- 6 Hot And In-Demand Tech Areas In 2024
- How To Forward Your Career With Cloud Skills?
- Top 7 On-Demand IT Certifications
- Most In-demand Technologies To Upskill Your Career
- Top 10 Hottest Tech Skills to Master in 2024
- Top Skills You Need to Become a Data Scientist
- Groovy Interview Questions
- Facets Interview Questions
- Crystal Reports Tutorial
- VAPT Interview Questions
- Flutter Tutorial
- Saviynt VS Sailpoint
- Flutter vs Xamarin
- PingFederate Interview Questions and Answers
- Dart vs Javascript : What's the Difference?
- Terraform Private Registry
- Cylance Interview Questions and Answers
- Sophos Interview Questions and Answers
- Top Camunda Interview Questions
- NUnit Interview Questions and Answers
- Impala Interview Questions and Answers
- ETL Tutorial
- Ionic Interview Questions
- Grafana Tutorial
- What is VAPT? - A Complete Beginners Tutorial
- SnapLogic Interview Questions
- Saviynt Interview Questions
- SnapLogic Tutorial
- Grafana Interview Questions
- RHCE Interview Questions and Answers
- Web Services Interview Questions
- Domo Interview Questions and Answers
- Terraform Interview Questions
- What is Sophos? | Sophos Turorial for Beginners
- Top Servlet Interview Question And Answers
- NLP Interview Questions and Answers
- Microsoft Intune Interview Questions
- Top XML Interview Questions And Answers
- Tosca Commander
- Katalon vs Cypress
- SQLite Tutorial
- Tosca Tutorial - A Complete Guide for Beginners
- Xamarin Interview Questions and Answers
- UiPath vs Automation Anywhere - The Key Differences
- OpenShift Interview Questions
- What is Katalon Studio - Complete Tutorial Guide
- Kronos Interview Questions
- Tosca Framework
- Burp Suite Tutorial
- Mendix Interview Questions
- Power Platform Interview Questions
- Burp Suite Interview Questions
- What is Mendix
- What is Terraform ?
- Burp Suite Alternatives
- Dart vs Kotlin
- What is Kronos?
- ES6 Interview Questions
- Entity Framework Interview Questions
- COBOL Interview Questions
- Express JS Interview Questions
- OSPF Interview Questions
- LINQ Tutorial
- CSS3 Interview Questions and Answers
- Auth0 Tutorial
- MS Access Interview Questions
- What is SPARQL - A Complete Tutorial Guide
- ExpressJS Tutorial
- UML Tutorial
- HTML vs XML
- Cypress vs Jest
- Impacts of Social Media
- OWASP Interview Questions
- Security Testing Interview Questions
- OpenShift vs Docker
- ES6 Tutorial
- Spark SQL Interview Questions
- Spark SQL Tutorial
- What is OWASP?
- AppDynamics Interview Questions
- Dynatrace Interview Questions
- Rest Assured Tutorial
- New Relic Interview Questions
- REST API Tutorial
- Datadog Interview Questions
- Rest API Interview Questions
- Rest Assured Interview Questions
- PTC Windchill Interview Questions
- Easiest Tech Skills To Learn
- Python SQLite Tutorial - How to Install SQLite
- Datadog Tutorial - Datadog Incident Management
- What is AppDynamics - AppDynamics Architecture
- RabbitMQ Interview Questions And Answers
- What is Dynatrace
- Datadog Vs Splunk
- Web Developer Job Description
- JP Morgan Interview Questions
- Types of Corporate Training
- Benefits of Corporate Training
- What is Corporate Restructuring?
- Blended Learning in Corporate Training
- What is Corporate Level Strategy?
- Flutter Projects and Use Cases
- How to Become a Web Developer
- How To Install Keras?
- How to Install Flutter on Windows?
- How to Install Cypress on Windows?
- How to Become a Computer Scientist?
- How to Install Katalon Studio in Windows
- How to Become a Programmer
- OWASP Projects and Use Cases
- How to Install Sophos?
- Workato Tutorial
- Workato Tutorial - What is Workato?
For business authentication and single sign-on, PingFederate is the gold standard. All of your identification systems and business apps are seamlessly integrated and automated using PingFederate Workflows.
What is PingFederate?
PingFederate is the industry's most popular enterprise federation server for user authentication and standards-based single sign-on (SSO) for the worker, partnership, and client identities.
Outbound and inbound SSO, federated identity management, customer identity and access management, mobile identity security, API security, and social identity integration are all possible with PingFederate. Using standard identity protocols like SAML, WS-Federation, WS-Trust, OAuth, OpenID Connect, and System for Cross-domain Identity Management, browser-based SSO extends employee, customer, and partner identities across domains without the use of passwords (SCIM).
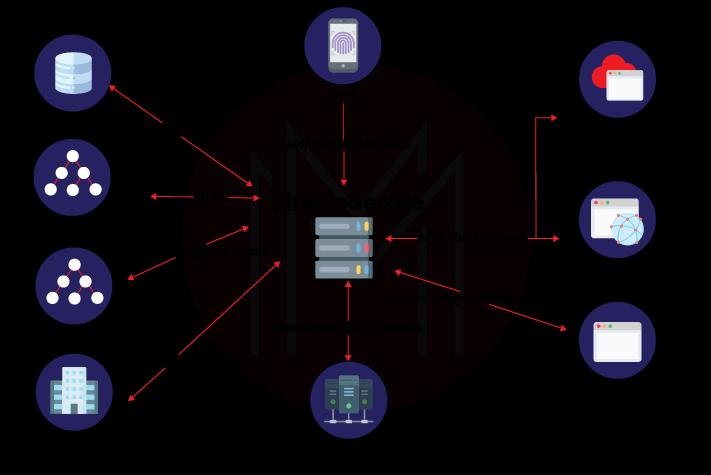
Features of PingFederate
Some of the things that PingFederate has to offer are as follows:
- Secure and standards-based
- Support diverse identity types and use cases
- Easily configurable
- Adaptive authentication
- Customizable branding
- Lightweight, scalable architecture
- Pre-built adaptors and integrations
- Multi-protocol support
- Advanced user management
What is PingFederate used for?
PingFederate helps firms to migrate away from inflexible, expensive legacy identity and access management solutions and instead adopt a modern identity and access management solution designed to meet the needs of complex enterprises.
| If you want to enrich your career and become a professional in PingFederate, then enroll in "PingFederate Online Training".This course will help you to achieve excellence in this domain. |
What is Adapter in PingFederate?
For a single sign-on request, PingFederate can utilize adapter selectors to select from a list of configured IdP adapter instances. The choice is based on the user's IP address, the authentication context, and other criteria.
An IDP adaptor collects information about the identity authenticating and transmits it to the PingFederate server to continue the federated authentication operation in the "first mile" of application integration.
What is PingFederate SAML?
SAML (Security Assertion Markup Language) is an accessible standard that allows people to sign in for just a single click (SSO). Users could offer continuous access to services and minimize unsafe passcode propagation by enabling numerous sources to be accessed with just a single pair of login credentials.
Identity federation is made possible via SAML, which allows identity providers (IdPs) to provide validated identities and attributes to service providers in a seamless and safe manner (SPs). When it comes to federated identity installations, SAML is the most widely accepted standard. SAML has been chosen as the standard protocol for transmitting identities across the internet by thousands of corporate organizations, government agencies, and service providers.
What is a Ping Agent?
Agents are server-side plugins that are implemented on the targeted app's web server. User requests to maintain apps are intercepted by agents, who then contact the Policy Manager or use cached information to certify or refuse the proposal to move ahead. The PingAccess Agent Protocol (PAAP), which defines the possible interactions between agents and the Policy Server, is used by agents to connect with the PingAccess Policy Server. Agents have a username that they use to identify themselves, as well as an encrypted message that they use to verify with Policy Server. Agents do not seem to be one-of-a-kind. There could be an unlimited count of agents with almost the same identity and secret, and Policy Server handles them all identically. This is effective for large distributions where managing individual agents would be onerous.
How do you integrate PingFederate?
PingFederate sells integration kits that include adapters for connecting to the PingFederate server and agents for interacting with local IdM systems or applications, allowing both the Identity Provider (IdP) and Service Provider (SP) sides of the integration to function.
What is the PingFederate SDK?
Integration with identity providers (IdPs) and service providers is possible with the PingFederate SDK (SPs). Developers can use the SDK to create bespoke implementations for transmitting authentication and security data between PingFederate and their enterprise environment.
Is PingFederate an IdP?
PingFederate is a federation server that aids in the management of identities, single sign-on, and API security for enterprises. Companies can use PingFederate to streamline employee access to all of their company's applications. Employees can log into a corporate dock with a single set of credentials and open all of their applications with a single click using a single set of credentials.
What is PingFederate OAuth 2.0?
OAuth 2.0 is a mechanism for granting user credentials to customers of Representational State Transfer (REST) APIs, which secures app access to secured resources (and non-REST APIs). Instead of utilizing credentials or the credentials of a user to connect directly to the API, OAuth allows the client to present a previously obtained token. The token defines (or includes) a collection of client-specific properties and/or policies. When compared to the use of credentials (or passwords) straightforwardly on the API call, these tokens pose a lower risk of security and privacy. The API uses the characteristics to authenticate and allow access to the request.
The following steps give you a clear view of how to get started and use PingFederate
1. Click Digital Signing & XML Decryption Keys & Certificates on the Server Configuration page after logging in to PingFederate.
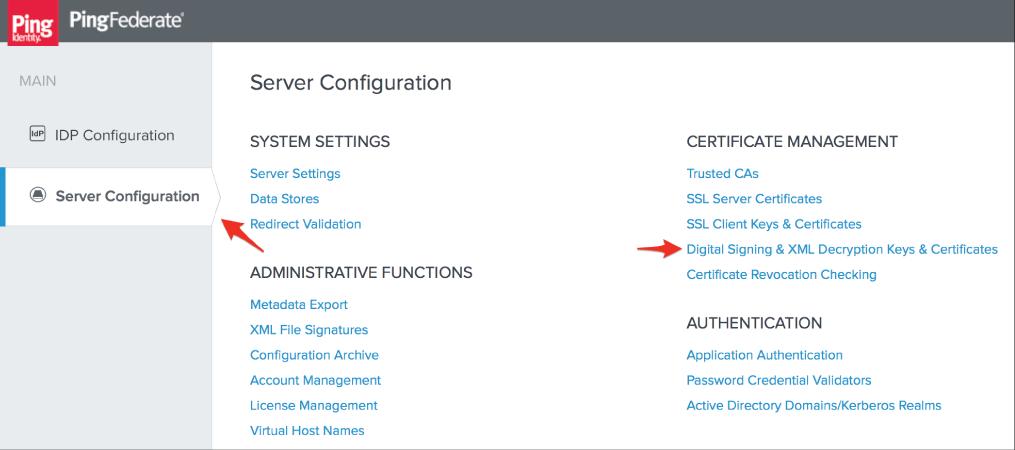
2. Skip to step 4 if you already have a certificate for your PagerDuty SSO configuration; otherwise, choose to Create New.
3. Enter the required information (Common Name, Organization, and Country) on the Create Certificate Summary screen, then click Next and Save. To return to the section Digital Signing & XML Decryption Keys &. For certificates, navigate to the section Digital Signing & XML Decryption Keys & Certificates.
4. You'll need the serial number of the certificate you're going to utilise with PagerDuty later. After that, select Export from the menu.
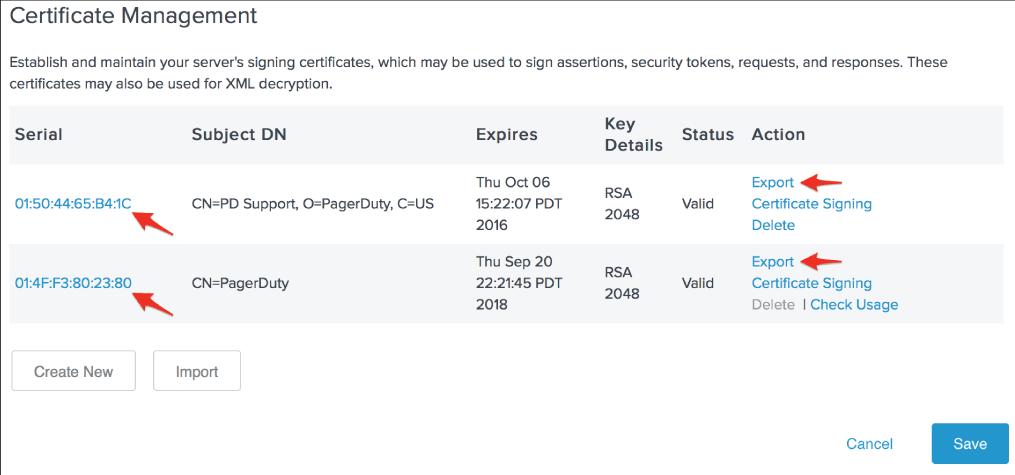
5. Click Next after selecting Certificate Only.
6. Save the certificate file to your computer by clicking Export, then open it in a plain text editor.
7. In a separate browser tab or window, log in to your PagerDuty account and click Account Settings from the Configuration menu. When you go to the Account Details page, on the right sidebar, click Single Sign-on.
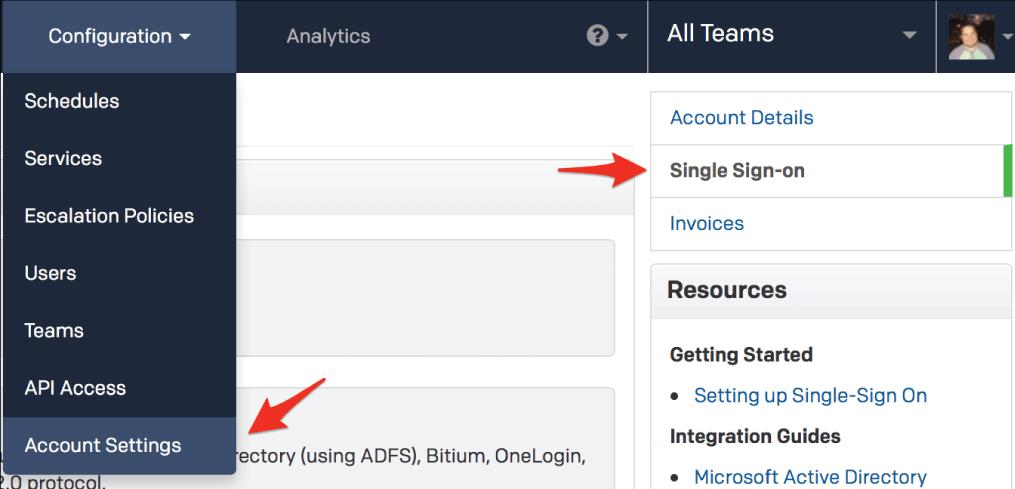
8. To configure Single Sign-On in PagerDuty, click the SAML radio button. In the X.509 Certificate area, paste the contents of the certificate file you downloaded in step 6 in the Login URL field and add the SAML endpoint for your PingFederate server. The default PingFederate SAML endpoint is
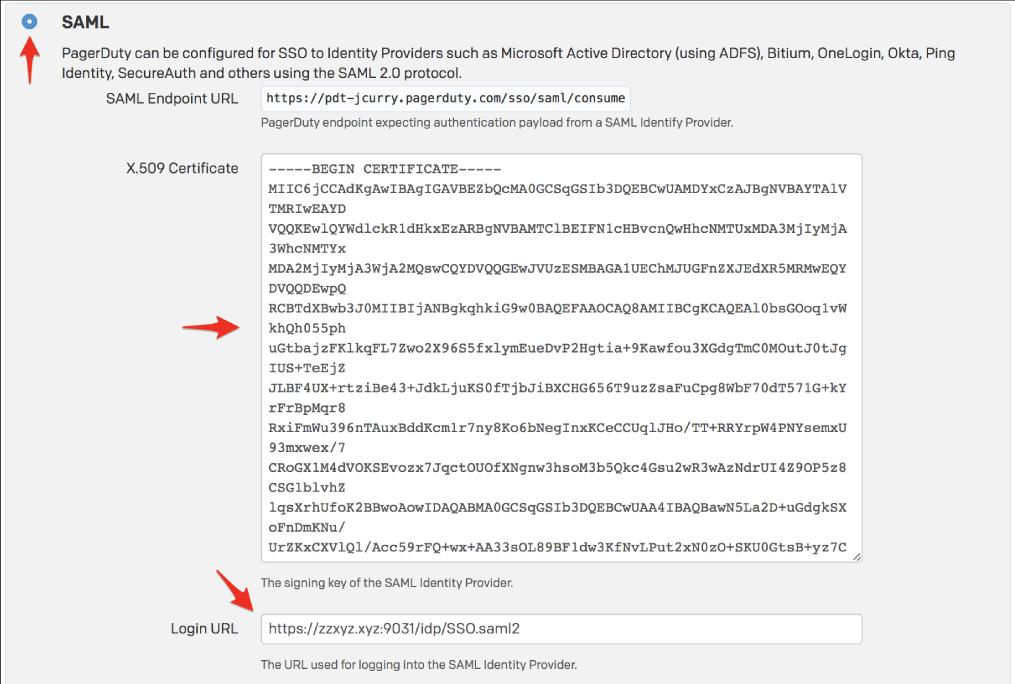
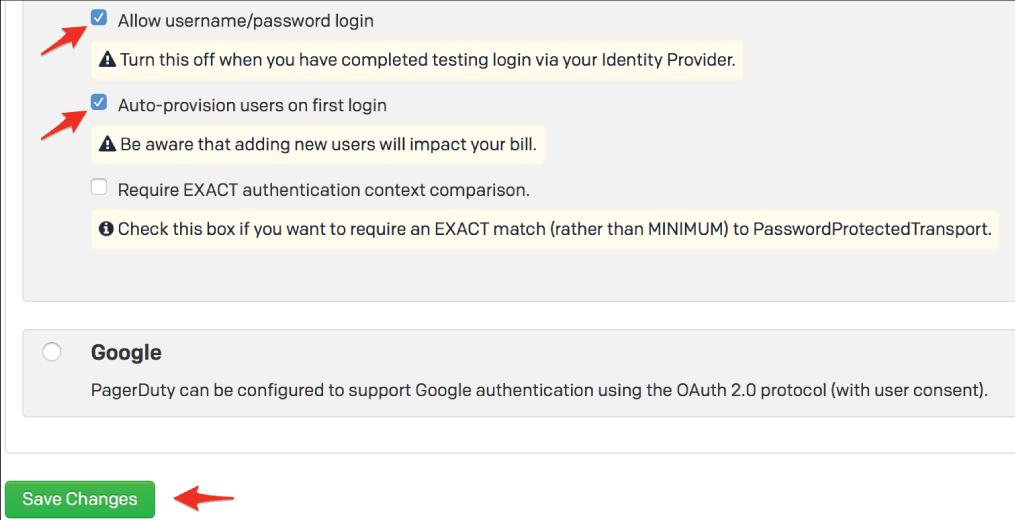
9. When you've finished testing the steps in this guide, come back to this page to stop user logins through username and password.
With auto-provisioning enabled, you may allow PingFederate users to create a PagerDuty account without having to do anything manually. However, going over the number of users included in your pricing plan will influence your payment.
When you're through with this page, click Save Changes.
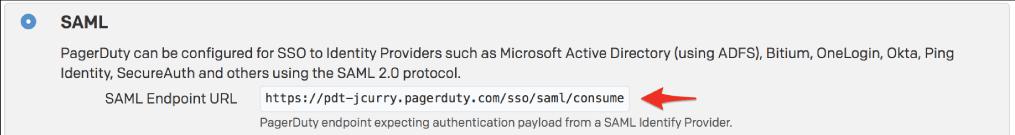
10. PagerDuty's SAML Endpoint URL should be copied.
11. In PingFederate, go to the IdP Configuration page, then select Create New under SP Connections.
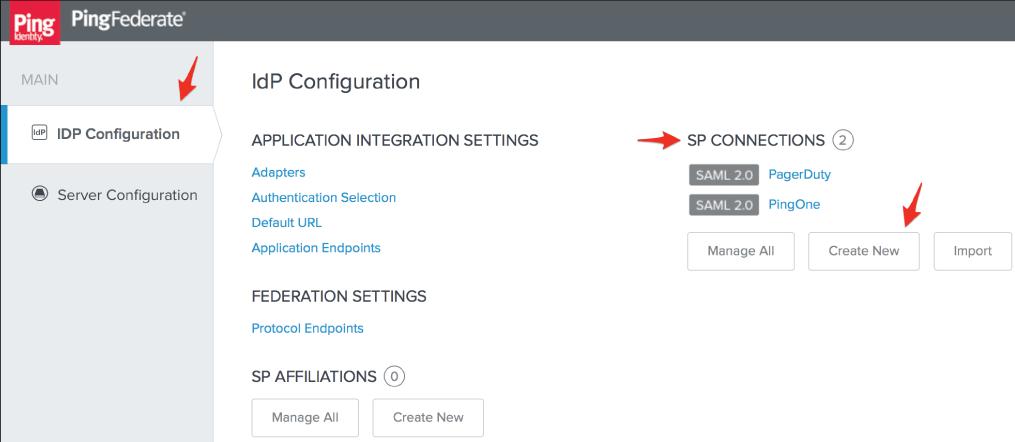
12. On the Connection Type screen, check the Browser SSO Profiles connection template and then click Next.
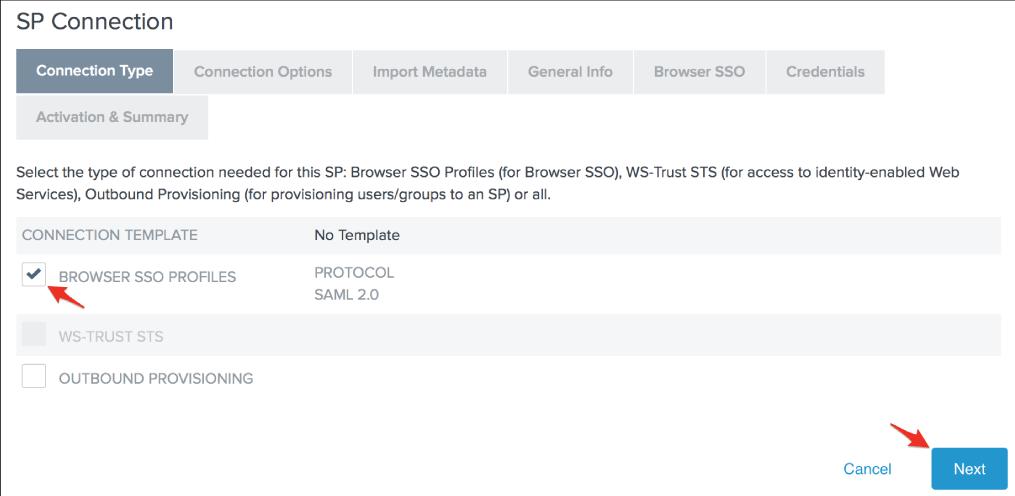
13. On the Connection Options screen, check the Browser SSO option and then click Next.
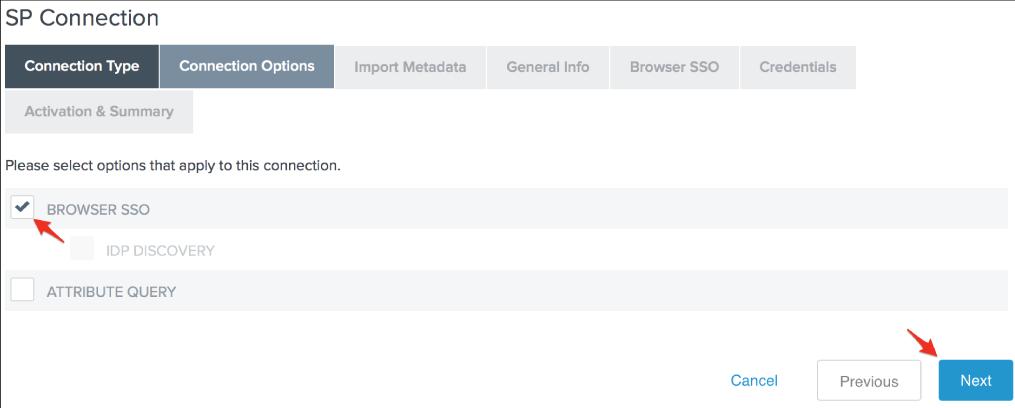
14. On the Import Metadata screen, there is no metadata to upload, so click Next to skip this step.
15. In the Partner's Entity ID (Connection ID) area, type your PagerDuty subdomain (with the https:// protocol handler), your preferred Link Id, and the SAML Endpoint URL you got through PagerDuty in the following steps in the above Basis URL field, then click Next.
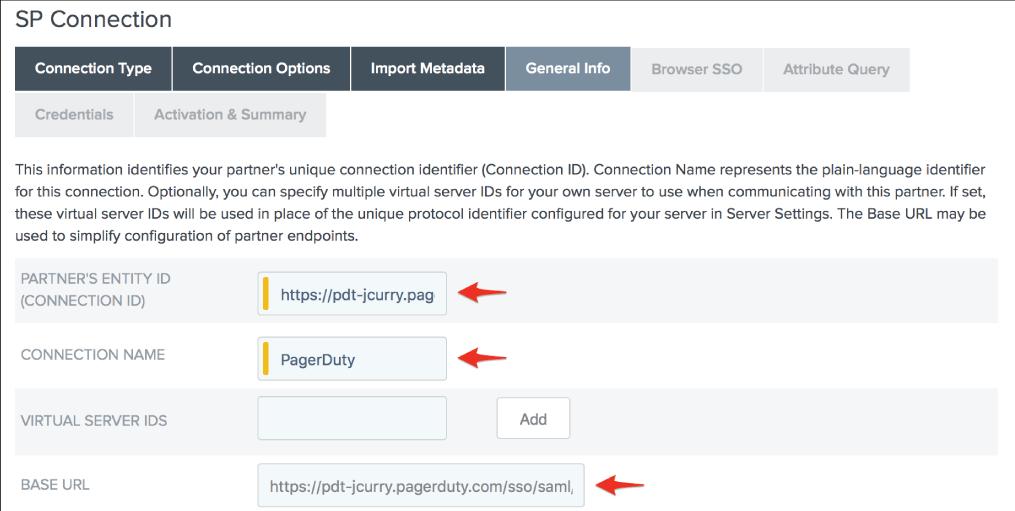
16. On the Browser SSO page, navigate to Configure Browser SSO.
17. On the SAML Profiles page, check the options for IdP-Initiated SSO and SP-Initiated SSO, then click Next.
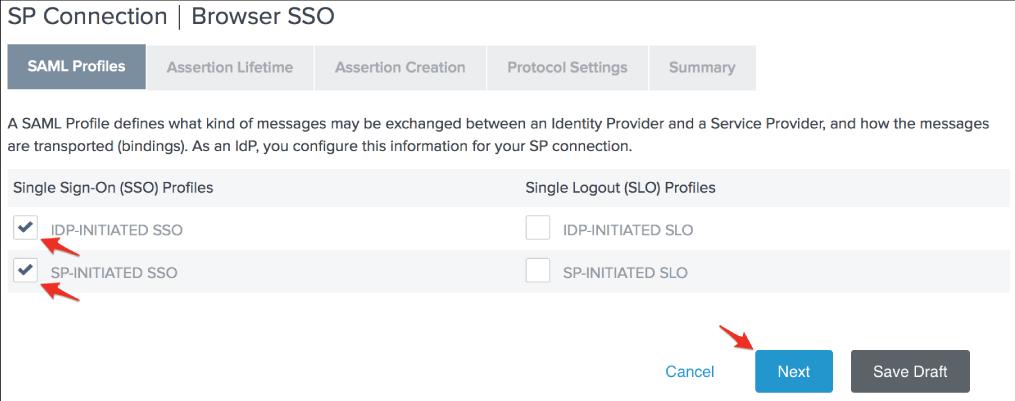
18. Click Next after entering your preferred Assertion Lifetime.
19. On the Assertion Creation page, click Configure Assertion Creation.
20. Click Next after selecting Standard Identity Mapping.
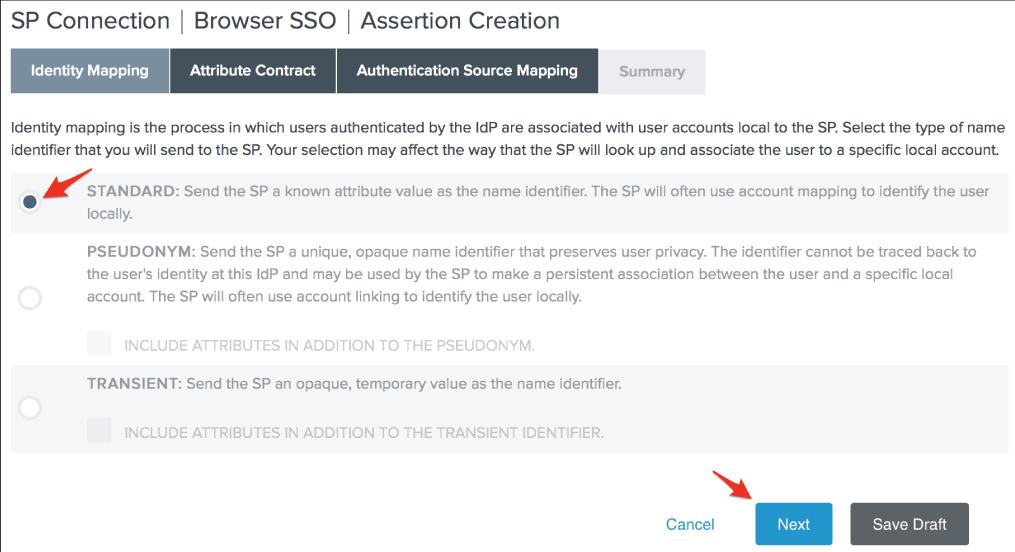
21. Change the SAML SUBJECT's Subject Name Format to
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
then ,click next.
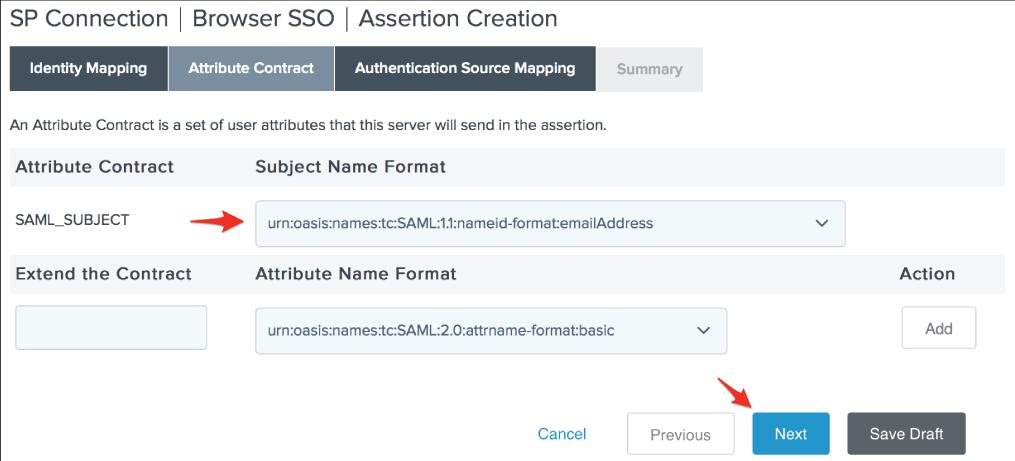
22. On the Authentication Source Mapping page, click Map New Adapter Instance.
23. Click Next after selecting your preferred Adapter Instance. We're utilizing the PingOne HTML Form Adapter in our environment, but you should choose the adapter that best suits your needs. PagerDuty's only condition is that the adapter you use offer the user's email address.
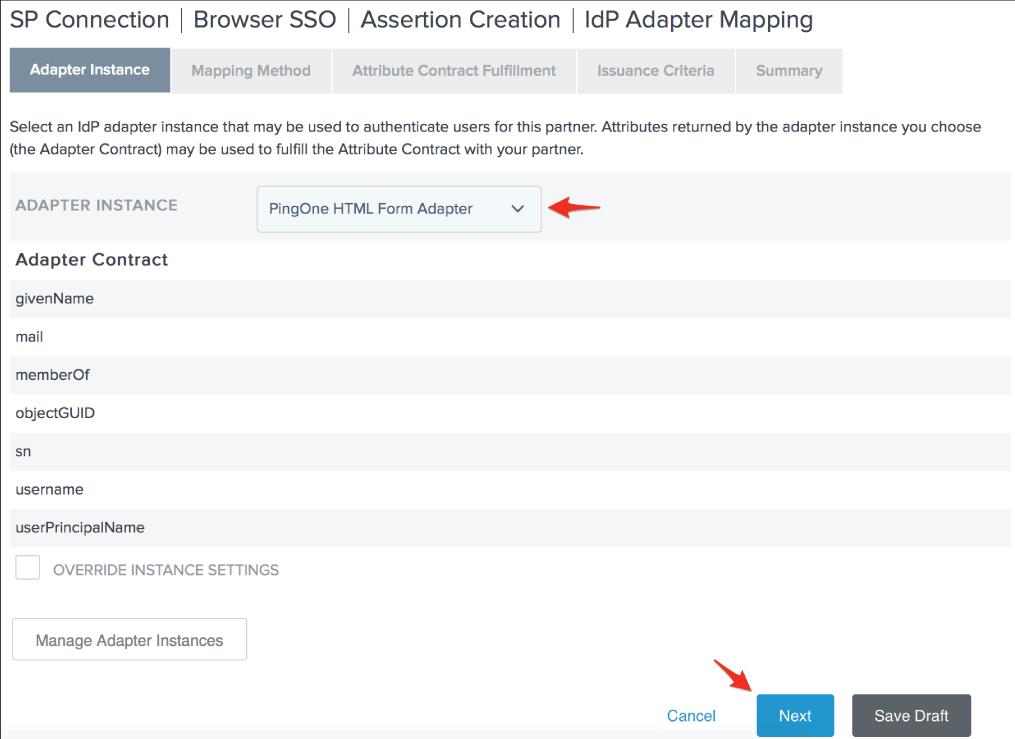
24. We can pick the Use solely the adapter contract values in the SAML assertion option and click Next because the adapter we selected for our environment contains the user's email address.
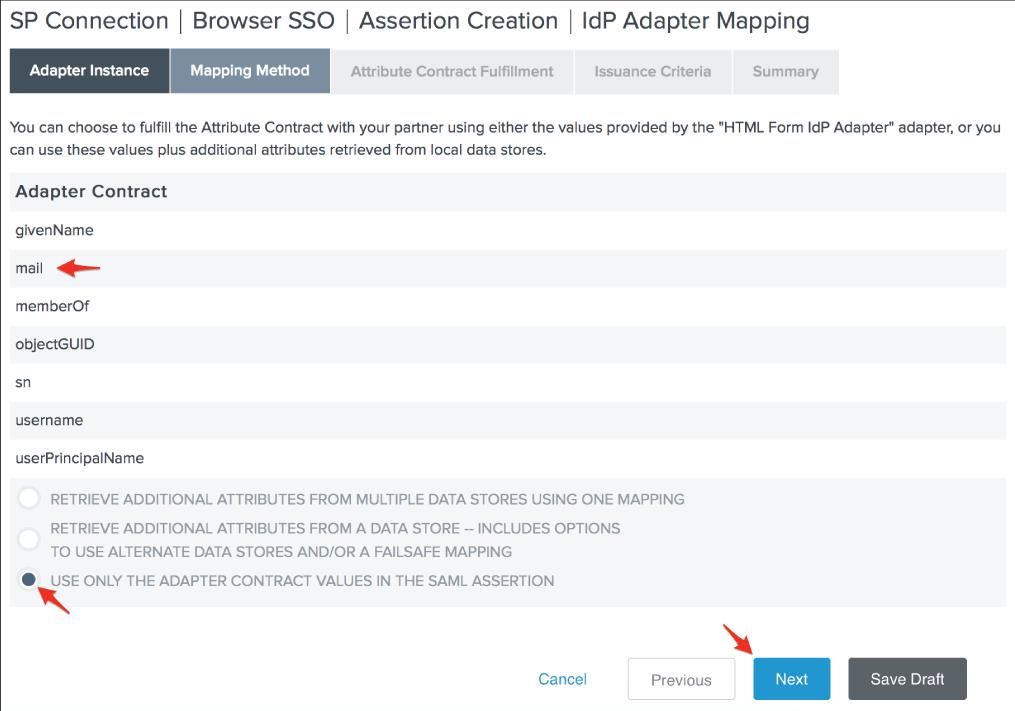
25. Click Next after setting your SAML_SUBJECT Source to your Adapter and its Value to the user's email address.
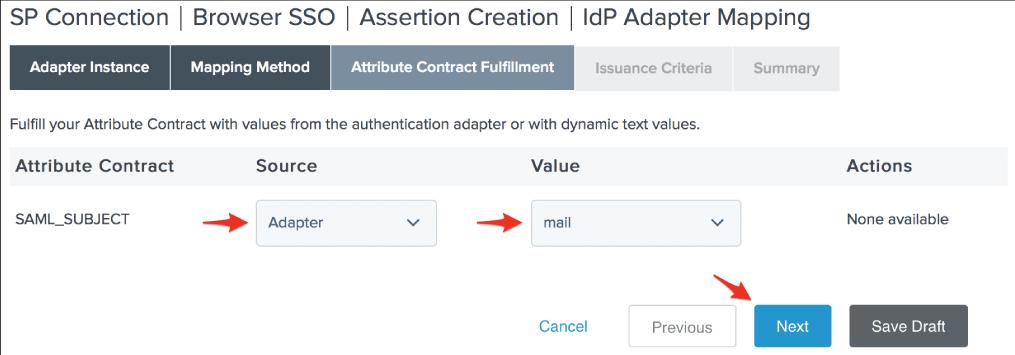
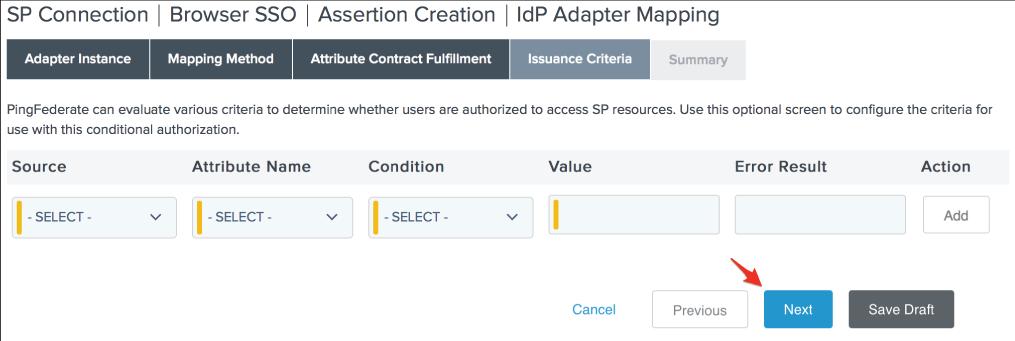
26. On the Issuance Criteria screen, specify any authorization conditions you want (if any), then click Next.
27. On the Adapter Mapping Summary screen, click Done.
28. On the Assertion Creation page, click Next, then on the Assertion Creation Summary page, click Done, and then on the Assertion Creation page, click Next.
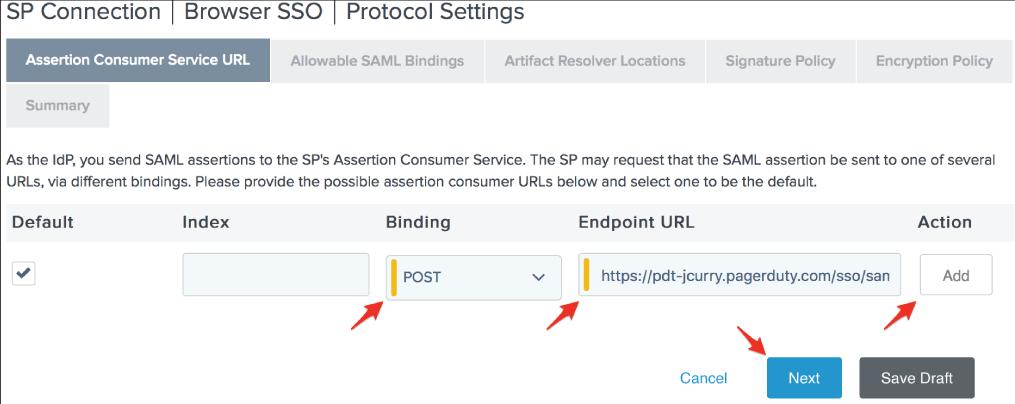
29. On the Protocol Settings page, click Configure Protocol Settings.
30. Set the Binding to POST and paste the PagerDuty SAML Endpoint URL into the Endpoint URL bar, then click Add and Next.
31. On the Allowable SAML Bindings page, check POST and then click Next.
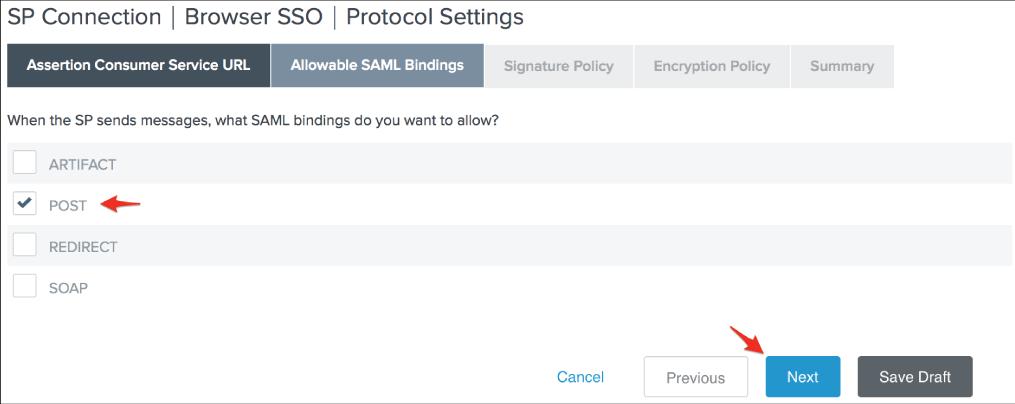
32. On the Signature Policy page, click Next, then Next again on the Encryption Policy page. Finally, on the Protocol Settings Summary page, click Done.
33. On the Protocol Settings screen, go to the next step by clicking Next.
34. On the Browser, SSO Summary page, click Done, then proceed to the Browser SSO page by clicking Next.
35. On the Credentials page, select Configure Credentials.
36. Choose the PagerDuty-compatible Signing Certificate. The serial number you noted in step 4 will assist you in determining which certificate is correct. Check Click Next after adding the certificate to the signature's keyinfo> section.
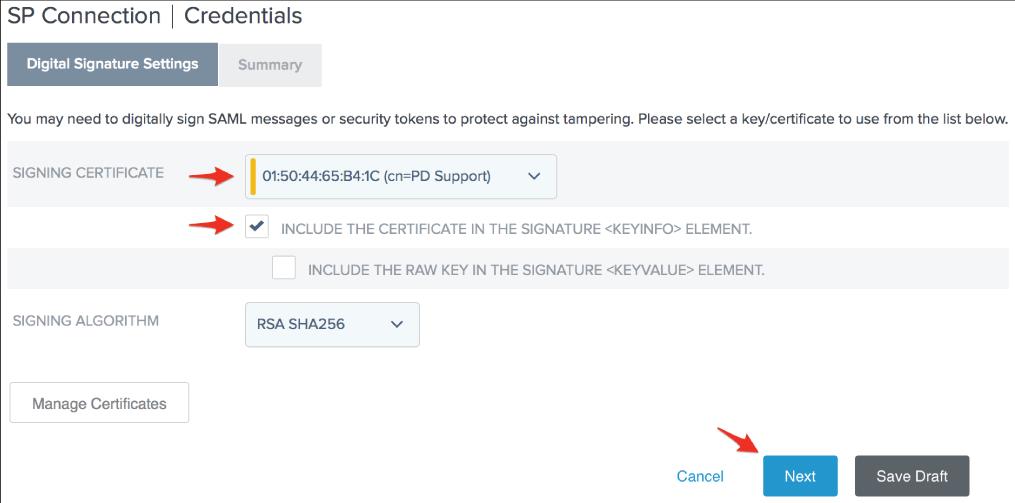
37. After clicking Done on the Digital Signature Settings Summary page, go to the Credentials page and click Next.
38. Change the Connection Status to Active on the Activation & Summary screen, then scroll down and click Save.
39. That concludes our discussion. PagerDuty should now be accessible using PingFederate.
What is SSO and how does it work?
Single sign-on (SSO) allows a user to access various applications and services with just one set of credentials. SSO improves security and user experience for customers, employees, and partners by lowering the number of required accounts/passwords and simplifying access to all of the apps and services they require.\
Working of SSO
- To make SSO possible, an identity provider (IdP) must set up a centralized authentication server that all apps can utilize to verify a user's identity. This server can verify user IDs and generate access tokens, which are encrypted bits of data that verify a user's identity and rights.
- The username and password are sent to the identity provider for verification the first time a user signs on. The authentication server compares the credentials to the directory containing the user's data and then starts an SSO session in the user's browser.
- Rather than asking for user credentials, the network operator requires that the identity provider verifies the digital credentials when the user seeks access to applications inside that trusted group.
- Without ever displaying the user the sign-on screen, the identity provider provides an access token, and the service provider grants access.
| Also, read PingFederate Interview Questions and Answers that help you in cracking your interview |
Conclusion
PingFederate allows you to deliver seamless access to data and applications without the burden of numerous sign-on and passwords, which increases staff productivity and improves customer experiences. We hope this blog on “What is PingFederate'' he lped you explore more about PingFederate.
 On-Job Support Service
On-Job Support Service
Online Work Support for your on-job roles.

Our work-support plans provide precise options as per your project tasks. Whether you are a newbie or an experienced professional seeking assistance in completing project tasks, we are here with the following plans to meet your custom needs:
- Pay Per Hour
- Pay Per Week
- Monthly
| Name | Dates | |
|---|---|---|
| PingFederate Training | Feb 28 to Mar 15 | View Details |
| PingFederate Training | Mar 03 to Mar 18 | View Details |
| PingFederate Training | Mar 07 to Mar 22 | View Details |
| PingFederate Training | Mar 10 to Mar 25 | View Details |

Madhuri is a Senior Content Creator at MindMajix. She has written about a range of different topics on various technologies, which include, Splunk, Tensorflow, Selenium, and CEH. She spends most of her time researching on technology, and startups. Connect with her via LinkedIn and Twitter .





