- Introduction to Amazon Elastic File System
- Amazon On-Demand Instance Pricing
- AWS Kinesis
- Amazon Redshift Tutorial
- Amazon SageMaker - AIs Next Game Changer
- AWS Console - Amazon Web Services
- AWS Architect Interview Questions
- AWS Architecture
- Amazon Athena
- Top 11 AWS Certifications List and Exam Learning Path
- How to Create Alarms in Amazon CloudWatch
- AWS CloudWatch Tutorial
- Introduction To AWS CLI
- AWS Configuration
- AWS Data Pipeline Documentation
- AWS EC2 Instance Types
- AWS Elastic Beanstalk
- AWS Elastic Beanstalk Available in AWS GovCloud (US)
- AWS Free Tier Limits and Faq
- AWS EC2 Instance Pricing
- Choosing The Right EC2 Instance Type For Your Application
- AWS Interview Questions And Answers
- AWS Key Management Service
- AWS Lambda Interview Questions
- AWS Lambda Tutorial
- What Is AWS Management Console?
- Complete AWS Marketplace User Guide
- AWS Outage
- AWS Reserved Instances
- AWS SDK
- What is AWS SNS?
- AWS Simple Queue Service
- AWS SysOps Interview Questions
- AWS vs Azure
- AWS Vs Azure Vs Google Cloud Free Tier
- Introduction to AWS Pricing
- Brief Introduction to Amazon Web Services (AWS)
- Clean Up Process in AWS
- Creating a Custom AMI in AWS
- Creating an Elastic Load Balancer in AWS
- How to Deploy Your Web Application into AWS
- How to Launch Amazon EC2 Instance Using AMI?
- How to Launch Amazon EC2 Instances Using Auto Scaling
- How to Sign Up for the AWS Service?
- How to Update Your Amazon EC2 Security Group
- Process of Installing the Command Line Tools in AWS
- Big Data in AWS
- Earning Big Money With AWS Certification
- AWS Certification Without IT Experience. Is It Possible?
- How to deploy a Java enterprise application to AWS cloud
- What is AWS Lambda?
- Top 10 Reasons To Learn AWS
- Run a Controlled Deploy With AWS Elastic Beanstalk
- Apache Spark Clusters on Amazon EC2
- Top 30 AWS Services List in 2024
- What is Amazon S3? A Complete AWS S3 Tutorial
- What is AMI in AWS
- What is AWS? Amazon Web Services Introduction
- What is AWS Elasticsearch?
- What is AWS ELB? – A Complete AWS Load Balancer Tutorial
- What is AWS Glue?
- AWS IoT Core Tutorial - What is AWS IoT?
- What is Cloud Computing - Introduction to Cloud Computing
- Why AWS Has Gained Popularity?
- Top 10 Cloud Computing Tools
- AWS Glue Tutorial
- AWS Glue Interview Questions
- AWS S3 Interview Questions
- AWS Projects and Use Cases
- AWS VPC Interview Questions and Answers
- AWS EC2 Tutorial
- AWS VPC Tutorial
- AWS EC2 Interview Questions
- AWS DynamoDB Interview Questions
- AWS API Gateway Interview Questions
- How to Become a Big Data Engineer
- What is AWS Fargate?
- What is AWS CloudFront
- AWS CloudWatch Interview Questions
- What is AWS CloudFormation?
- What is AWS Cloudformation
- Cloud Computing Interview Questions
- What is AWS Batch
- What is AWS Amplify? - AWS Amplify Alternatives
- Types of Cloud Computing - Cloud Services
- AWS DevOps Tutorial - A Complete Guide
- What is AWS SageMaker - AWS SageMaker Tutorial
- Amazon Interview Questions
- AWS DevOps Interview Questions
- Cognizant Interview Questions
- Cognizant Genc Interview Questions
- Nutanix Interview Questions
- Cloud Computing Projects and Use Cases
- test info
Amazon Web Services (AWS) cloud provides users with a secure virtual platform to deploy their applications. It offers high-level data protection when compared to an on-premises environment, at a lower cost. Among various AWS security services, Identity and Access Management (IAM) is the most widely used one. It enables secure control access to AWS resources and services for the users. Also, it helps to create and manage AWS users as well as groups and provides necessary permissions to allow or deny access to AWS resources. This article explains the working of AWS IAM, its features, and best practices.
| will be discussing the following topics: |
What is AWS IAM
AWS IAM is generally defined as Identity and Access Management, which is derived as one of the best web services that help to provide secured control access to all the AWS resources. You can use this IAM option in order to control both authorized and unauthorized resources easily.
If you want to create this identity and access management, you need to create the AWS account first. It is better to start with a single sign-in identity, which can complete all the possible access that needs to avail the AWS resources and services in the respective account. This particular identity can be named as the AWS account root user that can be easy to log in with the prospective users for all the tasks whether it is admin ones or some other ones. Instead, to combine all the best practices, it is better to create a new identity as the first IAM user. Then it can automatically secure the look away from the root user login credentials, which are used to perform all the management-related tasks.
Features of IAM at AWS
IAM at Amazon Web Services will offer you the following features
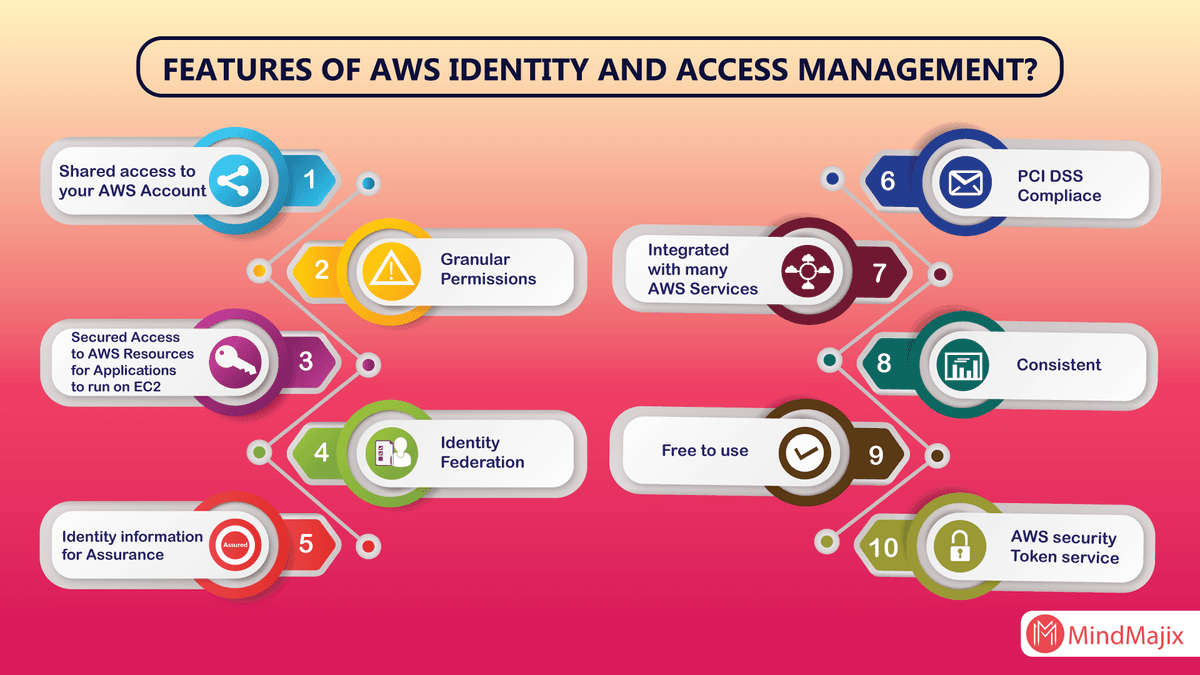
1. Shared access to your AWS account:
Without sharing your password you are eligible to access the other permission with respect to the administrator as well as the resources from your current AWS account.
| Want to become a Certified AWS Solution Architect? Go through our AWS Certification Course to get a clear understanding of AWS. |
2. Granular permissions:
By using this granular permission you are able to grant the permissions for different according to their resources. By considering an example, you can give the whole access to Amazon EC2, S3 (Amazon simple storage services) as well as to remaining AWS services. While the other users can allow getting the read-only access along with the administrator EC2 instances in order to access the process of billing information.
3. Secured access to AWS sources:
This IAM feature at AWS will be used to secure all the login credentials which can succeed on the EC2 instances. You can also offer them the permissions in order to access your application with respect to the AWS services.
4. Multi-factor authentication (MFA):
By using the MFA you can easily add the two-factor authentication not only for your account but also for the individual users for more security. Either you are your user can provide an access key or password in order to work with your account with the help of a code that is specifically configured by the device.
5. Identity Federation:
The identity federation at IAM will allow the users who already have their passwords. For example, let us consider an X corporate network or else an internet provider in order to get temporary access to your current AWS account.
6. Identity information for assurance:
Are you using the Cloud Trail option for your AWS account, then you will definitely get the log records that contain all the information that is made according to the resources in your account. All those information are generally named as the IAM identities.
Learn more about AWS from this Best AWS Training in Hyderabad to get ahead in your career!
7. PCI DSS Compliance:
The IAM at AWS will completely support all the storage, transmission, storage of data by both provider and merchant in order to validate the complaint with PCI (Payment Card Industry) DSS (Data Security Standard).
[Related Blog: What is Cloud Computing]
How does IAM work?
Before going to create the users, everyone should understand that How IAM will work. IAM offers the best infrastructure that is required to control all the authorization and authentication for your AWS account. The following are some of the elements of IAM infrastructure.
Principle:
The principle in the AWS IAM is nothing but an entity that is used to take any action on the AWS resource. The administrative IAM user is the first principle, which can allow the user for the particular services in order to assume a role. You can deniably support the federated users to allow the application to access your current AWS account. Roles, users, federated, and applications are some of the principles of AWS.
Request:
When the principal tries to use the AWS management console, the API or CLI will automatically send the request to AWS. This specific information will specify the following information.
- Actions are considered as the principles to perform.
- The actions are performed based on the resources.
- The principle information includes the environment where the request has been made previously.
Authentication:
It is one of the most commonly used principles which is used to sign in for AWS while sending the request to it. However, it also consists of alternate services like Amazon S3 which will allow requests from unknown users. In order to authenticate from the console, you need to sign in with your login credentials like username and password. But to authenticate you need to provide the secret and access key to them along with the required additional security information. It absolutely recommends the MFA enhance the security services for your account.
Authorization:
While authorizing the IAM values that are raised from the request will context to check all the matching policies and evaluate whether it is allowed or denied the respective request. All the policies are stored in IAM as JSON documents and offer the specified permission for the other resources. AWS IAM automatically checks all the policies which particularly match the context of all your requests. If the single action is denied then the IAM denies the entire request and regrets to evaluate the remaining ones, which is called an explicit deny. The following are some of the evaluation logic rules for IAM.
- All the requests are denied by default.
- The explicit can allow the overrides by default.
- An explicit may also deny the override by allowing them.
Actions:
After processing your request authorization or unauthenticated automatically AWS approves your action in the form of a request. Here all the actions are defined by services and things can be done by resources such as creating, editing, deleting, and viewing. In order to allow the principle of action, we need to include all the required actions into policy without affecting the existing resource.
Resources:
After getting the AWS approvals all the actions in your request can be done based on the related resources that contain in your account. Generally, a resource is called an entity that exists particularly within the services. These resource services can be defined as a set of activities that are performed particularly on each and every resource. If you want to create one request, first you need to perform an unrelated action that cannot be denied.
When providing the permissions by using the identity-based policy in IAM, you need to get all the permissions that are accessed to the resources of your same account, If you are looking for another account you need to raise a request based on the policy, which especially allows all the access from your account. Or else you must assume the resource-based policy within the account along with the permissions that you need.
What are AWS IAM Roles?
AWS IAM role is the same as the user in which AWS identity with certain permission policies to determine specific identity that can or cannot be done with AWS. One can also use similar roles to delegate certain access to the users, applications, or else services to have access to AWS resources.
The roles of AWS IAM are given below in a detailed manner like
- Increasing security and taking help for protection of certain AWS resources and also the configuration of Multi-Factor authentication can be done.
- The Best Practice of IAM users is that to enable MFA on Root accounts and privileged users
- Multi-Factor Authentication can be config with ease
Security Token Based
IAM Users or else AWS Root Users are mostly assigned to hardware or else virtual MFA devices
Based upon the synchronization of One Time Password algorithms, it can easily generate six-digit numeric code which is required at the time of the authentication process
SMS Text Message-Based (Preview Mode)
- By using the phone number of users, IAM users can easily config with SMS-compatible mobile devices that will receive a 6 digit code from AWS technology.
- Only for IAM Users, SMS Based MFA is always available and it mostly does not work for AWS root account
- As Root users and IAM users are separate entities, MFA needs to be enabled in the respective formats. Particularly, enabling MFA on root does not mostly enable it for all other users.
- The MFA device will get activated with only one IAM user or else AWS account respectively
- Suppose the MFA device suddenly stops working or else is lost, then there is no authentication to log in to AWS console and need to reach out to AWS support for deactivation of MFA
- The protection of MFA is easily enabled for respective service API calls by using Condition Bool which gives support to temporary security credentials.
What is AWS IAM CLI?
One can only use the AWS IAM Command Line Interface by using the respective role to get signed in as the IAM users. It is given as the externally authenticated user which takes the role already or else when you certainly go through the Amazon EC2 instances types which are attached to the role of instance profile. This particular role is specified with a certain set of permissions where you can simply access AWS resources. It is mostly similar to the user of AWS Identity and Access Management (IAM). There will be a set of permissions or else instructions to get the sign-in with certain accounts.
Mostly, this section is to describe some of the common tasks which are related to AWS Identity and Access Management (IAM) and the performing of basic instructions by using AWS Command Line Interface.
AWS IAM Policy Generator
AWS IAM Policy Generator is considered as the tool which helps or enables to the creation of various policies to control access to Amazon Web Services products and various resources. There are three basic steps where every user has to follow to get authenticated in an enormous way.
- Firstly, one has to select a certain Policy Type
- Then Add the respective statements
- And Generate Policy as per the requirement
This is the policy container for certain permissions where you can select anyone from respective policies such as IAM Policy, S3 bucket policy, and SNS topic policy, SQS queue policy, VPC endpoint policy, etc. Then adding statements is the respective policy to have a formal description for single access permission. The Final one, Generate Policy is the document that acts as the container for one or else massive statements
AWS IAM Best Practices
AWS IAM Best Practices helps to perform certain relative audits and removes all the unused users and credentials. This is to secure the AWS resources for certain AWS identities and Access Management Service (IAM).
- To Lock Away the AWS Account Root User Access Keys
- Creation of Individual IAM Users
- Use AWS Defined Policies for assigning the Permissions if required
- Usage of certain groups to assign permissions to IAM users
- Grant Least Privilege
- Usage of Access Levels to Review IAM Permissions
- The configuration of Strong Password Policy for Users
AWS IAM FAQ's
There are many of the AWS IAM FAq’s that help know in detail every concept with easy methods and real-time scenarios.
- What is AWS Identity and Access Management (IAM)?
- How do I get started with IAM?
- What problems does IAM solve?
- How do users call AWS services?
List Of AWS Courses Offered By Mindmajix:
| AWS Certified SysOps Administrator | AWS Certified Solutions Architect / Professional |
| AWS Technical Essentials | AWS Database Migration Service |
| AWS Lambda 2016 | and many more |
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| AWS Training | Mar 07 to Mar 22 | View Details |
| AWS Training | Mar 10 to Mar 25 | View Details |
| AWS Training | Mar 14 to Mar 29 | View Details |
| AWS Training | Mar 17 to Apr 01 | View Details |

Prasanthi is an expert writer in MongoDB, and has written for various reputable online and print publications. At present, she is working for MindMajix, and writes content not only on MongoDB, but also on Sharepoint, Uipath, and AWS.
















