- Splunk API
- Splunk Careers
- IBM QRadar vs Splunk
- Splunk Architecture
- Splunk Admin Interview Questions
- Splunk Alerts
- Splunk Alternatives
- Splunk CIM
- Splunk Cloud
- Splunk Dashboard
- Splunk Dedup
- Splunk Education
- Splunk Enterprise
- Splunk Enterprise Security
- Splunk Eval Commands With Examples
- Splunk Interview Questions
- Splunk Logging
- Splunk Regex Cheatsheet
- Splunk Rest API Overview
- Introduction to Splunk Rex
- Splunk Search Commands
- Splunk Software
- Splunk Stats
- Splunk Streamstats Command
- Splunk Timechart
- Splunk Tool
- Splunk Tutorial For Beginners
- What are Splunk Universal Forwarder and its Benefits
- Splunk vs ELK
- Splunk Alert and Report
- Monitor Windows Event Log Data – Splunk
- Splunk Universal Forwarder
- What are the Splunkbase Apps and Add-ons
- Splunk Join - Subsearch Commands & Examples
- What are Splunk Apps and Add-ons and its benefits?
- Splunk Connect For Kubernetes
- Grafana vs Splunk
- Elasticsearch vs Splunk
- Splunk vs Dynatrace
Usually, we all search for a lot of information on the internet, don’t we? If we don’t get the required results, then we stop. But have you ever thought about what rests in those page results? “Information”! And we can get this free information using various tools. Certainly, tools play a major role in today’s world, but without understanding the proper usage of a tool will leave you helpless.
Want to be part of the Power BI real-time environment? then visit here Power BI Online Course
Let’s explore the wide range of OSINT Tools in this article. But before diving into the tools, it’s necessary to know what is open-source intelligence and how it can be helpful for us.
Table Of Content
- ShadowDragon
- Maltego
- Google Dorks
- TinEye
- Shodan
- TheHarvester
- Search Code
- Recon-Ng
- Creepy
- SpiderFoot
- CheckUsernames
What is Open-Source Intelligence?
OSINT (Open Source Intelligence) is referred to as the process of collecting raw data legally from public sources over the internet, analyzing it, and using it in a raw intelligence context. Link crawling search engines often miss this data. But, there is a plethora of data available on the internet, so scouring all that is not possible. So, here comes Open Source Intelligence tools and techniques that dive deeper into the internet than a simple search on any search engine and collect data from numerous sources and scatter the open-source data conveniently in a matter of minutes. So, let’s take a look at some of the best open-source intelligence tools that have managed to make a splash recently.
Top 10 OSINT Tools Available in the Market
Here is the list of OSINT - open-source intelligence tools according to popular search engines
#1 ShadowDragon
ShadowDragon is an open-source intelligence (OSINT) tool that you can use to gather, process, and integrate information from public platforms. It can be used for monitoring and analysing data.
ShadowDragon products
The ShadowDragon tool is offered in three different formats.
- HorizonTM
This tool transforms data into intelligence and then into actions. It helps users to make investigations from anywhere, anytime. It enables access to billions of OSINT records.
This tool helps identify suspects, verify identities, and analyse networks for fraud with speed and clarity.
It converts scattered data into clear connections. So you can get the complete picture of the data. It acts as an ideal tool for fraud analysis and law enforcement.
- Horizon SocialNet
This tool is an API engine that connects with over 500 data sources and 1000 endpoints. It visualizes connections across platforms. You can use this tool to discover relationships, track digital behaviours, and identify links across social networks, domains, and forums.
- Horizon Monitor
This tool helps you to understand threat actors and emerging threats across dark web sources. It helps track malicious actors and keywords with real-time alerts.
#2 Maltego
Maltego is developed by Paterva and is also a part of the Kali Linux bundle. It helps to perform significant reconnaissance of any target using built-in transforms. You should register on the Paterva site for using Maltego, and it is free of cost. After registering, you can use this tool to design and build effective digital footprints of the specific target.
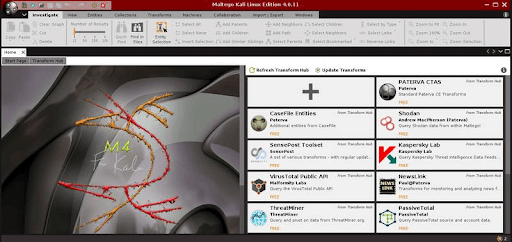
This tool is majorly used by security, law enforcement, and forensics professionals to collect and visualize data efficiently. The collected data from various sources is displayed graphically. Expected results may occur from domain to IP conversion, and netblock will be identified as the number is also identified, even the locations and phrases as well. All these are icons in Maltego that provide comprehensive information and view. So finally, it’s an outstanding tool for tracking the footprints of entities over internal networks and the internet.
#3 Google Dorks
Search engines do provide us with a lot of information, and Google is popular of all, which is used to gather information about a target. Google Dorks is one of the most useful open-source intelligence tools, which provides such information using some amazing operators, and it has been in place since 2002. Dork helps you to make more targeted searches efficiently.
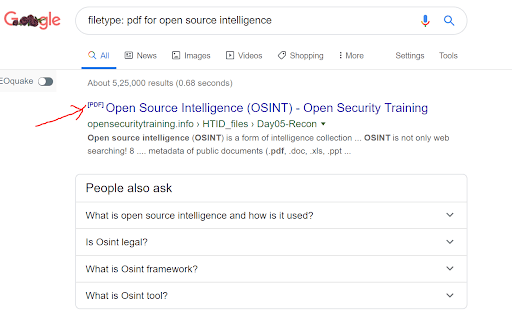
Google Dorks are often referred to as GHDB (Google Hacking Database) and are specifically intended for pen-testers during the information-gathering phase.
The following are some of its operators:
-
Ext: This is used to define what file extension to look for specifically.
-
Intext: This is used to find certain text on a page.
-
Filetype: This is used to find specific file types that a user needs to look for.
-
Inurl: This is used to retrieve web pages with a certain text in their URLs.
-
Intitle: This is used for retrieving web pages that have a certain text in their title.
Search engines also index log files and dorks can access them to find vulnerabilities and hidden data.
#4 TinEye
TinEye is another excellent tool that helps to do an image-related search on the web. You can even check if the image is available online and where that image appeared. It uses machine learning, neural network, and watermark/pattern recognition to look for similar images on the web rather than keyword matching. This tool helps to search images on social media websites using the reverse image search option
The image search can be made using an image URL or an image itself. Instead of accessing web applications repeatedly, API and browser extensions can also be used to look for a particular image directly.
#5 Shodan
Shodan is a “search engine for hackers”, as it gives a huge footprint of devices that are connected online. Instead of showing the results like other search engines, it’s a gold mine for researchers to see the exposed assets that have connected to the network.
This open-source tool primarily helps to identify the target and test it for different vulnerabilities, passwords, services, ports, etc. for security analysts. It offers users the topmost flexible searches. It is used as a Threat intelligence solution
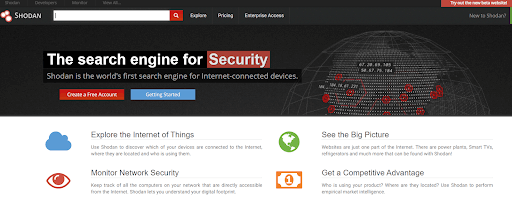
For example, anyone can view the connected webcams, traffic lights, netcams, etc. The following are some of the use cases of Shodan:
-
Using the RDP port open to testing the available assets
-
Assets with VNC viewer
-
Testing “default Passwords.”
-
This OSINT tool can also be used for monitoring databases to check whether they have any data leaks on public sites.
#6 TheHarvester
TheHarvester is developed in Python, and this amazing tool is used for collecting data from specific targets using detailed search patterns. This open-source tool mostly deals with emails and domain information. It is inbuilt into kali, is fast, and easier to use.

It collects valuable data like employee names, subdomains, virtual hosts, and open ports from search engines, and it’s also an ideal choice for organizations looking to perform penetration testing on their own network. Some of the most public sources like Hunter, Google, and Baidu, are also included for passive reconnaissance. You can also install some modules with an API key, such as GitHub, bing API, and many more.
#7 Search Code
While compared to text, searching for a code snippet is quite hard to find results on a search engine. But with search code, you can find a line of code that could be present from various code-sharing websites. You can search for functions, operations, variables, and anything that can constitute a code segment. Search results can be further filtered based on a particular language or repository.
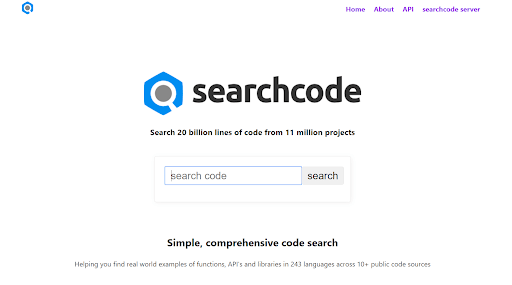
This tool checks for code in repositories of code from Bitbucket, GitHub, GitLab, Google Code, CodePlex, and more. Key features of this tool include search using special characters, source code, filter by the repository, and programming language.
#8 Recon-Ng
Recon-Ng is another valuable tool built into Kali Linux used to make a reconnaissance on the target. The total strength of this tool rests in the modular approach. Recon-ng has different modules inbuilt, and its usage somewhat resembles that of Metasploit. The tool also supports helpful features like database interaction, command completion, API key management, contextual help, and standardized outputs.
Workspaces are created to carry out all the operations inside modules. The domain can be specified using add domain <domainname> inside the workspace. After domains are added, recon-ng modules extract information about that domain.
There are some excellent modules like bing-domain-web and google-site-web, to check further domains related to the initial target domain. The outcome of those domains will be all indexed domains to these search engines. Finally, this is an excellent open-source tool.
#9 Creepy
Image sharing is one of the most used features of social media platforms. But while sharing sometimes we even share the exact location of where the image was taken. Creepy is a python application tool that extracts that details and presents the geolocation on a map. It collects geolocation data through various social networking platforms and presents reports as a search filter based on the exact date and location.
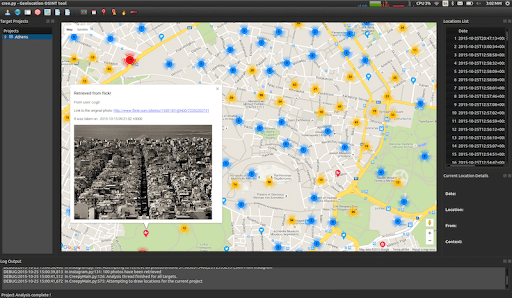
Creepy supports the search for Twitter, Flickr, and Instagram, and reports can be downloaded in CSV or KML format for additional analysis.
#10 SpiderFoot
SpiderFoot is a reconnaissance OSINT tool. It automatically queries over 100 public data sources to collect intelligence on domain names, emails, IP addresses, and more. It is mostly known as the fingerprinting with the most extensive OSINT collection
Just by specifying the target you want, SpiderFoot will gather information to build up a knowledge of all the entities and how are they related to each other. The software of this tool is written in Python. To get started with SpiderFoot, define the target and pick among the hundreds of different fingerprinting modules.
#11 CheckUsernames
Social media holds a lot of data, so looking for a username on different major social networks is a time taking task. By using CheckUsernames, you can perform a search for a username on several social networks at the same time. It will search for a particular username on more than 160 websites. The users can check the presence of a target on a specific site to make the attack more targeted. This tool is very useful for cybersecurity kind of activities
So, finally, it's a quick and useful tool for checking your brand across major social networks, in one simple search.
Conclusion:
With data growing every day, we all need the right tool to perform analysis and forecasts that help to make the most out of it. All these OSINT tools discussed above are a part of the new trend that will help you with that.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Power BI Training | Mar 03 to Mar 18 | View Details |
| Power BI Training | Mar 07 to Mar 22 | View Details |
| Power BI Training | Mar 10 to Mar 25 | View Details |
| Power BI Training | Mar 14 to Mar 29 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .
















