- Home
- Blog
- Business Analyst
- Deloitte Interview Questions

- Business Analysis Framework
- Business Analyst Interview Questions
- Business Analyst Tutorial
- ELK Stack Tutorial
- Kibana Tutorial
- Top 10 Business Analytics Tools For Business
- What Is Business Analytics?
- Product Analyst Interview Questions
- MS Excel Interview Questions
- Goldman Sachs Interview Questions
- Uber Interview Questions
- Accenture Interview Questions
- EY Interview Questions
- Mphasis Interview Questions
- Business Analyst Projects and Use Cases
Common Deloitte Interview Questions
Deloitte Technical Interview Questions
Deloitte Python Interview Questions
Deloitte SQL Interview Questions
Deloitte Java Interview Questions
Deloitte Data Science Interview Questions
Deloitte Analyst Interview Questions
Deloitte Consultant Interview Questions
Deloitte, one of the "big four" accounting companies, provides professional services to customers worldwide. It is a multinational professional services company headquartered in the UK that provides consulting, financial advising, audit, risk advisory, legal, and tax services.
Around 4% of the almost 500,000 applicants to Deloitte, every year are hired. Competition is exceptionally high for applicants, and thorough preparation is critical to get through the interviews. To help you nail your Deloitte interview, MindMajix's team has done enough research and compiled the requisite information in this blog. It includes the top 40 Deloitte interview questions and answers 2024 with the most researched answers.
This Blog covers the following:
- Deloitte Interview Process
- Common Deloitte Interview Questions
- Deloitte Technical Interview Questions
- Tips to Crack Deloitte Interview
- FAQs
- Conclusion
Top 10 Frequently Asked Deloitte Interview Questions
- Name the various built-in data types of Python.
- How can you delete rows and columns from a data frame?
- Is SQL a programming language?
- Distinguish MySQL and SQL.
- Briefly describe garbage collection in Java.
- Mention the different ways to create threads in Java.
- What do you understand by embedding?
- How to overcome imbalanced datasets?
- What exactly is LOD in Tableau?
- What do you mean by the cycle of R2R?
Deloitte Interview Process
Getting a job at Deloitte takes extreme skill. Knowing what to expect and thoroughly preparing helps you to have a successful interview experience with one of the most prestigious organizations.
Here is an outline of what to expect at the Deloitte interview, from applying to getting hired.
-
Application Submission
The most important aspect of the interview process is sending a polished and edited job application. This increases your chance of getting an interview call. Submit a detailed and well-constructed job application through employee referrals or the official organization's careers page.
-
First Round
If your resume impresses the hiring manager, you'll receive an email or call from them within one to three months. Depending on the role and location of employment, interviews may be held in person or over video conference.
The initial round usually consists of fundamental questions related to a resume and behavioral kind conducted by human resource professionals, regardless of the role.
-
Second Round
Deloitte is recognized for conducting in-depth interviews for job seekers. If you ace the first round, you'll be called for a second round of the interview, which usually lasts 30 minutes.
It includes behavioral and situational questions, usually conducted by a senior manager.
-
Third Round
Lastly, suppose you're looking for a senior or highly technical role in the company. In that case, you'll certainly be forced to go through another round with a senior professional, a panel of interviewers, or a departmental director after the second round.
Usually third round includes advanced situational and job-specific questions. Putting your best foot forward here is essential since every word is scrutinized and evaluated.
-
Pre-employment Aptitude Test
You may be further requested to take an aptitude level test to analyze further your skill based on the role you are applying for, skill level, and professional knowledge.
Quantitative, verbal, and logical reasoning is included in the Deloitte pre-employment aptitude test to check your skill level.
-
Orientation and Training
Once you clear all the rounds and receive the formal offer letter, only orientation and training remain in the onboarding process.
Every Deloitte employee, regardless of role, must attend employee orientation to understand corporate policies and procedures thoroughly.
| If you want to enrich your career and become a professional then enroll in "Business Analyst Training". This course will help you to achieve excellence in this domain. |
Common Interview Questions
Below are some of the common questions that HR and senior managers pose for all candidates to assess whether they fit into the work culture. Let us discuss these common interview questions and answers.
1. Tell me about yourself.
This is a fundamental question asked by any interviewer. Don't let this stump you during an interview. Give a brief introduction about your strengths and past experiences. Try highlighting your skills, knowledge, and personality during the interview process.
2. Why did you choose Deloitte?
Hiring managers across the organization ask this question to know your interest and learn more about the organization you're applying for.
Prepare for this question by researching Deloitte before attending the interview and familiarize yourself with its culture, mission, and professional principles. Try highlighting your experience and at least one factor that pulls you to the company in your response to the interviewer.
3. Are you willing to relocate to various parts of India?
Since the company is spread globally, you might need to relocate based on the project or role you're applying for. Do consider this fact before you answer the question.
4. What are your expectations from this role?
Talk about how this role will help you with new challenges and chances to improve your skills. Also, speak about how you can upgrade your skillset through this role.
5. What can you bring to Deloitte?
This is the most asked interview question to job seekers by the Deloitte recruiting team to analyze your skills and competencies further. This is the best opportunity to showcase your finest skills. Try to answer by highlighting your relevant expertise and emphasizing your professional qualities.
6. What made you find a new job?
Focus on your response. This is a behavioral question to test whether you are a correct fit. The interviewer would like to assess whether you criticize former or current employees. Through that, the hiring manager assesses whether you are a good fit for the organization.
7. How did you get into the accounting field?
If you are interviewing with Deloitte, this is the most probable question you face. Try to recall the specific interests that drew you to the accounting field and highlight your devotion to the job in your response.
8. How do you stay focused while performing audits and other tax services?
Working with numbers might become tedious, but staying focused is crucial if you work with Deloitte. Recruiting managers often ask this question to assess your ability to complete the task on time and stay focused. In your response, express your capacity and pay close attention to detail while providing audits and legal services.
9. How do you handle multiple deadlines and tasks?
Working quickly and meeting deadlines are essential to employee success at Deloitte. Hiring managers mostly prefer passionate and focused employees. In your response, highlight your time management and organizational skills.
10. What do you know about Deloitte?
Regardless of the position you apply for, this is the common question you certainly face throughout the interview. Prepare your response by researching and having a few essential facts about Deloitte.
Deloitte Technical Interview Questions
Deloitte Python Interview Questions
1. What is exactly a Python language?
Python is one of the general-purpose and high-level programming languages. It is a dynamically typed language that provides simple syntax. It is easy to learn and offers good readability to codes. Also, it is an object-oriented and interpreted language.
Moreover, Python is a language that comes with built-in data structures and dynamic binding. That's why it supports developers in building robust applications quickly.
| Related Article: Python Tutorial |
2. Why is Python known as an interpreted language?
Generally, Python codes are interpreted first and then executed by the interpreter at the runtime directly. The interpreter executes the source codes line by line. This is the reason why Python is known as the interpreted language.
3. Name the various built-in data types of Python.
The below graphic shows the various built-in data types of Python.
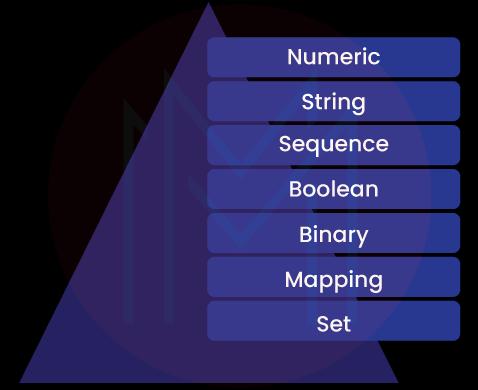
4. What is the role of the _init_ method in Python?
We use the _init_ method to create objects. In a way, the _init_ method is similar to constructors in C++. This method initializes the attributes of an object. And it is only used within classes. Besides this, the _init_ method has no specific role.
5. What do you understand by unit tests in Python?
Unit tests are codes written to test other codes in Python. A unit can be a function or method.
Python uses two frameworks to perform unit tests: PyTest and unit test.
6. How do you create a class in Python?
We create a class in Python by using the class keyword. Below is an example of a class in Python.
class MyClass:
x=57. How is a new modifier different from an override modifier?
The new modifier directs the compiler to use the new implementation. On the other side, an override modifier overrides a base function. Note that it occurs inside a child class.
8. How will you identify a missing value in a Pandas data frame?
We can use the isna ( ) function to check whether any value is missing in a pandas data frame. This function returns a Boolean value if any value is missing in a Pandas column.
9. How can you delete rows and columns from a data frame?
We shall use the .drop ( ) method to delete records from a data frame. In this regard, the column or index names are used to remove the rows and columns.
10. Create a Python code to find the shape of a NumPy array.
Code:
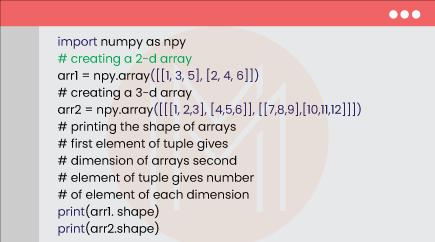
Result:

Deloitte SQL Interview Questions
11. Define subquery and name its types.
A subquery is nothing but a query nested inside a query or statement. The statements can be SELECT, UPDATE, INSERT, DELETE, etc. No wonder the subquery can be nested inside another subquery.
Further, Subqueries can be present inside the WHERE, HAVING, and FROM clauses. Another essential thing is that we can directly perform operations on specific rows with subqueries.
Here is a list of different subqueries used in SQL.
- Single row subquery
- Multiple column subquery
- Correlated subquery
- Multiple row subquery
- Nested subquery
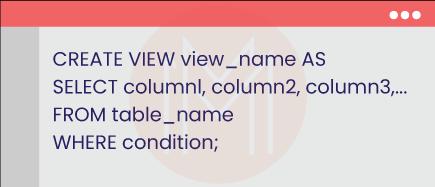
12. What do you mean by view in SQL?
A view is a virtual table that we can create based on the results of a SQL statement. Like tables, a view consists of multiple rows and columns. The rows and columns of a view are essentially the rows and columns of one or more tables stored in a database.
We can create a view using the CREATE VIEW statement. Below is an example of the same.
13. What is precisely an implicit cursor?
An implicit cursor is usually generated when we perform operations such as DELETE, INSERT, and UPDATE in databases. Besides, this cursor is used for internal processing.
14. What is the use of collation in SQL server?
Collations are nothing but a set of rules that we use to access, store, and compare data. They direct the database engine on handling the character data efficiently. Know that we can find collations on servers as well as databases.
Following is the list of collations supported in the SQL server.

15. What is the role of the recursive stored procedure?
It is a recursive stored procedure that repeatedly calls itself until it reaches a particular condition. So we can avoid writing the same codes multiple times on a program.
16. Is SQL a programming language?
SQL is not a general-purpose language (GPL) but a domain-specific language. It means we can use SQL to query and manage databases. As it is a domain-specific language, we can use SQL to solve only specific problems.
We must note that we cannot use SQL to build applications.
17. Compare a unique key with a primary key.
| Unique key | Primary key |
| Unique key acts as a unique identifier in the absence of primary key. | It acts as a unique identifier for all rows in a table. |
| By default, it generates a non-clustered index. | By default, it generates a clustered index. |
| There can be one or more unique keys for a table. | There can be a single primary key for every table. |
| We can alter the values of a unique key. | We cannot change the values of a primary key. |
| It doesn’t support auto-incrementing values. | It supports auto-incrementing values. |
| It accepts NULL values. | It doesn’t take NULL values. |
18. Distinguish MySQL and SQL.
| MySQL | SQL |
| It is a software that uses SQL. | It is a query language. |
| It is open-source software. | It is not an open-source tool. |
| It works on all platforms perfectly. | It works well with Windows. But it doesn’t work perfectly with Linux and macOS. |
| It supports different storage engines. | It helps only a single storage engine for making multiple operations. |
| It doesn't support XML and user-defined functions. | It supports them. |
19. How is BETWEEN operator different from IN operator in SQL?
When it comes to the BETWEEN operator, it returns all the data that lies between two values. The value can be a text, number, etc.
The syntax for the BETWEEN operator is given as follows
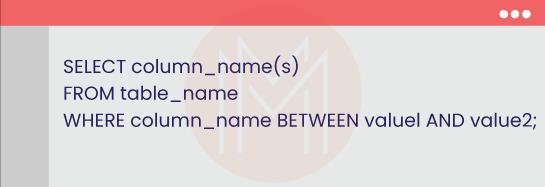
When it comes to the IN operator, it returns only the specified data. In other words, it retrieves a set of records that match the given values.
The IN operator's syntax is given as follows
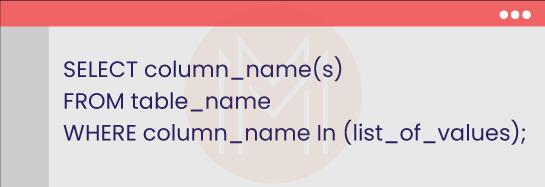
20. Why do we use the DISTINCT keyword in SQL?
We use the DISTINCT statement to remove duplicate values from the result set of a SQL statement. Simply put, it returns only distinct values of the result set.
Generally, the DISTINCT keyword is used along with the SELECT keyword. It can also be used with aggregate statements such as COUNT, MAX, AVG, etc.
The main thing about this keyword is that it acts on a single column only.
| Related Article: SQL Interview Questions |
Deloitte Java interview questions
21. Briefly describe garbage collection in Java.
It is the automatic memory management system used in Java. Generally, Java programs create objects on the heap while running on the JVM. The objects will be used by programs as and when required. However, some of the objects will remain unused. Garbage collectors delete unused objects and free up memory space.
22. What do you mean by Java Daemon Thread?
It is a low-priority thread that does many background operations, such as action listeners, garbage collection, etc.
In a way, a daemon thread is a ‘service provide thread’ that supports user threads extensively. The main thing is that the lifespan of this thread depends on the user threads. Once all the user threads are executed, the JVM terminates the daemon thread immediately.
23. What are the default values assigned to instance variables in Java?
The default value is zero for numbers. It is false for Boolean. Further, it is NULL for object references.
It is essential to note that the default values are assigned within a constructor.
24. Mention the different ways to create threads in Java.
We can create threads in Java in the following ways.
- We can create threads by using a runnable interface. Also, we can create them overriding the run ( ) method. After that, we need to generate thread objects.
- We can create threads by extending the thread class. This is because the thread class provides methods and constructors with which we can operate on threads.
25. What is a composition in Java, and list its uses?
It is a design technique used in Java to implement the ‘has-a’ relationship in classes. It is achieved with the help of instance variables. And these variables typically refer to objects.
In composition, one object is contained in another object. Mainly, one object cannot exist without the other.
Following are the uses of composition.
- It supports multiple inheritances.
- It encourages the reuse of codes.
- We can change member objects at run time.
26. Why doesn't Java use pointers?
Jotted down are the reasons why Java doesn’t use pointers.
- Pointers consume more memory
- Memory is directly accessed if we use pointers. It will raise security issues.
27. Differentiate the .equals ( ) method and the ‘==’ operator in Java.
| equals( ) | == operator |
| It is essentially a method. | It is an operator. |
| It is used to compare the actual contents of objects. | It is used to compare reference objects. |
| We cannot use this method with primitives. | It is possible to use this operator with primitives. |
| We can override this method. | We cannot override this operator. |
| We can compare conflicting objects with the support of this operator. | We cannot compare conflicting objects |
28. State the differences between throw and throws in Java.
| Throw | Throws |
| It is a keyword that we use to throw an exception inside a function. | It is a keyword used to declare an exception in the function signature. |
| It is followed by an instance of an exception. | It is followed by class names of exceptions. |
| It is used within a method. | It is used with a method signature. |
| Only one exception is thrown. | Multiple exceptions can be thrown. |
| It cannot propagate checked exceptions. | It can propagate checked exceptions. |
29. Is it possible to make the main thread a daemon thread?
Yes. It is possible. A thread created in the main method is a daemon thread by default.
30. Write a Java program to represent numbers as strings.
Code:

Result:

Deloitte Data Scientist Interview Questions
31. What is precisely machine learning?
Machine Learning (ML) is essentially a subset of Artificial Intelligence (AI). We use advanced ML algorithms to make predictions and uncover insights from data. Thus, ML supports businesses in making informed decisions.
ML uses historical data to make predictions and recommendations. We use ML for fraud detection, predictive maintenance, malware threat detection, and many more.
Know that there are three types of ML algorithms: supervised ML, semi-supervised, and unsupervised ML.
32. Outline a few commonly used ML algorithms.
Following are the different commonly used ML algorithms.
- Linear Regression – a relationship between independent as well as dependent variables is established in this algorithm.
- Gradient boosting algorithms - We use this algorithm to analyze large data and make predictions.
- K-means algorithm - This unsupervised learning algorithm classifies datasets into several clusters.
- Decision Tree – This is a supervised learning algorithm with which we can classify problems.
- Dimensionality reduction algorithms – This algorithm helps to find relevant details.
33. What do you mean by linear search algorithm?
It is one of the easiest methods data scientists use to search for an element in a dataset. This algorithm searches all data elements from the first to the last element until it finds the correct match.
We can apply linear search only when the dataset contains fewer unordered elements.
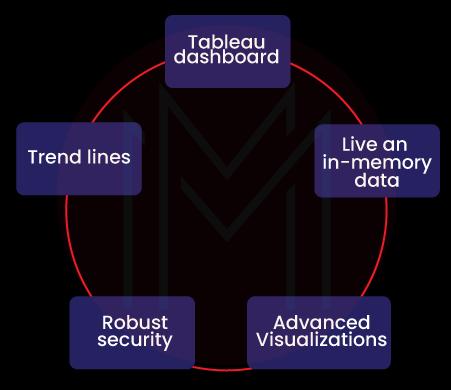
34. What is Tableau, and brief its vital features?
Tableau is a powerful Business Intelligence (BI) or data visualization tool.
Below are the vital features of Tableau.
35. What do you understand by embedding?
It is a process of converting high-dimensional data into low-dimensional one. It allows for analyzing a large set of inputs like sparse vectors.
It is essential to note that embedding improves the efficiency as well as usability of ML models. It simplifies data so that it can be the best fit for training and making predictions.
36. Differentiate Random Forest with Extra Trees classifier.
| Random forest classifier | Extra trees classifier |
| It is faster. | It is slower compared with random forest. |
| It is best when a dataset is smaller. | It is best when a dataset is large. |
| The decision rule is selected randomly. | It is not randomly chosen |
37. How to overcome imbalanced datasets?
We can overcome imbalanced datasets using the following ways:
- Resampling with various ratios
- Choosing the proper evaluation metric
- Clustering the abundant classes
- Using the K-fold cross-validation
- Performing oversampling as well as undersampling
38. Write a Python code to find the squares of numbers using the pow( ) function.
Code:

Result
6439. Define Markov Chains.
Markov chain is a stochastic process. The main thing about this process is that it is memory-less. It means that the future state doesn't depend on the past states.
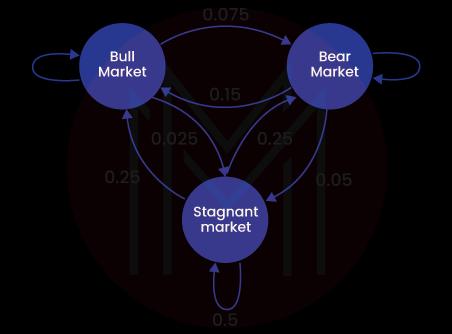
It is widely used in speech recognition, search engine algorithms, etc.
40. Why is the language R commonly used in data visualization?
Here are the reasons why we use R in data visualization.
- It offers data visuals in the form of charts and 3D models
- It has a wide array of visualization libraries.
- Customization is a cakewalk in R. We can easily change axes, labels, legends, etc.
Deloitte Analyst Interview Questions
41. What is precise Data Analysis?
Data analysis is the process of cleaning, modifying, and processing the original data. As a result, we can dig out actionable and valuable data that we can use to make informed decisions. The processed data is presented as images, graphs, tables, etc.
By doing data analysis, we can reduce operational costs, solve problems, satisfy customers, and enhance business outcomes.
42. State the different methods of data cleaning.
Jotted down are a few methods used in data cleaning.
- Ignoring the tuples in records
- Binning
- Filling in the missing values
- Clustering
- Regression
43. What do you mean by type I & II errors in Statistics?
- A type-I error occurs when we reject a NULL hypothesis that is actually true and accurate. Also, it is a 'false positive' error made by wrongly rejecting a null hypothesis.
- A type-II error occurs when we fail to reject a NULL hypothesis that is indeed false. It is also known as an error of omission. Besides, it is a 'false negative' error made by not rejecting an incorrect null hypothesis.
44. What exactly is LOD in Tableau?
LOD stands for Level of Detailed expressions. It helps select the granularity level to make computations. Also, it helps to operate on data at the source level.
As mentioned below, there are three granularity levels
- EXCLUDE (Less granular level) - It subtracts dimensions from the view level.
- INCLUDE (more granular level) - It computes data using specified dimensions.
- FIXED (entirely independent level) - It computes data without referring to any other dimension.
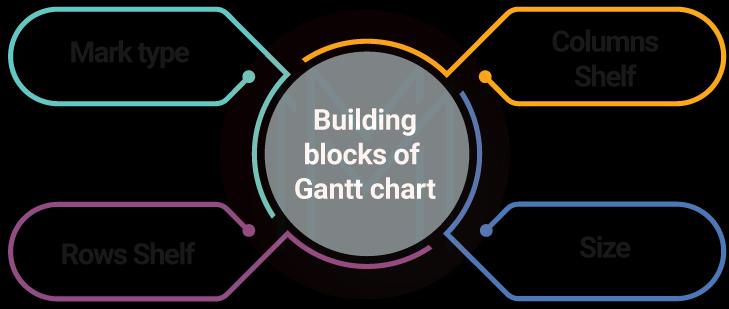
45. What is the use of the Gantt chart in Tableau?
With Gantt charts, we can know the duration of events. The building blocks of the Gantt chart are shown below.
46. Why do you use time-series data analysis?
Time series analysis helps to infer the underlying causes of trends. Also, it helps to know the systematic patterns in data over time. In simple words, we can forecast the future using time-series data analysis.
It is a simple but essential note that time-series analysis is performed for non-stationary data.
47. State the differences between prescriptive analysis and predictive analysis.
| Prescriptive analysis | Predictive analysis |
| We can analyze the whole business data with this analysis. | We can analyze the data of a specific section of a business with this analysis. |
| It goes beyond predictions and provides actionable insights and recommendations. | It gives forecasts about trends. |
48. Compare Univariate, Bivariate, and Multivariate data analysis.
| Univariate Analysis | Bivariate Analysis | Multivariate Analysis |
| It summarizes a single variable at a time. | It summarizes two variables at a time. | It summarizes more than two variables. |
| This analysis aims to describe things. | This analysis seeks to explain things. | This analysis seeks to infer the relationship among the variables. |
| Histograms, Bar charts, and pie charts are a few examples of univariate analysis. | Chi-square test, Scatter plot, Z-test, and t-test are a few examples of this type. | Principal component analysis, Cluster analysis, and correspondence analysis are a few examples of multivariate analysis. |
49. How to treat outliers in datasets?
We can treat outliers in datasets in the following ways
- Setting up a filter in testing tools
- Changing the value of outliers
- Removing outliers during post-test analysis
- Considering the importance of mild outliers.
- Considering the underlying distribution
50. Distinguish blending and joining in Tableau.
| Blending | Joining |
| Blending is done when a dataset is taken from multiple sources. | Joining can be done when a dataset is taken from the same source |
| It aggregates data first and then combines it. | It combines data first and then aggregates it. |
| We can use only the left join. | We can apply many join methods, such as left, inner, right, etc. |
| Data can have different levels of granularity. | All the data must be at the same level of granularity. |
Deloitte Consultant Interview Questions
51. What is the difference between cash flow and profit and loss statements?
A Profit and loss statement calculates the profitability of a business. On the other side, a cash flow statement indicates the sources of money, where it goes, and the cash in hand at a single point in time.
It is essential to closely monitor the above statements since they greatly influence a business's financial health.
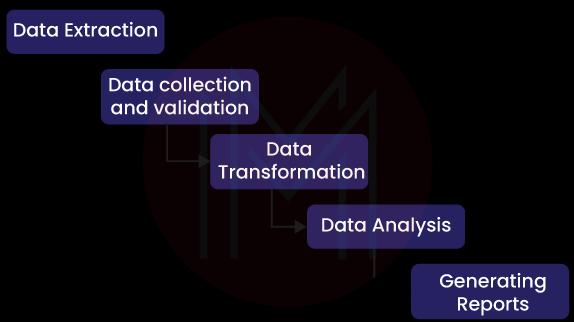
52. What do you mean by the cycle of R2R?
R2R stands for Record to Report cycle. The finance and accounting management process includes garnering, processing, and providing accurate information. Thus, we will perform informed decisions to stabilize the financial condition or level up the financial health of a business.
The R2R cycle includes the following processes:
53. How can you increase the profitability of a business?
We need to leverage the below strategies to increase the profit of a business.
- Focusing on the profit margins accurately
- Assessing the effectiveness of cost management methods
- Reviewing the bottom-line performance
- Reducing the error rates as low as possible.
- Monitoring the business productivity closely.
54. What are the things you should consider before making mergers and acquisitions?
Below are the things we must consider for making mergers and acquisitions.
- The core values, culture, and management style should correctly fit. Otherwise, it will create issues later.
- The communications must be clear and transparent.
- We must thoroughly consider customer loyalty, brand value, and market share.
55. What are the essential things you should consider before entering a new market?
Listed below are the critical things we need to consider before entering a new market.
- Tracking the behaviors of new target customers
- Understanding the cultural differences in different markets
- Identifying the effective communication channels
- Learning the regional regulations
- Knowing the payment methods
56. What will be the common problems that may arise between a client and employer?
Following are the common problems that usually occur between a client and an employer.
- Differences in product expectations
- Non-stop communication and inquiries
- Unexpected and changing client demands
- Poor response from clients on serious matters.
- Frequent revisions on the progress
57. How will you keep track of the progress of a project?
We can keep track of the progress of a project in the following ways effortlessly.
- Finalizing deliverables and key mileposts accurately
- Meeting teams as well as stakeholders regularly
- Employing a project tracking software so that we can keep track of time, costs, and activities
- Encouraging transparency at all levels of the project.
58. How can you size a market efficiently?
We can follow the below three steps to size a market efficiently.
- Defining the target market perfectly
- Calculating the potential sales in advance
- Conducting detailed market research
59. How will you research a company?
We will consider the following points while researching a company.
- Going through the website of the company from the landing page to all pages
- Knowing the history of the company through Google News
- Tracking their business activities on LinkedIn and other social media platforms
- Reading the publications, blogs, newsletters, and press releases thoroughly.
60. What methods will you use to bring consensus to a team?
We can follow the below tips to bring consensus in a team.
- Conducting brainstorming sessions to explore endless ideas regarding the subject of discussion
- Performing nominal group technique, which is one of the structured approaches.
- Working multi-voting to reduce the number of solutions to a problem to few.
Tips to Crack Deloitte Interview
Tips #1: Consider the tools and skills necessary for the position. Check out the job description carefully for the core knowledge you must have. This may include working with data structures, business intelligence tools, or programming in a particular language. A firm understanding of the fundamentals will help you respond more effectively to any vital interview question.
Tips #2: The more you prepare for the interview will boost your chances of success. Learn everything there is to know about an interview's rounds, stages, and questions.
Tips #3: Prepare answers in advance to typical management and HR interview questions. Also, review the company's accomplishments, organizational structure, vision, work-life balance, and more.
Tips #4: Check your resume thoroughly to ensure you have included all the necessary information about yourself and that it is correct to the best of your knowledge.
Tips #5: Employers prefer to hire applicants who come with questions. Before the interview, spend some time reviewing the job description. Make a note of any questions you have. Applicants need to save their questions for the end of the interview process.
Deloitte FAQs
1. How do you prepare for a Deloitte interview?
Deloitte interviews are more challenging than regular interviews at larger corporates. Their interview format is specific, and the questions are complex. But with good preparation, you can succeed at the Deloitte interview. So train thoroughly for the job role you apply for with quiz questions, practice tests, mock interviews, and more.
2. Are Deloitte interviews tough?
Deloitte interviews are tough. Only the industry's best and most confident professionals are able to crack the interview. Understand the role thoroughly, including what they expect from you and the skillset you need. The more you prepare for the job interview, the more likely you will succeed.
3. What is the best answer for why Deloitte?
Deloitte allows you to learn and develop through working with the best and exploring the best paths for you.
4. How many rounds of interviews are in Deloitte?
Generally, three rounds of interviews to the basic recruitment process of Deloitte, such as online Assessment, Group Discussion, and Face-to-Face Interviews.
5. What is the lowest salary at Deloitte?
The starting salary for freshers at Deloitte is roughly 4.5 lakh per annum.
6. Is getting placed in Deloitte easy?
As long as you possess the skillset that they are looking for, you have more chances of getting placed in Deloitte.
7. Why should we hire you?
The interviewer, through this question, is trying to assess if you are a good fit or not for the organization. Therefore, you need to persuade them. Discuss your skills, past experiences, and how you can bring freshness to this role.
8. What are your strengths and weaknesses?
When hiring managers ask this question, they want to evaluate some things, like how you conduct a self-assessment yourself. Whether you know your positive traits, how you bring them into the workplace, and how you've worked on your weaknesses to improve them.
9. What are your salary expectations?
This is a challenging one. You can skirt this question with a broad answer like 'my salary expectations align with the professional experience and qualifications.'
10. Where do you see yourself in 5 years?
This question mainly assesses whether you plan to remain with the company long-term. In your response, you must include the company in your plans.
Conclusion
Now that you understand Deloitte interview questions well, it's time to put them into practice and build a successful career in this inclusive and rewarding field. If you want to improve your skill set, sign up with Business Analyst Training, where industry professionals design courses as per the latest business need to make you job-ready.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Business Analyst Training | Feb 21 to Mar 08 | View Details |
| Business Analyst Training | Feb 24 to Mar 11 | View Details |
| Business Analyst Training | Feb 28 to Mar 15 | View Details |
| Business Analyst Training | Mar 03 to Mar 18 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .


