- 6 Hot And In-Demand Tech Areas In 2024
- How To Forward Your Career With Cloud Skills?
- Top 7 On-Demand IT Certifications
- Most In-demand Technologies To Upskill Your Career
- Top 10 Hottest Tech Skills to Master in 2024
- Top Skills You Need to Become a Data Scientist
- Groovy Interview Questions
- Facets Interview Questions
- Crystal Reports Tutorial
- VAPT Interview Questions
- Flutter Tutorial
- Saviynt VS Sailpoint
- Flutter vs Xamarin
- PingFederate Interview Questions and Answers
- Dart vs Javascript : What's the Difference?
- Terraform Private Registry
- Cylance Interview Questions and Answers
- Sophos Interview Questions and Answers
- Top Camunda Interview Questions
- NUnit Interview Questions and Answers
- Impala Interview Questions and Answers
- ETL Tutorial
- Ionic Interview Questions
- Grafana Tutorial
- SnapLogic Interview Questions
- Saviynt Interview Questions
- What is PingFederate? - A Complete Beginners Tutorial
- SnapLogic Tutorial
- Grafana Interview Questions
- RHCE Interview Questions and Answers
- Web Services Interview Questions
- Domo Interview Questions and Answers
- Terraform Interview Questions
- What is Sophos? | Sophos Turorial for Beginners
- Top Servlet Interview Question And Answers
- NLP Interview Questions and Answers
- Microsoft Intune Interview Questions
- Top XML Interview Questions And Answers
- Tosca Commander
- Katalon vs Cypress
- SQLite Tutorial
- Tosca Tutorial - A Complete Guide for Beginners
- Xamarin Interview Questions and Answers
- UiPath vs Automation Anywhere - The Key Differences
- OpenShift Interview Questions
- What is Katalon Studio - Complete Tutorial Guide
- Kronos Interview Questions
- Tosca Framework
- Burp Suite Tutorial
- Mendix Interview Questions
- Power Platform Interview Questions
- Burp Suite Interview Questions
- What is Mendix
- What is Terraform ?
- Burp Suite Alternatives
- Dart vs Kotlin
- What is Kronos?
- ES6 Interview Questions
- Entity Framework Interview Questions
- COBOL Interview Questions
- Express JS Interview Questions
- OSPF Interview Questions
- LINQ Tutorial
- CSS3 Interview Questions and Answers
- Auth0 Tutorial
- MS Access Interview Questions
- What is SPARQL - A Complete Tutorial Guide
- ExpressJS Tutorial
- UML Tutorial
- HTML vs XML
- Cypress vs Jest
- Impacts of Social Media
- OWASP Interview Questions
- Security Testing Interview Questions
- OpenShift vs Docker
- ES6 Tutorial
- Spark SQL Interview Questions
- Spark SQL Tutorial
- What is OWASP?
- AppDynamics Interview Questions
- Dynatrace Interview Questions
- Rest Assured Tutorial
- New Relic Interview Questions
- REST API Tutorial
- Datadog Interview Questions
- Rest API Interview Questions
- Rest Assured Interview Questions
- PTC Windchill Interview Questions
- Easiest Tech Skills To Learn
- Python SQLite Tutorial - How to Install SQLite
- Datadog Tutorial - Datadog Incident Management
- What is AppDynamics - AppDynamics Architecture
- RabbitMQ Interview Questions And Answers
- What is Dynatrace
- Datadog Vs Splunk
- Web Developer Job Description
- JP Morgan Interview Questions
- Types of Corporate Training
- Benefits of Corporate Training
- What is Corporate Restructuring?
- Blended Learning in Corporate Training
- What is Corporate Level Strategy?
- Flutter Projects and Use Cases
- How to Become a Web Developer
- How To Install Keras?
- How to Install Flutter on Windows?
- How to Install Cypress on Windows?
- How to Become a Computer Scientist?
- How to Install Katalon Studio in Windows
- How to Become a Programmer
- OWASP Projects and Use Cases
- How to Install Sophos?
- Workato Tutorial
- Workato Tutorial - What is Workato?
Vulnerability Assessment and Penetration Testing (VAPT) is a wide term that refers to a variety of security assessment services aimed at identifying and mitigating cyber security risks throughout an organization's IT infrastructure.
It's critical to understand the many types of VAPT services and the variations between them in order to pick the correct form of evaluation for your company's needs. Because VAPT assessments are so varied in terms of depth, breadth, scope, and price, this knowledge is essential for ensuring that tests provide the best value for money.
What is a Vulnerability Assessment and Penetration Testing?
-
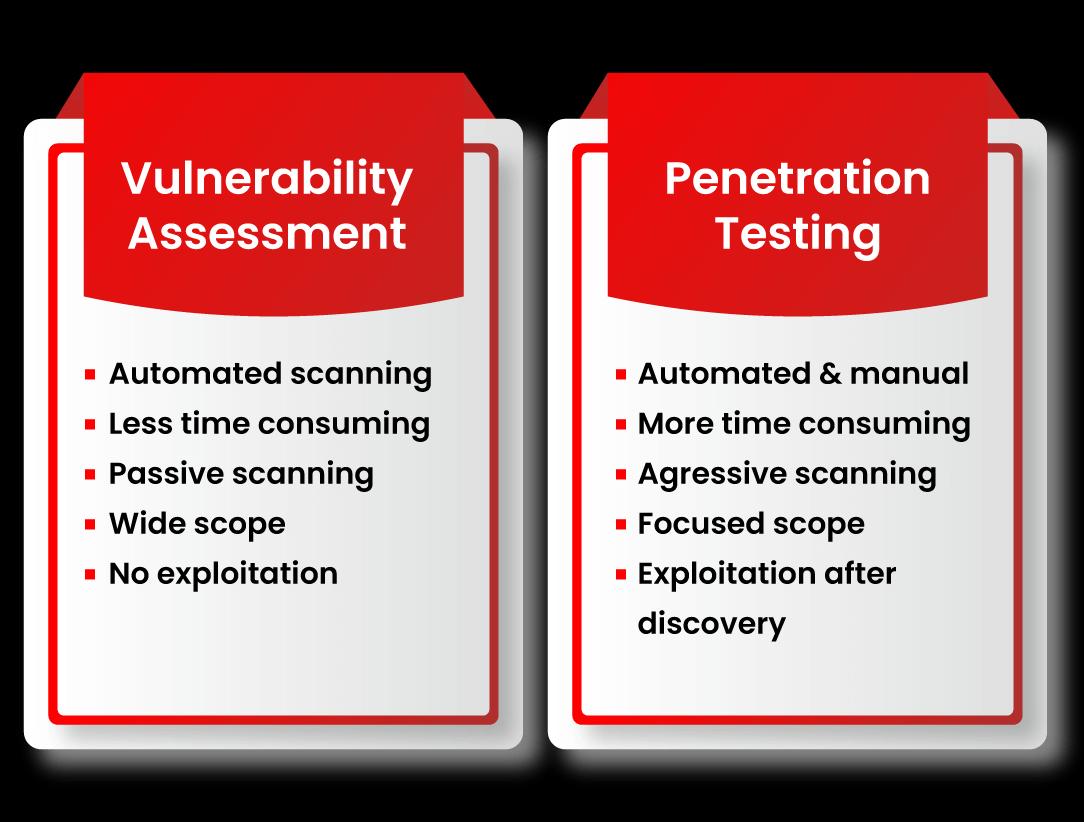
Vulnerability Assessment
Although Vulnerability Assessment (VA) and Penetration Testing (PT) are methods for detecting flaws in systems, networks, or online applications, there are some distinctions. A Vulnerability Assessment (VA) examines, discovers, and discloses known vulnerabilities first. It generates a report that details the vulnerability's categorization and priority.
| If you want to enrich your career and become a professional in VAPT, then enroll in "VAPT Training".This course will help you to achieve excellence in this domain |
-
Penetration Testing
On the other side, a Penetration Test (PT) seeks to exploit vulnerabilities to identify the level of entrance. It assesses the level of defense. The VA is similar to approaching a door, assessing it, and examining its potential flaws. The VA is usually automated, but a PT is generally done by a security expert.
What is VAPT?
Vulnerability Assessment and Penetration Testing is a sort of security testing that examines an application, network, endpoint, or cloud for flaws. Vulnerability Assessment and Penetration Testing have distinct advantages, and they're typically used together to generate a comprehensive analysis.
What is the purpose of VAPT?
Because hackers' tools, strategies, and processes for breaching networks are constantly improving, it's critical to assess the organization's cyber security frequently.
VAPT assists in the security of your organization by offering insight into security flaws as well as advice on how to remedy them. For organizations wishing to comply with standards such as the GDPR, ISO 27001, and PCI DSS, VAPT is becoming increasingly crucial.
What are the deliverables from a VAPT?
Execution of Vulnerability Assessment and Penetration Testing for specified network devices, security devices, servers, apps, websites, and other systems as per the scope outlined in the Approach, as well as analysis and suggestions on how to resolve the issues.
The following are the deliverables for VAPT activity
- Verification of the critical vulnerability's closure.
- Verify that the findings have been closed in accordance with the findings.
- First, a draught VAPT report, then a final report.
- Verification of compliance. (Optional)
The following should be included in the VAPT Report
- Identifying the Auditee (Address & contact information)
- VAPT Schedule and Locations.
- Terms and conditions.
- Testing was confirmed in accordance with International Best Practices and OWASP Web/Mobile Application Security Guidelines.
- Vulnerabilities and problems of concern are examined.
- Recommendations for resolving the problem.
- Personnel who took part in the audit.
| Related Article: VAPT Interview Questions |
What are the benefits of performing VAPT?
- It will provide you with a thorough assessment of your application.
- It will assist you in identifying security flaws or faults that might lead to catastrophic cyber-attacks.
- VAPT provides a more complete picture of the dangers posed to your network or application.
- It assists businesses in defending their data and systems from harmful assaults.
- Compliance standards necessitate the use of VAPT.
- Defends your company against data loss and unwanted access.
- It will assist you in safeguarding your data from both external and internal dangers.
How to Evaluate Vulnerability?
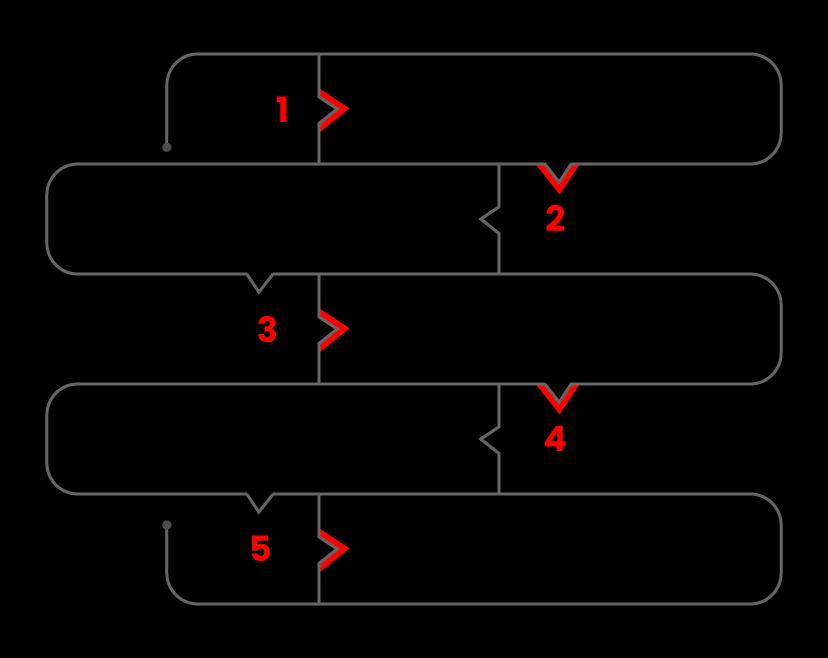
The following is a step-by-step guide to doing a vulnerability assessment

Step1: Set up
- Begin the documentation process.
- Secure permissions.
Step 2: Tool Setup
- Execution of the Test:
- Execute the tools
Run the data packet you just saved (A packet is a data unit routed between an origin and a destination.) When a file is transferred across the internet, such as an e-mail message, an HTML file, or a Uniform Resource Locator(URL) request, the TCP layer of TCP/IP breaks it into many "chunks" for efficient routing, each of which is uniquely numbered and includes the destination's Internet address. These portions are referred to as packets. While the assessment tools are running, the TCP layer at the receiving end will reassemble the packets into the original file once they have arrived.
Step 3: Vulnerability Analysis
- Identifying and categorizing network and system resources. Prioritize the resources (for example, High, Medium, Low)
- Identifying the dangers that each resource may face.
- Creating a strategy for dealing with the most pressing issues first.
- Defining and implementing strategies to reduce the impact of an assault.
Step 4: Reporting
Step 5: Remediation
- The procedure for repairing the flaws.
- Every vulnerability was tested.
What is a VAPT Tool, exactly?
A VAPT tool performs a VA to detect vulnerabilities and a PT to acquire access by exploiting such flaws. A VA, for example, could assist in detecting poor encryption, but the PA will try to decode it. The VAPT tools scan for vulnerabilities, create a PA report, and, in certain circumstances, run code or payloads. VAPT products assist with PCI-DSS, GDPR, and ISO27001 compliance.
Top VAPT tools
1. Netsparker Security Scanner
A robust vulnerability scanning and management tool designed specifically for businesses. It can detect and exploit flaws like SQL injection and XSS. Netsparker can scan any online application, independent of the platform or programming language used to create it. Netsparker is the only online web application security scanner that exploits discovered vulnerabilities in a read-only and secure manner to validate concerns.
It also provides evidence of the vulnerability, so you don't have to waste time manually validating it.
2. Acunetix Scanner
A web app vulnerability scanner aimed at small and medium-sized businesses, but with the possibility to expand to more prominent organizations. It can detect SQL injection, XSS, and other threats. The Acunetix Web Vulnerability Scanner is an automated web application security testing tool that analyses your web applications for vulnerabilities such as SQL Injection, Cross-Site Scripting, and other exploitable flaws.
3. Intruder
It is a web vulnerability assessment tool that detects a wide range of threats using an automated online web vulnerability testing tool. Intruders are attackers who seek to compromise the security of a network. They attack the network in order to get unauthorized access.
4. Metasploit
A solid framework with ready-to-use exploits code. The Metasploit project helps it by providing information on many vulnerabilities and associated exploits. With Metasploit, the pen testing team can use ready-made or custom code and introduce it into a network to probe for weak spots. As another flavor of threat hunting, after defects are located and recorded, the knowledge may be utilized to address systemic weaknesses and prioritize remedies.
Notable Mentions Nexpose, OpenVAS, Nmap, Wireshark, BeEF, and John the Ripper are more tools that can aid in the VAPT process.
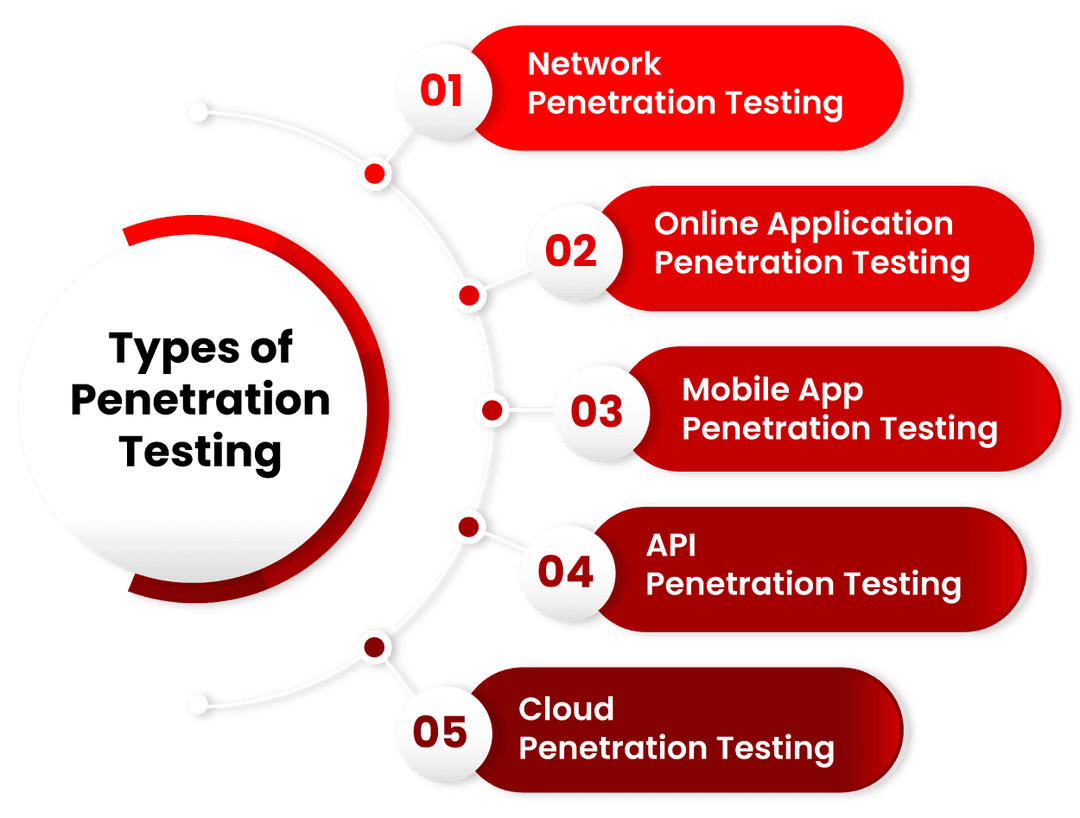
What are the five significant types of penetration testing?
An organization's cyber security relies on a secure and reliable infrastructure. Given the financial penalties of a data breach, frequent internal and external penetration testing to discover and remedy vulnerabilities is recommended.
A network penetration test is a sort of security assessment carried out by an ethical hacking firm to detect cyber security flaws that might be exploited to infiltrate on-premises and cloud systems. Pen testing on a network might entail evaluating perimeter security policies and equipment like routers and switches.
An internal network pen test is used to determine what an attacker could do with initial network access. Insider threats, such as personnel acting maliciously, whether purposefully or accidentally, can be mirrored by an internal network pen test.
An external network pen test is used to evaluate the efficiency of perimeter security policies in preventing and detecting attacks, as well as to find flaws in internet-facing assets like web, mail, and FTP servers.
This testing entails a set of processes aimed at acquiring information about the target system, identifying flaws or vulnerabilities, and researching exploits that will attack such flaws or vulnerabilities and breach the web application.
Because certain online apps include sensitive data, it's critical to maintain them safe at all times, especially because many of them are publicly accessible.
The best and most cost-effective technique for combating web application vulnerabilities is web application penetration testing is part of the SDLC process (Software Development Life Cycle).
This testing identifies flaws in a mobile application's cyber security posture. The safety and security of iOS and Android applications are the ones that get the most assessed.
Penetration testing for mobile applications helps protect apps and reduces the chance of fraud, virus or malware infections, data leaks, and other security breaches.
APIs have ushered in a new digital transformation era in the cloud, IoT, and mobile and web apps. Every day, the average individual interacts with many APIs without even realizing it, especially on mobile. APIs are the connective tissue that allows data to flow from one system to another, both internally and externally. All too frequently, however, deployed APIs are not subjected to thorough security testing, if they are checked at all. A poorly protected API, whether SOAP or REST, can expose security holes in everything it is linked to. The API's security is equally crucial as the applications for which it delivers services.
An authorized simulated cyber-attack against a system housed on a Cloud provider, such as Amazon's AWS or Microsoft's Azure, is known as Cloud Penetration Testing. A cloud penetration test's primary purpose is to identify a system's flaws and strengths so that its security posture may be appropriately appraised.
How often one should conduct VAPT?
The frequency of VAPT is determined by the sort of pen testing services provided by the company. This is why organizations fall short of their goals. They do these tests on a modest basis, once or twice a year or every few months.
Compliance standards and certifications of VAPT
Two forms of vulnerability testing are Vulnerability Assessment and Penetration Testing (VAPT)... Penetration tests try to exploit system defects in order to discover whether unauthorized access or other malicious conduct is feasible, as well as to assess whether faults constitute a threat to the application.
VAPT Certification is a technological way to address security flaws in an organization's IT infrastructure (application, software system, network, etc.). Vulnerability Assessment is a method of finding vulnerabilities to not miss any loopholes.
Conclusion
VAPT testing has the potential to be a highly useful tool for businesses. It raises the security level to protect them from cyber-attacks and criminal activity. As a result, most organizations are taking it quite seriously to achieve worthwhile security benefits.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| VAPT Training | Feb 17 to Mar 04 | View Details |
| VAPT Training | Feb 21 to Mar 08 | View Details |
| VAPT Training | Feb 24 to Mar 11 | View Details |
| VAPT Training | Feb 28 to Mar 15 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .
















