- Top 10 DevOps Tools for Continuous Integration
- Top 10 Devops Tools
- Repository Management Tools
- 10 Tools For Effective DevOps Collaboration
- Top 12 Open Source DevOps Build Tools
- Configuration Management Tools in DevOps
- Agile Vs DevOps
- Chef DevOps Interview Questions
- What is Continuous Integration in DevOps?
- Insights of DevOps Architect
- DevOps Automation: How is it Carried Out?
- Introduction To DevOps Docker
- DevOps For Dummies
- DevOps Interview Questions
- 13 DevOps Testing Tools For DevOps Professionals
- Best DevOps Tools and Frameworks to explore
- DevOps Tutorial For Beginners: A Step-by-Step Guide To Learn DevOps
- Cacti Graphing And Monitoring
- RANCID Tool Keeps Config Files Clean
- How To Enable LLDP on Linux Servers for Link Discovery
- How to set up a modern web stack in Ubuntu
- Useful Iperf Commands for Network Troubleshooting
- Migration of MongoDB to DynamoDB
- MongoDB and Tree Structures
- Multihost SSH Wrapper
- DevOps Tools for Infrastructure Automation
- Introduction To Azure DevOps
- Introduction To DevOps Tools
- List of DevOps Monitoring Tools
- The Ultimate List of DevOps Deployment Tools
- Top 10 Open Source Containerization DevOps Tools
- Reasons for the Rise of DevOps
- Role Of a DevOps Engineer
- DevOps Security Tools
- Some Common Myths about DevOps
- Top 10 Devops tools in cloud
- Release Management Tools
- Top 10 SCM Tools
- Logging DevOps Tools
- DevOps And Its Significance
- Ansible vs Chef
- DevSecOps Tutorial
- What is Site Reliability Engineering - SRE Tools
- Site Reliability Engineer(SRE) Interview Questions
- What is DataOps?
- DevOps Vs SysOps
- DevOps Engineer Job Description
- Azure DevOps Jira Integration
- What is Pipeline in DevOps?
- SonarQube Azure DevOps
- Azure DevOps CI/CD
When it comes to security, it must be a team effort from the beginning to the end. Security threats can never go unnoticed without integrating security into the entire application system. One of the essential elements of DevSecOps is that it creates shorter and more frequent development cycles. This, in turn, greatly decreases disruptions and fosters close collaboration between the kind of teams that would be isolated from each other in ordinary circumstances. DevSecOps, with its shorter development cycles strategy, strengthens the team and also increases efficiency.
Enterprises must ensure that their workforce can keep up as they attempt to integrate security into every step of a DevOps workflow, a concept known as DevSecOps. To get an idea of what to expect, we have provided 40 DevSecOps interview questions below. Take a look!
Highlights for DevSecOps
- DevSecOps stands for development, security, and operations. It provides an approach to integrate security including the platform design in the IT lifecycle.
- The entire security can be automated using DevSecOps workflow. It provides a development environment similar to IDE to meet the essential requirement of security.
- DevSecOps deal with the entire built-in security. Thus, it doesn't have any influence on the perimeter security path of any app and data that function on the outside. The inbuilt security benefits of DevSecOps open up future scope for the long-term adaptation for IT industry that need strict security requirements.
- It addresses every security issue emerging in the mid-way of operation and gives signals to take action from the beginning to lower the heavy economical burden in future.
We have categorized DevSecOps Interview Questions into 3 levels they are:
Frequently Asked DevSecOps Interview Questions
- How does configuration management fit into DevOps?
- How does DevOps increase system security?
- Differentiate between continuous delivery and continuous deployment.
- Tell us about the Blue/Green Deployment Pattern.
- What is Automation Testing?
- What are the perks of continuous testing for DevOps?
- Tell us about DAST in DevOps.
- What may some of the duties of a DevOps/DevSecOps architect entail?
- Please define an illustrative DevOps maturity model.
- What are the DevOps anti-patterns?
| If you want to enrich your career and become a professional in DevSecOps, then enroll in "DevSecOps Training". This course will help you to achieve excellence in this domain. |
DevSecOps Interview Questions For Freshers
1. Elaborate on DevSecOps security?
The acronym for development, security, and operations is DevSecOps. Making everyone responsible for security is its guiding principle, with the aim of implementing security choices and actions at a similar pace and scale as those of development and operations.
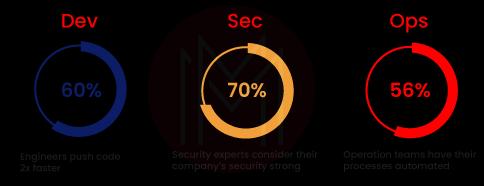
2. How does configuration management fit into DevOps?
- Allows for the management of numerous systems and changes to them.
- Standardized resource configurations manage IT infrastructure as a result.
- In addition to preserving the integrity of the overall infrastructure, it aids in the management and administration of several servers.
3. How do you get started with the DevOps initiatives?
To begin with DevOps or DevSecOps projects in your organization, there are a number of stages that must be taken, including assessment, gap analysis, maturity modeling, project implementation roadmap, etc. Choosing the correct team is important when beginning a DevOps or DevSecOps project.
This team should be familiar with DevOps tools and procedures as well as have knowledge of both operations and development. You might need to hire outside consultants if your internal staff is lacking in all the necessary expertise. Understanding your present infrastructure is a crucial part of starting with DevOps or DevSecOps.
This entails being aware of details such as the number of servers you have, the operating systems they are using, and the person responsible for each server's configuration. This data will be necessary for your strategy and for testing any latest procedures or technologies you create.
4. List some of the highly popular used DevOps tools.
Some of the highly popular DevOps tools are:
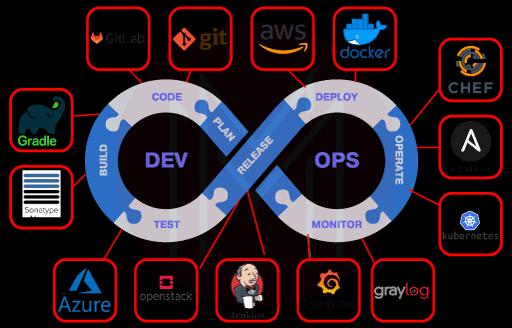
[ Related Article: DevOps Tools and Frameworks ]
5. How does DevOps increase system security?
Through VM images or scanning containers for defined software flaws, rejecting builds that include known problematic packages, and executing static analysis tools on calls to possibly harmful system functions, DevOps boosts system security.
6. Could DevOps be accomplished without establishing continuous delivery systems and procedures?
Yes. Ad-hoc automation of deployment, build, and environment provisioning operations could be used to implement DevOps with the primary objective of lowering MTTC and MTTR.
7. Differentiate between continuous delivery and continuous deployment.
| Continuous Delivery | Continuous Deployment |
| Makes sure that the secure deployment of code to production | All the changes that qualify the automated tests are automatically deployed to production. |
| Makes certain that business services and applications perform as anticipated | Improve the speed and reliability of software development and its release process |
| Brings each change to a production-like environment with the help of careful automated testing | Developers do not expressly approve, and a culture of monitoring has to be established. |
8. Do you think Kubernetes is secure?
Kubernetes has built-in advantages for security. As an instance, application containers are often replaced fully with new versions as opposed to being patched or updated. As a result, stringent version control is possible, and quick rollbacks are possible when a vulnerability in fresh code is found.
9. Describe the various stages of the continuous software delivery model.
Some of the steps of the continuous delivery model include:
- Developers checking in code that activates WebHooks and triggers CI Builds
- Application compilation and deployment artifacts creation
- Uploading deployment artifacts to artifactories
- Provisioning of test environments,
- Distribution of application artifacts across various test environments
- Production deployment of app artifacts.
10. How does maintaining the system's whole architecture benefit from continuous monitoring?
The process of finding, recognizing, and reporting any errors or risks in the system's complete infrastructure is known as continuous monitoring in DevOps.
- Makes sure that all resources, services, and applications are functioning properly on the servers.
- Checks the status of the servers to see if the applications are operating properly.
- Allows for controlled monitoring, transaction inspection, and ongoing audit.
11. Tell us about the Blue/Green Deployment Pattern.
This continuous deployment method is often used to cut down on downtime. Transferring traffic from one occurrence to another takes place here. We must swap out the outdated code with the new code version in order to use the same new code version.
The old version is present in a blue environment, while the new version is present in a green environment. We require a fresh instance out from the old one after doing changes to the old one in order to run the upgraded version of that instance.
12. Describe DevOps agile.
By embracing agile ideas and practices, such as enhanced automation and improved coordination between operations and development teams, DevOps is a method of software development that allows teams to build, test, and deliver software more quickly and reliably.
13. What DevOps stage should security be built in?
Every segment of the DevOps lifecycle, covering conception, design, maintenance, development, test, release, support, and beyond, should incorporate security.
14. What is Automation Testing?
To evaluate an application or system, automation is the action of automating a given manual procedure. Using independent testing tools to create test scripts that can be executed repeatedly without requiring human input is known as automation testing.
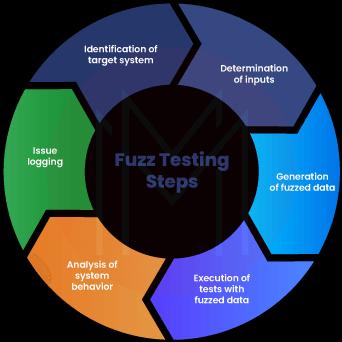
15. Tell us about fuzz-based testing.
Fuzz testing, also known as fuzzing, is a type of automated software testing used in the field of cybersecurity. It involves randomly introducing inaccurate inputs that are unusual and data into just a computer program in an effort to identify coding errors and security flaws.
DevSecOps Interview Questions and Answers For Experienced
16. What are the perks of continuous testing for DevOps?
With continuous testing, any code modification may be immediately tested. As a result, issues with quality and release postpones that could arise if big-bang testing is postponed until the completion of the cycle are avoided. Continuous testing makes it possible for high-quality releases to happen more frequently.
17. How would you assess the effectiveness of DevOps implementation across the organization?
The following metrics are used as the main indicators of DevOps success:
- Mean-Time-to-Change (MTTC): It's a metric for determining how rapidly a company can adjust to change. The time it uses to develop a change is divided by the total number of modifications made to arrive at the MTTC.
- Mean Time to Recovery (MTTR): MTTR is a metric that evaluates how quickly issues are resolved. By comparing the pre-and post-DevOps MTTR figures, one can utilize MTTR to assess the performance of DevOps projects.
- Mean-time-to-incident (MTTI): It's a metric that assesses the speed at which issues arise.
18. Describe Git.
DVCS or Distributed Version Control System is provided by Git. It can keep track of file changes and let you go back to any specific update.
The fact that it does not rely on a single server to save every version of a project's files is one of its distributed architecture's numerous perks over various Version Control Systems (VCS) such as SVN. Instead, every developer "clones" a copy of the repository I've labeled with "Local repository" in the diagram below and keeps the entire history of their project on an HDD so that, in the event of a server failure, all you need is one of your team members' local Git repository for recovery.
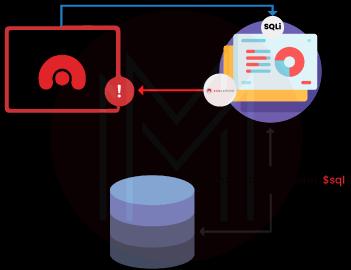
19. Tell us about DAST in DevOps.
Using simulated attacks, a web application is examined using dynamic application security testing (DAST) to identify vulnerabilities. By targeting the application as a spiteful user would, this kind of strategy assesses the program from the "outside in."
20. Many discuss creating a DevOps team to deploy DevOps in their organization. What do you think of this relationship?
There cannot be an independent DevOps team. This is so that Developers and IT/OPs employees can collaborate on a single team to achieve common Sprint (Agile SCRUM) goals, which is required by the DevOps philosophy of software development. As a result, the product team changes to follow the DevOps or DevSecOps mindset.
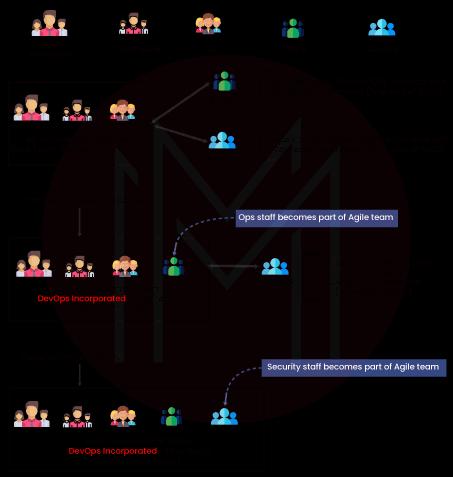
21. What distinguishes the DevOps or DevSecOps methods of software development from Agile?
The incorporation of IT/OPs and members of the Security staff in the Agile teams results in sprint goals that include events for IT/OPs and security staff members, which is the main distinction between DevOps/DevSecOps and traditional Agile teams. More significantly, the meaning of DONE is altered. The definition of DONE in Agile Scrum development is finishing a sprint with demonstrable software or artifacts. The concept of DONE alters in an Agile SCRUM team working with the DevOps/DevSecOps philosophy when producing demonstrable software or artifacts in a setting similar to production at the end of a sprint.
[ Check out Agile vs DevOps ]
22. What fundamental components make up tools for continuous testing?
The essentials of continuous testing are:
- Test Optimization - It ensures that experiments yield accurate findings and useful data. Examples of elements include test optimization management, test data management, and test maintenance.
- Advanced Analysis - It uses automation in areas like change effect analysis, scope assessment/prioritization, and static code analysis to prevent issues from arising as well as to accomplish more during each cycle.
- Policy Analysis - It ensures that all procedures are in alignment with the organization's shifting operational needs and that all legal obligations are upheld.
- Risk Assessment - To ensure that the build is prepared to go to the next stage, technical debt, test coverage optimization, risk mitigation responsibilities, and quality review are all covered.
- Service Virtualization - Assures the availability of real-world testing situations. Service visualization ensures its availability and cuts down on time needed to establish the test environment by giving availability to a virtual portrayal of the necessary testing phases.
- Requirements Traceability - It ensures that genuine criteria are met and that no additional work is required. An object assessment is used to identify the needs that need more validation, are at risk, and are operating as planned.
23. What may some of the duties of a DevOps/DevSecOps architect entail?
A DevOps Architect may be responsible for the following duties:
- Define the continuous delivery pipeline's architecture.
- Create and put in place self-service provisioning tools.
- Define and implement processes for configuration management.
- Make a plan for implementing DevOps across various teams.
- Ensure that DevOps is being used. Work with the operations team and developers to streamline the application delivery procedure.
- Identify the technology that will be used to implement DevOps. These technologies might have something to do with build, deployment, environment provisioning, or another component of automation.
- Manage and keep track of deployments of cloud infrastructure
- Sync with the monitoring tools to give users visibility into the state of the system.
24. What advantages does version control offer?
The advantages of utilizing version control are as follows:
- Utilizing the Version Control System (VCS), any team members are able to engage on any certain file at any time. The team will later be able to combine all of the improvements within a single version, thanks to VCS.
- Every occasion we save a fresh version of the project, the VCS prompts us for a brief description of the changes that were made. We also get a chance to look at the specific changes made to the file's content. As an outcome, we would be able to determine who changed the project and when.
- All of the prior versions and variants are correctly stored within the VCS. At any time, we will just be able to arrange any version, and we will have access to a snapshot of the overall project.
- All team members can access the entire project history using a distributed VCS like Git. This makes it possible for developers or other interested parties to access any teammate's local Git repository even in the event that the main server goes down.
25. How would you look at a project that needs to apply DevOps?
DevOps can be implemented using one of the following common methods in a particular project:
- Stage 1 - A road plan for the implementation will be created by the team after a two- to three-week assessment of the current process and implementation to determine areas for improvement.
- Stage 2 - Put together a proof-of-concept (POC). The team can begin the actual execution and walk into the project plan once it has been accepted and approved.
- Stage 3 - Your project is finally ready for the step-by-step use of DevOps employing version control, deployment, integration, testing, and finally, delivery.
The project is now prepared for DevOps implementation after adhering to the correct procedures for version control, deployment, integration, testing, distribution, and monitoring.
26. Why has DevOps been more popular in recent years?
First, discuss the current state of the market before discussing the increasing popularity of DevOps. Start by citing several instances of major players, like Netflix and Facebook, engaging in DevOps to expedite and automate application deployment and how this has aided in their business growth. You might use Facebook as one of the examples and discuss how its code ownership models and continuous deployment have allowed it to scale up while maintaining the quality of the user experience. Several hundred code lines are used without degrading the program's quality, dependability, or security.
The use case after that is Netflix. Similar procedures are followed by this on-demand and streaming video provider, which uses entirely automated systems and processes. Mention these two organizations' respective user bases: While Netflix has more than 100 million subscribers worldwide, Facebook has members that tally to 2 billion.
These are excellent illustrations of how DevOps can assist firms in ensuring higher release success rates, cutting the lead duration between bug patches, streamlining and automating continuous delivery, and generally lowering human expenses.
[ Related Article: Reasons For The Rise of DevOps ]
27. Please define an illustrative DevOps maturity model.
The stages that a company might consider moving through in order to succeed with the introduction of DevOps or DevSecOps include the following:
- Ad-Hoc: Complete on-demand ad-hoc tasks, including environment provisioning automation and build automation.
- Planned or Organized: Plan the project roadmap of DevOps; as part of the planning, select the team, tools, and frameworks to be used, as well as the necessary training and mentorship for the teams.
- Align & Assess: Perform important DevOps implementation proofs-of-concept for one or two teams. In order to use the strategy for a big rollout across many teams in the business, learn from the mistakes made and make the necessary changes.
- Implementation: Implement DevOps/DevSecOps across all teams in the enterprise to institutionalize the practice.
- Continuous Improvement: Take the lessons you've learned and keep working to make DevOps processes better.
28. What are the DevOps anti-patterns?
Patterns are standard procedures that organizations frequently follow. When a company keeps obediently adhering to a pattern that has been implemented by someone else but does not suit their needs, it creates an anti-pattern. The following are a few DevOps myths:
- DevOps → developers do production management
- DevOps → Process
- Can't perform the DevOps → Having the wrong people
- A whole another group needs to be created for DevOps
- DevOps → Agile
- The ultimate solution to every problem of organization → DevOps
- Unable to perform DevOps → Unique Organization.
29. Could you describe to us the DevOps idea of "Shift left to reduce failure?"
A DevOps concept called "shift left" can be used to enhance performance, security, and other aspects. Let's look at an instance: if we examine every DevOps process, we may conclude that security is evaluated before the deployment stage. By using the left shift method, we may increase security throughout the development period, which is on the left. [Will be shown in a schematic] Not just during development but also during testing, we may integrate with all phases. Due to the early failure detection, this probably increases security.
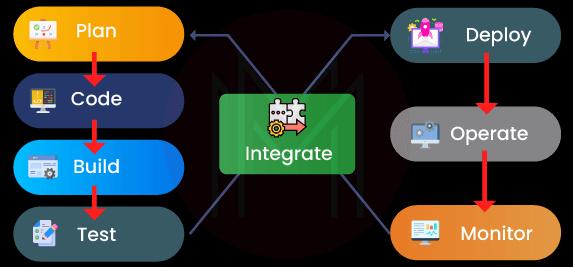
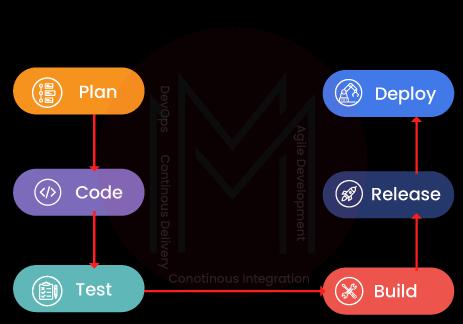
30. Describe the various phases of DevOps.
The following are the different stages of the DevOps lifecycle:
- Plan - Prior to beginning, a sort of application development project should have a plan in place. It's always wise to get a general grasp of the development process.
- Code - Application code has been written to meet the needs of the end user.
- Build - Create the program by combining the numerous codes that were created in the earlier steps.
- Test - The most important stage of developing an application is the test. If required, test the program and recompile it.
- Integrate - To combine several programs' codes into a single one.
- Deploy - To be used later, code is placed into a cloud environment. It is made sure that any fresh adjustments won't interfere with a popular website's functionality.
- Operate - If necessary, operations are carried out on the code.
- Monitor - The performance of the application is being watched. To adapt to end-user needs, changes are made.
[ Check out Complete Guide on DevOps Automation ]
Most Common DevSecOps FAQs
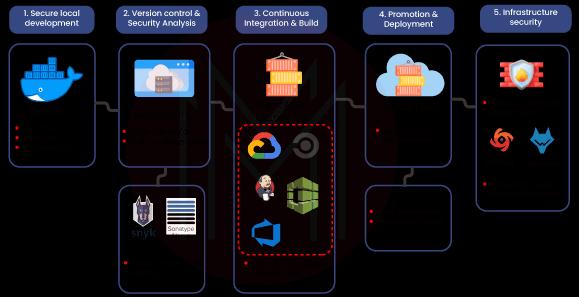
1. Tell us about the DevSecOps framework.
DevSecOps integrates security procedures and generates security and compliance objects automatically throughout the process to help guarantee that security is covered as part of every DevOps activity.
2. What exactly are DevSecOps tools?
The primary objective of DevSecOps build tools is automated security analysis of the build output object. Static application software testing (SAST), unit testing, and software component analysis are all crucial security procedures. To automate these tests, tools can be added to CI/CD pipeline that already exists.
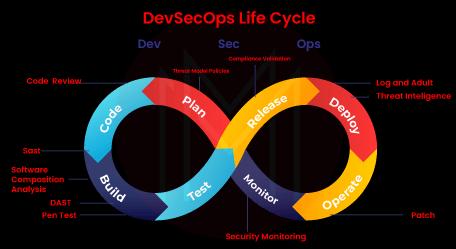
3. List the prime components of DevSecOps?
The prime components of DevSecOps are:
- Application/API Inventory
- Compliance monitoring
- Cultural factors.
- Custom Code Security
- Open Source Security
- Runtime Prevention.
4. What exactly is CI/CD DevSecOps?
Security engagement is encouraged to become a significant or active component of the life cycle of software development by DevSecOps (SDLC). Processes like CI/CD or Continuous Integration and Continuous Delivery have been introduced by the General DevOps.
5. Do you think DevSecOps is a methodology?
To increase the security of your SDLC, DevSecOps is a necessary methodology that must be incorporated into your DevOps process/pipeline.
6. What are some examples of DevSecOps?
Scanning for security flaws in repository code, static code analysis, early threat modeling, security design reviews, and code reviews are a few instances of DevSecOps procedures.
7. How can you secure DevSecOps?
The following are some key practices for organizations looking to implement DevSecOps.
- Make automation your ally.
- Checking the dependencies on your code.
- Avoid taking on more than you can.
- Some tools are much more practical than others.
- Even though threat modeling is challenging, you've got to do it.
- Instruct secure coding to your developers.
[ Related Article: DevSecOps Tutorial ]
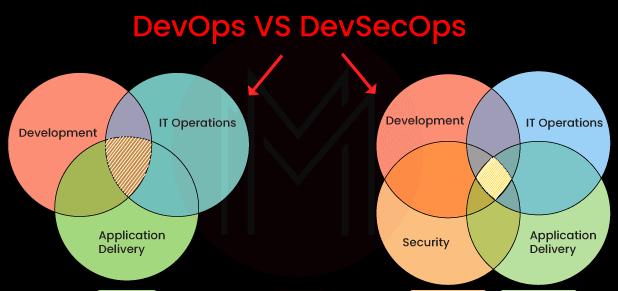
8. Differentiate between DevOps and DevSecOps?
As teams became aware that the DevOps methodology wasn't adequately addressing security problems, DevSecOps evolved from DevOps. DevSecOps arose as a method to integrate the management of security before all stages of the development cycle, as opposed to retrofitting security further into the build.
9. There are four pillars of DevOps. What are they?
Planning, sourcing, developing, and distributing are the four main components of a strong DevOps approach. By establishing these four latest software development and delivery pillars, your team will be able to produce apps at DevOps speed and scale while still being effective and agile.
10. What are the three components of DevOps?
The following fundamental elements should be part of any effective DevOps pipeline:
- CI/CD framework
- Build automation tools
- Source control management.
Conclusion
So here are some of the highly demanding questions to help you excel in your DevOps Interview. As a method to lessen security risks that span from an application deployment into code generation, DevSecOps has grown in popularity. Whether you've previously worked in DevOps or are a newbie to the field, we've covered almost everything from the total basic up to the latest techniques. We hope it helps, and All the Best for the interview!
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| DevSecOps Training | Feb 24 to Mar 11 | View Details |
| DevSecOps Training | Feb 28 to Mar 15 | View Details |
| DevSecOps Training | Mar 03 to Mar 18 | View Details |
| DevSecOps Training | Mar 07 to Mar 22 | View Details |

Viswanath is a passionate content writer of Mindmajix. He has expertise in Trending Domains like Data Science, Artificial Intelligence, Machine Learning, Blockchain, etc. His articles help the learners to get insights about the Domain. You can reach him on Linkedin
















