- Abstraction in Java
- Clojure Tutorial
- Control Statements in Java
- Core Java Interview Questions
- Data Types in java
- Top 9 Java EE Frameworks
- Java EE vs Spring Framework
- Java Frameworks List - Top 14 Java Frameworks
- Java Interview Questions
- Java Tutorial
- Java Web Dynpro Interview Questions
- JavaFX Interview Questions
- Method Overloading in Java
- Multithreading in Java
- List of Popular Open Source Java Build tools
- Operators in Java
- Program Logics in Java
- String Handling in Java
- Why You Should Learn Java Programming
- Data Structures Interview Questions
- Exception Handling in Java
- Multithreading Interview Questions
- Design Patterns Interview Questions and Answers
- C++ Interview Questions and Answers
- JSP Interview Questions
- EJB Interview Questions
- SOAP in Web Services
- JPA Interview Questions
- DXC Interview Questions and Answers
- Java Concurrency Interview Questions
- What is Java Concurrency?
- What is JPA - Complete Tutorial Guide
- What is EJB?
- Java Collections Interview Questions
- Java Swing Tutorial
- Java Stream Tutorial
- Linked List Interview Questions
- Compiler Design Interview Questions
- Java Collection Tutorial
- Java Stream Interview Questions
- Thymeleaf vs JSP
- Thymeleaf Tutorial - What is Thymeleaf
- Socket Programming in Java - What is TCP
- Apache Tomcat Interview Questions
- Capgemini Interview Questions
- Zoho Interview Questions
- PwC Interview Questions
- Hexaware Interview Questions
- Intuit Interview Questions
- Tech Mahindra Interview Questions
- Qualcomm Interview Questions
- Arcesium Interview Questions
- PayTM Interview Questions
- DXC Technology Interview Questions
- Java Developer Job Description
- MAQ Software Interview Questions
- Amdocs Interview Questions
- TCS NQT Interview Questions
- Virtusa Interview Questions
- Siemens Interview Questions
- Tricky Java Interview Questions
A Java Technical Architect oversees creating, integrating, and updating a comprehensive architecture that supports Java applications to help a business reach its objectives. They must be able to recognize performance bottlenecks, eliminate them, and create scalable systems to succeed in this position. They must be well-versed in the principles of Java and have prior knowledge of distributed systems and microservices. Now keep reading to find out more about Java Architect Interview Questions!
Some basic facts about Java:
- Java shares a whopping 33.27% market share in the world of programming languages globally, as per Statista.
- The average salary of a Java architect in the USA is $150,000 per annum.
Now let's skim through the following Java Architect Interview Questions- 2022 (updated) for:
Top 10 Java Architect Interview Questions
- What does Java's Final Keyword mean?
- Define message-driven design and list its advantages?
- Explain the Architecture of Java J2EE?
- Tell us about the various methods in Servlets for session management?
- How to dodge the Lazyinitializationexception?
- Describe the types of JDBC architecture?
- State the advantages of using the Lambda Expressions
- How can one do database migration?
- What are some essential elements of Hibernate Architecture?
- What is Cloud Computing? Mention the benefits of the same.
Java Architect Interview Questions For Freshers
1. What does Java's Final Keyword mean?
Java programmers use the Final Keyword to declare constants. Any element defined with the keyword Final cannot later have its values modified. When a method is final, its subclasses cannot override it. Additionally, because they are resolved at build time, the Final methods are quicker than the others.
2. How do you dodge a database deadlock?
I would create a queue to validate each request before sending it to the database to prevent the database from entering a cyclic wait stage. Using fewer cursors to prevent locking the tables is another approach to get around this problem. Another method to prevent a database deadlock is to use a short transaction.
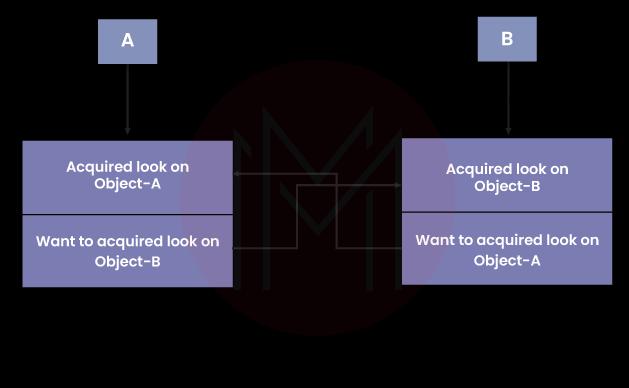
3. State the main difference between Abstract Class and Interface in Java?
Interface and Abstract Class are fundamentally different from one another in that the former only permits the definition of public static methods. It does not contain any application of the aforementioned approaches.
Contrarily, abstract classes are open to any access specifier, whether or not it has a class implementation. Another distinction is that a class that implements an interface must also implement all the interface's methods. On the other hand, this is not necessary for Abstract Class.
4. How can you differentiate Hibernate from JDBC?
Hibernate and JDBC's respective architectural distinctions impact how they are utilized. One of the main differences is that JDBC lacks an object-relational mapping (ORM) mechanism, whereas Hibernation has one.
Regarding caching, the two also differ from one another. Hibernate features a caching system that stores data for later use, unlike JDBC, which does not. This method works in conjunction with its automatic object mapping functionality. As a result, JDBC starts up a little quicker than the Hibernate.
| Know More About "Classes and Objects in Java" |
5. Define message-driven design and list its advantages?
By applying standardized message-oriented middleware to deliver messages from one module to another module, message-driven architecture aims to connect distributed systems.
- It is asynchronous and non-blocking.
- System resources can be released instantly without having to wait for a response. It lowers contention and increases the likelihood of greater scalability.
- Messages can be sent when the recipient is available.
6. Does importing packages automatically import sub-packages in the Java language?
No. Only the packages and not the sub-packages will be imported if we import packages. If necessary, the programmer must import the sub-packages independently.
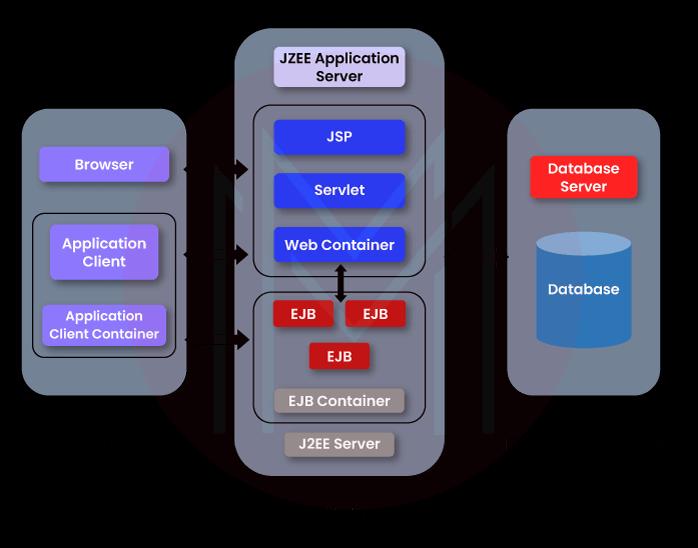
7. Explain the Architecture of Java J2EE?
- J2EE, or Java 2 Enterprise Edition, offers a practical method for creating and using Java enterprise applications. Client, Middle, and Enterprise Data Tiers are the three layers that make up the J2EE architecture.
- Client Tier - A client tier is an interactive tool used to communicate with the client or user. There are web clients and application clients in it.
- Middle Tier - The operational units are specified in the Middle Tier.
- Data Tier - The Data Tier's primary function is storage. A relational database, containers, components, and services are some of the ways it is used.
8. How is exception handling performed in the Spring MVC Framework?
The following methods are available in Spring MVC to configure exception handling in our program:
Controller-based: Here, we define techniques for handling exceptions. All that is required is to annotate these methods with @ExceptionHandler.
The @ControllerAdvice annotation is used as a global exception handler. The definition of the global exception handler can be done using any class.
Implementation of the HandlerExceptionResolver: To develop global exception handlers, Spring MVC offers HandlerExceptionResolver. This approach was chosen since the Spring framework also provides a few default classes that may be included in our spring bean configuration file to gain the advantages of exception handling.
| Read more in this "Exception Handling in Java" Now! |
9. What particularly does Java8 support functional programs?
Nearly everything was object-oriented before Java 8. Java only has primitives; anything else is an object. Methods/Functions didn't just appear out of nowhere. All method/function calls must be made using references to objects or classes.
Functional programming was introduced in Java 8 and enabled this. The best object-oriented language is Java. All data types in Java other than rudimentary ones are in the form of objects. As a result, anonymous functions are a practical choice.
Even lists are objects made by classes. A function or method cannot be defined in Java and then remain in Java. In that case, there is no way to return the body of a method or pass a method as a parameter.
10. Tell us about the various methods in Servlets for session management?
Sessions are states of communication between the client and the server. As a result, several responses and requests may be made throughout a single session. Due to the statelessness of the Web Server and HTTP, a session is only maintained when the client and server send the session ID (or another distinctive identifier about the session) in all requests and answers.
Among the techniques for managing servers are:
- URL Rewriting
- session management API
- HTML hidden fields
- User authentication
- Cookies
11. Describe Domain Driven Design?
Domain-driven design is a technique and process prescription for creating complex systems that focuses on translating activities, processes, events, and data from a problem domain into the technical objects of a solution area. Making your program a realistic depiction of a system or process is key.
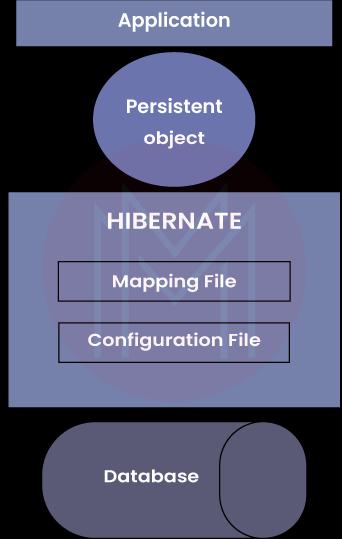
12. Tell us about the Hibernate Architecture concerning its layers.
The given four layers are there in Hibernate Architecture:
- Application layer
- Framework layer
- Backhand API layer
- Database layer
13. What criteria do you use to choose between locally installed software and web applications?
The structure I employ is dictated by the overall objective the client hopes to accomplish with their application. Before applying for the position, I closely worked with clients to ascertain the objectives they had for their program. For instance, a large-chain shop requires a complex web application to manage client internet purchases. I met with the client to identify the most important application criteria, and I used these details to choose a web application that would better support the client's commercial success.
14. How to dodge the Lazyinitializationexception?
Follow these steps shown below to avoid the Lazyinitializationexception in Java:
- Lazy is set as false in the config file of hibernating.
- Set @Basic(fetch=FetchType.EAGER) at the mapping.
- Make sure you access the dependent objects before closing the session.
- Using Fetch Join in HQL.
15. Tell us about the differences between a local variable and an instance variable?
A local variable is utilized within a method, block, or constructor– and is specific to that scope. A variable not local to its scope won't be known to other methods or blocks in the class.
On the other hand, an instance variable is linked to its object. These variables are declared outside of the procedure but inside of a class. The instance variable is accessible to all the class's methods and blocks in this manner.
Java Architect Interview Questions For Experienced
16. Describe the types of JDBC architecture?
The JDBC design uses two-tier and three-tier processing models to access a database. These are listed below:
Two-tiered structure: A Java program speaks with the data source directly. The JDBC driver makes communication possible for the application and data source. When a user submits a query to a data source, the data source responds with results that are provided back to the user.
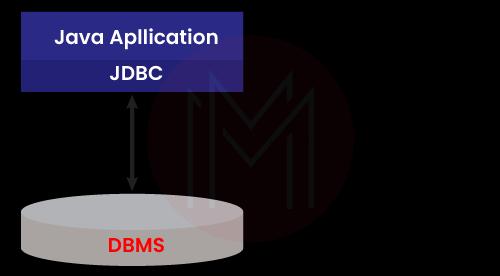
The data source may be on a different computer connected to the user's network. In a client/server configuration, the system used by the user serves as the client while the machine running the data source serves as the server.
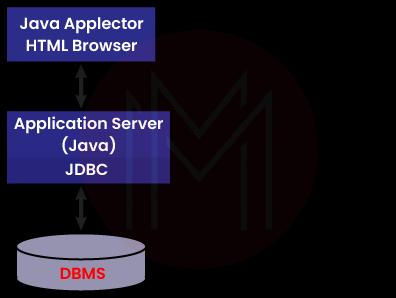
Three-tier model: The user's commands are transferred from middle-tier services back to the data source in this architecture. The middle tier receives the results and relays them to the user.
This sort of model is helpful to management information system directors.
17. What are the gains (advantages) of using Spring Framework in Java?
For creating enterprise Java applications, Spring is a potent Java framework. Some major advantages of adopting the Spring framework include the following:
- It helps in managing business assets and making its services available.
- It makes XML-based and annotation-based configurations easier.
- Utilizing interfaces and predefined classes enables a simple and effective programming technique.
- Because it is modular, we can pick and choose which components to work on.
- It offers assistance for programming using the POJO and POJI models.
- It supports a compact container that is simple to use.
18. State the differences between Monolithic, SOA, and Microservices Architecture?
The LTS version's goal is to finish the preview features and make them reliable and presentable over the following three years:
- In a monolithic architecture, all the software components of the application are integrated and firmly wrapped inside a big container.
- A collection of services that communicate with one another is service-oriented architecture. Simple data transfer or the coordination of such actions by two or more services are both examples of communication.
- Microservice Architecture is a type of architectural design that builds applications as a collection of tiny, independent services based on a business domain.
19. What are the most typical memory leaks, and how do you think you would deal with them?
Memory leakage through static fields:
The frequent use of static variables is one scenario that frequently leads to memory leaks. When using static variables, we must be careful. Collections and huge objects designated as static take up valuable memory that may be used elsewhere during the program's lifetime.
Reduce the use of static variables and, when using singletons, implement them so that the object is loaded slowly rather than quickly.
Unclosed resources:
Java memory leaks can occur if you don't remove a reference to an object or fail to close a resource. Unclosed file/text buffers Improper equals() and hashCode() implementations.
It's common to overlook including appropriate overrides for the equals() and hashCode() methods while developing new classes.
These actions are performed by HashSet and HashMap using these methods, and if they are incorrectly overridden, memory leaks may result.
In this case, duplicate objects will accumulate and take up more memory if we don't override the equals() and hashCode() methods in the Employee class, which is why many instances will be produced in memory.
As a result, this Map would only contain one Employee object if we had overridden the equals() and hashCode() methods in the Employee class.
finalize() Methods
The objects of a class that have to finalise() function overridden are not instantly disposed of. Instead, they are placed in a queue for the GC to finalize later.
Additionally, our application will eventually run into an OutOfMemoryError if the finalise() method's logic is inefficient, and the finalizer queue cannot keep up with the Java garbage collector.
20. State the advantages of using the Lambda Expressions
Some of the key advantages of using the lambda expression are:
- The code lines needed to be written get reduced by lambda expressions.
- It increases readability.
- It eliminates shadow variables.
- It provides functional programming.
- It increases the code reusability.
- T provides enhanced iterative syntax.
- It provides simplified variable scope.
- It allows JAR file size reductions.
- It supports Parallel processing opportunities.
21. When should someone use a NoSQL database rather than a relational database?
In relational databases, the ACID is enforced. As a result, transaction-oriented schema-based data storage is possible. It is tried and true for 99 percent of applications in the real world. With relational databases, practically anything is possible.
There are performance and scalability restrictions regarding large, high-availability data warehouses. Terabytes of data, for instance, are kept in huge data centers like Google and Amazon. Because of the blocking, schema, and transactional characteristics of the RDBMS in these situations, querying and inserting are unsuccessful.
They have therefore introduced their databases to greatly improve performance and allow for scaling (actually, key-value stores).
- When the client demands 99.999 percent availability at busy sites, we typically employ NoSQL databases.
- Your data is illogical in SQL, and you frequently need to run several JOIN queries to get a single piece of data.
- The relational model is separated, denormalized data is stored in CLOBs, and external indexes are built to find that data.
| Read more in this NoSQL database Now! |
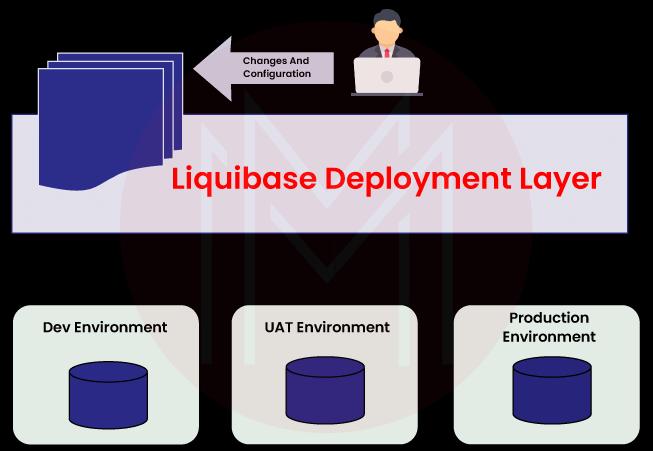
22. How can one do database migration?
Two technologies that aid in managing, tracking, and deploying database schema changes are Liquibase and Flyway. They are both migration-based technologies that, by considering database code like app code and automating it, seek to close a gap in many teams' workflows.
23. What technologies and tools do you use to look out for performance bottlenecks?
To find performance bottlenecks, a variety of methods and technologies are available. Among the most well-liked are:
- New Relic: It's a software analytics platform that aids in real-time application monitoring. I can discover and address bottlenecks quickly because of the extensive performance insights it offers.
- AppDynamics: It's an additional application performance monitoring tool that offers in-the-moment perceptions of the performance of applications. Additionally, it provides options like custom dashboards and code-level tracing.
- Dynatrace: It's a thorough application monitoring solution that includes capabilities like AI-powered root cause analysis and automatic issue identification.
24. What are some essential elements of Hibernate Architecture?
The following are the essential elements of Hibernate Architecture:
- SessionFactory
- Session
- Transaction
- ConnectionProvider
- TransactionFactory
SessionFactory
The session objects are kept in the session factory. It includes the secondary data cache ( optional). The org.hibernate is used. A factory method to retrieve the session object is provided by the SessionFactory interface.
Session
The session object serves as a conduit between the database and the application. It offers the application an interface to access the database's stored data.
The JDBC connection is contained within the session object, which has a limited lifespan. It serves as a factory for the many session components, including query, transaction, and criterion. It houses the primary data cache (mandatory). The hibernate.org. The session interface offers ways to add, update, and remove the object. The factory methods for Transaction, Query, and Criteria are also included.
Transaction
The atomic component of the tasks is contained in the transaction objects. It's a choice-based component. Methods for managing transactions are provided via the 'org.hibernate.Transaction' interface.
ConnectionProvider
JDBC connections are provided via the 'ConnectionProvider'. It is a choice-based component. It removes the application's dependence on "DriverManager" or "DataSource."
TransactionFactory
The element TransactionFactory is optional. The transaction objects are kept there.
25. How do you go about creating a project's scalable architecture?
Java architects' top issue is scalability. I take the project's predicted expansion into account when creating a scalable architecture. You must create an architecture that can manage more data and traffic without stuttering or crashing. When creating a scalable architecture, the following factors must be considered:
- Use scalable components: Decide on components that can be expanded vertically or horizontally by adding new instances (by adding more resources to a single instance).
- Designing failure: Consider the possibility of anything going wrong when designing your building. Redundancy must be used, and fail-over systems must be in place.
- Monitor performance: This will help you find bottlenecks and other potential problems. To keep everything functioning properly, be ready to modify the architecture as necessary.
26. How are production Spring Boot applications managed and watched over?
A Spring Boot sub-project called Spring Boot Actuator gives your production-ready apps new monitoring and management features. It provides a variety of HTTP or JMX endpoints for communication.
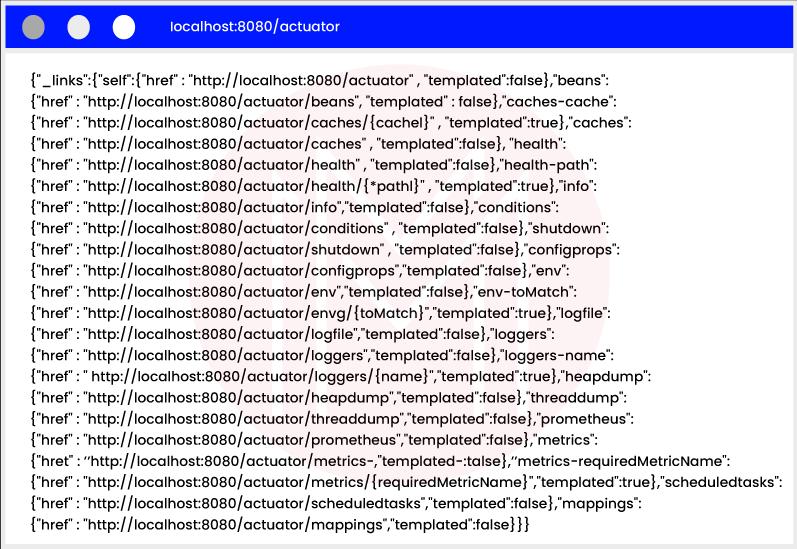
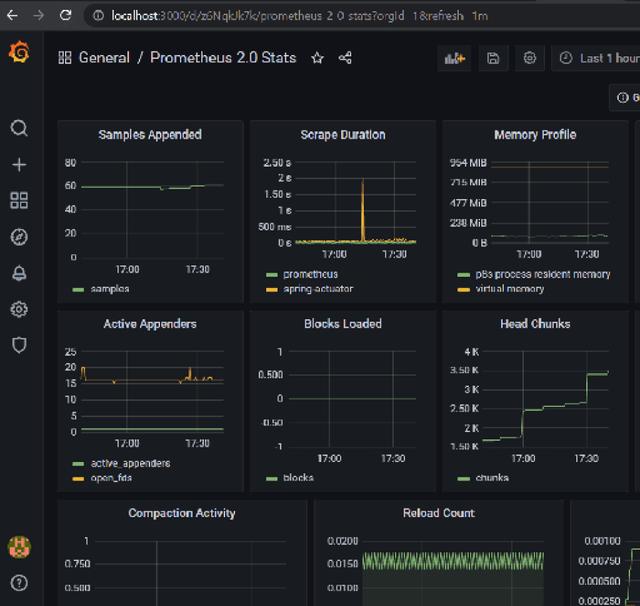
The Spring Boot Actuator supports the Prometheus (a tool for monitoring) endpoint, which is frequently pulled for metric data and provides a graphic representation of data. Another option is to use Grafana, which has many graphical representations.
Below is a graph created using Grafana and data from Prometheus.
27. Can you tell us how exactly Design Principles are different from Design Patterns?
The guiding principles for all software development, regardless of platform or programming language, are known as design principles.
Design Principles Examples:
- Abstraction as a source of dependency rather than concrete classes.
- This program's primary emphasis is on interfaces rather than implementations.
- Design patterns are solutions to often occurring generic problems, but they are not exact programs that can be utilized to solve your problem; rather, you must modify them to meet your needs. Design Patterns are pre-existing solutions that have undergone extensive testing and are secure to use.
Design Patterns Examples:
- To separate, distinct layers of the application(Business Repository, Data Repository), utilize the repository design pattern.
- Use the single design pattern if you need one instance of a class.
28. What can assets besides the architecture itself be considered members of a product line?
An asset collection is made up of various elements such as:
- Reusable Components: While not directly related to code reuse, this item incorporates and makes use of every component from previously built and successful system sections. This entails reusing the structure, design, documentation, and other aspects of the component.
- Personnel can move easily between projects and pick up on changes if the products have the same structure.
- Finding and correcting a problem in a project where a component is reused helps with other projects.
- It is easier to plan a project when you have prior knowledge of how it will perform, which is a challenge that impacts all goods to some extent.
- There is an increase in predictability. Because of how they were previously formed and understood, processes, methods, and instruments are routinely recycled.
- The advantage of observing systems in operation and functioning is that it shows a company's capacity to keep its promises.
29. What is Cloud Computing? Mention the benefits of the same.
A computer system based on the internet called "cloud computing" enables storage and online access to digital data and applications.
- Access to storage, software, processing power, and other resources is available instantly, thanks to the internet. The cost of the available storage and services must be covered by the technology's users.
- Significant aspects include scalability and elasticity, self-service billing, automatic de-provisioning, and self-service provisioning.
- One of the main benefits of the service is the absence of capital expenses for software and hardware acquisitions.
- Cloud computing's tremendous server capabilities increase access speed. Additionally, it provides secure backups, a ton of storage, and increased productivity.
30. What does the term SOLID mean? What principles does it uphold?
The abbreviation SOLID stands for the initials of Robert C. Martin's first five object-oriented design (OOD) principles, which are:
- S - Single-responsibility principle: A class should only have one job and should have one reason to change.
- O - Open-closed principle: Objects and entities should be open for extension but closed for modification, according to the open-closed concept.
- L - Liskov substitution principle: Let q(x) be a property that can be proven to exist for objects of type T that fit the description of x. Then, for objects, y of type S, where S is a subtype of T, q(y) should be provable.
- I - Interface segregation principle: it states that no client should ever be required to develop an interface that it does not use or to rely on methods that it does not use.
- D - Dependency Inversion Principle: it states that entities must depend on abstractions rather than concreteness. It states that the high-level module should depend on abstractions rather than the low-level module.
Frequently Asked Java Architect Interview Questions
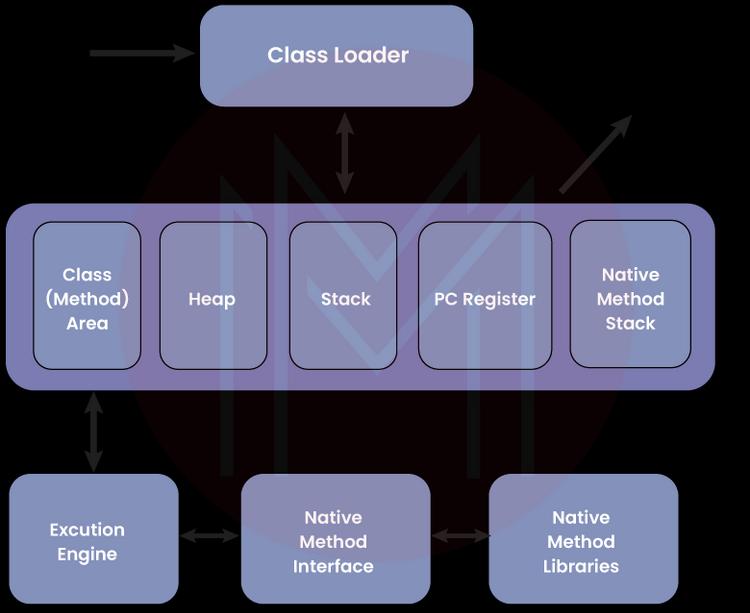
1. What are the main parts of the JVM?
Three distinct parts make up the JVM:
- ClassLoader.
- Runtime Memory/Data Area.
- Execution Engine.
2. Define the JIT compiler in Java?
The JavaTM Runtime Environment includes the Just-In-Time (JIT) compiler, which boosts Java programs' runtime performance. Classes in Java applications contain platform-neutral bytecodes that a JVM may understand on various computer architectures.
3. In JDK, what files are present?
JDK and JRE File Structure include:
- bin. java*
- localedata.jar. lib. applet. Charsets.jar. ext. fonts. security. rt.jar. sparc. server. client.
4. Tell us about the 3-tier model in Java?
Commands would be sent to a "middle tier" of services in the three-tier paradigm, which transmits the commands to the data source. The middle tier receives the results from the middle tier, which then provides them to the user when the data source has processed the commands. Because the middle tier allows for the maintenance of control over access and the kinds of adjustments that can be made to company data, MIS directors find the three-tier model particularly alluring. Another benefit is that it makes application deployment simpler. Finally, the three-tier architecture frequently offers performance benefits.
Until recently, the intermediate tier was frequently programmed in performance-oriented languages like C or C++. However, the Java platform is quickly replacing other platforms as the preferred one for middle-tier development thanks to the advent of optimizing compilers that convert Java bytecode into effective machine-specific code and technologies like Enterprise JavaBeansTM. This is a huge bonus because it enables using Java's multithreading, security, and robustness capabilities.
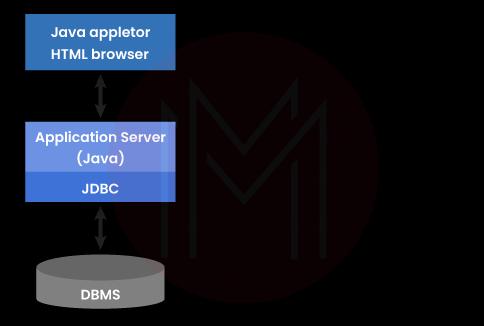
5. What is JDBC vs. ODBC?
Microsoft developed the ODBC Application Programming Interface (API), which allows Windows software programs to connect to databases using SQL. Open Database Connectivity, as its name suggests, literally means that it is compatible with all languages, including C, C++, Java, and others. Sun Microsystems developed the JDBC SQL-based API to allow Java programs to use SQL for database access. It refers to a database connectivity feature that is solely available for Java.
These APIs enable connections between a client-side application and a server-side data source, whether those two locations are the same client computer or different server machines.
6. What is heap memory in Java?
The region of memory used to hold objects created by JVM-based applications is the Java heap. As long as the program runs, heap memory is allocated when the JVM is started and any items can be shared between threads.
7. How many architectures are there in Java?
JVM, JRE, and JDK are the three primary parts of the Java language. Their full forms are Java Development Kit, Java Virtual Machine, and Java Runtime Environment, respectively.
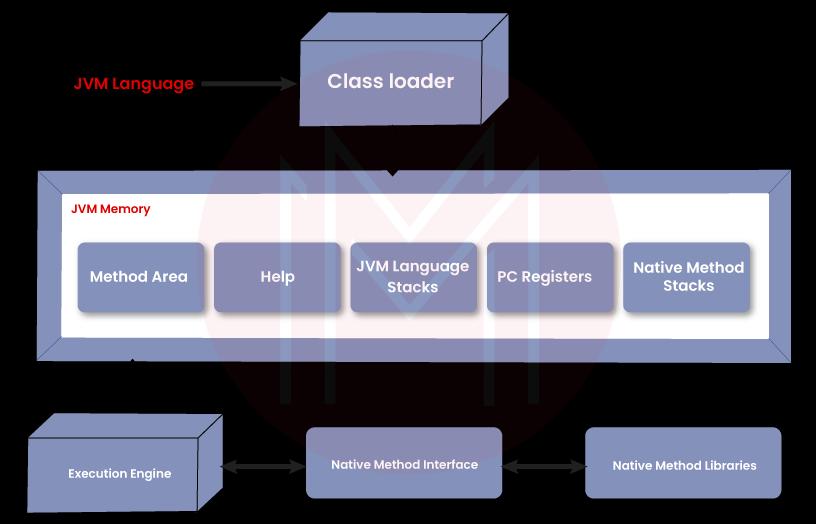
8. Tell us about the differences between JDK, JRE, and JVM?
JDK is largely used for code execution and contains essential development functionality. JRE, on the other hand, is mostly in charge of building the environment for code execution. On the other hand, JVM describes every implementation and oversees giving JRE these implementations.
9. Tell us about garbage collection in Java?
Java programs automatically manage memory using garbage collection. Programs of Java can be executed on a Java Virtual Machine, or JVM, by compiling to bytecode. Objects are made on the heap, a part of memory allocated for the application when Java programs are launched on the JVM.
10. What is JDBC architecture?
Java Database Connectivity (JDBC) API specifies interfaces for accessing relational databases. JDBC facilitates connecting to a database, sending queries and updates therein, and retrieving and processing the database's results for queries.
Conclusion:
The PYPL (Popularity of Programming Language Index) reported in February 2022 that Java is the second most famous language across the world. That's why a vast pool of opportunities is available for Java Architects. But Java is a very challenging yet demanding field. Going for Java Architect as a profession can be a tough but rewarding choice. Keep in mind that these questions are just some of the questions frequently asked questions. Sitting for a Java interview might be tricky. So, make sure you know the topics well by repeated revisions. And make sure to go through these Java Architect Interview Questions at least once before your interview. And then, nothing can stop you from crossing new milestones.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| Core Java Training | Feb 28 to Mar 15 | View Details |
| Core Java Training | Mar 03 to Mar 18 | View Details |
| Core Java Training | Mar 07 to Mar 22 | View Details |
| Core Java Training | Mar 10 to Mar 25 | View Details |

















