- 6 Hot And In-Demand Tech Areas In 2024
- How To Forward Your Career With Cloud Skills?
- Top 7 On-Demand IT Certifications
- Most In-demand Technologies To Upskill Your Career
- Top 10 Hottest Tech Skills to Master in 2024
- Top Skills You Need to Become a Data Scientist
- Groovy Interview Questions
- Facets Interview Questions
- Crystal Reports Tutorial
- VAPT Interview Questions
- Flutter Tutorial
- Saviynt VS Sailpoint
- Flutter vs Xamarin
- PingFederate Interview Questions and Answers
- Dart vs Javascript : What's the Difference?
- Terraform Private Registry
- Cylance Interview Questions and Answers
- Sophos Interview Questions and Answers
- Top Camunda Interview Questions
- NUnit Interview Questions and Answers
- Impala Interview Questions and Answers
- ETL Tutorial
- Ionic Interview Questions
- Grafana Tutorial
- What is VAPT? - A Complete Beginners Tutorial
- SnapLogic Interview Questions
- Saviynt Interview Questions
- What is PingFederate? - A Complete Beginners Tutorial
- SnapLogic Tutorial
- Grafana Interview Questions
- RHCE Interview Questions and Answers
- Web Services Interview Questions
- Domo Interview Questions and Answers
- Terraform Interview Questions
- What is Sophos? | Sophos Turorial for Beginners
- Top Servlet Interview Question And Answers
- NLP Interview Questions and Answers
- Microsoft Intune Interview Questions
- Top XML Interview Questions And Answers
- Tosca Commander
- Katalon vs Cypress
- SQLite Tutorial
- Tosca Tutorial - A Complete Guide for Beginners
- Xamarin Interview Questions and Answers
- UiPath vs Automation Anywhere - The Key Differences
- OpenShift Interview Questions
- What is Katalon Studio - Complete Tutorial Guide
- Kronos Interview Questions
- Tosca Framework
- Burp Suite Tutorial
- Mendix Interview Questions
- Power Platform Interview Questions
- Burp Suite Interview Questions
- What is Mendix
- What is Terraform ?
- Burp Suite Alternatives
- Dart vs Kotlin
- What is Kronos?
- ES6 Interview Questions
- Entity Framework Interview Questions
- COBOL Interview Questions
- Express JS Interview Questions
- OSPF Interview Questions
- LINQ Tutorial
- CSS3 Interview Questions and Answers
- MS Access Interview Questions
- What is SPARQL - A Complete Tutorial Guide
- ExpressJS Tutorial
- UML Tutorial
- HTML vs XML
- Cypress vs Jest
- Impacts of Social Media
- OWASP Interview Questions
- Security Testing Interview Questions
- OpenShift vs Docker
- ES6 Tutorial
- Spark SQL Interview Questions
- Spark SQL Tutorial
- What is OWASP?
- AppDynamics Interview Questions
- Dynatrace Interview Questions
- Rest Assured Tutorial
- New Relic Interview Questions
- REST API Tutorial
- Datadog Interview Questions
- Rest API Interview Questions
- Rest Assured Interview Questions
- PTC Windchill Interview Questions
- Easiest Tech Skills To Learn
- Python SQLite Tutorial - How to Install SQLite
- Datadog Tutorial - Datadog Incident Management
- What is AppDynamics - AppDynamics Architecture
- RabbitMQ Interview Questions And Answers
- What is Dynatrace
- Datadog Vs Splunk
- Web Developer Job Description
- JP Morgan Interview Questions
- Types of Corporate Training
- Benefits of Corporate Training
- What is Corporate Restructuring?
- Blended Learning in Corporate Training
- What is Corporate Level Strategy?
- Flutter Projects and Use Cases
- How to Become a Web Developer
- How To Install Keras?
- How to Install Flutter on Windows?
- How to Install Cypress on Windows?
- How to Become a Computer Scientist?
- How to Install Katalon Studio in Windows
- How to Become a Programmer
- OWASP Projects and Use Cases
- How to Install Sophos?
- Workato Tutorial
- Workato Tutorial - What is Workato?
Generally, organisations allow users to access their applications and resources only after they make the login process to ensure user identification. But, you cannot simply move considering user identity as a mere login process – yes, it is beyond that. Organisations must be vigilant of all the user activities they make in applications and resources - round-the-clock. A slight compromise on security would significantly affect organisations’ reputations and bottom line. Hence, a need arises for corporates to ensure the security of resources through robust identity management solutions.
This way, Auth0 is one identity management platform that offers robust security solutions for user authentication and authorisation for accessing resources. In this tutorial, we will have an overall coverage of Auth0 features, solutions offered, how to configure android apps for secured login, benefits of auth0, and more in greater detail.
Auth0 Tutorial - Topics of Content:
- What is Auth0?
- Why Auth0?
- What are the features of the Auth0 platform?
- What are the solutions offered with Auth0?
- How to get started with Auth0?
- How to authenticate users with Auth0?
- How to manage users with Auth0?
- How to secure applications with Auth0?
- How to deploy and monitor Auth0?
- How to troubleshoot with Auth0?
- Benefits of Auth0
What is Auth0?
Auth0 is a popular identity authentication and authorisation platform which supports secure access to organisational resources. In simple terms, it is a developer-friendly tool that provides secured access control. By incorporating Auth0, you can only allow developers, employees, and customers to access your applications and resources. Auth0 uses OAuth 2.0 and OpenID Connect Protocol (OIDC) authorisation framework for making secured connections. Thus, you can safeguard your applications and resources from unauthorised entries and attacks with Auth0.
Why Auth0?
No worries if you are eager to know why Auth0 is preferred over protecting applications. Get the reasons below:
Auth0 offers easy-to-use and adaptable authentication processes. In other words, it simplifies signing-on and authentication processes to the convenience of customers. Mainly, it provides high security and reasonable control over organisational resources. As mentioned earlier, Auth0 is a developer-friendly tool because of its low code or no code features. Besides, Auth0 was named a Leader in Gartner Magic Quadrant for Access Management in 2021.
What are the features of the Auth0 Platform?
When it comes to Auth0, it offers fantastic features to secure applications. Let us look over them below in detail.
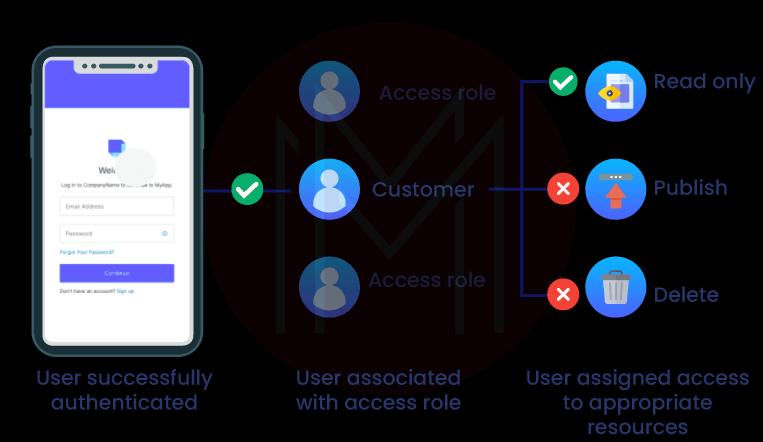
Access Management: Auth0 executes a dynamic access control system by defining access roles for all users. This process will ensure secured access to applications and resources.
Access management has the following methods to ensure security.
- Universal Login: Because of this feature, users must only make a login process once. It allows users to make continuous navigation through all the applications and resources seamlessly.
- Frictionless Login: Users can have frictionless access to all the resources they are allowed to.
- API Authorisation: Auth0 effectively carries out API authentication for the first party, third party, and non-interactive client applications.
- Role-Based Access Control (RBAC): With Auth0, users can only access resources based on their roles.
Extensibility: Auth0 offers stand-alone serverless developer tools to achieve extensibility and customise Auth0 per individual needs.
Following are the methods used to achieve extensibility with Auth0.
- Auth0 Marketplace: You can identify all the third-party identity management solutions in one place.
- Actions: Auth0 offers various easy-to-use tools for developers, such as drag and drop flow editor, VS code editor, version control, IntelliSense code completion, drafting, and advanced testing and debugging capabilities. These tools help simplify developers' tasks and significantly reduce their developing time.
Let's now know the use of the different developer tools below:
With the Drag and drop option, you can customise identity flows in the flow editor to optimise the authentication process. This feature helps to avoid rewriting codes and reconfiguring functions.
With the IntelliSense code completion, you can simply write Java functions. Not only limited to this, but Auth0 also supports minimising developing time with real-time syntax checking and allowing auto-completion of commands and functions.
Auth0 allows you to draft, verify, and test codes efficiently with a single user interface. Also, you can save the changes you have made to the codes without committing to production. Besides, Auth0 simplifies testing and debugging processes by tracking state changes literally.
Security:
- Attack Protection: Auth0 protects applications from Bot attacks and detects anomalies in the access by tracking the suspicious activities. In this regard, the central authorisation server helps to prevent these attacks. With threat intelligence capability, Auth0 prevents automated attacks through bots. On the same lines, brute force detection helps identify if multiple attempts are made to access a single account.
- Adaptive Multifactor Authentication (MFA): Whenever Auth0 identifies suspicious activities in accessing applications, it enables adaptive MFA. According to MFA, it requires additional authentication to allow users to access applications. This setup makes sure a frictionless login experience for users. It means that all other times users can be allowed to access applications with a single signing on.
- Step-up Authentication: Auth0 allows users to access sensitive and restricted resources with additional authentication.
User Management:
- User Migration: With all the multiple options provided, the migration process is made simpler in Auth0.
- User Connections: Users can easily create accounts and sign on using the credentials of social media platforms such as Facebook or LinkedIn. On similar tracks, enterprises can easily connect with Auth0 with their identity providers. Moreover, the easy-to-use management interface helps to gain deeper insights about customers.
- Scalable User Directory: No matter what would be the size of users – Be it hundreds or millions – Auth0 can manage any number of users seamlessly with its scalable user directories.
Authentication:
- Single Sign-on (SSO): With this option, users must sign on only once, which is enough to access all the resources they are allowed to do. So, it is clear that Auth0 simplifies the access management for customers, employees, and enterprises with SSO.
- Password less: No doubt that using the same password in many applications is indeed vulnerable. To overcome this setback, Auth0 provides a WebAuthn-based passwordless authentication process, which is unphishable and comes with good safety features. Know that WebAuthn is a phishing-resistant tool. With this tool, you don’t need to use passwords whenever you sign on. Instead of that, you can use emails, SMS, etc.
- Identities: It is true that users may have different online identities for social media, legal, or enterprise. Auth0 supports integrating and managing them all without friction.
Machine-to-Machine:
Auth0 easily handles non-interactive applications like IoT devices and allows them to access APIs securely.
Breached Passwords:
Auth0 notifies users whenever third parties breach their credentials. It blocks the credentials until users create new passwords.
| Related Article: OKTA vs Auth0 |
What are the Solutions offered with Auth0?
From SSO to Step-up authentication, Auth0 offers numerous business solutions for many businesses such as finance, public sector, retail, healthcare, and B2B SaaS services. As a result, Auth0 optimises the security of applications and resources, access to B2B services, reduces frictions in signing on, protects high-risk transactions, and so on.
Let us now look at what solutions can be provided by Auth0 in various businesses.
Financial Services: Auth0 uses battle-tested industry standards such as OpenID Connect, SAML, LDAP, OAuth, and JSON web tokens for identity authentication and authorisation. By complying with these standards, Auth0 ensures access control to applications. Moreover, Auth0 conducts due diligence checks to ensure customers' identities.
Healthcare: Auth0 offers easy-to-use access controls, which help provide quality patient care. Mainly, Auth0 support satisfies HIPAA compliances for organisations with PHI data. Note that PHI is the Protected/Personal Health Data.
Retail: Customers can manage their profiles in retail portals without compromising data security. On the other side, companies can gain business growth and increase the bottom line because of the frictionless access provided by Auth0.
B2B SaaS: Auth0 is highly scalable and capable of managing as many users as possible. This kind of scaling can be realised with the support of Active Directory, LDAP, Ping Federate, and custom SAML-P Providers. What’s more! Enterprises can store their data in Active Directory or custom databases securely.
Public Sector: What if attackers access confidential government resources? No doubt that it would result in serious negative consequences. Auth0 allows only authenticated citizens to access government services, ensuring the right people access the right data. This way, government services can share data among themselves securely with the support of Auth0.
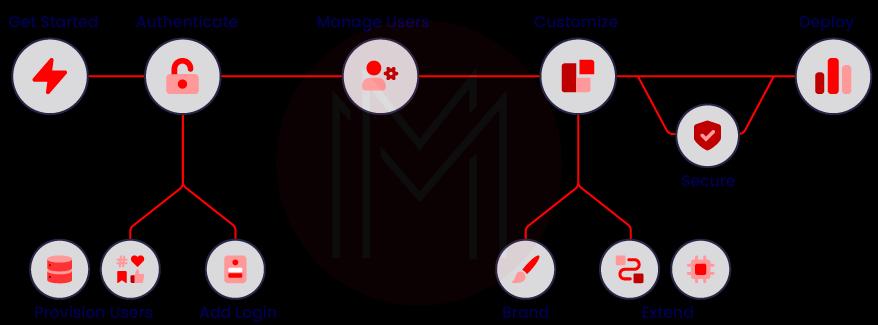
What are the different stages involved in the implementation of Auth0?
Implementation of the Auth0 platform involves the following stages:
- Get Started
- Authentication
- Managing users
- Customisation
- Securing
- Deployment and Monitoring
- Troubleshooting
The following sections will elaborate on the processes performed in each stage mentioned above.
How to Get Started with Auth0?
Configuring Auth0: In this stage, how will Auth0 work with applications and APIs is configured. Also, who can control the Auth0 dashboard and the behaviour of Auth0 tenants is configured.
Plan and Design: Auth0 employs different flows to authenticate and authorise users. The following are the different types of flows used in Auth0:
- Authorisation code flow
- Implicit flow with form post
- Hybrid flow
- Client credentials flow
- Device authorisation flow
- Resource owner password flow
Also, Auth0 supports different types of application architecture scenarios. They can be listed as follows:
- Multiple Organisations
- SSO for Webapps
- Server Application + API
- Single Page Application + API
- Mobile Application + API
How to authenticate users with Auth0?
Add login: This stage deals with using universal login to access applications and resources better. It includes Single Sign On (SSO) and Passwordless login. In the SSO method, a user must sign on only once, which is enough to access all applications. And passwordless is another login method that allows users to access applications using OTPs received through their email addresses or phone numbers.
Provision Users: Auth0 allows using Facebook and Salesforce credentials for authentication. In this regard, database connections are used to store users' credentials. Note that the databases may be Auth0-provided stores or users’ own databases.
How to manage users with Auth0?
Manage Users: This stage includes importing, grouping, and managing user data and controlling their access to applications. Simply put, you can easily migrate, arrange, and administer user accounts and data. Here, the users' data is imported from many data sources such as identity providers, own databases, and enterprise connections and stored in Auth0’s cloud database store. Then, migration is performed through custom database connections, Auth0 management API, and user import/export extensions.
Manage Access: Auth0 controls users' access and interaction with applications very closely. Based on this, Auth0 aggregates users’ interactions in terms of page views, e-commerce transactions, social interactions, events, and so on.
How to customise the Auth0?
Brand Customisation: Auth0 allows customising the universal login pages and uses version control to manage source code. Also, you can customise emails and modify the flow of emails. Further, Auth0 allows customising error messages displayed by lock v11.
Code Customisation: With the secure, tenant-specific, and versioned functions, you can customise Auth0 capabilities for better efficiency. Also, you can maintain legacy rules of applications used in the authentication pipeline.
Third-party Customisation: You can use Auth0 extensions to install apps and run commands, thereby extending the capabilities of the Auth0 platform. Similarly, Auth0-reviewed integrations are used to reduce implementation time. Furthermore, you can monitor the events such as changed passwords and new registrations whenever they are made.
How to secure applications with Auth0?
Protecting applications: Auth0 ensures the right people access the right resources. It can detect malicious attacks and prevents them immediately before they cause any severe harm to applications. When there are repeated login failures, or a single IP address attempting to access multiple user accounts, Auth0 enables step-up authentication. Therefore, users must go through additional identity checks before accessing applications.
Compliance: Auth0 supports compliance with essential requirements such as GDPR and HIPAA.
How to deploy and monitor Auth0?
Deployment: This stage includes planning, verifying, and implementing Auth0 deployment. Before deployment, the evaluation must be made to decide whether to deploy Auth0 in the public or private clouds. And Run Checks are performed to ensure applications are ready for production. Know that Auth0 supports continuous integration and deployment using the deploy CLI tool.
Monitoring: You can monitor Auth0 implementation along with its status and services. Say, for instance, you can monitor event logs for making business analyses and gaining insights.
How to troubleshoot with Auth0?
Get Support: From support plan to changelog, Auth0 offers various kinds of support for developers and the user community. In simpler terms, Auth0 offers multiple tiers of support to users and developers to solve their challenges quickly while working with Auth0. It includes defect resolution, how to open and manage Auth0 support tickets, how to report a security issue, and so on.
Troubleshoot: The challenges faced by developers and users may be commonplace, along with authentication, integration and extensibility issues. To solve these issues, Auth0 uses various tools such as generating and analysing HAR files, inspecting tokens and debugging.
How to add login in an Android App with Auth0?
Step 1: Configuring Auth0:
- Configuring Application: Create a new Auth0 application using the interactive selector or selecting from the existing application. Note that all the applications in Auth0 are assigned with a unique client ID.
- Configure callback URLs: Once the authentication process is over, Auth0 will direct users to this callback application URL.
- Configure logout URLs: Once users log out from the application, Auth0 will redirect users to this logout application URL.
Step 2: Installing the Auth0 Android SDK:
You can add Auth0 Android SDK to your project. This is the library that is used to make requests to the Auth0's authentication and management APIs. You need to add the following build.gradle dependencies in the application.
You can find the build.gradle dependencies section in the following codes used for configuration:
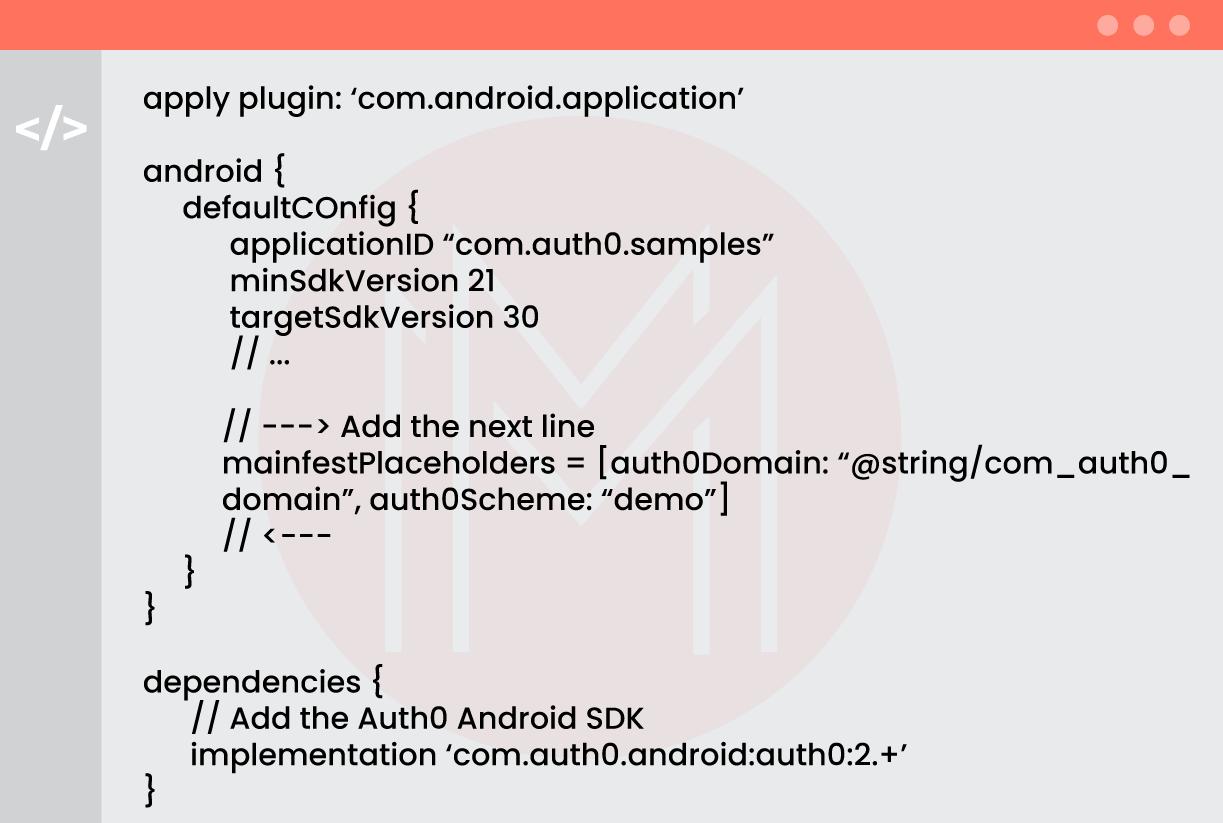
Step 3: Adding Manifest Placeholders:
With manifest placeholders, Auth0 defines an intent-filter internally. It helps to capture the authentication callback URL. Know that you need to set the callback URL Scheme and Auth0 tenant domain in this regard.
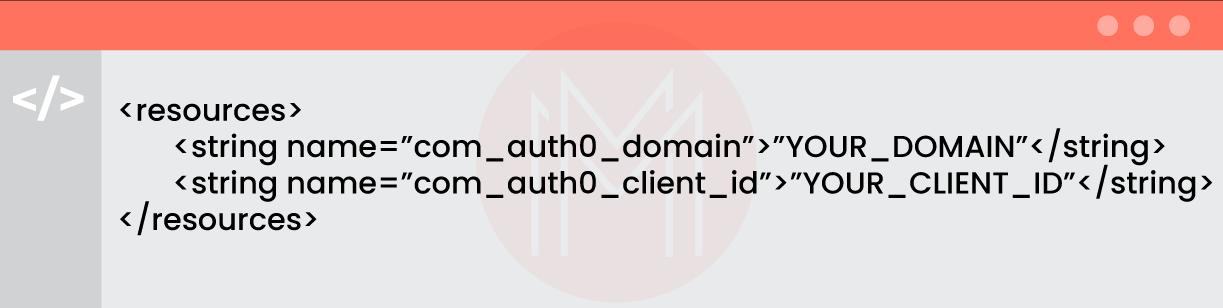
Step 4: Configuring the Application:
To ensure SDK works properly, we need to set the following properties in strings.xml:
- com_auth0_domain: This is the domain of the Auth0 tenant, which can be found under the application’s settings in the domain field.
- com_auth0_client_id: This is the ID of the Auth0 application that we set earlier. It can be found under the application’s settings client ID field.
The strings.xml coding section is given as follows:
Make sure that the Andriodmanifest.xml file specifies the android.permissions.INTERNET permission as follows:
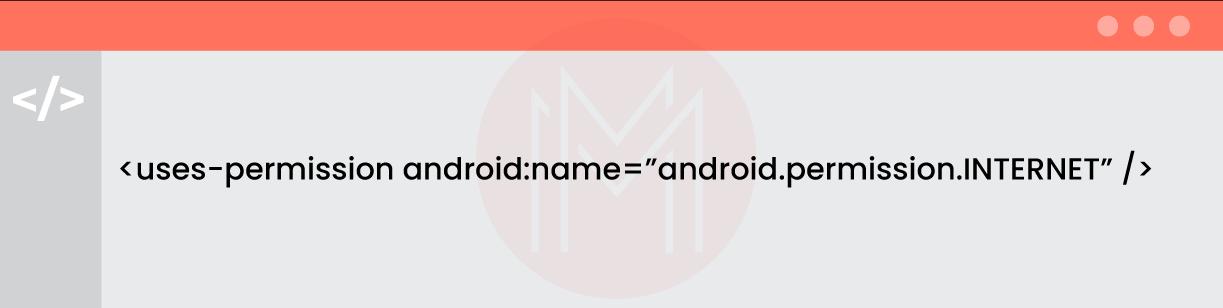
Then, you can run the Sync Project with Gradle Files inside the Android Studio. Or else, you can execute .gradlew clean assembleDebug from the command line.
Step 5: Adding a login to the Application
As universal login is the best and easiest authentication method, it is mainly recommended for applications. You can hold user credentials by creating a new instance of the Auth0 class using the onCreate method.
Using the webauthprovider class and creating a loginWithBrowser method authenticates the new connections enabled on your application. As part of the initial configuration, you can pass the scheme value used in the auth0scheme manifest placeholder.
Once you call the webauthprovider#start function, the browser launches the login page. The callback URL is called after the user is authenticated. The callback URL will have the final result of the authentication process.
Step 6: Adding log out to the application
You can use webauthprovider to remove the cookies set by browsers when authentication is made. Therefore, users have to re-enter credentials whenever they login into applications.
Next, add a logout method to the application so that users can close their session and log out from the application. As part of the initial configuration, you can pass the scheme used in the auto0scheme manifest placeholder.
You can use the webauthorprovider class to log out of the session. This call helps open the browser and navigate users to the logout point.
Step 7: Showing user Profile Information
You can use the AuthenticationAPIClient class to get users’ profiles from Auth0. It requires the following two conditions:
- The access token must be returned from the login phase
- The webauthprovider.login contains the profile scope.
In case you need to retrieve the email scope of users, then you have to specify the email scope.
Excellent! Now you can log in, log out, and run a user profile in your Android application with the authentication made by Auth0.
Benefits of Auth0
- The heightened security offered by Auth0 reduces the security and compliance risks.
- Easy-to-use tools and procedures reduce developing time
- You can customise applications for authentication and authorisation
- Auth0 supports monitoring activities on accessing applications and resources
- Offers MFA and step-up authentication processes
- Insights gained from the analytics help to make crucial decisions
- Customisable User Interface supports users to make effective interaction
- Allowing Social media credentials simplifies signing-in processes
Conclusion:
Now, let’s wrap off! Auth0 offers excellent features such as SSO, MFA, customisable UI, etc. The tutorial on logging on to Android with Auth0 might have helped you learn better. As a whole, Auth0 supports protecting applications and resources by preventing unauthorised entries and attacks. Auth0 is one of the best tools for authentication and authorisation processes, which allows for keeping user and enterprise data safe and secure.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| OKTA Training | Feb 24 to Mar 11 | View Details |
| OKTA Training | Feb 28 to Mar 15 | View Details |
| OKTA Training | Mar 03 to Mar 18 | View Details |
| OKTA Training | Mar 07 to Mar 22 | View Details |





