- Linux Commands for Beginners
- Linux Environment Variables
- Linux File Permissions
- Linux Interview Questions
- Linux Kernel Tutorial
- Linux Networking Commands with Examples
- What is Linux? - A Complete Beginners Tutorial
- Linux vs Unix
- Linux Advanced Functions And Commands
- Introduction to Linux Operating System
- Monitoring Tools in Linux
- Top 10 Reasons Why You Should Learn Linux
- Shell Scripting Tutorial
- What is Kali Linux ?
- What is Linux Operating System?
- Arch Linux Vs Ubuntu
- Parrot OS vs Kali Linux
- Linux Projects and Use Cases
- Linux Connect to MySQL
- Linux Networking Tutorial
A group of computers linked together for sharing resources is called a computer network. The primary resource shared on the network is the internet. In this advanced technology world, there are none who have never utilized the internet. So, it makes sense to learn computer networking and start your career in the networking domain.
Sometimes, it could be a little scary about what topics to cover to ace the networking job interviews in one go. We have collected the best network administration interview questions to simplify your interview preparation. To fuel your practice, go through these easy-to-read top network security interview questions and answers in 2024.
We have categorized Network Administrator Interview Questions into different levels they are:
Top 10 Network Administrator Interview Questions
- Explain FTP?
- Explain SSH?
- Describe Mesh Topology?
- What is Appletalk?
- Explain the Subnet mask?
- What is IPX?
- How does Tracert work?
- Differentiate HTTP and HTTPS?
- Explain Sneakernet?
- What is Clustering support?
Network Administrator Interview Questions for Freshers
1. Define Network?
A Network is defined as a set of devices linked to each other using a physical media link. In other words, a network is an interlinked group of similar things like computers, devices, people, etc. The below diagram represents a network:
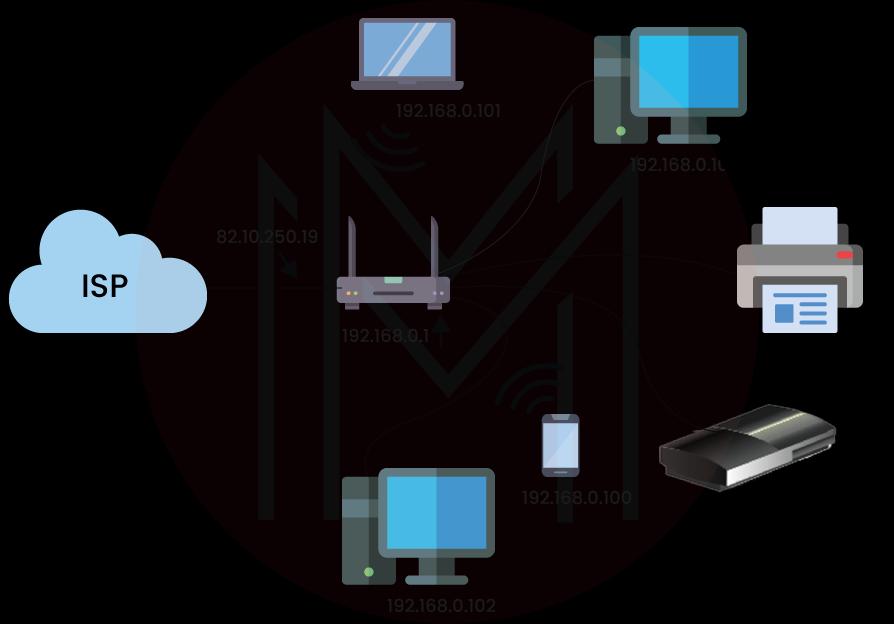
2. What is HTTP?
HyperText Transfer Protocol or HTTP is the primary protocol for glossy web content. Most webpages utilize this protocol for transmitting their web content and enabling the display and navigation of the links or “hypertext.” While HTTP can use various carrier protocols from system to system, the primary protocol and port utilized is TCP port 80.
| If you want to enrich your career and become a professional in Linux Networking, then visit Mindmajix - A global online training platform: "Linux Networking Training" This course will help you to achieve excellence in this domain. |
3. Explain FTP?
File Transfer Protocol, or FTP, is one of the main inherent protocols that must be retired. FTP is mainly designed as large file transfers, which can resume downloads if disrupted. We can access the FTP server through two different techniques: standard login and anonymous access. Both are the same; besides, anonymous access does not need the active user login, while the standard login does. FTP utilizes TCP ports 21 and 20. The following image gives you a detailed explanation of File Transport Protocol:
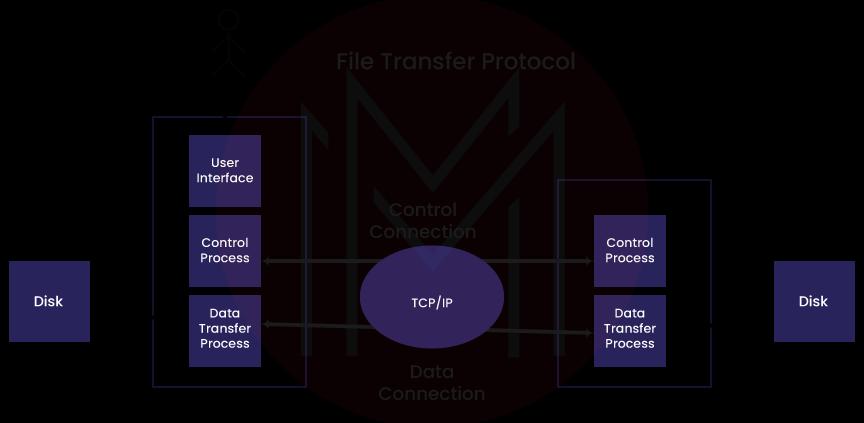
4. What is HTTPS?
Secure HTTP or HTTPS is used for designing identity verification. HTTPS utilizes SSL certificates to verify whether the server you are connecting to is the one it says. While HTTPS has an encryption capability, it is generally considered insufficient; moreover, encryption methods are required whenever possible. HTTPS traffic goes on TCP port 433.
5. Describe OSI Reference Model?
OSI is called Open System Interconnection. It is a reference model that tells how applications can interact with each other in a networking system. It also displays the network's relationship and describes the network's communication. Following are the different layers of the OSI Model:
- Physical Layer
- Data-Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
The following diagram gives a pictorial representation of OSI layers:
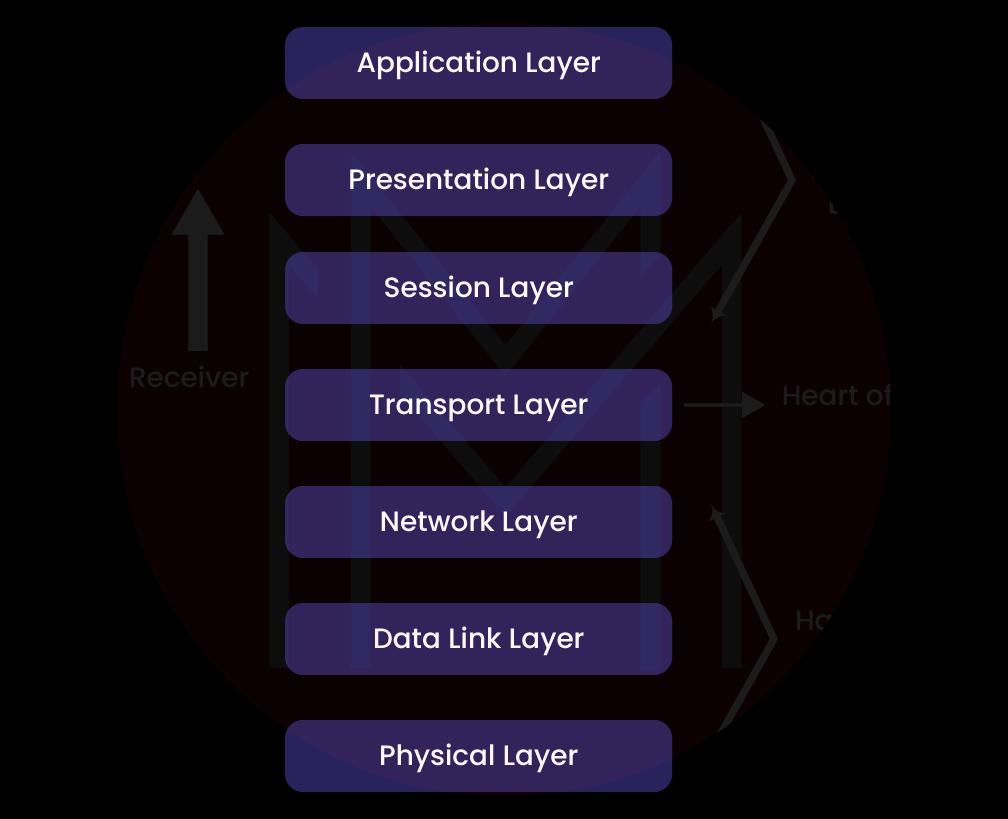
6. Describe DHCP?
DHCP(Dynamic Host Configuration Protocol) is the default method to connect to a network. The implementation differs throughout operating systems, but the description is that there is a server on the web that distributes IP addresses when requested. After connecting to the network, the DHCP request will be broadcast from the new member system. The DHCP server will reply and issue the address lease for a variable time. If the system connects to the network, it will publish a new address by that server, yet if it re-connects to the original network before the lease is up, it will re-publish the same address.
7. Explain SSH?
Secure Shell or SSH is well-known to Linux users but has the main deal that can be used. SSH is designed to create a secure tunnel between the devices, whether switches, systems, toasters, thermostats, etc. SSH also has the unique ability to tunnel other programs using it, the same as the VPN concept, so even programs or insecure programs running on unsecured connections can be utilized in a secure state if appropriately configured. SSH runs on TCP port 22.
8. Explain UDP?
UDP is a connectionless protocol. UDP messages include packets that are transmitted one by one. It also verifies the integrity at arrival time. It is not connection-oriented; thus, the program can send a lot of packets to other packets.
9. What is TCP?
TCP is a connection-oriented protocol. It reads the data as a stream of bytes and sends the message to fragment boundaries. TCP messages go through the internet from one system to another. TCP rearranges data packets in a particular order. It does error checking and makes error recovery. It also utilizes handshake protocols like ACK, SYN, and SYN-ACK.
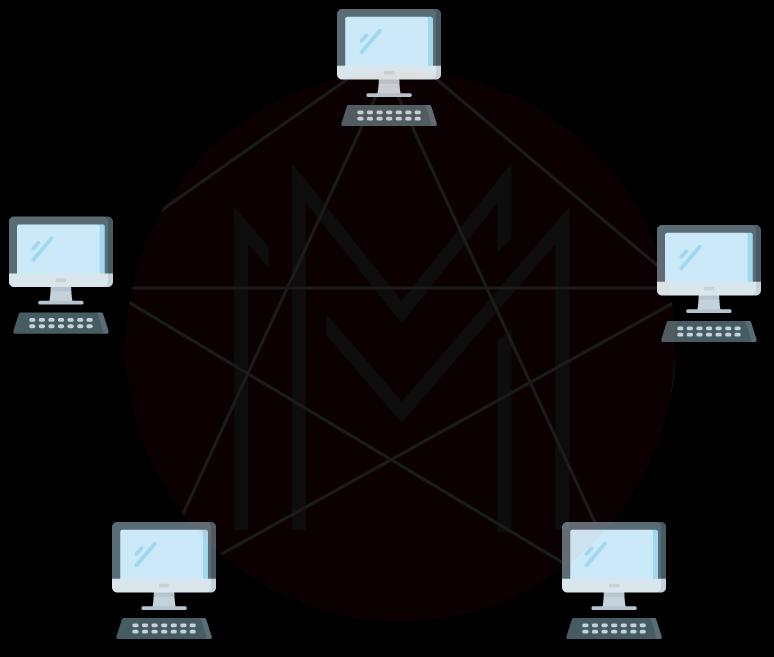
10. Describe Mesh Topology?
The mesh topology has a distinct topology in which each network system connects to another system. It builds a point-to-point(P2P) connection between all the network devices. It provides a high level of redundancy, so even if a single network cable fails, data still have a substitute path for reaching its destination. Following are the different kinds of mesh topology:
Partial Mesh Topology:
Almost every device is connected similarly to a complete topology in this topology. The only contrast is that few devices are linked with two or three.
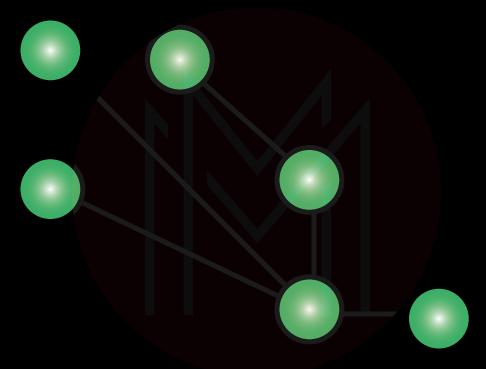
Full Mesh topology:
Every device or node is directly linked with each other in this topology.
| Related Article: "Linux Operating System Introduction" |
11. Describe IP Classes?
The IP address is the numerical label allocated devices to devices linked to the computer network that utilizes the IP for communication. IP addresses serve as identifiers for the particular machine on the web. Classful addressing is the network addressing the internet’s architecture from 1981 till Classless Inter-Domain routing was released in 1993. This addressing method classifies the IP address into five separate classes. Classes A, B, and C provide the address for the networks of three unique network sizes. Class D is utilized for multicast, and Class E is detached exclusively for experimental purposes.
12. Explain ICMP?
ICMP is Internet Control Message Protocol. Like UDP and TCP, it is the element of the IP suite and utilizes IP port number 1. Most users will identify names using tools like traceroute and ping since this is the protocol that these services run, among other things. The primary use of ICMP is to tell the systems when they try to connect remotely if the other end is available.
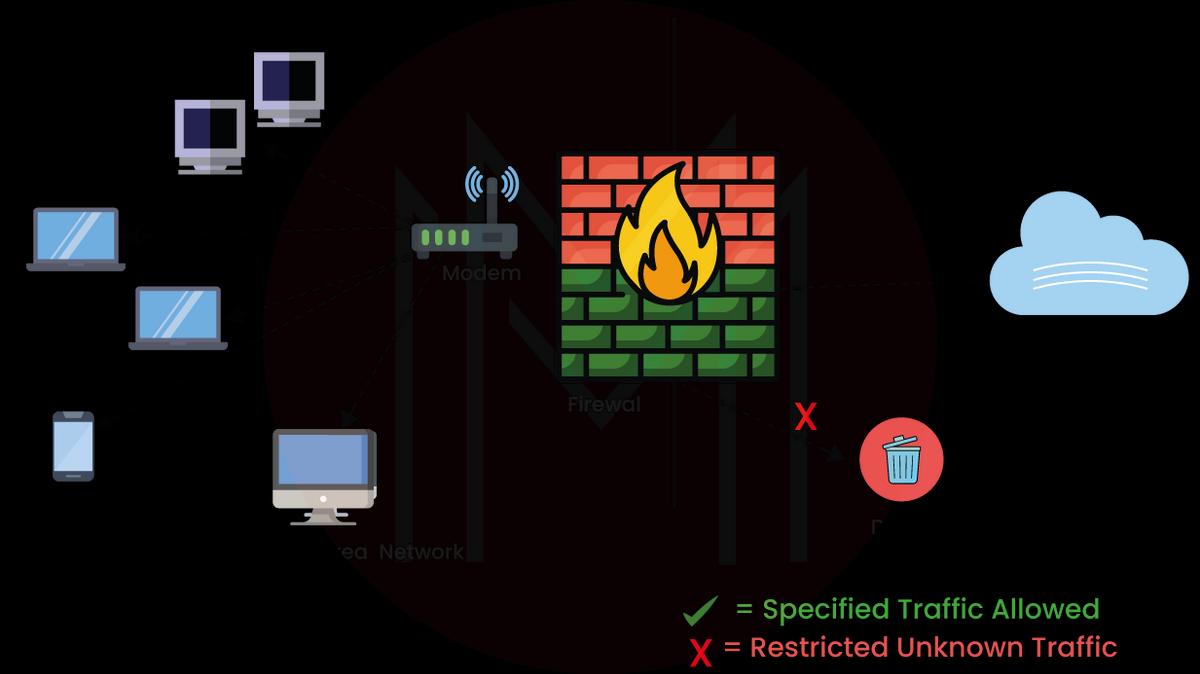
13. Explain the Firewall?
A firewall is a network security device that filters and monitors the outgoing and incoming traffic per the enterprise’s previously used security policies. A firewall is a barrier that settles between the private internal network and the public internet. The firewall's primary purpose is to allow non-threatening traffic in and maintain dangerous traffic out. The following diagram gives a graphical representation of Firewall:
14. What is Appletalk?
AppleTalk is the networking protocol used in Apple Macintosh computers and networking devices to interact with each other that was released in 1984. In 2009, with the introduction of macOS, the Appletalk protocol was replaced by TCP/IP.
| Related Article: "Linux Interview Questions" |
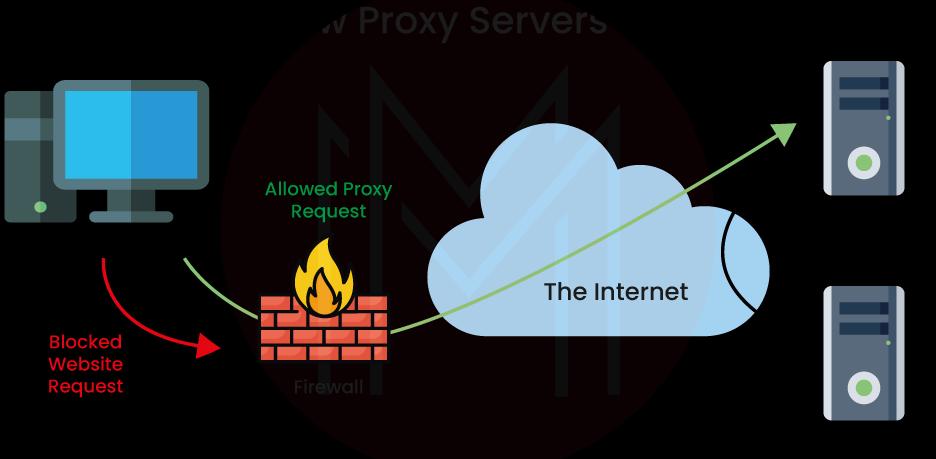
15. What is the use of a Proxy Server?
A Proxy Server is the system or the router that offers the gateway between the users and internet. It is the server, known as an “intermediary,” because it goes between web pages and end-users, they visit online. When the computer links to the internet, it utilizes the IP address. So, it enables us to stop cyber attackers from entering into a private network. The below diagram tells you how a proxy server works:
Network Administrator Interview Questions For Experienced
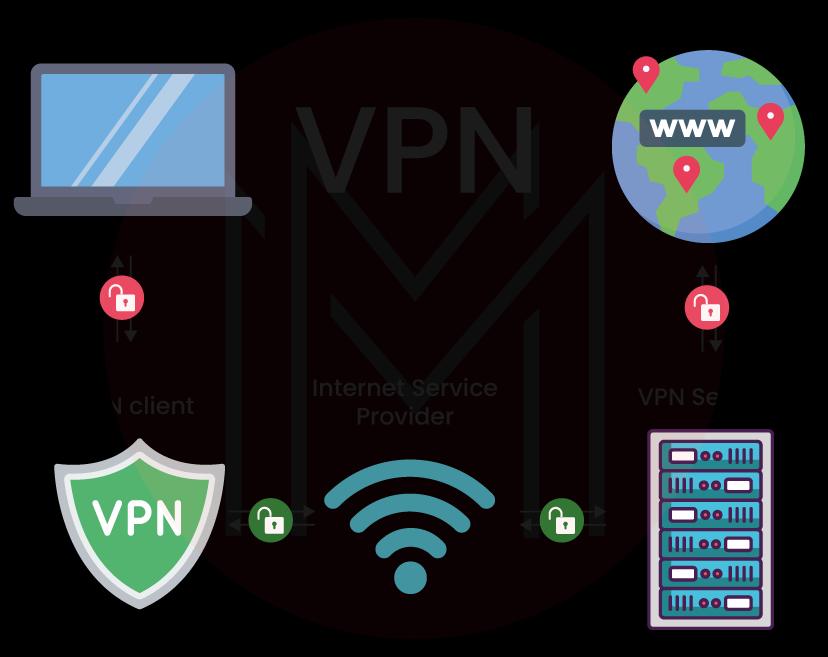
16. Describe VPN?
A VPN(Virtual Private Network) allows us to create a secure connection on a public network like the internet. Generally, VPN is utilized by mobile workers for accessing the enterprise’s network from remote locations. The below image tells you how a VPN looks:
17. What is the purpose of the Network layer?
The Network Layer handles switching, routing, and transmitting the data from one point to another; this layer is also accountable for packet sequencing and handling.
18. Explain Authentication?
Authentication is a mechanism for verifying the user’s credentials before he can log into the network. It is carried out using a username and password. This gives a secure way of limiting access from unwanted intruders on the web.
19. Explain the Subnet mask?
A subnet mask is the 32 bits address used to distinguish between the network and host addresses in the IP address. It identifies which part of the IP address is the network address and host address. They are not displayed in the data packets traversing the internet. They maintain the destination IP address, which the router will match with the subnet. We have two kinds of Subnet masks, they are:
- Default Subnet mask: It is the number of the bits which is reticent y address class. We can accommodate a single network subnet in a relative class through this default subnet mask.
- Custom Subnet Mask: The administrator can specify a Custom Subnet Mask for accommodating several networks.
20. Explain IDS?
An IDS(Intrusion Detection System) is a system that monitors the network traffic for suspicious activity and issues an alert when such action is found. It is the software application that scans the network or the system for policy breaching and harmful activities. Intrusion Detection System has two approaches: 1) Network Intrusion Detection System and 2) Host Intrusion Detection Systems.
21. Explain DNS?
Domain Name System is the Phonebook of the Internet. Humans access information online using domain names like espn.com and google.com. Web browsers communicate using internet protocol addresses. DNS converts domain names to IP addresses so browsers can load internet resources. Every device connected to the internet has a separate IP address that other machines use for finding the services.
22. Explain Bonjour?
Bonjour is Apple’s implementation of zero-configuration networking. It enables devices to run both Apple and Windows operating systems to share and connect the resources without configuration settings. Using the Bonjour, we can find other devices like printers and scanners on the local network and link with them. We can also share the files regardless of the operating system you utilize, whether it is macOS, Linus, or Windows.
| Related Article: "Important Linux Commands" |
23. What is IPX?
Internetwork Package Exchange(IPX) is the networking protocol that performs affairs and activities of the end-to-end process of managed and secured data. Initially, IPX was used by the Novell NetWare operating system, and later Windows adopted it. Since they displaced NetWare LANs, they are extensively used on the networks deploying the Microsoft Windows LANs.
24. Differentiate between a workgroup and a domain.
A workgroup is a group of systems with rules and local user logins linked to that specific system. A domain is a collection of systems with a centralized authentication server that tells them the rules. While the workgroups work efficiently in small numbers, once you send the relatively low threshold, it becomes more challenging to handle permissions and share efficiently.
25. How does Tracert work?
The Tracert diagnostic utility determines the route to the destination by transmitting Internet Control Message Protocol(ICMP) echo packets to the destination. In these packets, TRACERT utilizes varying IP Time-To-Live(TTL) values.
26. What is Two-Factor Authentication?
Two-Factor Authentication, also called dual-factor authentication or two-factor verification, is the security process in which users offer two different authentication factors to check themselves. 2FA is better implemented to protect users' credentials and the resources users can use.
27. Differentiate HTTP and HTTPS?
HTTP refers to the Hyper Text Transfer Protocol utilized by almost all websites for transmitting data, enabling us to use hyperlinks. The HTTP protocol utilizes TCP port 80, while HTTPS is the secure version of HTTP. HTTPS enables us to verify the identity and low-level encryption through TCP port 443.
28. What is the maximum length of UTP cable allowed?
The maximum length of UTP cable allowed is 90 to 100 meters for one segment collection.
29. Describe the loopback IP Address?
127.0.0.1 is the loopback IP Address. If you ping this IP address and finish successfully, it indicates that your hardware is fine. While troubleshooting the network connection issues, we use it for testing the Network Interface Card for functionality.
30. What is IPCONFIG?
IPCONFIG is a command used to determine the TCP/IP settings. DNS, Subnet Mask, Default Gateway, and DJCP configuration. It can also be used for changing the Local DHCP settings; for example, ipconfig/renew and /release…
Advanced Level Network Administrator Interview Questions
31. How does dynamic protocol configuration assist in network administration?
Rather than visiting every client computer to configure the static IP address, the network administration applies the dynamic host configuration protocol for creating the pool of the IP addresses known as the scope that we can dynamically allocate to the clients.
32. What are the main components of protocol?
The following are the main components of the protocol:
- Semantics: It explains the meaning of bits of every section.
- Syntax: It is the data format and order of the data displayed.
- Timing: What time will the data be transmitted, and how rapidly will it be shared?
33. Explain Sneakernet?
Sneakernet is the initial version of networking where the data is physically transported through removable media like tapes and disks.
| Related Article: "Linux Networking Commands with Examples" |
34. What is the use of IEEE in computer networking?
The Institute of Electrical and Electronics Engineers, or the IEEE, is an organization consisting of engineers who handle and issue the standards for electronic and electrical devices. It contains networking devices, cablings, networking interfaces, and connectors.
35. How can we resolve the signal attenuation problem?
To resolve that problem, we have to use the hubs and repeaters because it will allow you to regenerate the signal and thus prevent signal loss. Verifying whether the cables are correctly terminated is also a should.
36. What are the different technologies used in establishing WAN links?
Following technologies are used in establishing WAN links:
- Digital connections - through the digital-grade telephone lines
- Analog connections - using the traditional telephone lines
- Switched connections - using the multiple groups of links between sender and receiver for transmitting the data.
37. While troubleshooting computer network problems, what general hardware-related problems can happen?
A large amount of network contains hardware. Problems in these areas can vary from broken NICs, malfunctioning hard drives, and hardware startups. Invalid hardware configuration is also one of those problems we can look into.
38. How are IP addresses organized and displayed?
IP addresses are displayed in the form of a series of four decimal members that are separated by dots or periods. Another term for this organization is the decimal-dotted format. One example is 127.0.0.0
39. Differentiate CSMA/CA and CSMA/CD?
CSMA/CA, or Collision Avoidance, will first broadcast the intent to send before the data transmission.CSMA/CD, or Collision Detect, retransmits the data frames whenever a collision happens.
40. What is the best location for installing the Anti-virus?
An Anti-virus should be installed on all the workstations and servers to ensure security. That’s why individual users can use any workstation. You can utilize their removable flash drives or hard drives.
41. When we move NIC cards from one PC to another, does the MAC address get transferred as well?
Yes, because MAC addresses are hard-wired into NIC circuitry, not PC. It also indicates that the PC can have a different MAC address when another one displaces the NIC card.
42. What is Clustering support?
Clustering support is the capability of the network operating system for connecting multiple servers in the fault-tolerant group. The primary use of this is if one server breaks down, all the processing continues with the subsequent server in the cluster.
43. Can two PCs be connected for file sharing without using a router or hub?
Yes, you can connect two PCs using a single cable. A crossover cable can be utilized in this situation. In this setup, the data transmitter will pin one cable linked to the data receive pin of another cable, and conversely.
44. Differentiate straight-through and crossover cables?
A straight-through cable connects the computers to the router, hub, or switch. A crossover table connects two similar devices, like PC to PC or Hub to Hub.
45. What are the maximum networks and hosts in Class A, B, and C networks?
Class A has 126 possible networks and 16,777 214 hosts. For Class B, there are 16,384 possible networks and 65,534 hosts. For Class C, there are 2,097,152 possible networks and 254 hosts.
Frequently Asked Network Administrator Interview Questions
1. How do I prepare for the Network Administrator Interview?
Before going to an interview, study different protocols and terms about network administration, which will help you display to the interviewer that you have the knowledge required for that position. For an efficient answer, you can tell your real-time experience in which you carried out these tasks successfully.
2. What is the main role of a network administrator?
The Network Administrator's role is to ensure the steady operation of computer networks. It contains developing, planning, configuring, installing, optimizing, and supporting all the network software, hardware, and communication connections.
3. What every network administrator should know?
Every Network Administrator should know the following things:
- Updating and Maintaining the existing networks
- Setting up the new networks
- Configuring and Updating the virus protection
- Troubleshooting the flaws in software, communications equipment, and hardware configuration.
- Communicating problems and updates to other employees
- Monitoring and Maximizing performance
4. What are the 3 Ps of Networking?
The 3 Ps of Networking is Purpose, People, and Process.
5. What skills do you need for Network Administrator?
Following are some of the essential skills required for a Network Administrator:
- Critical-thinking
- Problem-solving
- Analytical skills
- Communication
- Knowledge of Networks and Servers
- Maintaining and Repairing the Networks and Servers
- Familiarity with the Networking and Diagnostic software
- Experience with multiple kinds of networks
6. Is coding required for a network administrator?
To work as a network administrator, you must have a solid understanding of popular programming languages like PHP, HTML, C++, Javascript, Python, Ruby, and Java.
7. Is networking a hard career?
No, networking is not a hard career. Organizations across different industries need computer networking professionals to build, secure and troubleshoot their computer systems. Although computer networking is challenging, you only need good training and real-time experience.
8. What are the three essential skills of an administrator?
Successful Administration relies on three skills: 1) Human, 2) Conceptual, and 3) Technical.
Network Administrator Interview Preparation Tips
1. Revise the Basics
Along with the frequently asked questions, a network administration interview will also include networking basics like networking protocols, topologies, networking devices, etc.
2. Don’t bid on mistakes
Be comfortable while giving answers. If you make a blunder, don’t allow it to affect the remaining interview. You will be able to answer the remaining questions, and the interviewer will forgive a single mistake. When something goes wrong, move on and concentrate on the rest of the interview.
3. Utilize the interview to display your passion for technology
Demonstrating your passion for networking and experience working with protocols and topologies, you can tell why you are the right candidate for that position.
4. Be ready for a lengthy interview
The technical interview process may take a number of weeks and include multiple rounds. After the preliminary round, you may meet with managers and HRs in the coming weeks or days. So, you should be ready for a lengthy interview.
5. Don’t Forget to prepare for Behavioural/Conventional Questions
Employers say that students are concerned about the technical interview and have not thought through answers to general questions like “why are you interested in this job” or “Tell me about yourself.” So, prepare to answer the general interview questions along with the technical concepts.
Conclusion
The networking field offers you different roles like Network Engineer, System Engineer, Network Architect, Support Engineer, and Network Administrator. Among all the job roles, businesses of all scales need skilled network administrators to keep their systems working smoothly. So, job security is guaranteed for those who want to become network administrators.
But, proper interview preparation and cracking job interview is the key to achieving the job. For that reason, we have brought these 45 most frequently asked Network Administrator interview questions that include all the core concepts of network administration and will help you assess your knowledge. I hope these top Network Security interview questions and answers for 2023 are sufficient to ace the job interviews; if you have any queries, let us know by commenting in the below section.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Linux Networking Training | Mar 03 to Mar 18 | View Details |
| Linux Networking Training | Mar 07 to Mar 22 | View Details |
| Linux Networking Training | Mar 10 to Mar 25 | View Details |
| Linux Networking Training | Mar 14 to Mar 29 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .










