for providing access.
- All tools in Kali Linux are free from OS to hypervisors and cybersecurity tools.
- Learning everything you can about cybersecurity is nothing less than an investment. So invest your time and effort to make the most out of your career.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Linux Training | Feb 28 to Mar 15 | View Details |
| Linux Training | Mar 03 to Mar 18 | View Details |
| Linux Training | Mar 07 to Mar 22 | View Details |
| Linux Training | Mar 10 to Mar 25 | View Details |

As a content writer and storyteller, Raunaak Mitra regards himself to be a prodigy in writing. He firmly believes that language is borderless, and anyone can write as long as they have a strong narrative capability and the ability to emote feelings into words. Authors like F. Scott Fitzgerald and R. K. Narayan have influenced him to keep the writing as simple as possible for anyone to understand. Other than being well-versed about technological trends like AI, Machine Learning, AR, VR, Gaming, Microprocessors, Cloud Computing, Industry 4.0, literally any technological advancement (old or new), he also shares a knack to curate fiction on sci-fi, satire, and thriller genres.










